Method and device for clearing malicious power consumption applications, and user terminal
A technology of user terminal and cleaning method, which is applied in the field of user terminal equipment, can solve problems such as damage to battery life of smart terminals, inability to accurately locate bad applications, and high screen brightness, so as to improve battery life, avoid power consumption, and ensure use The effect of experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
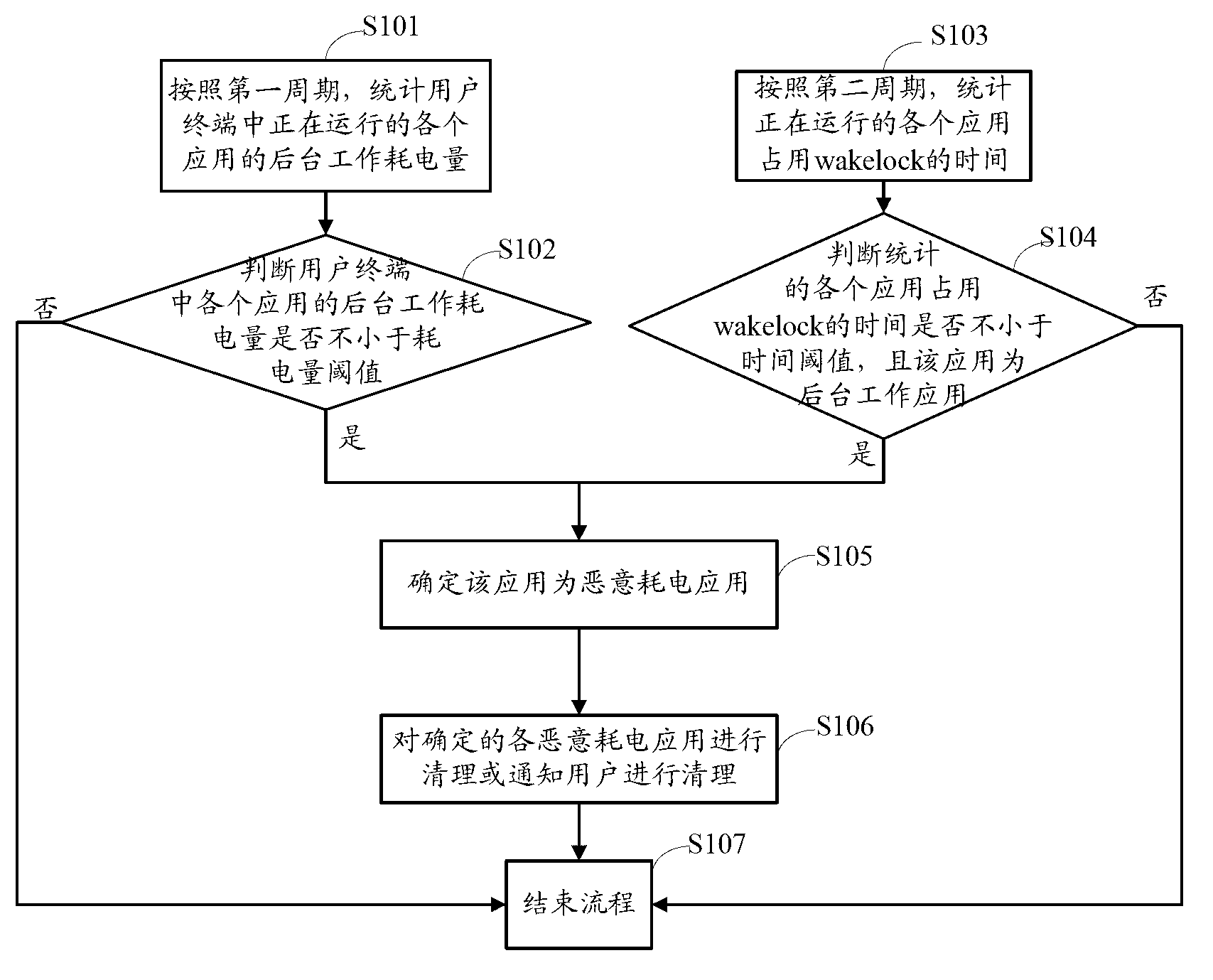
[0049] The following describes specific implementations of a method, device, and user terminal for cleaning malicious power-consuming applications provided in the embodiments of the present invention with reference to the drawings in the description.
