Multi-image encryption method based on fractional mellin transform
A technology of Merlin transformation and encryption method, which is applied in the field of information security, can solve the problems of weak resistance to attack and inability to effectively resist chosen plaintext attacks, and achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0041] Embodiment 1: Spectrum cutting and splicing are performed on multiple images.
[0042] The specific process of spectrum cutting and splicing described in the present invention is as follows:
[0043] Step 1: Perform Zigzag scanning on n two-dimensional matrices respectively to form n one-dimensional matrices, which is beneficial to spectrum cutting.
[0044] Step 2: Cut the front elements in the n one-dimensional matrices respectively, because the front elements in the one-dimensional matrix represent the DC component and the low frequency part of the image. The cutting factor is generally set to M×N / n.
[0045] Step 3: Stitch all the cut elements together to form a one-dimensional matrix containing M×N elements, and convert it into a two-dimensional matrix with a size of M×N by row (or column), so as to realize multiple Image Compression.
[0046]When there are 8 images to be encrypted, 12.5% of the DC components and low-frequency coefficients in the discrete cosi...
Embodiment 2
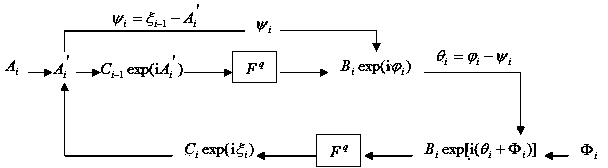
[0047] Embodiment 2: Image encryption based on multi-order fractional Merlin transform.
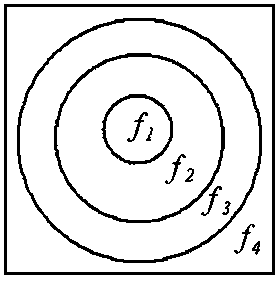
[0048] Perform different orders of fractional Merlin transform on different regions of the image f(x,y). Since the fractional Merlin transform is convenient for ring processing, the sub-image f i (x, y), i=1, 2, . . . , N are annular regions with different inner radii and outer radii. Taking N=4 as an example, decompose f(x,y) into 4 ring domains. Such as figure 2 As shown, these rings are all centered on the center of the picture, where f 1 (x,y) is the radius r 1 circle, f 2 (x,y) is the inner radius r 1 The outer radius is r 2 ring domain, f 3 (x,y) is the inner radius r 2 The outer radius is r 3 ring domain, f 4 (x,y) is the inner radius r 3 The outer radius is r 4 ring domain, where r 4 It is the distance from the center of the image to the top corner of the image. to f i carry on p i Order fractional Merlin transform to get g i , where i=1,2,...,N.
[0049] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com