Method and system for access controlling, and equipment
An access control and access technology, applied in the transmission system, electrical components, etc., can solve the problems of increasing terminal load, increasing the cost and workload of software maintenance and upgrading such as virus database and firewall, etc., so as to reduce load and save Cost and Effort Effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
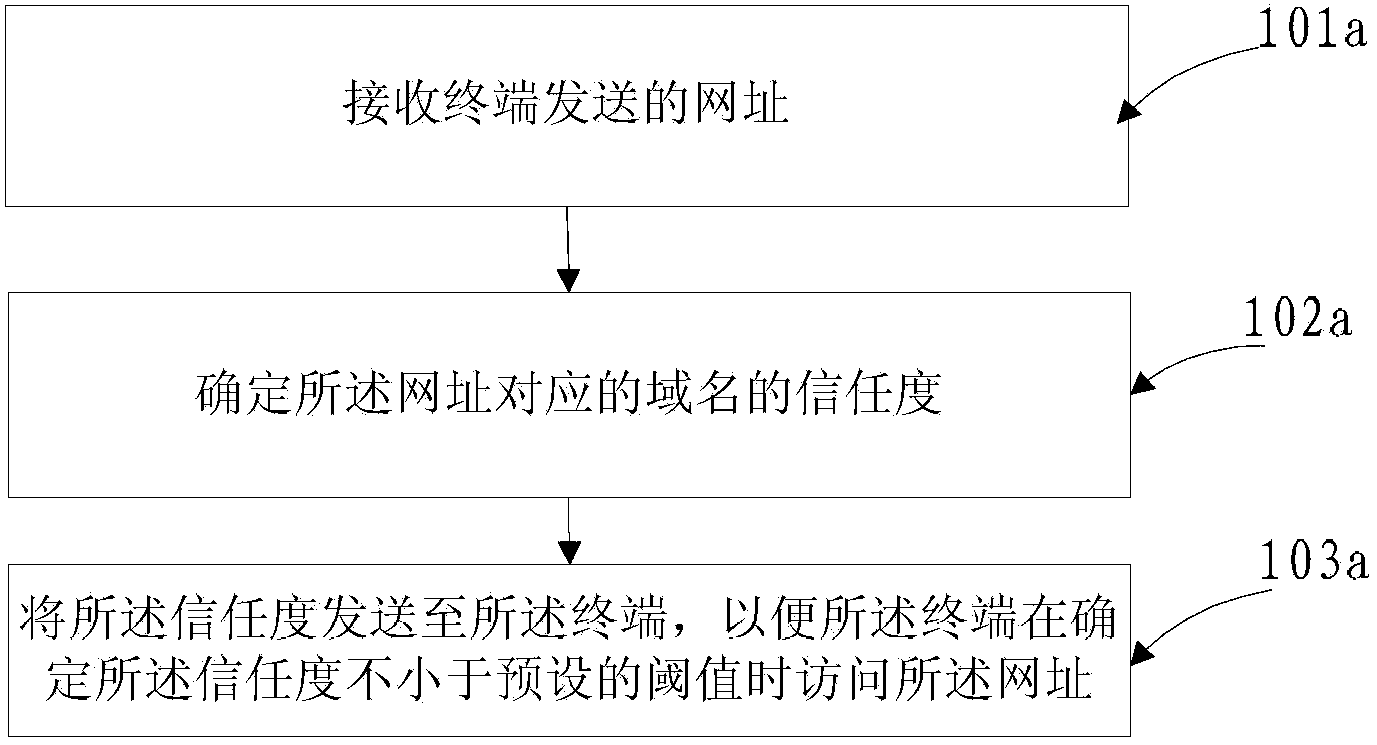
[0036] On the one hand, the embodiment of the present invention provides an access control method, see Figure 1a , the method includes:
[0037] Step 101a: receiving the URL sent by the terminal;
