Identity authentication method based on mouse behaviors of user
A technology of identity authentication and behavior, which is applied in the field of identity authentication based on user mouse behavior, and can solve the problems of inapplicable authentication technology, high hardware cost, complicated process, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] An embodiment of the present invention will be further described below in conjunction with the accompanying drawings.
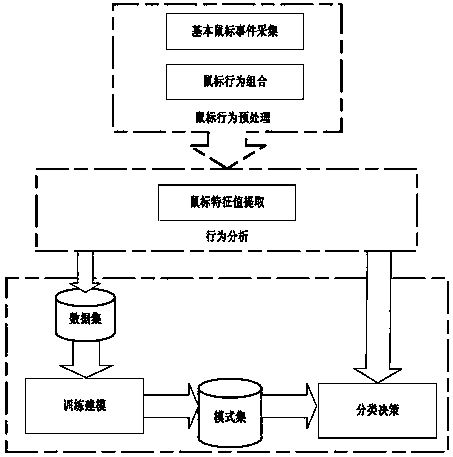
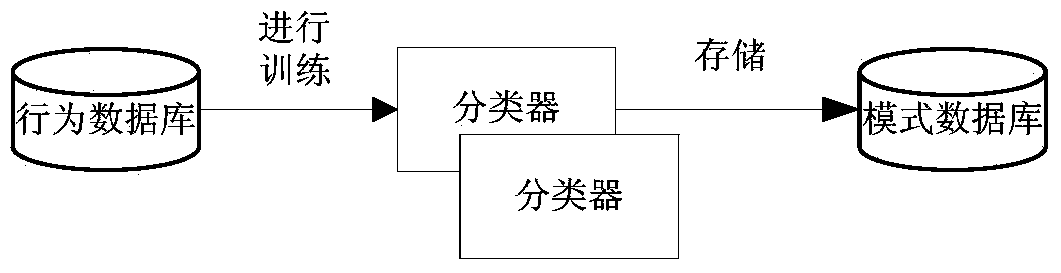
[0071] Identity authentication based on mouse behavior is a kind of biometric authentication, which conforms to the general process of biometric authentication, such as figure 1 As shown, the identity authentication scheme based on mouse behavior mainly includes four processes, mouse behavior preprocessing, mouse behavior feature value extraction, classification model construction, and classification decision-making.
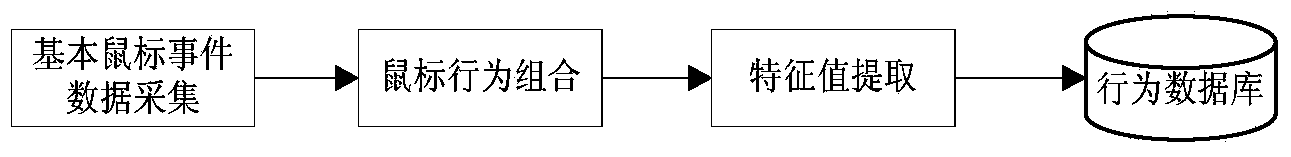
[0072] (1) The mouse behavior preprocessing process includes the collection of basic mouse events and the combination of mouse behavior. In order to effectively describe the mouse behavior, this work divides the mouse behavior into layers. The low-level mouse behavior is composed of the directly available basic mouse events, and the high-level mouse behavior is composed of low-level mouse behaviors according to certain rules.
[0073] (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com