A method and a system for processing mixed secret keys with an asymmetric cryptographic algorithm
An asymmetric encryption and mixed key technology, applied in the field of mixed key processing, to achieve the effect of ensuring information security and satisfying security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
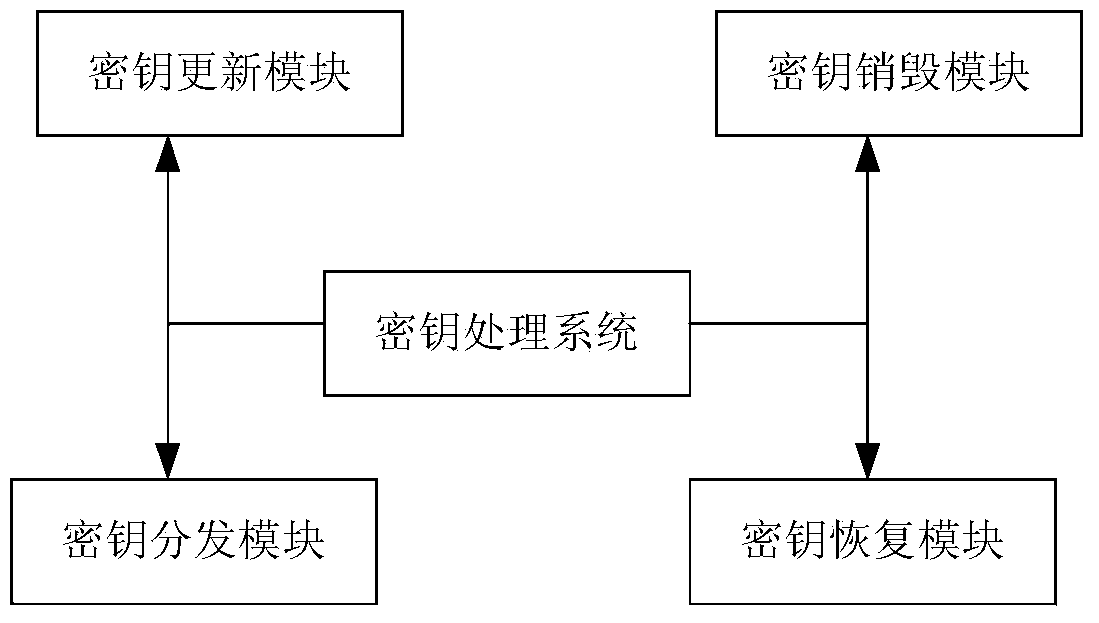
Method used
Image
Examples
Embodiment Construction
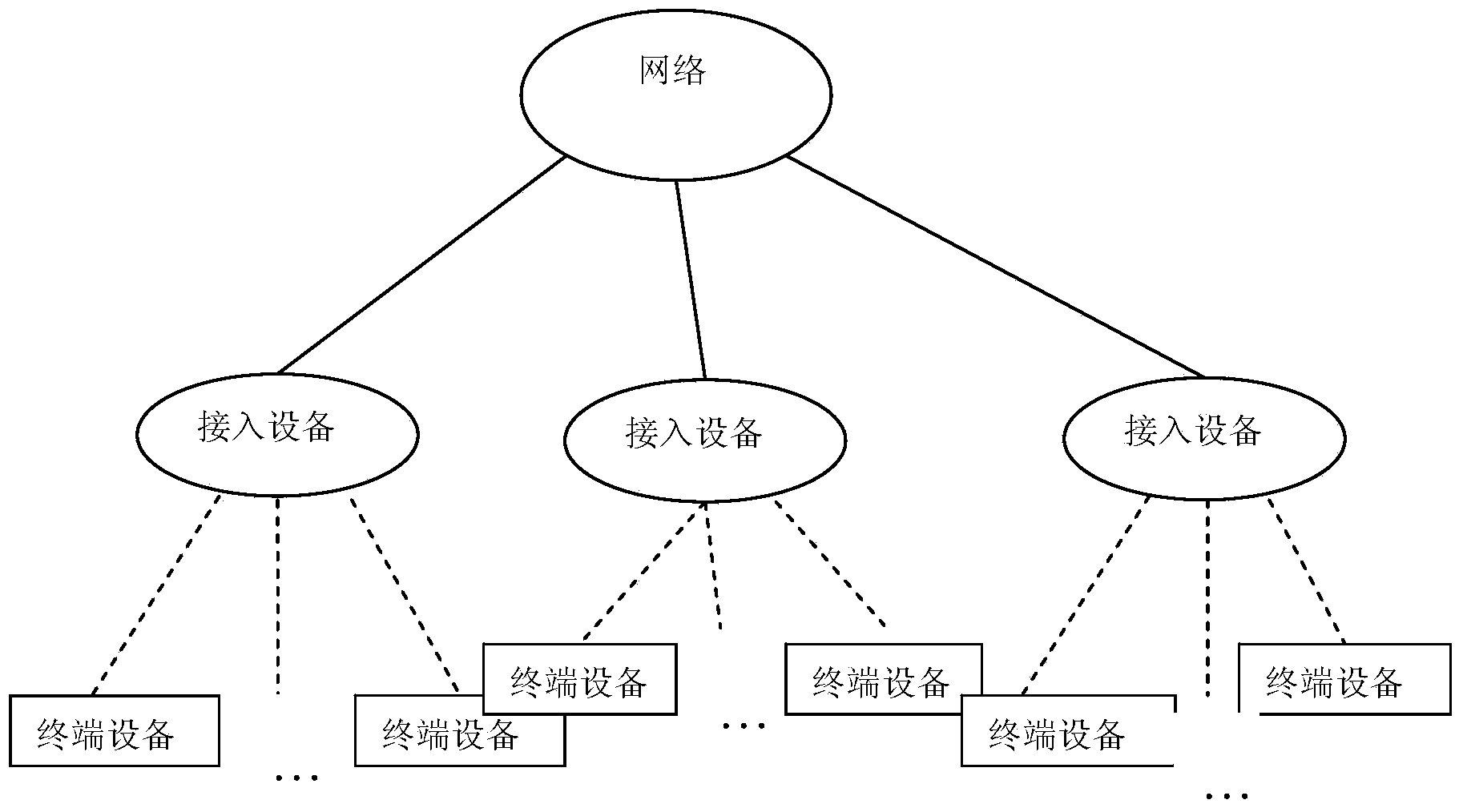
[0034] Such as figure 1 Shown is a network topology schematic diagram of a mixed key processing method of an asymmetric encryption algorithm in a weak terminal environment according to the present invention. The method specifically includes:
[0035] Distribute key pairs or key seed pools according to device forms, and set various trigger conditions;
