Chaotic secret communication system based on digital chaotic coding algorithm
A coding algorithm and technology of chaotic ciphers, which are applied in the field of secure communication systems, can solve problems such as digital chaotic cipher methods and technologies that have not been reported, and effectively generate complex and unsolved problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] In order to describe the digital chaos security technology more clearly, then the figure introduces the principle and method of the digital chaos security technology in detail.
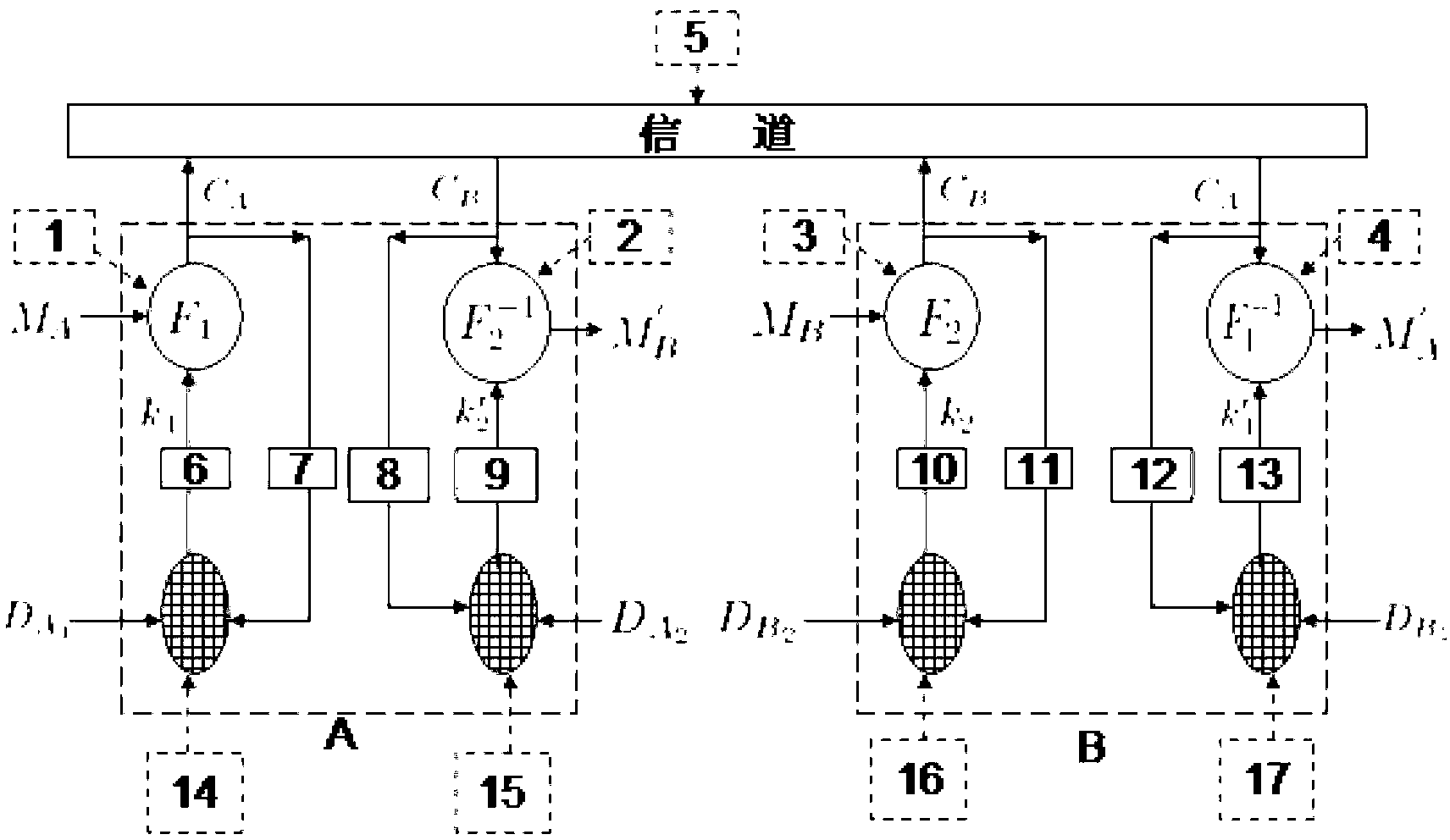
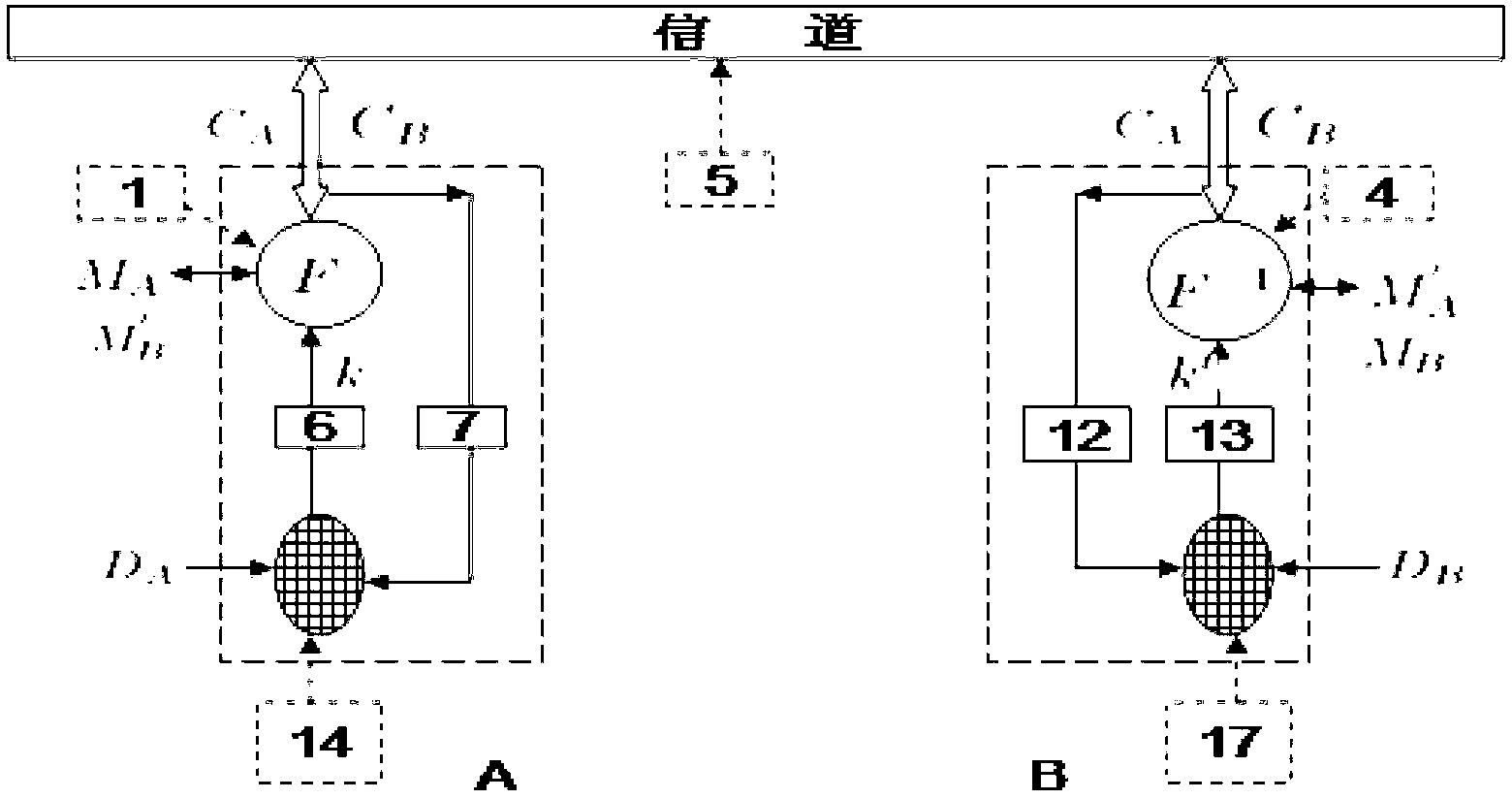
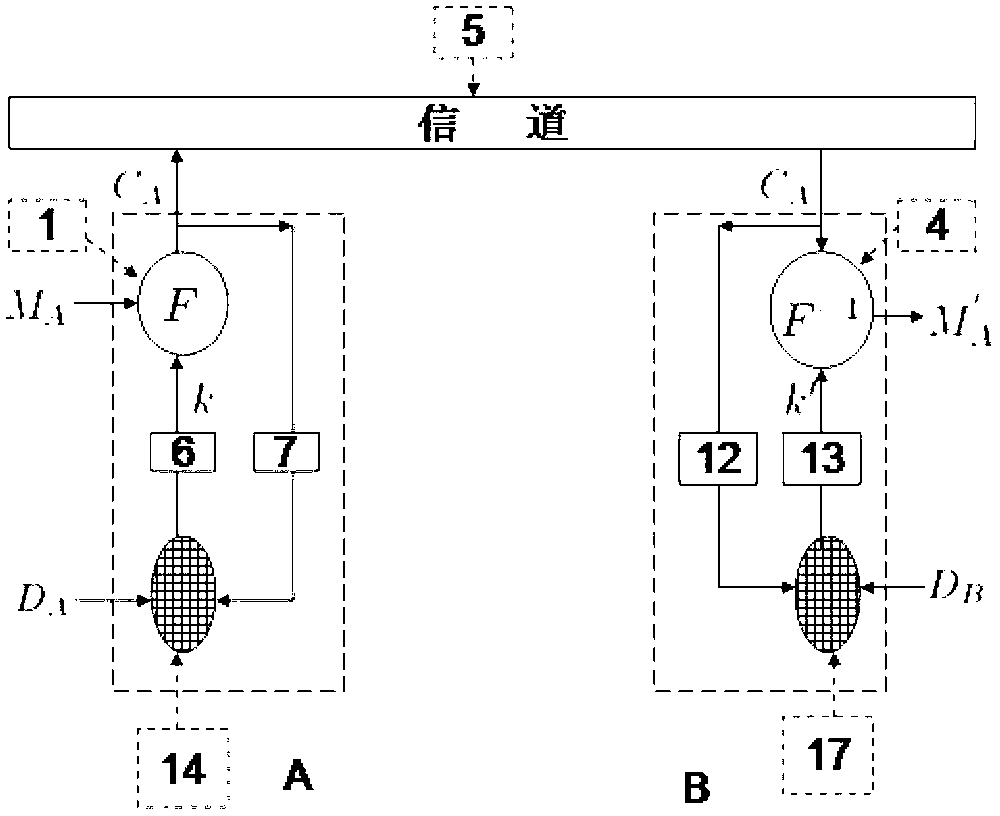
[0065] figure 1 It is a full-duplex two-way digital chaos security communication system of the invention technology. The information sender and the receiver each have two (same or different) chaotic networks for chaotic encryption and chaotic decryption. The encryption and decryption passwords of one party are generated by different chaotic networks, but the corresponding pair of both parties (such as figure 1 14 and 17 and 15 and 16) Encryption and decryption chaotic networks must have the same topology and dynamics. encryption function F i (i=1,2) satisfy F i f i -1 =I. The digital information M is encrypted by the chaotic cipher through the F function operation and the ciphertext C is transmitted to the receiving end through the channel (including digital multiplexer, modulator, demodu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com