Vulnerable main machine recognition method and device of power system
A power system and identification method technology, applied in circuit devices, transmission systems, digital transmission systems, etc., can solve problems such as low efficiency and identification of hidden danger hosts.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to further illustrate the technical means adopted by the present invention and the achieved effects, the technical solutions of the present invention will be clearly and completely described below in conjunction with the accompanying drawings and preferred embodiments.
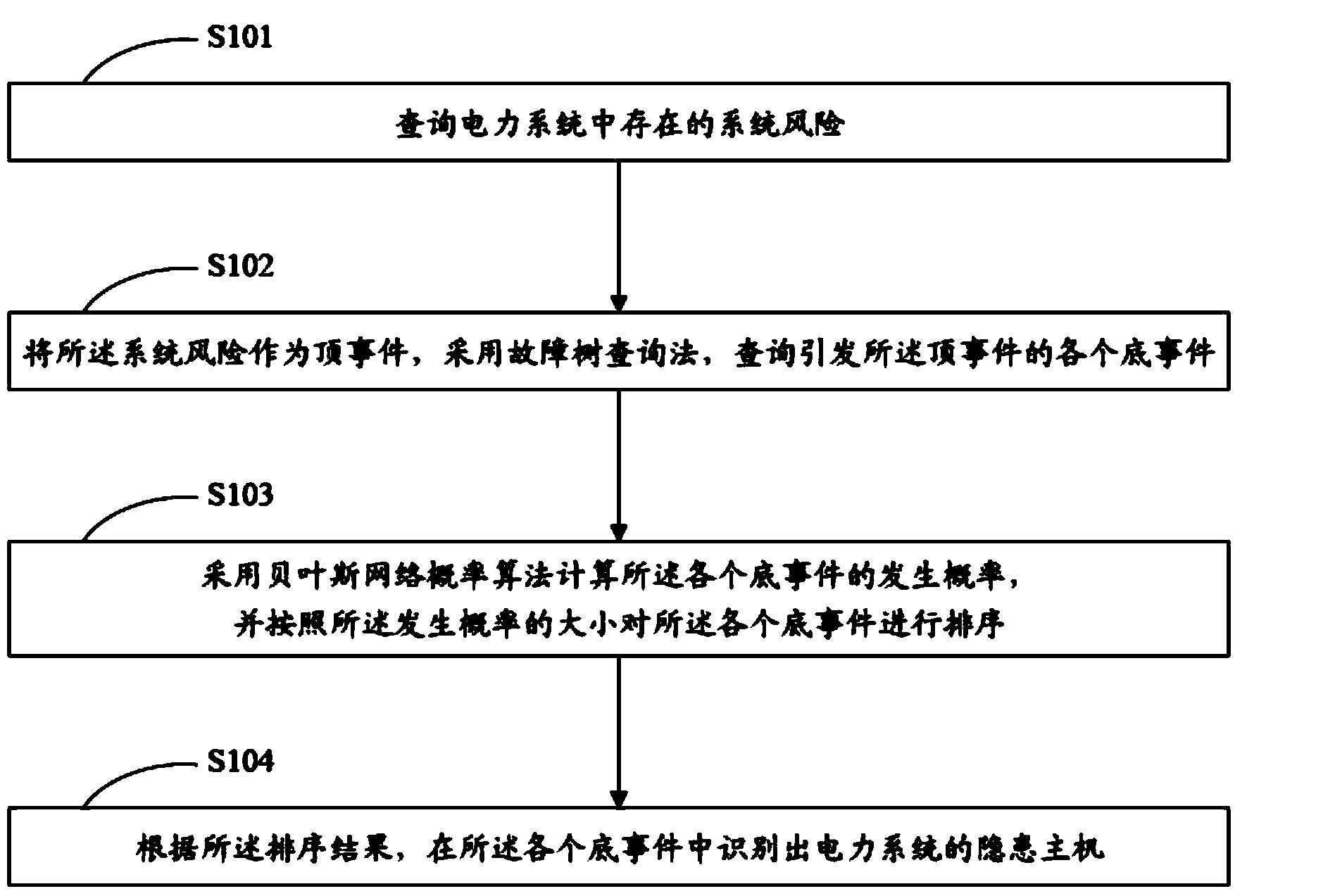
[0020] see figure 1 , is a schematic flowchart of a method for identifying a hidden host in a power system according to the present invention.
[0021] The method for identifying a hidden danger host in a power system of the present invention comprises the following steps:
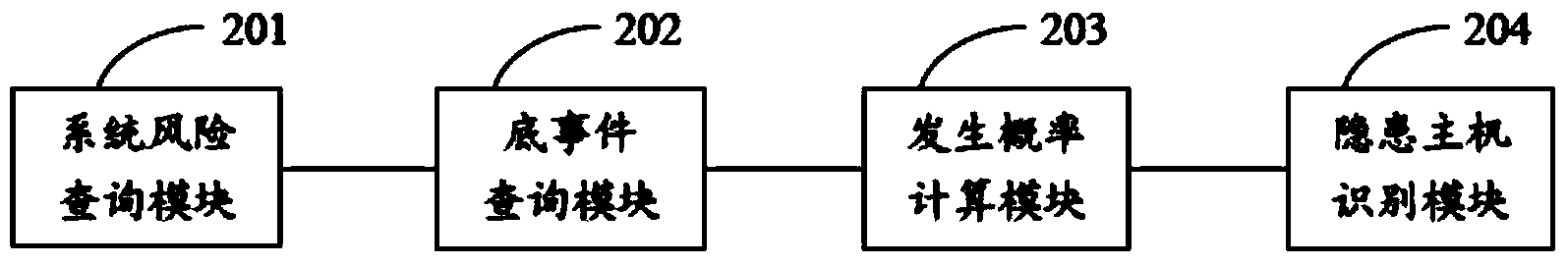
[0022] S101 Query system risks existing in the power system;
[0023] S102 takes the system risk as a top event, and uses a fault tree query method to query each bottom event that causes the top event;
[0024] S103 Calculate the occurrence probability of each bottom event by using the Bayesian network probability algorithm, and sort the bottom events according to the magnitude of the occurrence probability;
[0025] S10...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com