Encryption method and encryption system based on ARM TrustZone
An encryption method and encryption and decryption technology, which are applied in the field of encryption methods and encryption systems based on ARM TrustZone, can solve problems such as hidden dangers, slow encryption and decryption speed, and restrict the efficiency of encryption systems, and achieve the effect of improving efficiency and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
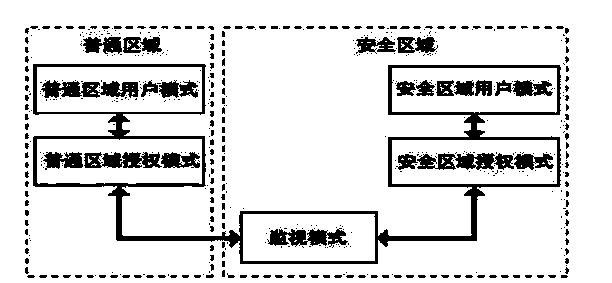
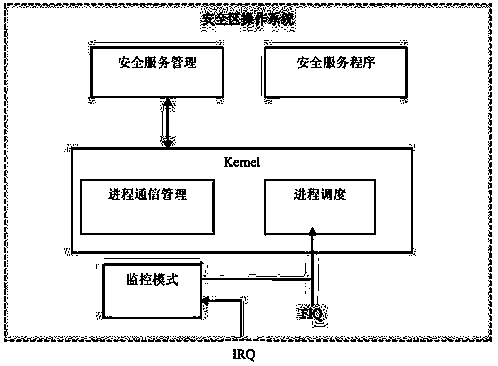
[0049] This embodiment proposes an encryption method based on ARM TrustZone, which stores the key of the mobile device in a security area invisible to the user and performs encryption, decryption and authentication operations in this security area, and this encryption and decryption operation and this block The security of the security area is ensured by both ARM bus encryption and interrupt protection. This security encryption technology utilizes the existing characteristics of the CPU of the ARM TrustZone architecture, so it is a security encryption technology combining software and hardware.
[0050] see figure 1 As shown, the solution provided by this embodiment first provides a security framework, so that the device can defend against many specific threats that will be encountered. And it also supports building a programmable environment to prevent mobile device hardware from being cracked and content copyright from being attacked. Using the TrustZone architecture ARM pl...
Embodiment 2
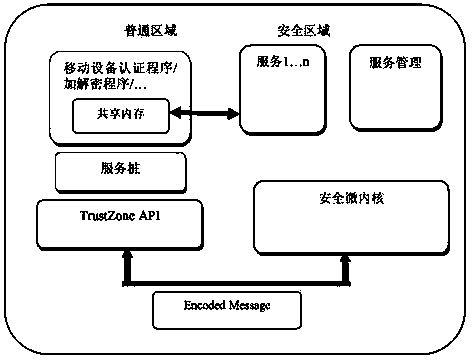
[0077] This embodiment provides an encryption system based on ARM TrustZone, see Figure 5 As shown, the system is used for a mobile device, and the mobile device has an ARM processor, and the system includes:
[0078] The security microkernel module 501 is used to divide the security area memory into multiple task memory spaces, and supports multiple independent security applications to run simultaneously without mutual detection and trustworthiness;
[0079] A secure boot module 502, configured to perform secure boot, so that the mobile device runs in a safe zone when the system kernel is started;
[0080] The communication module 503 is configured to call the secure microkernel module through the TrustZone API to complete the encryption and decryption when the upper layer application needs encryption and decryption.
[0081] Preferably, the communication module 503 may specifically include:
[0082] The driver layer calls the submodule, which is used to call the mobile de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com