A method for constructing a virtual reconstructed ubiquitous network architecture based on identity and location separation
A technology of virtual reconfiguration and system architecture, which is applied in the transmission system, data exchange through path configuration, electrical components, etc., can solve the problems of being unable to meet the diversified multimedia needs of ubiquitous network users, and reduce technical difficulty and cost , the effect of supporting mobility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
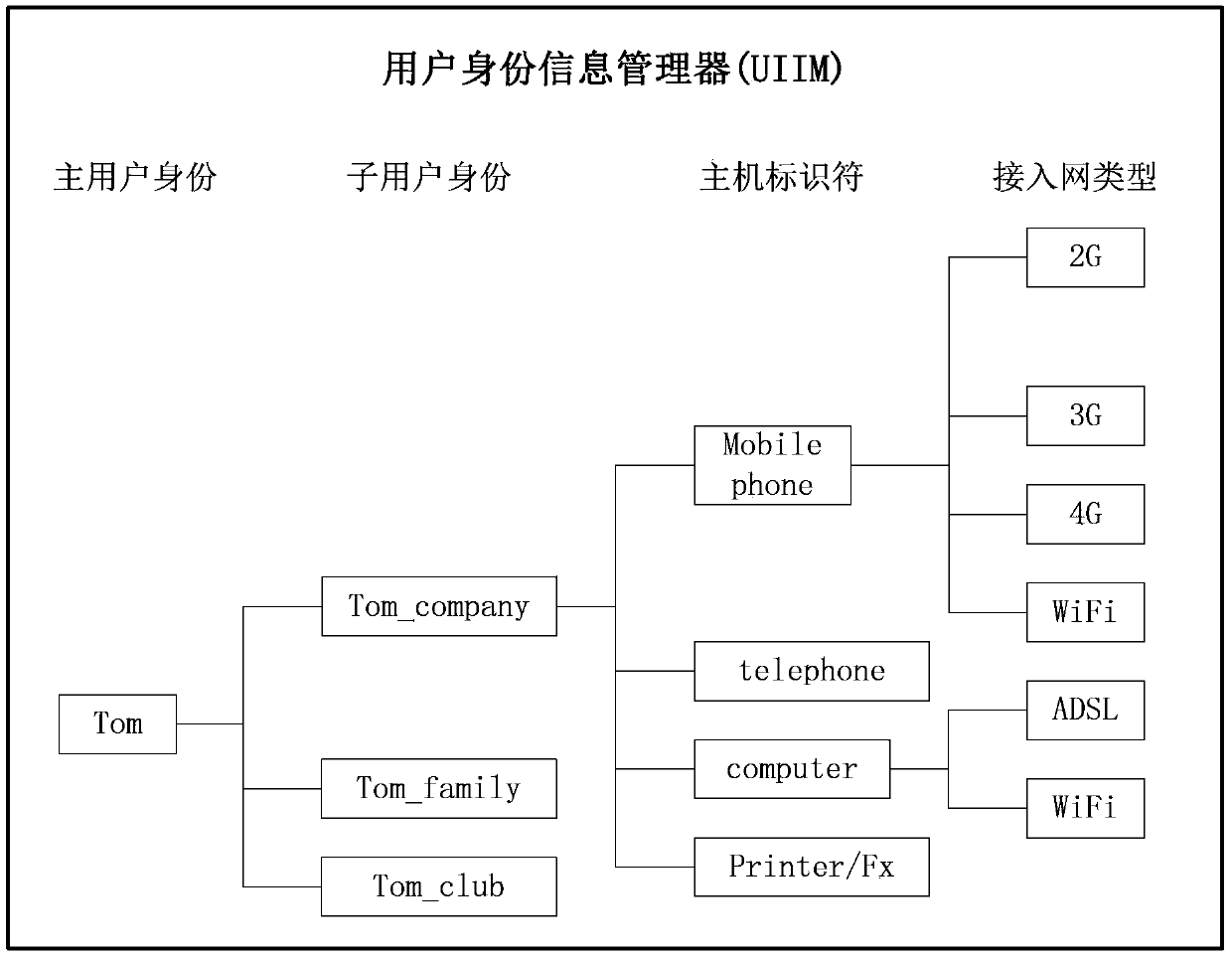
[0066] Figure 5 Shown is a schematic diagram of a ubiquitous network user registration process. Assuming that the ubiquitous network user has the main user identity Tom, at this time, he wishes to register as the sub-user identity Tom_company through the smart terminal held by him. The steps include:
[0067] 1) Tom starts up, opens all available interfaces, scans all available networks, selects a certain access network according to the internally configured network selection scheme, and chooses to register as a sub-user Tom_company, assuming that a 3G network is selected;
[0068] 2) To establish a PDP context, the 3G access network first authenticates the user. The authentication process is the same as the traditional mechanism and will not be repeated. The registration message contains the terminal host identifier, and the 3G access network edge router assigns an IP address to the authenticated terminal. address, establishing a mapping relationship between the terminal ho...
Embodiment 2
[0082] Image 6 Shown is a schematic diagram of the implementation of the identity and location separation mechanism. User A and user B communicate through terminal A and terminal B respectively, including the following steps:
[0083] 1) User A and user B register with terminal A and terminal B respectively, the process is as in one of the embodiments, and will not be repeated;
[0084] 2) The host of terminal A is identified as HID_A, currently connected to network A, and the edge router of access network A assigns a location identifier GLOCa to it; the host of terminal B is identified as HID_B, currently connected to network B, and is assigned by the edge router of access network B The router assigns the location identifier GLOCb to it;
[0085] 3) User A sends a data packet to user B, and the source and destination addresses in the data packet are host identifiers HID_A and HID_B of terminal A and terminal B respectively;
[0086] 4) After receiving the data packet, the ...
Embodiment 3
[0092] Figure 7 According to another embodiment of the present invention, it is a schematic diagram of user mobility support based on virtual reconstructed ubiquitous network architecture based on separation of identity and location. Ubiquitous network user Tom is a sub-user identity Tom_company and partner Bob during working hours. To communicate, the conversation process includes:
[0093] 1) Tom first registers on the smart terminal and office computer as the sub-user Tom_company, and the registration process will not be repeated;
[0094] 2) Tom configures the business of the sub-user identity Tom_company through the smart terminal, and sets video conversations and instant messages to be received by the computer. The smart terminal only receives short messages to facilitate information query when going out. At the same time, the office fixed line is established with the sub-user identity Tom_company Association, so that ordinary voice calls are received through the offic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com