Method for updating and using secret key in power grid SSL VPN
A medium-key, power grid technology, applied in the field of quantum cryptography and communication, can solve problems such as stealing, and achieve the effect of enhancing security and saving costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
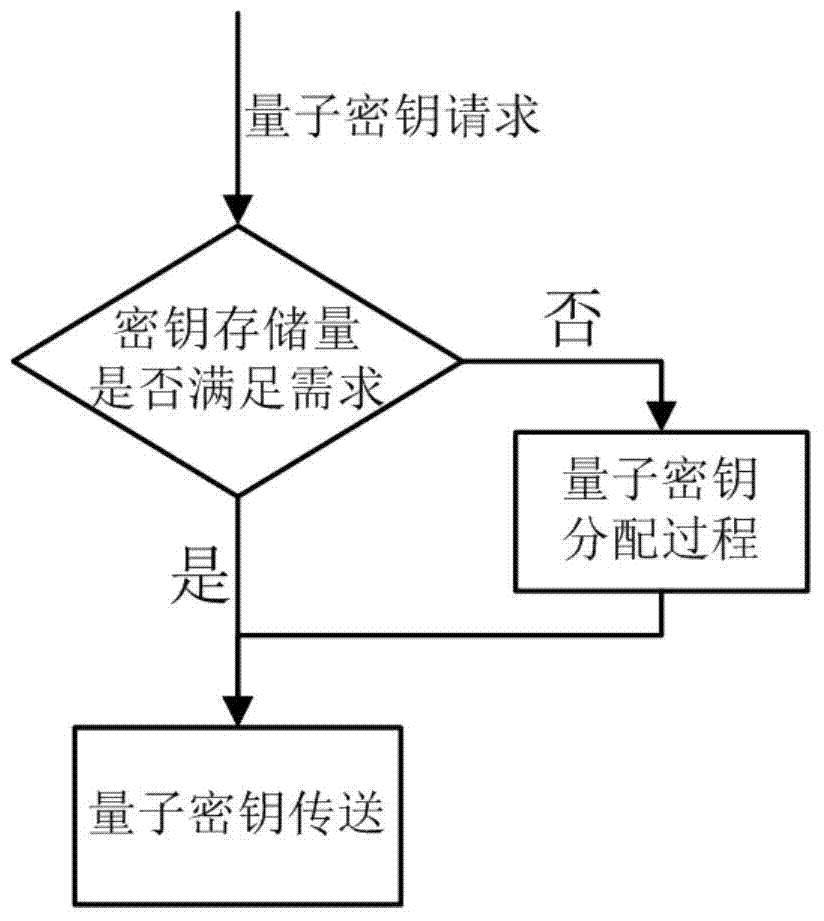
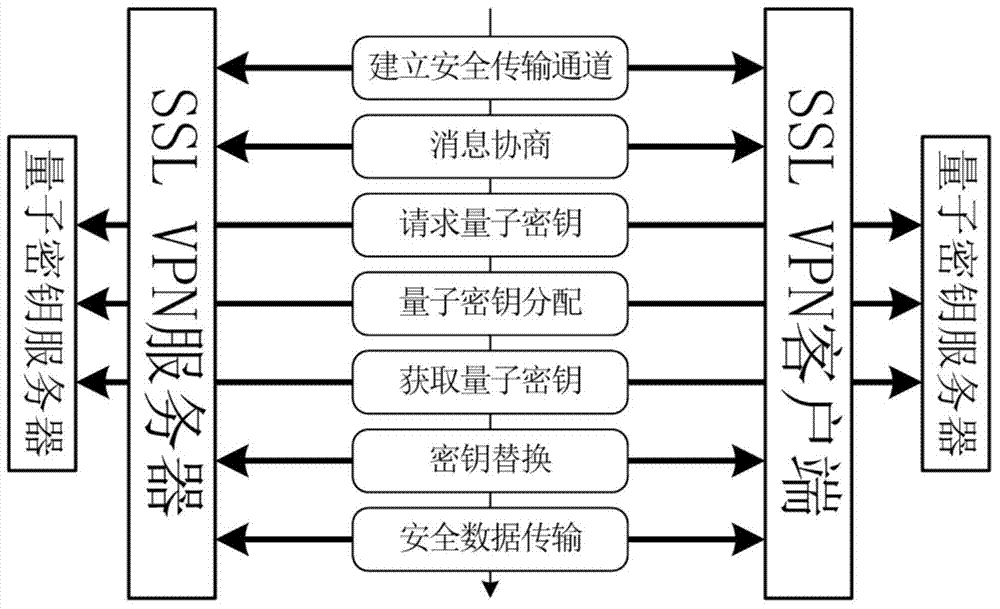
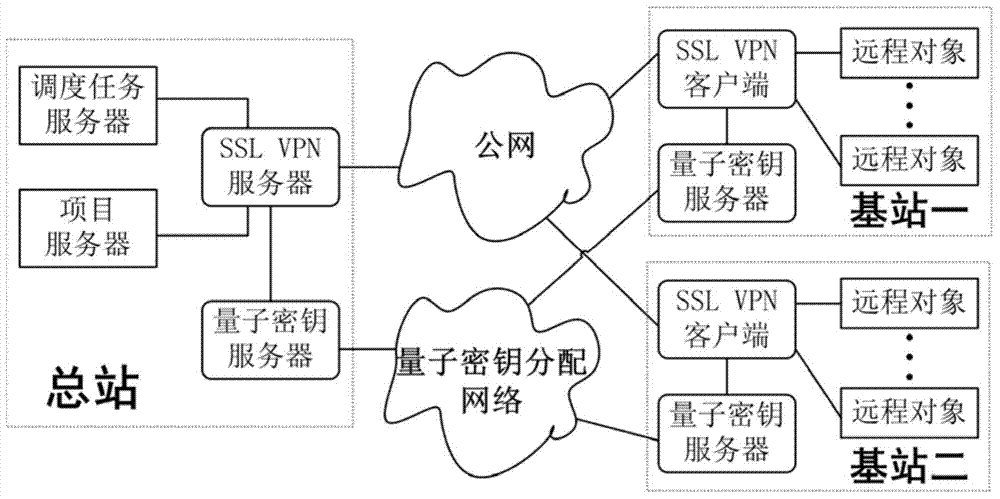
[0036] In the present invention, the existing SSL VPN protocol is directly used to first establish a secure transmission channel, and then negotiate relevant parameters about the use of the quantum key. Refer to attached figure 2 , the SSL VPN client and server first establish an SSL connection, and then the two parties perform a handshake negotiation. This negotiation includes encryption algorithm selection, quantum key usage form, quantum key survival time and so on. The specific protocol steps of the method of use are as follows:
[0037] (1) The communication parties use the traditional SSL VPN protocol to establish a virtual tunnel. In this step, the original SSL protocol does not need to be modified, and the auth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com