[0038] Step 102a: Determine the trust degree of the domain name corresponding to the website address, the trust degree is used to indicate the security degree of the domain name;
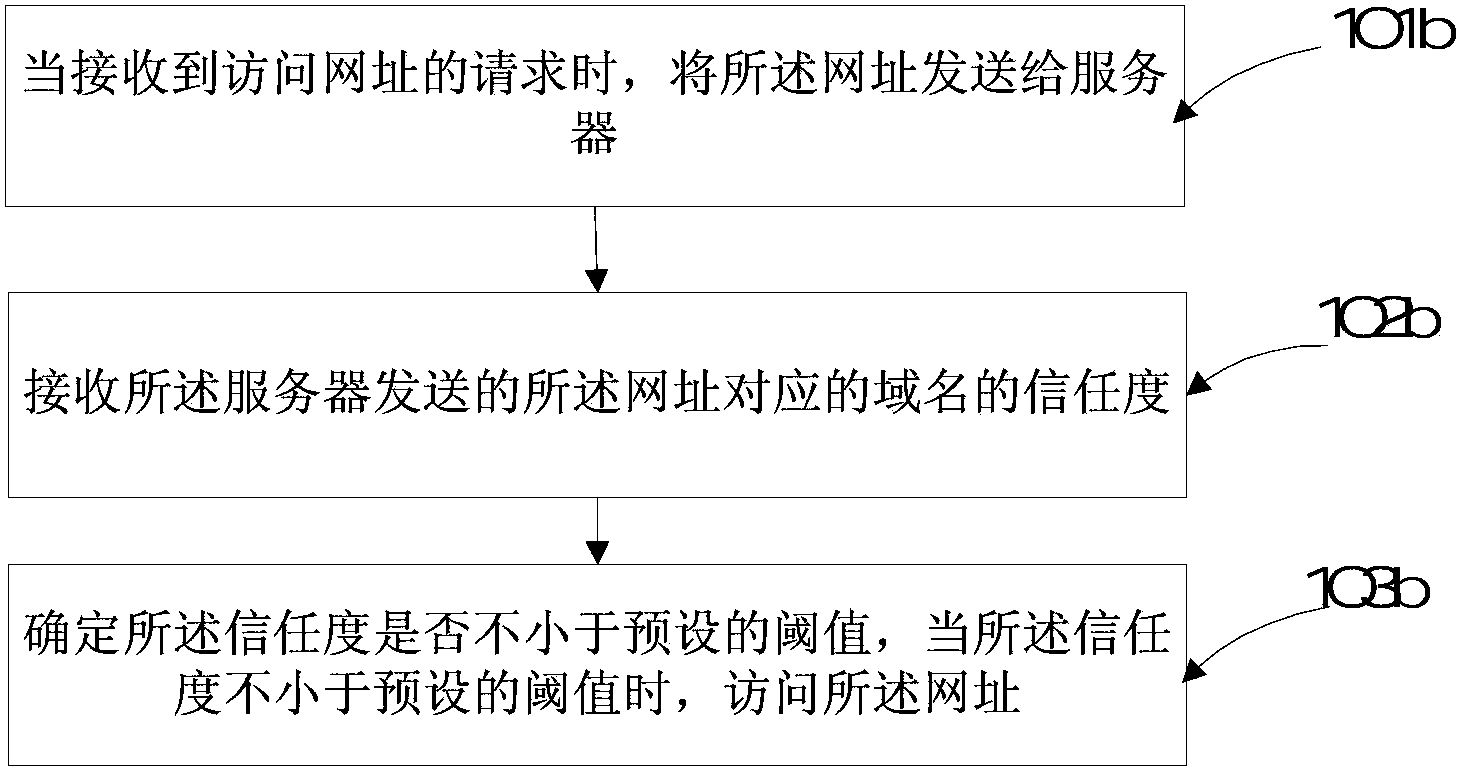
[0039] Step 103a: Send the trust degree to the terminal, so that the terminal accesses the website when determining that the trust degree is not less than a preset threshold.
[0040] The beneficial effects brought by the technical solution provided by the embodiment of the present invention are: receiving the website sent by the terminal; determining the trust degree of the domain name corresponding to the website, and sending the trust degree to the terminal, wherein the trust degree It is used to indicate the security level of the domain name; so that the terminal can access the website when it is de...
