Deadlock detecting method, equipment and system
A deadlock detection and deadlock technology, applied in the field of clusters, can solve problems such as poor real-time performance and inapplicability to distributed cluster environments
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
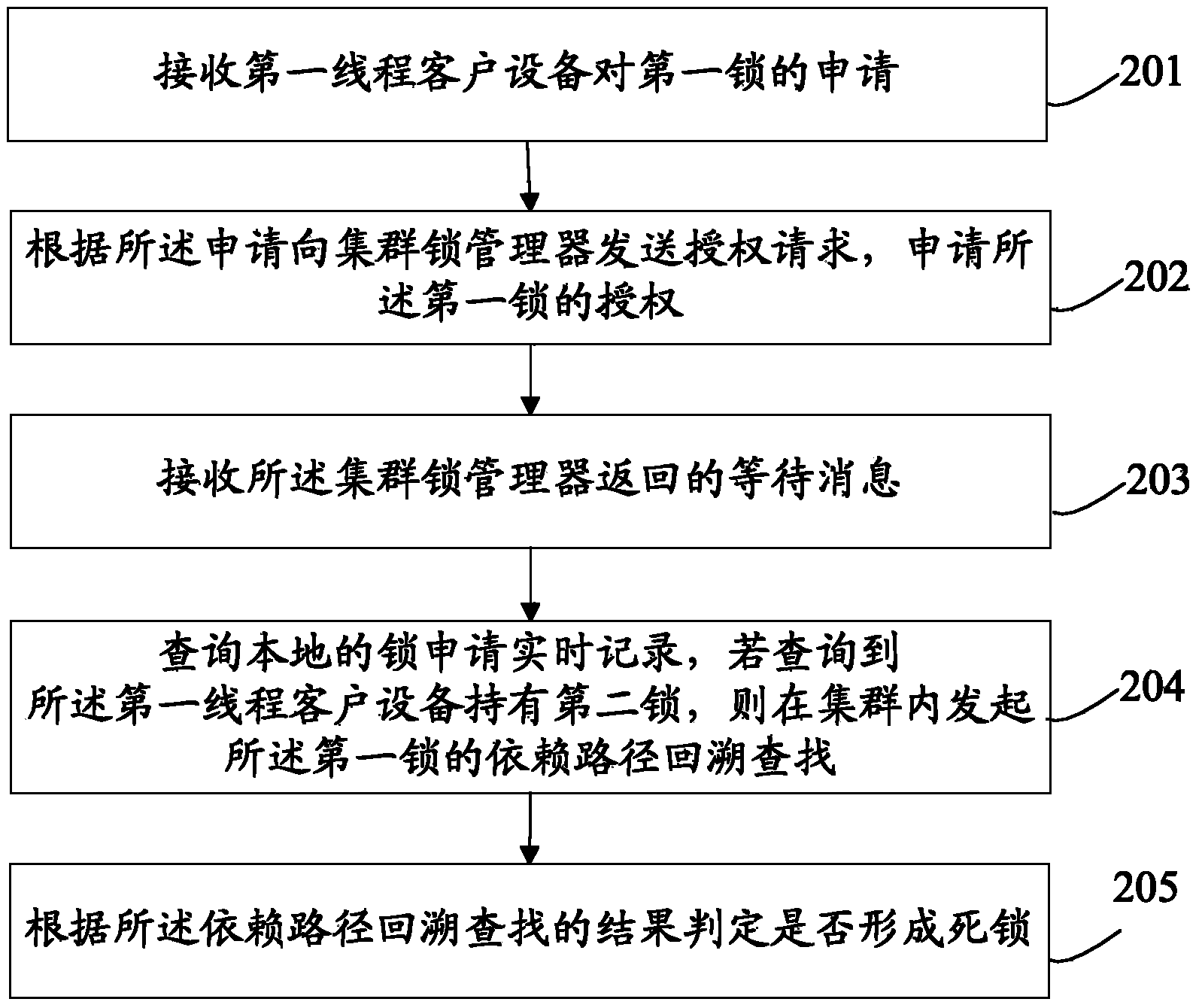
[0047] An embodiment of the present invention provides a deadlock detection method for a proxy server, and the proxy server establishes communication connections with the cluster lock manager and the first thread client device respectively, see figure 2 , the method flow includes:
[0048] 201. Receive the first thread client device's application for the first lock;
[0049] 202. Send an authorization request to the cluster lock manager according to the application, and apply for authorization of the first lock;
[0050] 203. Receive a waiting message returned by the cluster lock manager;
[0051] 204. Query the local real-time lock application records, and if it is found that the client device of the first thread holds the second lock, initiate a traceback search of the dependency path of the first lock in the cluster;
[0052] 205. Determine whether a deadlock is formed according to the result of the dependency path backtracking search.
