Authentication method and wireless connection device
一种无线连接装置、认证方法的技术,应用在安全装置、无线通信、数字数据认证等方向,能够解决第三者非法利用等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
[0073] A-1. The general structure of the system:
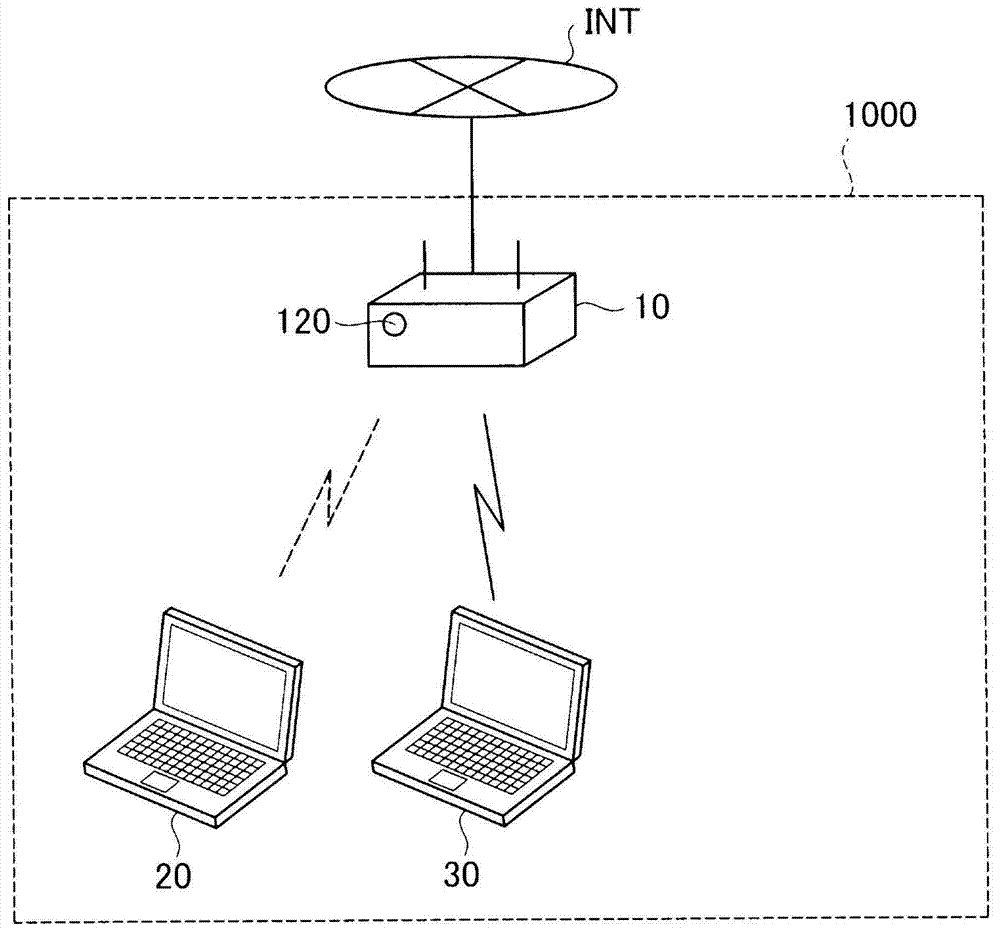
[0074] figure 1 It is an explanatory diagram showing a schematic configuration of a network system using a wireless network relay device according to an embodiment of the present invention. The network system 1000 includes a wireless network relay device 10 as a wireless connection device and two client devices 20 and 30 . In addition, the client device is simply referred to as "client" below.