[0050] Firstly, the method for cleaning malicious power-consuming applications provided by the embodiments of the present invention will be described in detail.
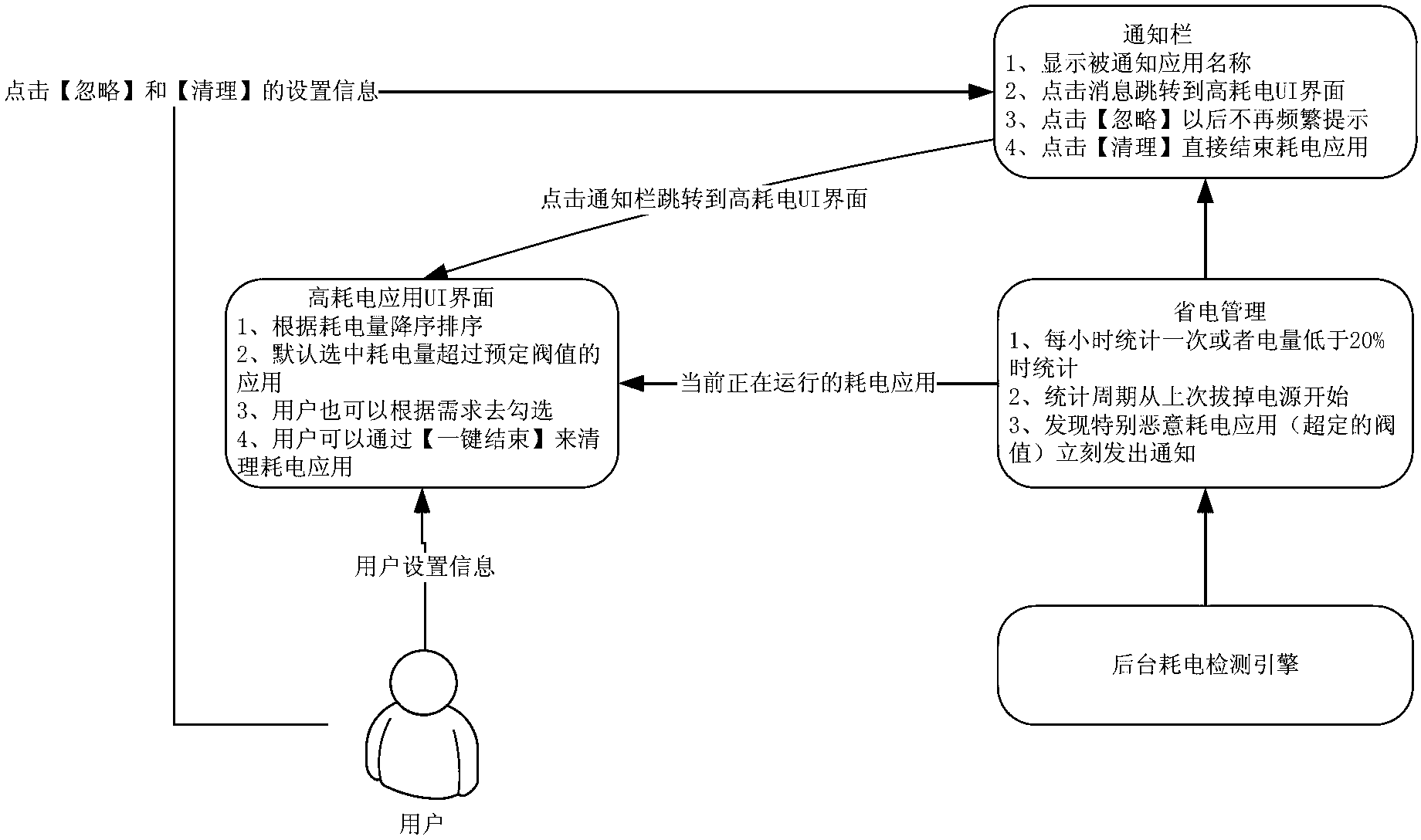
[0051] Starting from the methods of malicious power consumption in existing user terminals, the inventors found that malicious power consumption applications can usually consume the power of user terminals in the following two ways:
[0052] One way is that under normal use of the user terminal, the application uses resources unreasonably in the background, resulting in high power consumption;
[0053] Another way is that when the screen is turned off (that is, when the user does not need to use the mobile phone, also known as the black screen), a background applicatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com