[0053] Further, the real-time re...
Embodiment 2
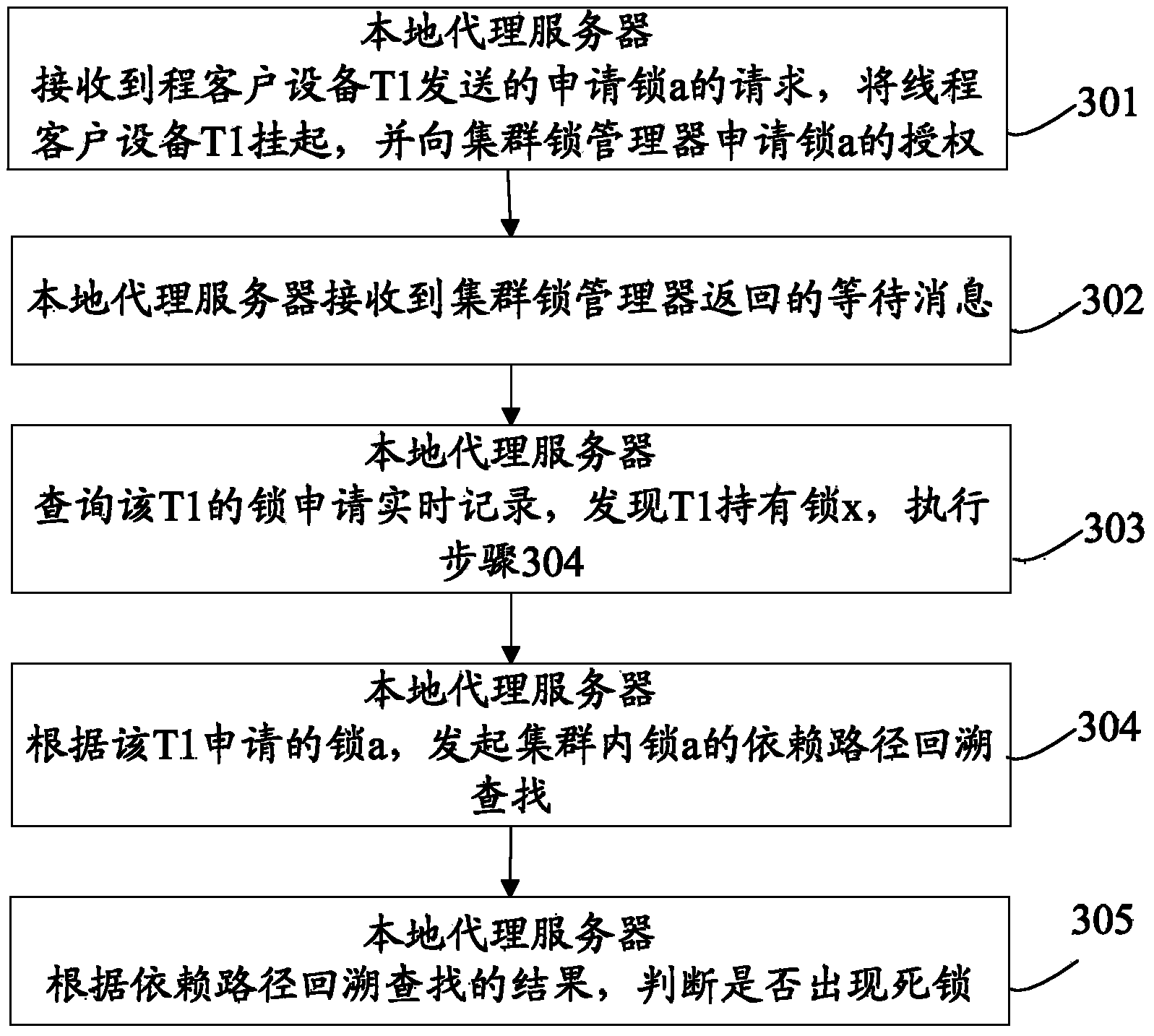
[0078] The embodiment of the present invention provides a deadlock detection method, see image 3 , the method flow includes:
[0079] 301. The local Proxy receives the request for lock a from the thread client device T1, suspends the thread client device T1, and applies to the Master for authorization of the lock a.
[0080] 302. The local Proxy receives the waiting message returned by the Master;
[0081] 303. The local Proxy queries the real-time lock application record of T1, finds that T1 holds lock x, and executes step 304.
[0082] Specifically, after the Proxy receives the authorization from the Master to the Proxy, it needs to perform secondary authorization (that is, distribution) to the local lock applicant (that is, the thread client device), so the Proxy needs to maintain the lock application and authorization status of the local thread client device The lock application is recorded in real time. The local Proxy can query the locks already held by T1 and the lo...