Embodiment 2
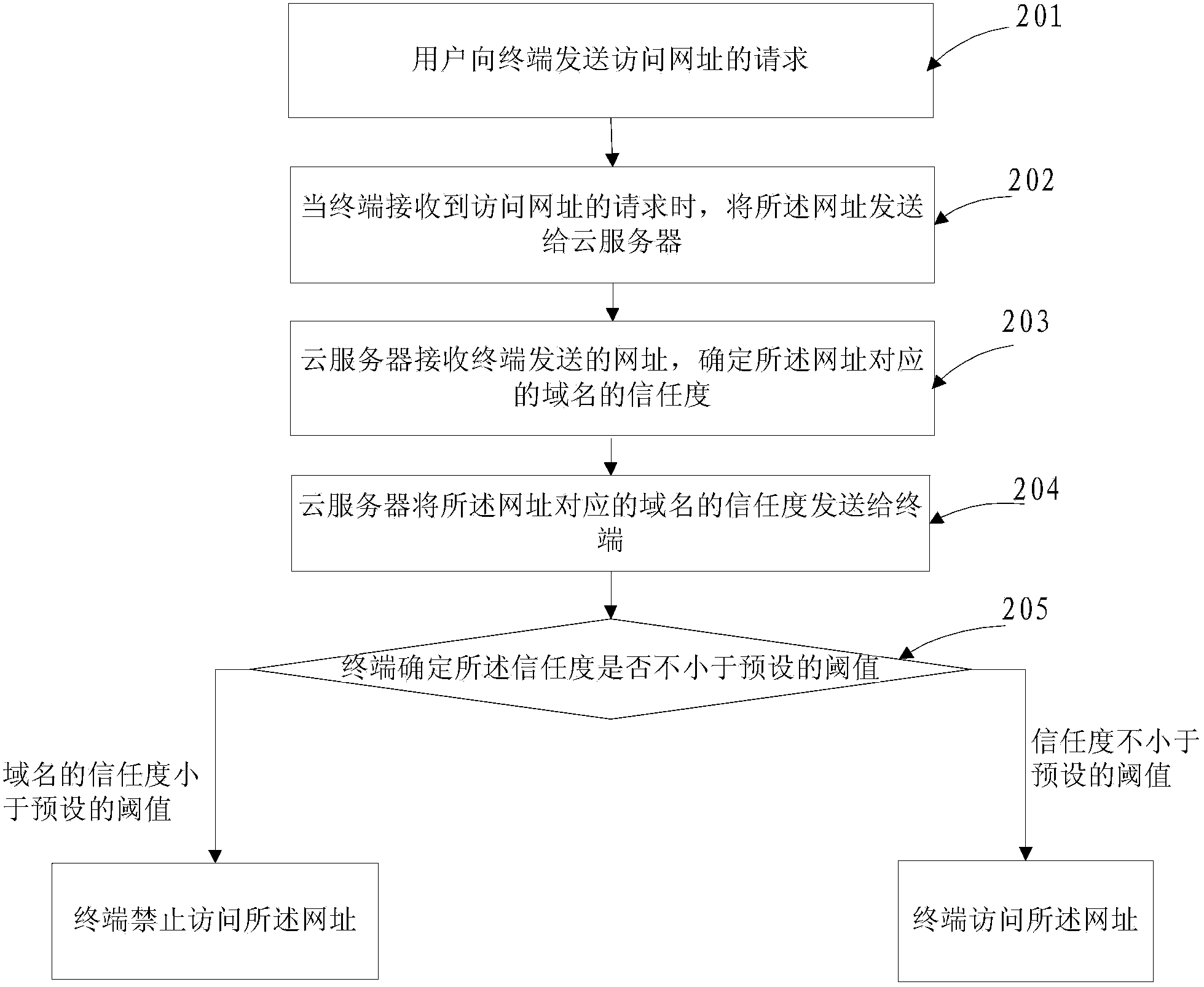
[0047] As a realizable embodiment, the embodiment of the present invention provides an access control method, see figure 2 , the method may specifically include the following operations:
[0048] Step 201: The user sends a request to the terminal to access a website. In the embodiment of the present invention, the website may be a download address or a web page address;
[0049] Specifically, the user can send a request to visit the website through the web browser installed on the terminal;
[0050] Step 202: When the terminal receives a request to access a website, send the website to the cloud server;
[0051] Step 203: The cloud server receives the website address sent by the terminal, and determines the trust degree of the domain name corresponding to the website address;
[0052] In the embodiment of the present invention, the trust degree of the domain name is used to indicate the security degree of the domain name, and the higher the trust degree of the domain name i...
Embodiment 3
[0127] see Figure 4 , the embodiment of the present invention provides a server, and the server may be specifically the same as the cloud server described in the second method embodiment, including: a receiving module 401, a first determining module 402, and a first sending module 403;
[0128] A receiving module 401, configured to receive the URL sent by the terminal;
[0129] The first determination module 402 is configured to determine the trust degree of the domain name corresponding to the website, and the trust degree is used to indicate the security degree of the domain name;
[0130] The first sending module 403 is configured to send the trust degree to the terminal, so that the terminal accesses the website when determining that the trust degree is not less than a preset threshold.
[0131] Wherein, the first determining module 402 is specifically configured to extract the trust information of the domain name corresponding to the website, and calculate the trust deg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com