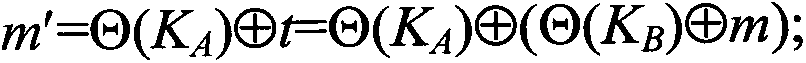Method for establishing anti-attack public key cryptogram
A public key cryptography, anti-attack technology, applied in the field of information security, can solve problems such as hidden dangers in the security of public key cryptography identity verification data protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] A public key cryptographic protocol against quantum computing attacks of the present invention will be further described in detail below in conjunction with embodiments.
[0061] 1. Establish a platform for public key cryptographic protocols
[0062] The platform for establishing all public-key cryptographic protocols is an infinite non-abelian group G and two subgroups A and B of G, so that for any a∈A and any b∈B, the equation ab=ba holds. In addition, due to the needs of encoding and key generation, G must also meet the following conditions:
[0063] 1) A word representing an element of G on the generator set of G has a computable normal form;
[0064] 2) G is at least exponential growth (exponential growth), that is, the number of elements in G whose word length is a positive integer n is bounded by an exponential function about n;
[0065] 3) The product operation and inversion operation based on the normal form of the group are feasible and computable.
[0066] F...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com