Integrated core network and accessing method thereof
A core network and access network technology, applied in the field of converged networks, can solve problems such as AC forwarding bottlenecks and affect AC performance, avoid business and management bottlenecks, and ensure access control and service quality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
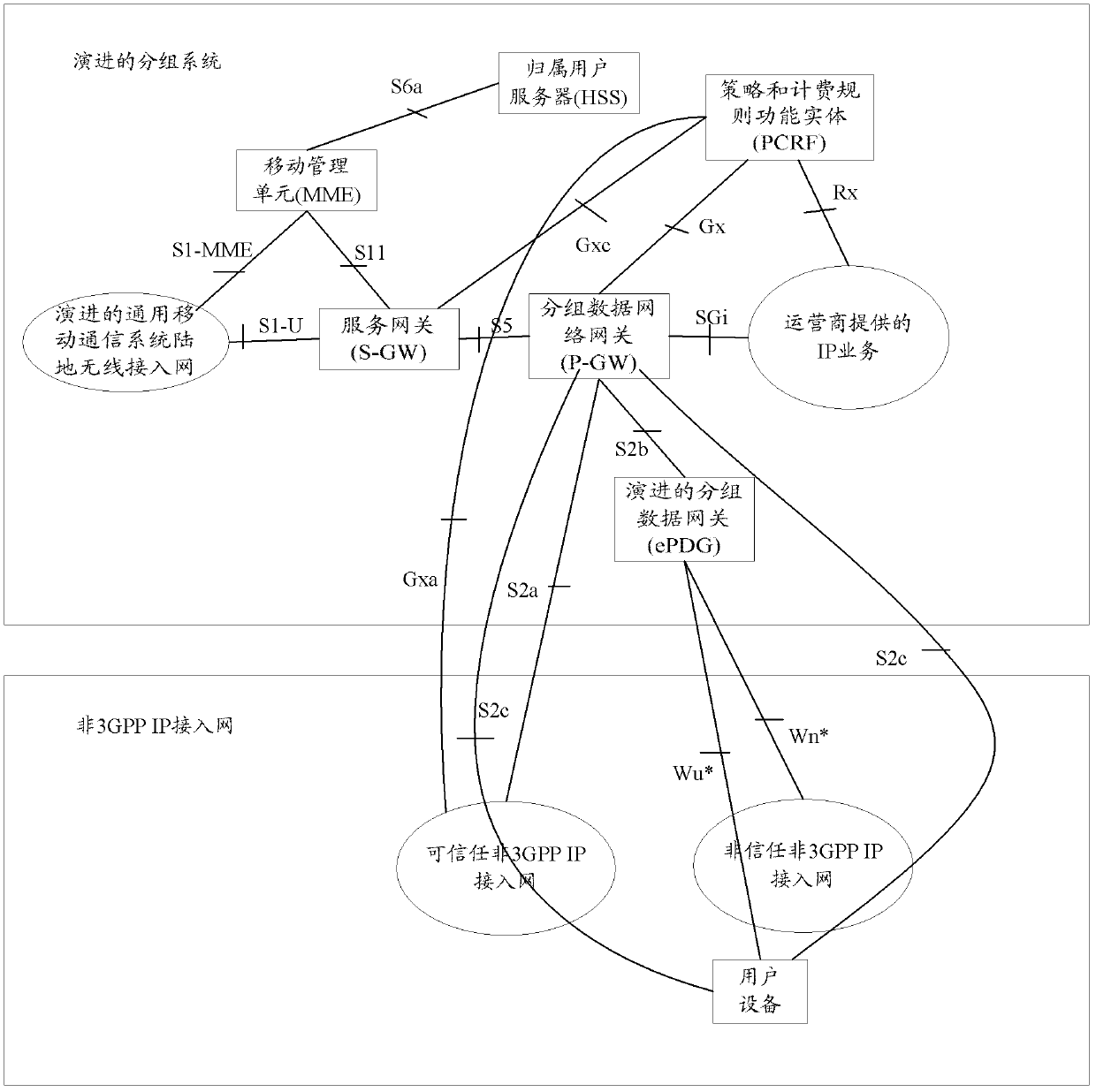
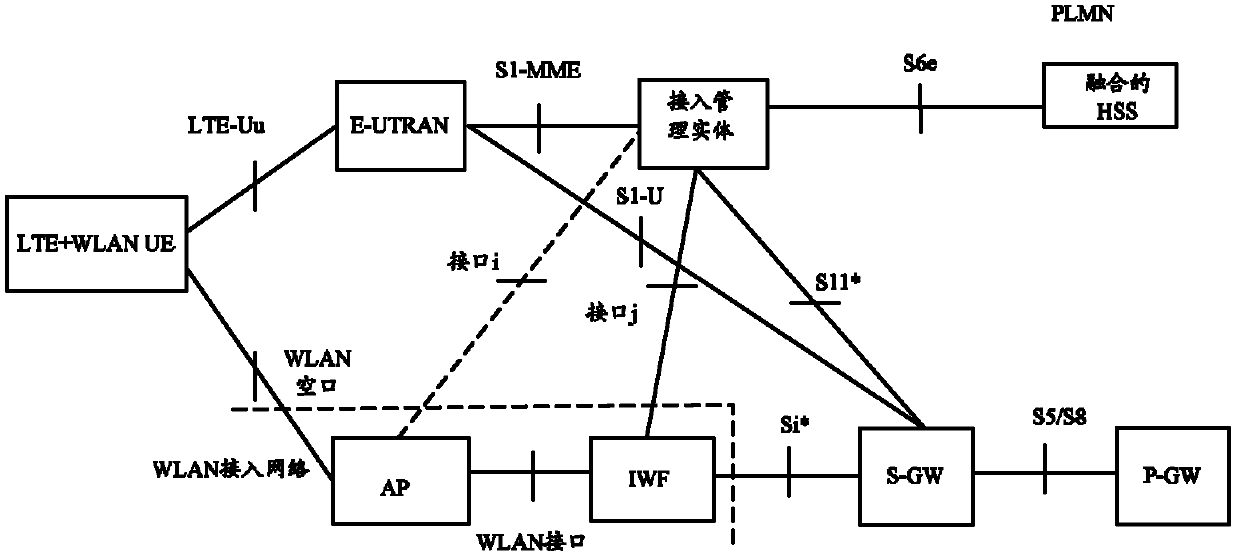
[0097] Figure 3a It is a schematic diagram of a non-roaming scenario of architecture 1 in which UE accesses EPS through a trusted WLAN in the present invention, Figure 3b It is a schematic diagram of a roaming home access scenario in architecture 1 in which UE accesses EPS through a trusted WLAN in the present invention, Figure 3c It is a schematic diagram of a roaming access scenario in Architecture 1 in which a UE accesses an EPS through a trusted WLAN in the present invention. In this embodiment, it mainly describes the UE supporting WLAN access and LTE access, respectively through the trusted WLAN and LTE access fusion core network architecture diagram, the network element connection interface and connection structure