Embodiment 3
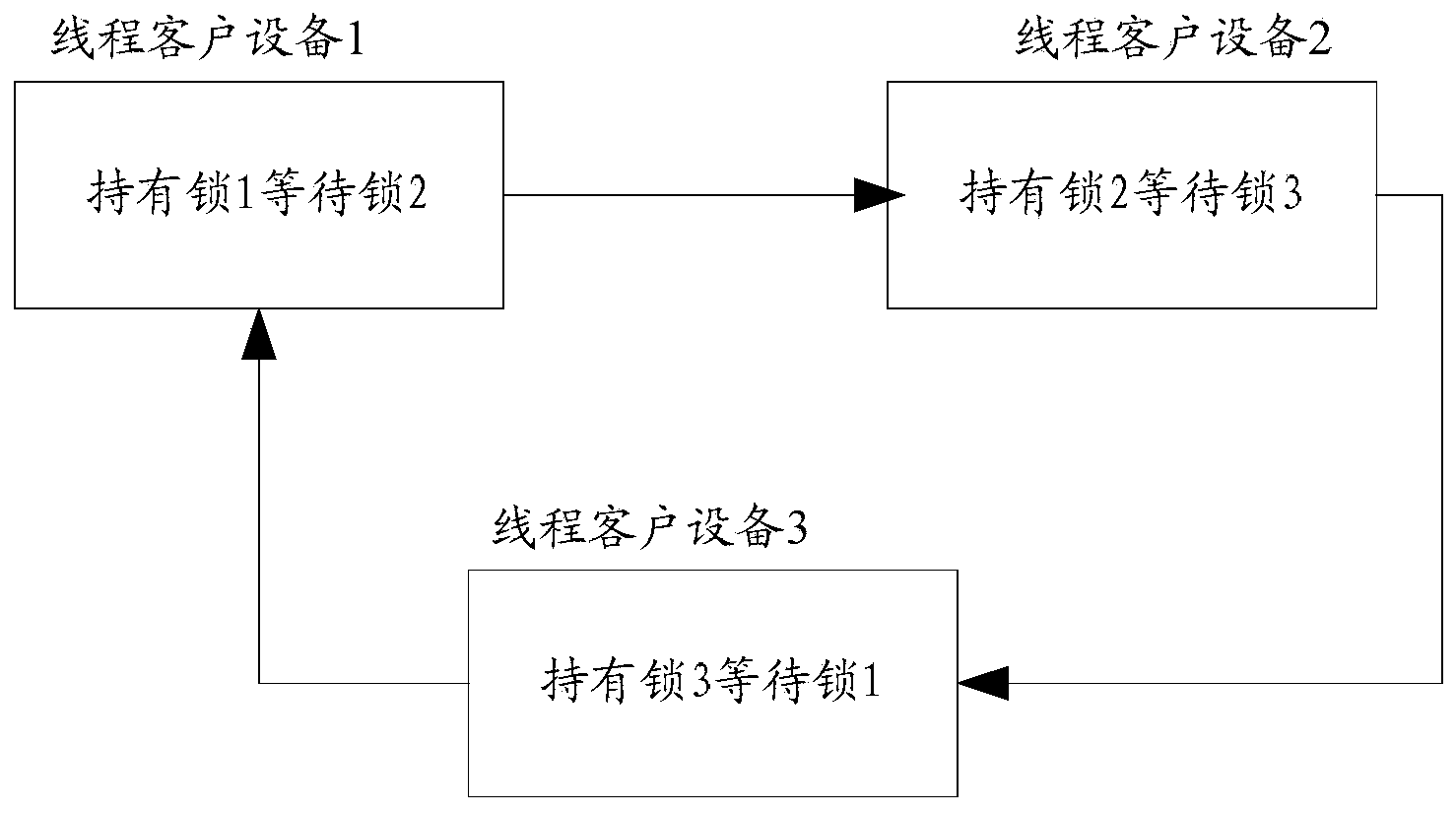
[0102] The embodiment of the present invention also provides a deadlock detection method, see Figure 6 , to explain the commonly used ABBA locks in the cluster. The thread client device T1 and Proxy1 are on node 1, and the thread client device T2 and Proxy2 are on node 2. The method flow includes:
[0103] 601. The thread client device T1 applies to the Proxy1 for the authorization of the lock 1, and the Proxy1 suspends T1, sends a Request (request) message to the Master, and applies for the authorization of the lock 1.
[0104] 602. The Master sends a Grant (authorization) instruction to Proxy1, and sends the authorization of lock 1 to Proxy1, and Proxy1 activates T1 (that is, performs a second authorization of lock 1 to T1). At this time, T1 holds lock 1.
[0105] 603. The thread client device T2 applies to the Proxy2 for the authorization of the lock 2, and the Proxy2 suspends T2, and sends a Request message to the Master, requesting to apply for the authorization of the l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com