Service node configuration method and service node pool logger and system
A technology of service node and configuration method, applied in the field of communication, can solve problems such as overload, heavier burden, and easy failure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
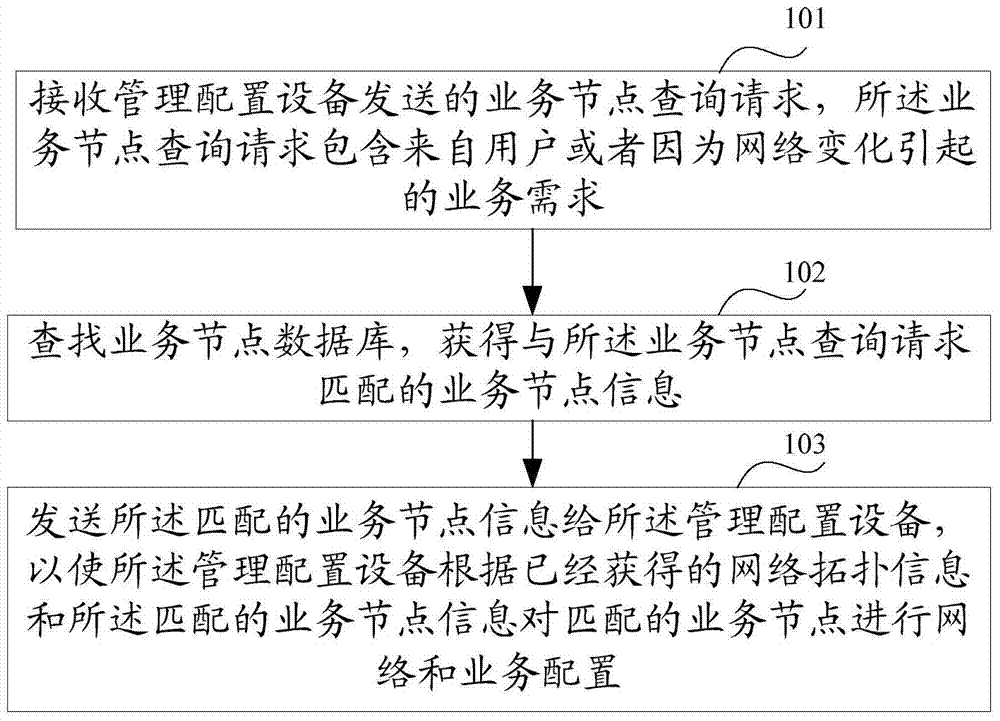
[0101] Combine below figure 2 Illustrate preferred embodiment one of the present invention, the processing procedure of business node registration is as follows:
[0102] The service nodes in the embodiment of the present invention are all service nodes (such as vFW, vLB) that have been successfully created, and their related function templates are issued by the management configuration device, as in step 1a in the figure, the firewall service template is issued and assigned to tenant A, and the notification The next hop of Service Node1 is Service Node2, 1b delivers the LB business template and assigns it to tenant A, and 1c delivers the WoC business template without specifying a tenant;
[0103] The service node configures corresponding functions, as in step 2a in the figure, the service node configures the firewall service, 2b the service node configures the LB service, and 2c the service node configures the WoC service;
[0104] After the service node is successfully cre...
