User credibility authentication system and method based on user behaviors
A reliable and user-friendly technology, applied in the fields of digital data authentication, instruments, electronic digital data processing, etc., can solve the problem of illegal account/password misappropriation, and achieve the effect of ensuring security and improving accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
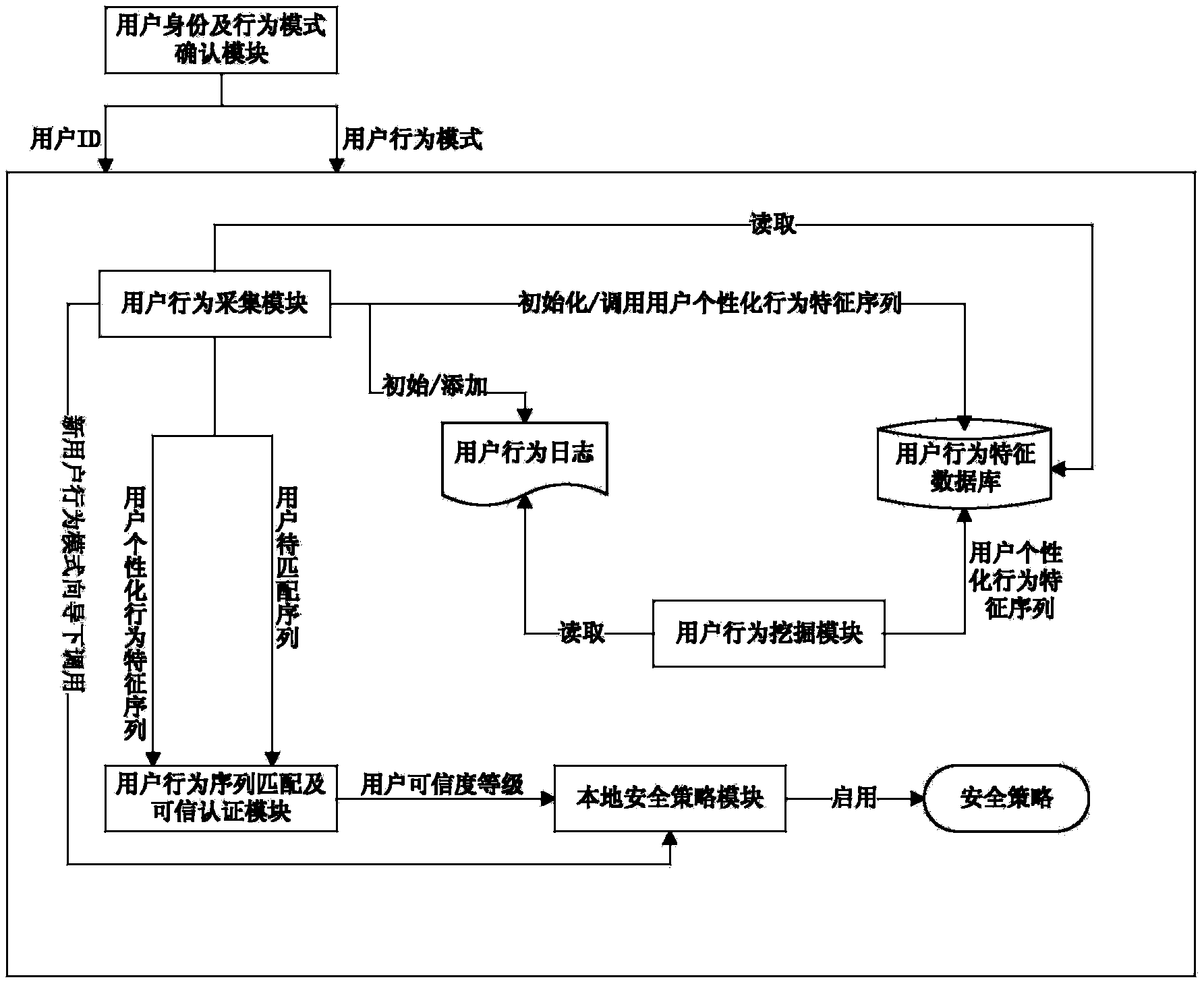
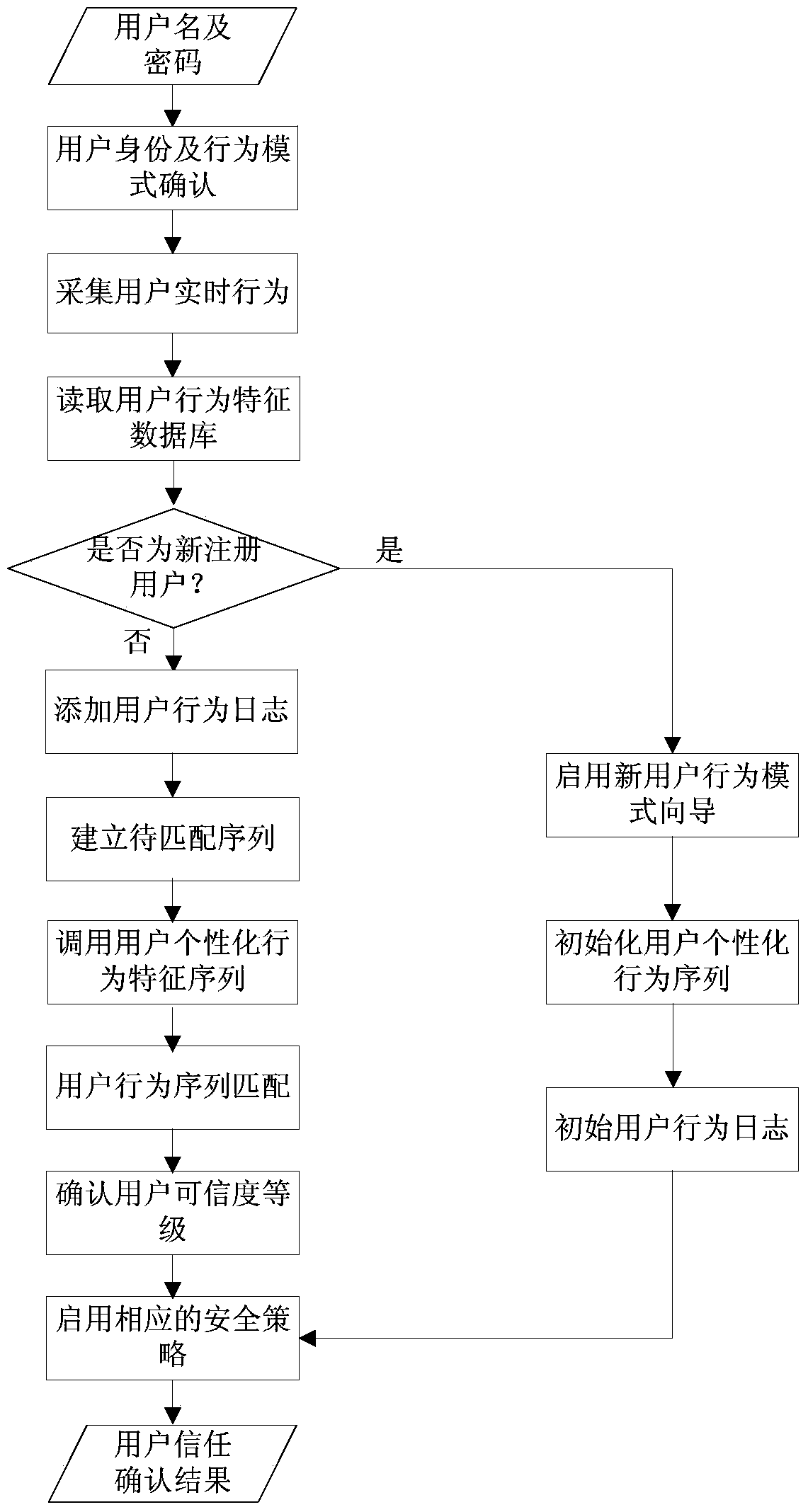
[0047] As we all know, because everyone's job type, income, consumption habits, living environment and other factors are different, although there will be certain fluctuations due to emergencies or changes in habits, the consumption behavior and operation behavior of a trusted user It will maintain a certain fixed characteristic for a long period of time, showing a certain pattern, and it is difficult to be stolen. Therefore, user credibility authentication based on user behavior can not only greatly improve the identification rate of user identities, effectively prevent criminals from stealing other people's legitimate accounts for network fraud, but also prevent legal users, especially system managers, from illegally operating To a certain extent, alleviate the loss of corporate and personal property caused by the imperfect security system of online transactions.
[0048] Based on the above principles, the present invention provides a user credibility authentication syst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com