Method for protecting wireless network
A wireless network and wireless access technology, applied in network topology, wireless communication, security devices, etc., can solve problems such as security risks, leaking wireless access points, etc., to achieve the effect of protection, avoidance of leakage, and risk reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
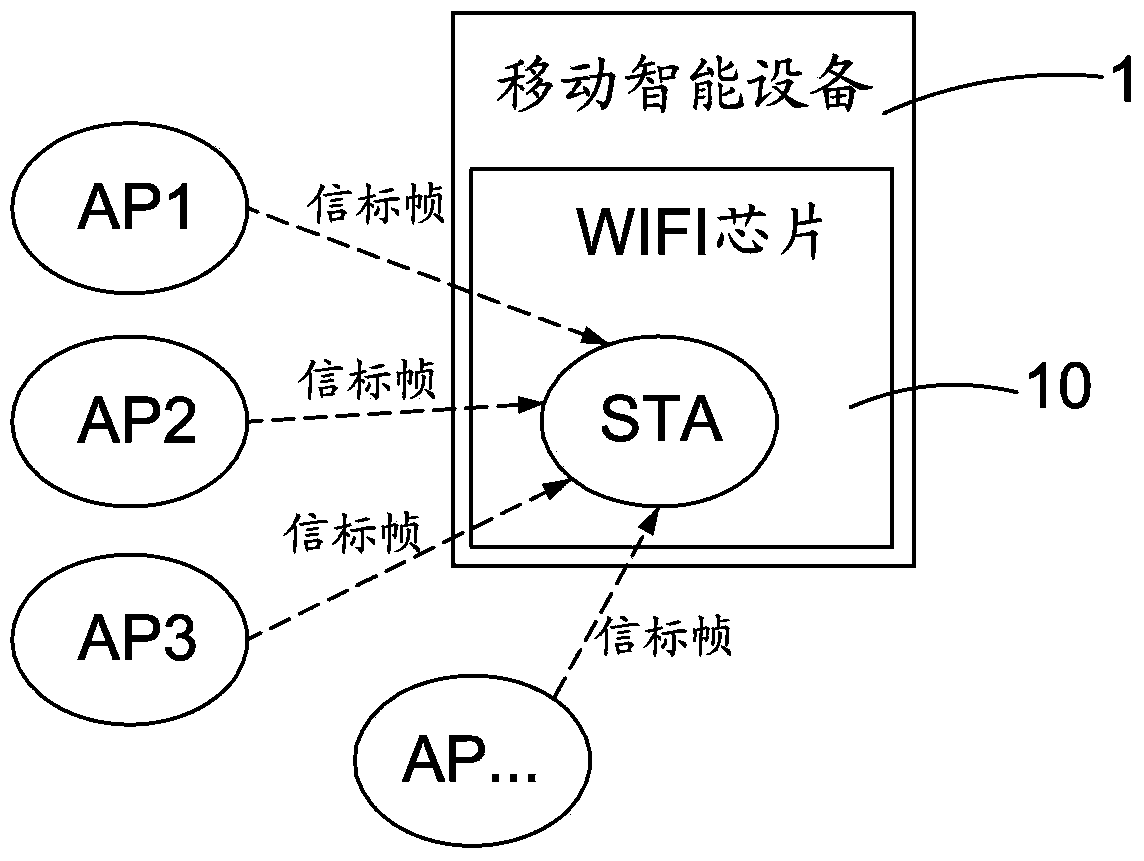
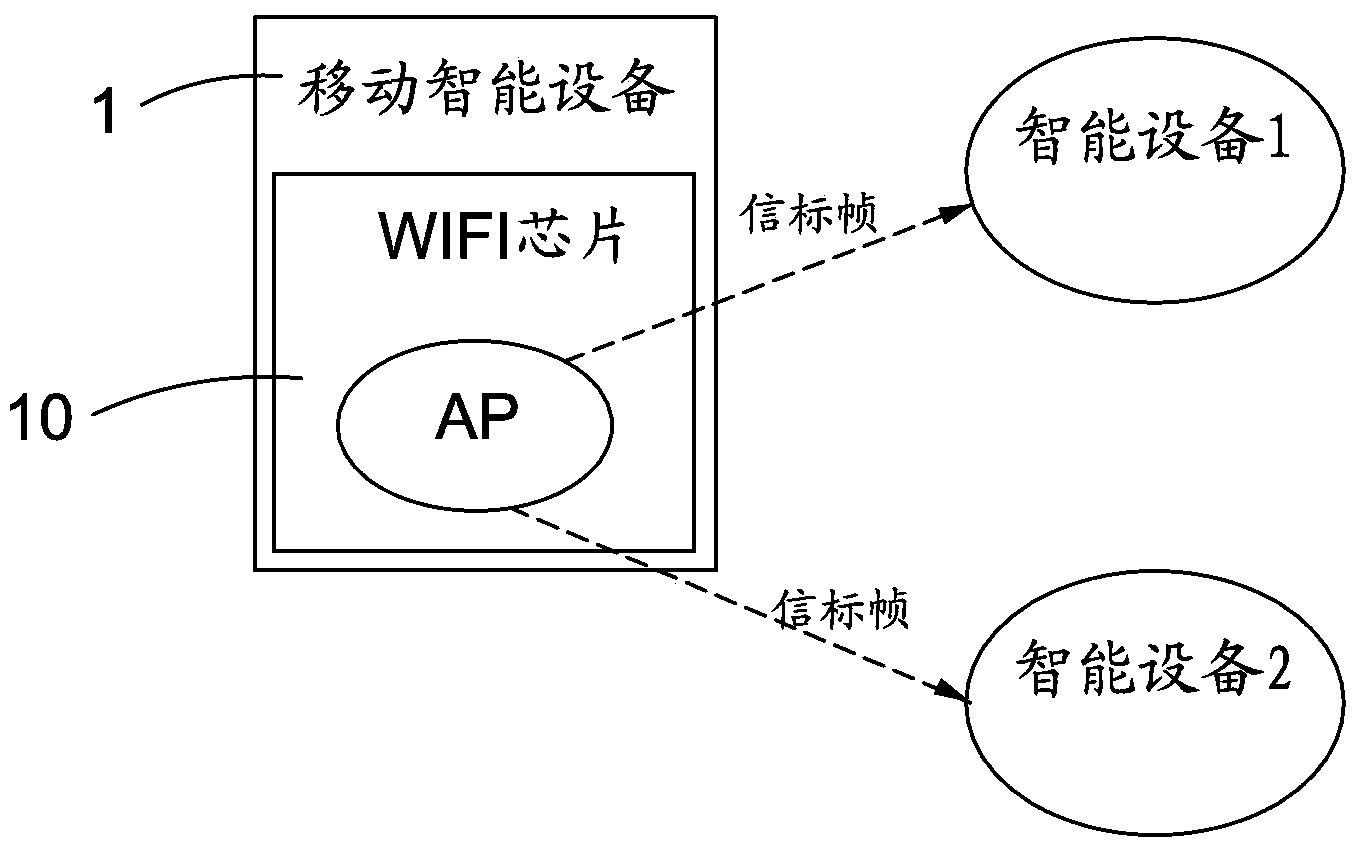
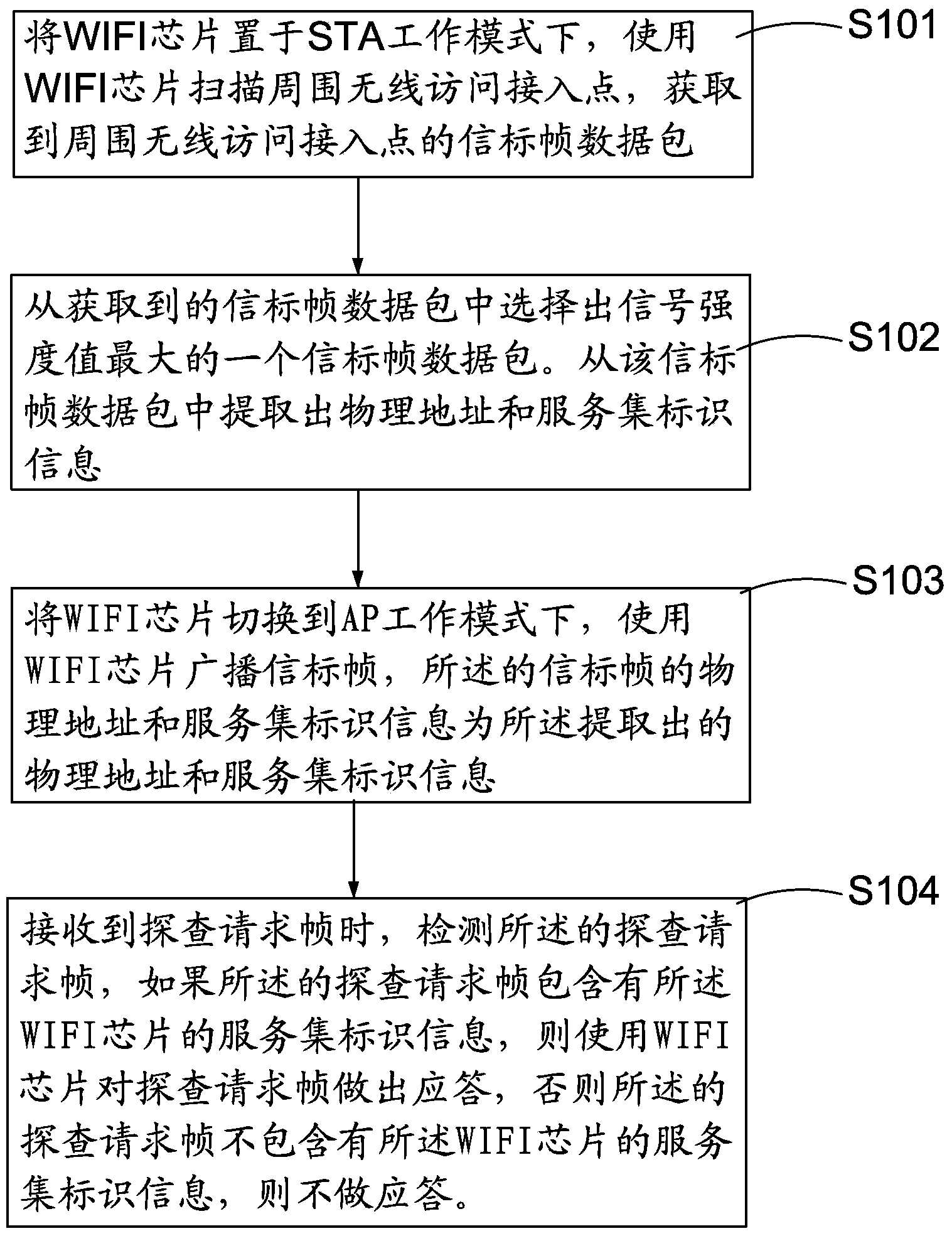
[0025] Such as Figure 1 to Figure 3 As shown, the preferred embodiments of the present invention will be described in detail next.
[0026] The working modes of the WIFI module include STA working mode and AP working mode. The STA in the STA working mode is the abbreviation of station. In the STA working mode, the WIFI module can scan and connect to the wireless access point to realize the Internet access function. The AP in the AP working mode is the abbreviation of Access point (wireless hotspot or wireless access point). In the AP working mode, the WIFI module can be used as a wireless access point to realize the routing function.
[0027] The method of the present invention can be implemented on devices such as routing devices with WIFI modules, computers or mobile smart devices. The preferred embodiment of the present invention uses a mobile smart device for detailed description. Now a mobile smart device is basically equipped with a mobile communication module and a W...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com