are as follows Figures 3a-3c shown. In the architecture of this example, the functions of the control plane and the user plane of the WLAN network are separated. Among them, the access management entity in the 3GPP network implements the management fun...
Embodiment 2
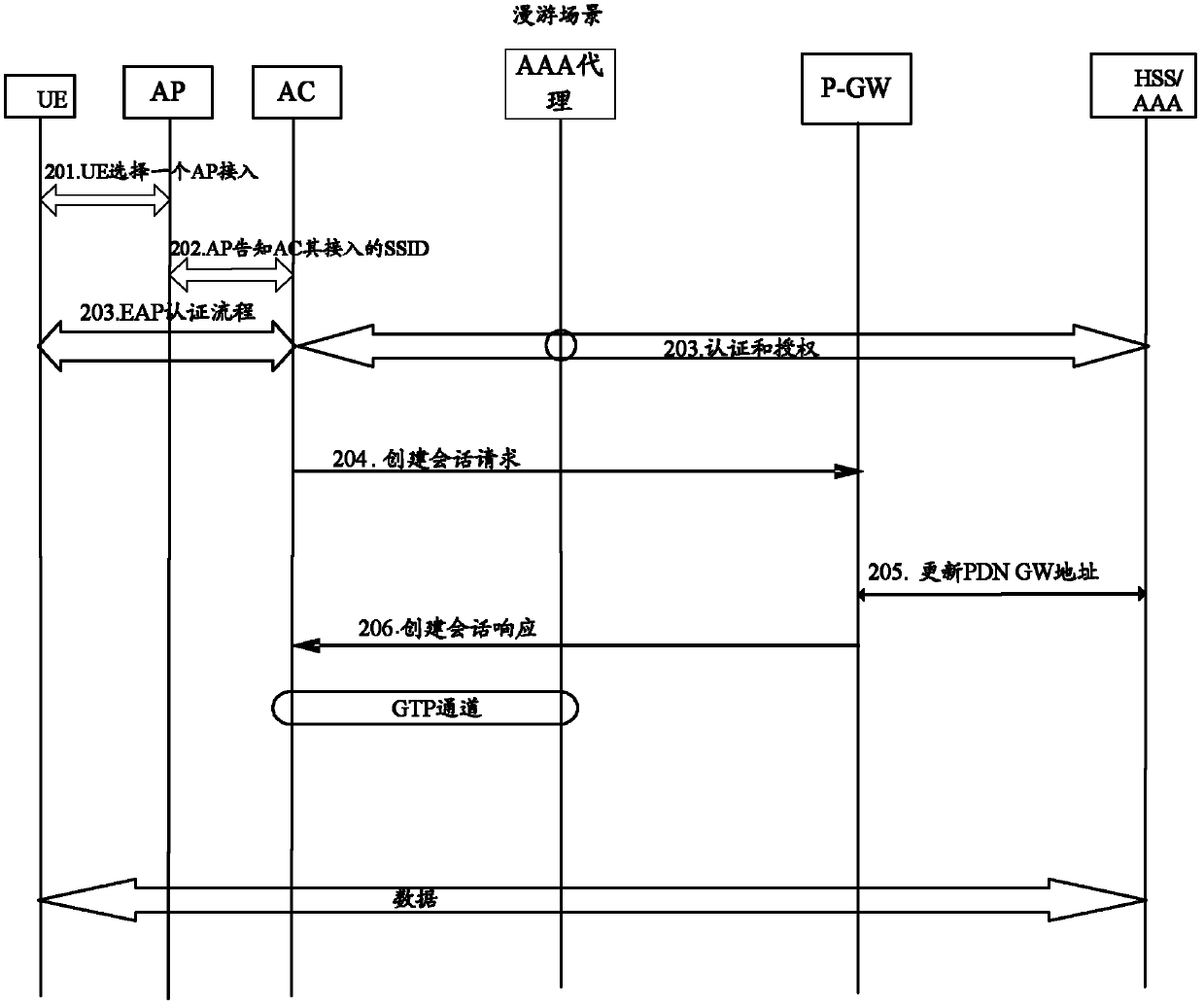
[0115]This example is based on architecture 1-1. In the roaming home access scenario, the UE attaches to the EPC through the WLAN. In this process, the AP only needs to discover and select the address of the IWF, and the AC discovery mechanism in the existing WLAN network can be used. The IWF needs to discover and select the access management entity, and the DNS / DHCP query mechanism or other discovery mechanisms can be used. Figure 4 In the roaming home access scenario of Architecture 1-1 in the present invention, the UE attaches to the EPS through a trusted WLAN, as shown in Figure 4 As shown, in this example, the attach process of the UE accessing the EPS includes the following steps:
[0116] In step 401, the UE selects a service set identifier (SSID, Service Set Identifier) according to the wireless mechanism of the WLAN, and accesses the corresponding AP.
[0117] Step 402-step 404, the AP can determine the SSID it accesses according to the UE's Medium Access Control...
Embodiment 3
[0137] This embodiment is an attachment process of a user accessing an EPC through a WLAN in a roaming home access scenario in architecture 1-2. The main difference between this embodiment and Embodiment 2 is that a CAPWAP tunnel needs to be established between the access management entity and the AP, and the AP needs to discover the addresses of the IWF and the access management entity, which is equivalent to connecting the AP to two ACs at the same time , and the current AP is only connected to one AC, so the AP needs to be enhanced. Figure 5 It is the attachment flow chart of UE accessing EPS through trusted WLAN in the roaming home access scenario of architecture 1-2 in the present invention, as shown in Figure 5 As shown, in this example, the attach process of the UE accessing the EPS includes the following steps:
[0138] Step 501 is the same as step 401.
[0139] Step 502-step 504, the AP can determine the SSID it accesses according to the medium access control laye...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com