Embodiment 2
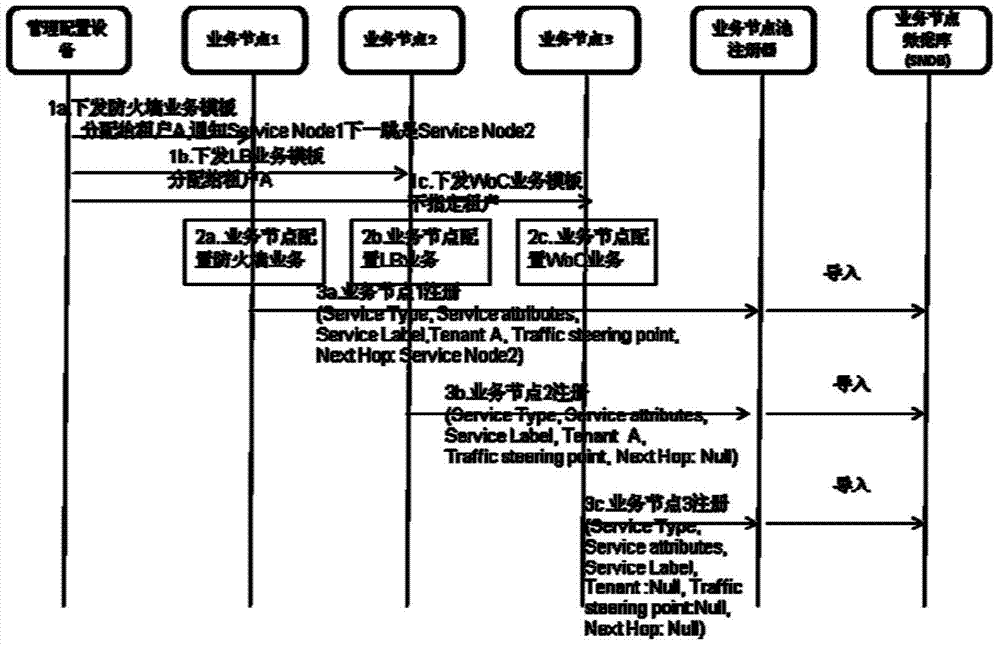
[0105] Combine below image 3 Describe the second preferred embodiment of the present invention. After the firewall service node executes the first packet to pass, the logout process is as follows:
[0106] The function of passing the first packet supported by the firewall mainly refers to: after the first packet passes, it confirms that the packet of this type of forwarding information meets the requirements, so as to directly issue the forwarding entry to the forwarding device, so that subsequent packets with the same forwarding attribute can pass directly, without It needs to be processed by the firewall again, so as to improve the processing efficiency;
[0107] Business node deregistration needs to send a deregistration message to the service node pool register, and at the same time, it needs to attach the identification information of the business node it jumps up and down, so as to update the relevant content in the service node database;
[0108] Finally, the manageme...
Embodiment 3
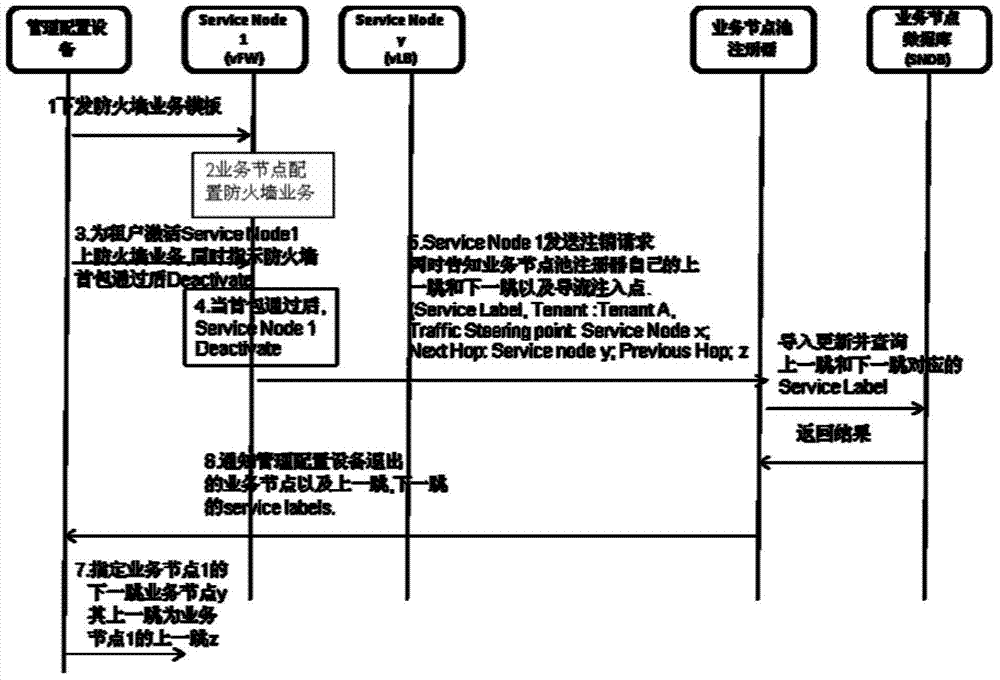
[0119] Combine below Figure 4 Illustrate the preferred embodiment three of the present invention, the processing flow of the heavy part of the service node is as follows:
[0120] For the relocation of service nodes, the most important thing is to query the qualified source service nodes and destination service nodes in the service node database of the service node pool register according to the restrictions of relocation;
[0121] If two corresponding service nodes can be found, the following operations are the deregistration and release of the source service node, the creation and update of the destination service node, and the update of the service node chain.
[0122] The specific steps are:
[0123] 1. Management and configuration equipment submits restrictions on relocation of service nodes (source and destination nodes of service relocation, functional specifications, relocation policies, etc.);
[0124] 2. The service node pool register queries the qualified sourc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com