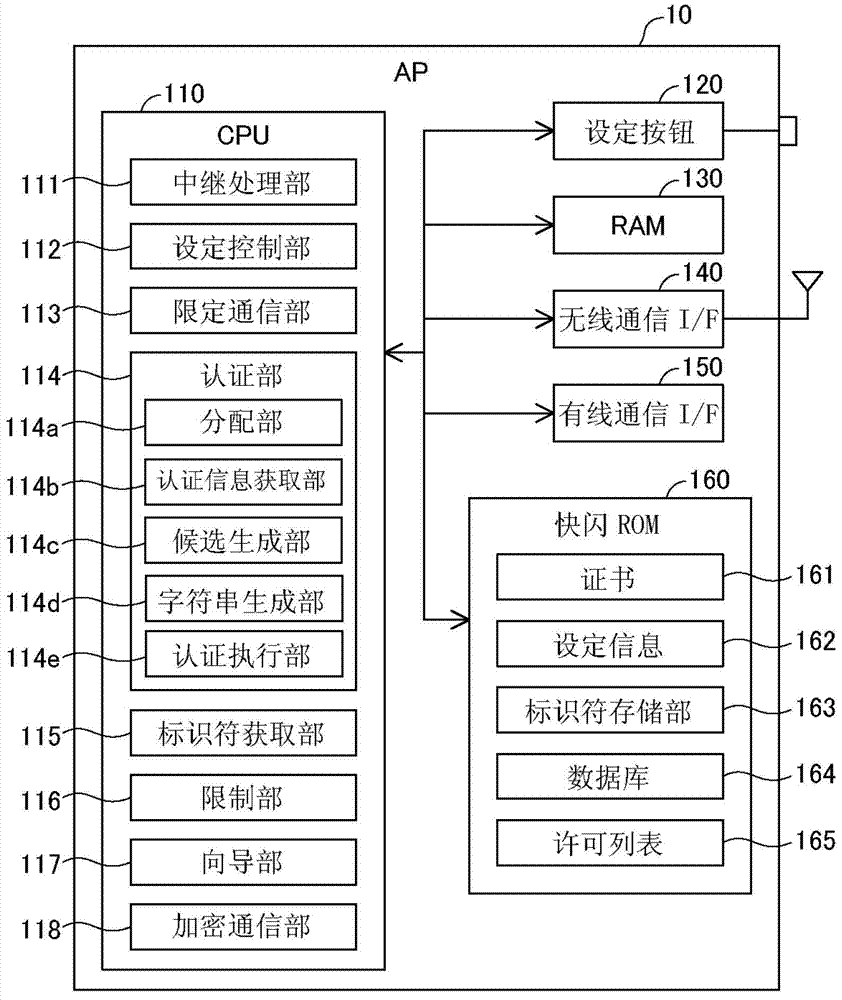
[0075] The wireless network relay device 10 in this embodiment is an access point device conforming to IEEE802.11. The wireless network relay device 10 is also referred to as "AP10" below. The AP 10 relays the wireless communications of the client devices 20 and 30 . In this embodiment, AP10 also functions as a router, and is connected to the Internet INT via a wired cable. AP10 supports conventionally known AOSS (AirStationOne-Touch Secure System: one-touch wireless network simple setup system) and WPS (Wi-Fi ProtectedSetup: W...
no. 1 example
[0154] As above, according to the first embodiment of the simple authentication process, the AP 10 (wireless connection device) causes the PC 20 (client device) to display that a plurality of groups are assigned in a correspondence list in a one-to-one correspondence with each of a plurality of characters. An image group composed of images. In the example of the above-mentioned embodiment, three sets of display are performed using the three image selection boxes C71, C72, and C73 of the authentication screen W7. Furthermore, the AP 10 acquires designation of one image and designation of order for each image group ( C71 , C72 , C73 ). That is, since the operation of specifying the images and specifying the order of the plurality of displayed image groups is only required on the PC 20 side, the input is simple. In addition, on the PC 20 side, images are designated one by one from a plurality of image groups, so that the degree of freedom of image designation can be increased, a...
no. 2 approach
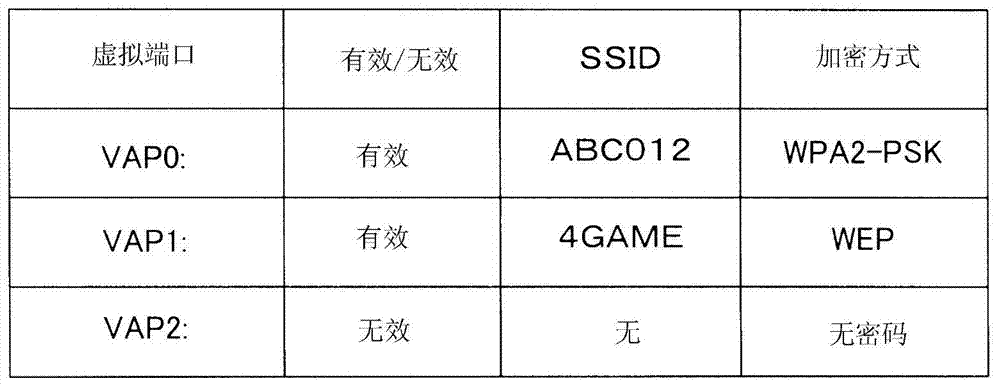
[0184] In the second embodiment of the present invention, a configuration in which filtering processing executed in wireless communication setting processing is different will be described. In addition, "filtering processing" here means that AP10 discards the source MAC address and in step S112 ( Figure 5 ) to process packets whose MAC addresses are inconsistent. Only parts having different configurations and operations from those of the first embodiment will be described below. In addition, in the drawings, the same reference numerals as those of the first embodiment described above are attached to the same structural parts as those of the first embodiment, and detailed description thereof will be omitted.
[0185] Figure 24 It is a sequence diagram showing the procedure of wireless communication setting processing in the second embodiment. In addition, in Figure 24 For the convenience of illustration, the illustration of step PH4 (acquisition of recommended files by t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com