Method for detecting network data package
A network data packet and detection method technology, which is applied in the field of network data packet detection, to achieve the effect of reducing false alarm rate, improving speed, and ensuring rapid response
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The method of the present invention will be described in further detail below in conjunction with the accompanying drawings.
[0033] The network packet detection method of the present invention comprises the following specific steps:
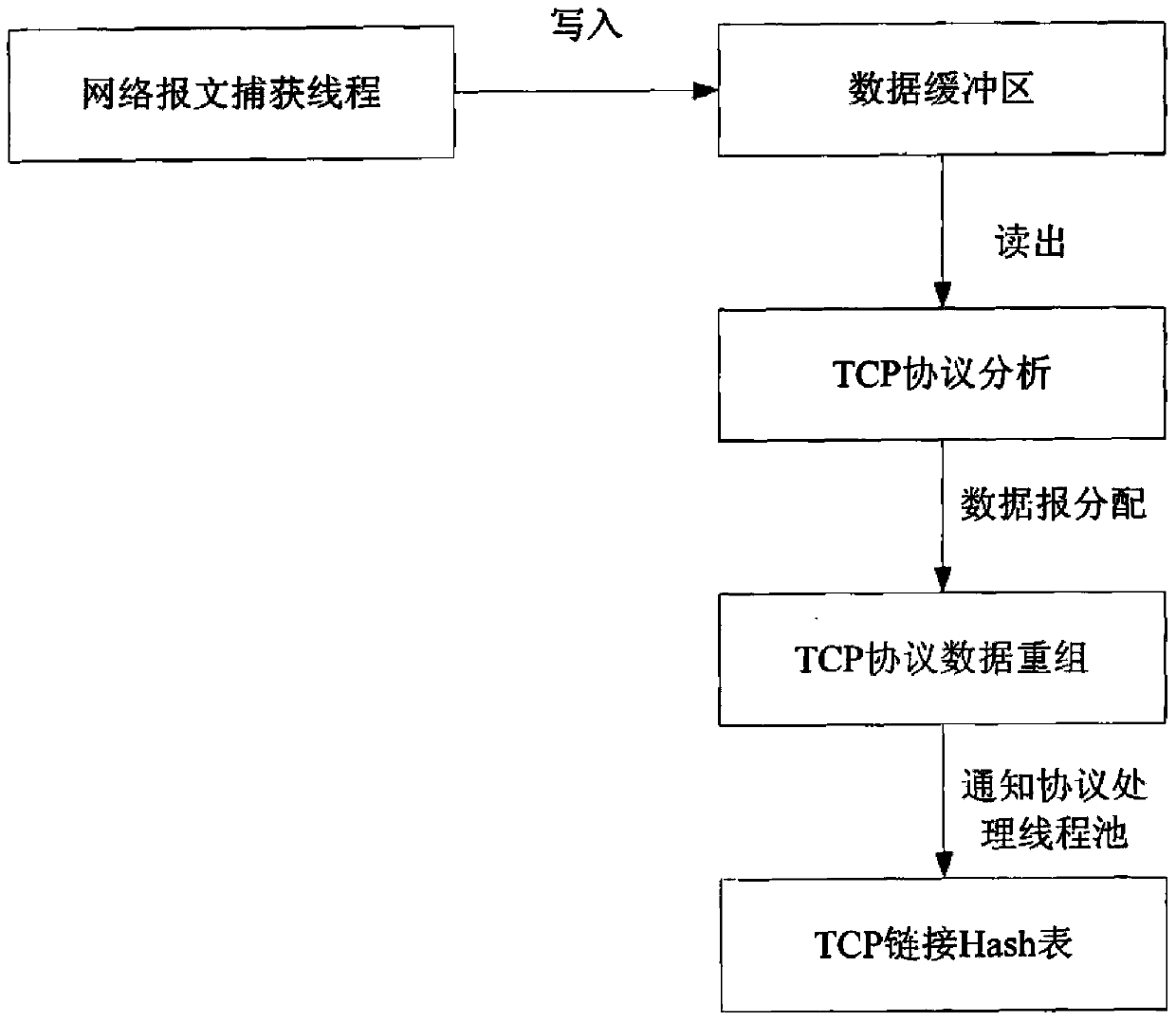
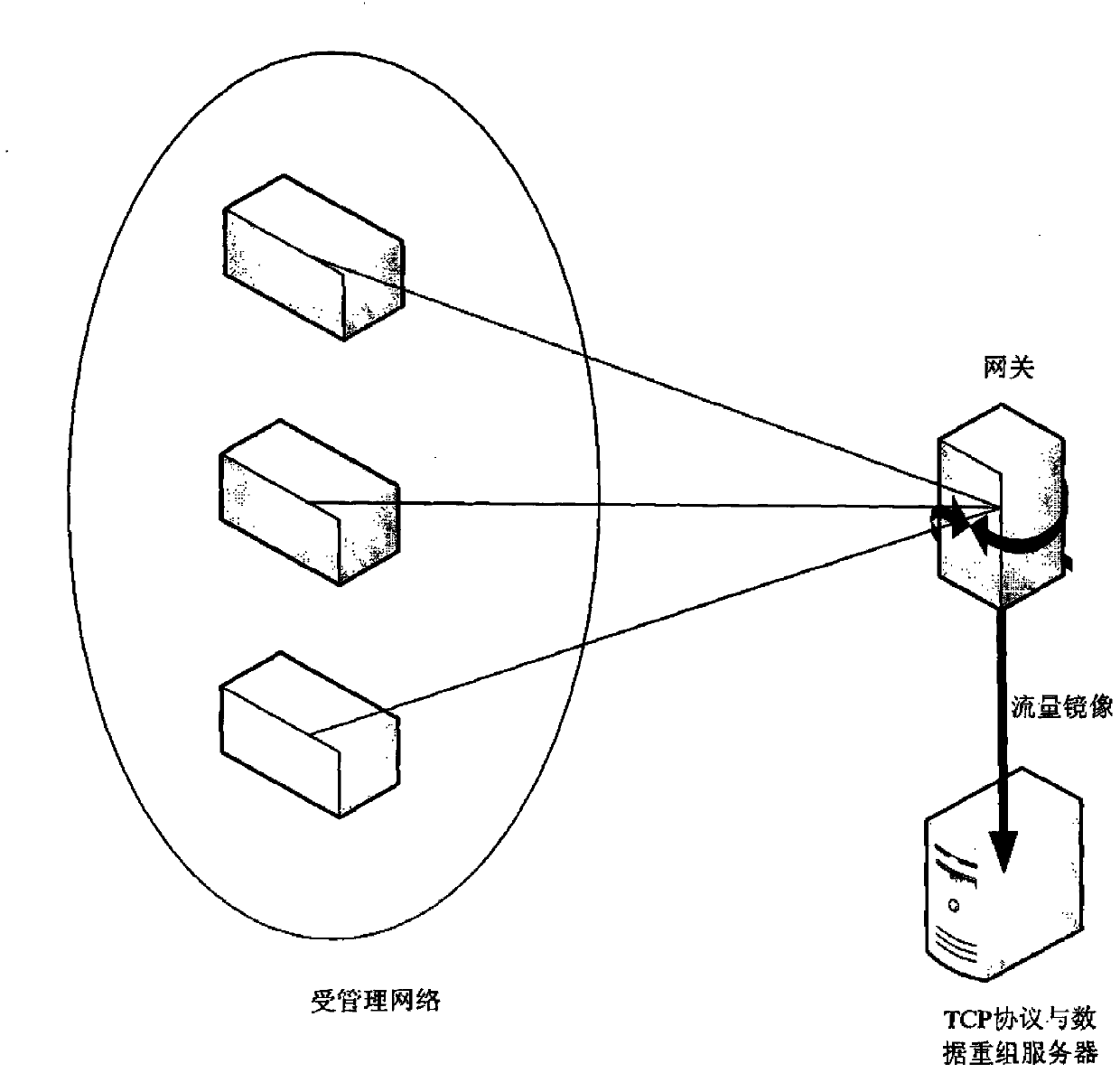
[0034] The first step is to capture the data packets in the network;
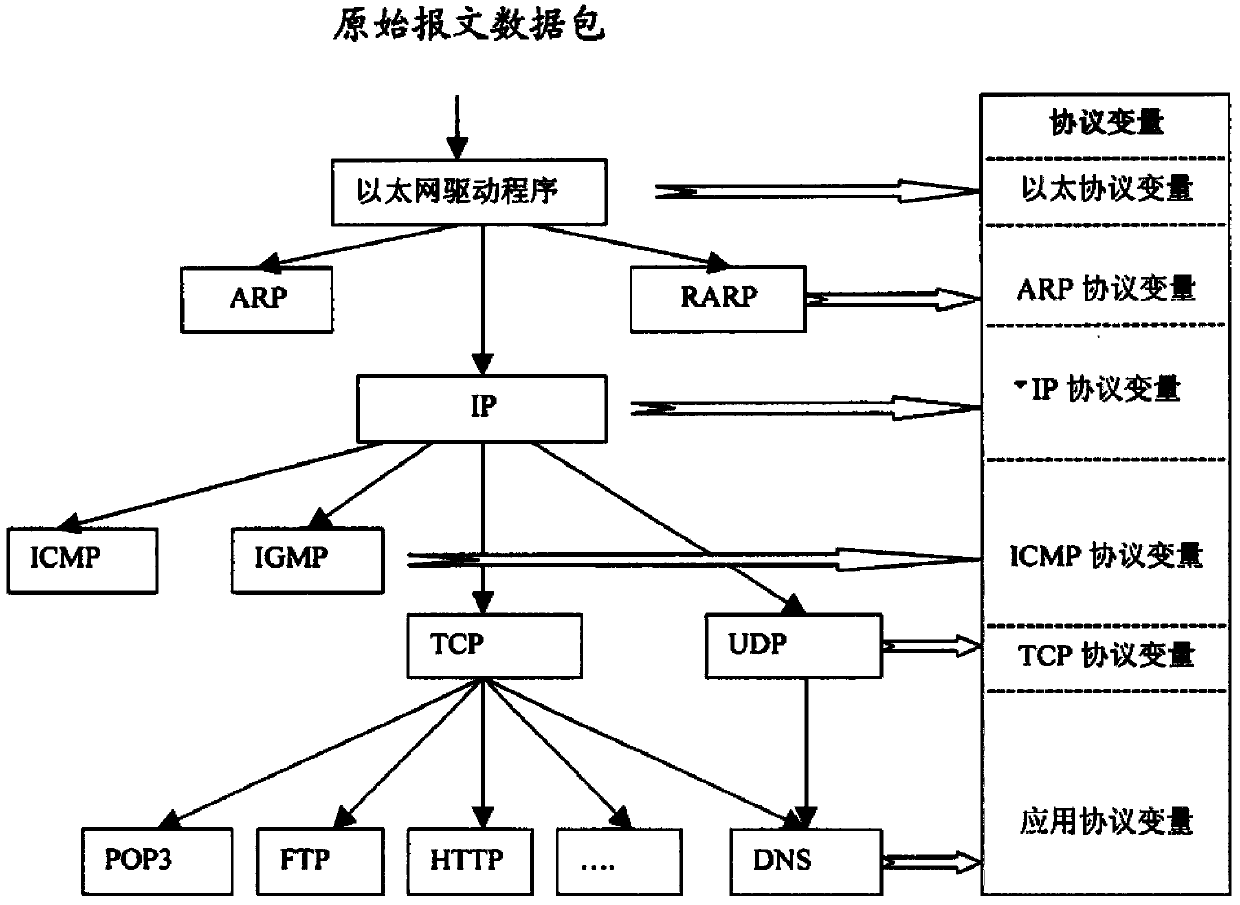
[0035] In the second step, the captured data packets are analyzed by the whole protocol stack to obtain the protocol variables, that is, the data of each protocol layer of the original message data packets;
[0036] The third step is to select the most suitable multi-pattern matching algorithm according to the preset pattern characteristics and protocol variable characteristics, then load the pattern matching algorithm library, and dynamically adjust the matching algorithm according to the current network status during the detection process.
[0037] The specific implementation method of the second step is as follows:
[0038] Full protocol stack analysis refers to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com