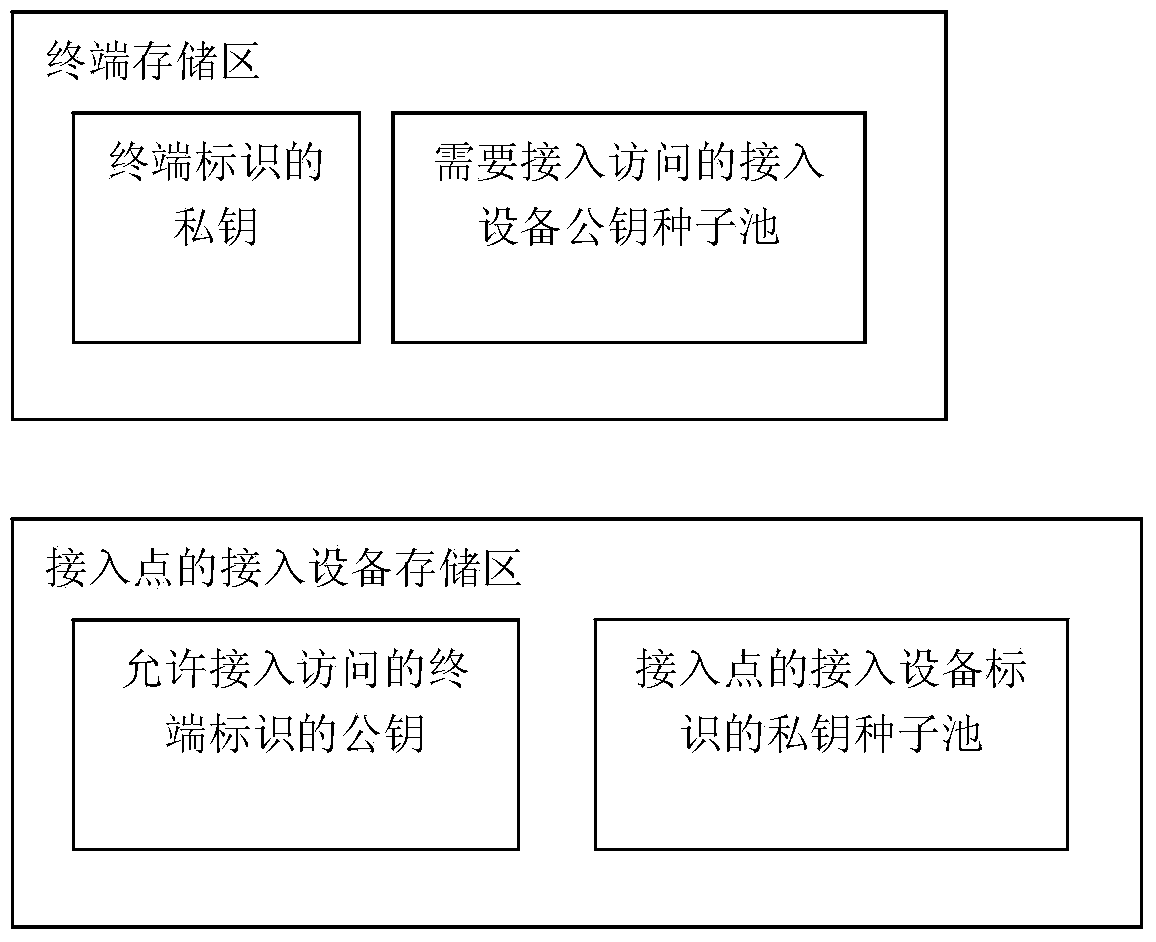
[0036] Among them, such as image 3 Shown is a schematic diagram of the key in the device storage area and the key seed pool. The main steps of distributing the key pair or the key seed pool according to the device form are:
[0037] S11. The device form is a terminal device, and the key processing system distributes the private key identified by the terminal device and the access device public key seed pool that the terminal device needs to access;
[0038] S12. The device form is an access device of an access point, and the key processing system distributes the private key seed pool of the access device identification of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com