Network attack event analysis method and device associated with alarm log
A technology of network attack and analysis method, which is applied in the direction of data exchange network, electrical components, digital transmission system, etc., and can solve the problems of leakage of confidential documents inside the company and leakage of company personnel information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
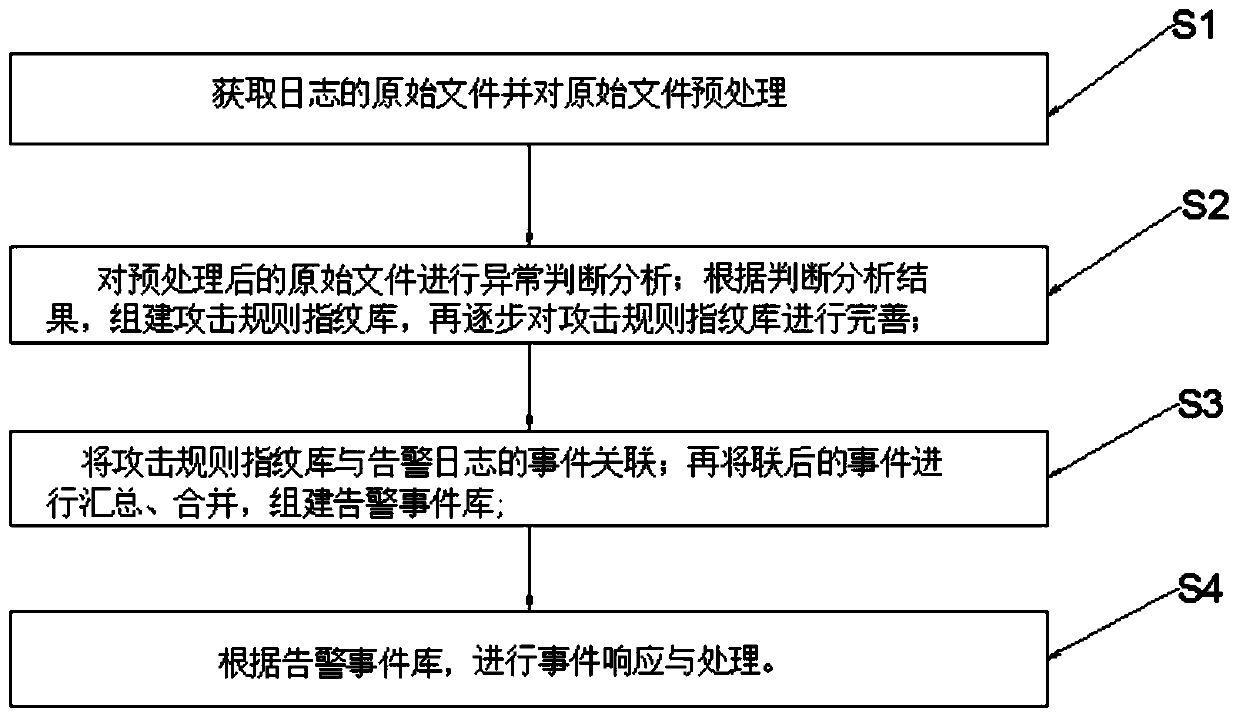
[0089] figure 1 The flow block diagram of the network attack event analysis method associated with the alarm log provided by Embodiment 1 of the present invention, as shown in figure 1 , in an embodiment of the present invention, a network attack event analysis method associated with an alarm log, including:
[0090] S1. Obtain the original file of the log and preprocess the original file;
[0091] The original files of the obtained logs include:
[0092] 1) Through the core switch port mirroring technology, the collection of network traffic information in the information network is realized, and a pcap file is generated; PCAP is a packet capture library;
[0093] 2) Collect syslog logs of data such as desktop management systems, anti-virus systems, IDS (Intrusion Detection Systems), WAF (WebApplication Firewall), firewalls, attack traceability systems, and vulnerability scanning devices;
[0094] The original file preprocessing includes:
[0095] Apply the big data platfo...
Embodiment 2
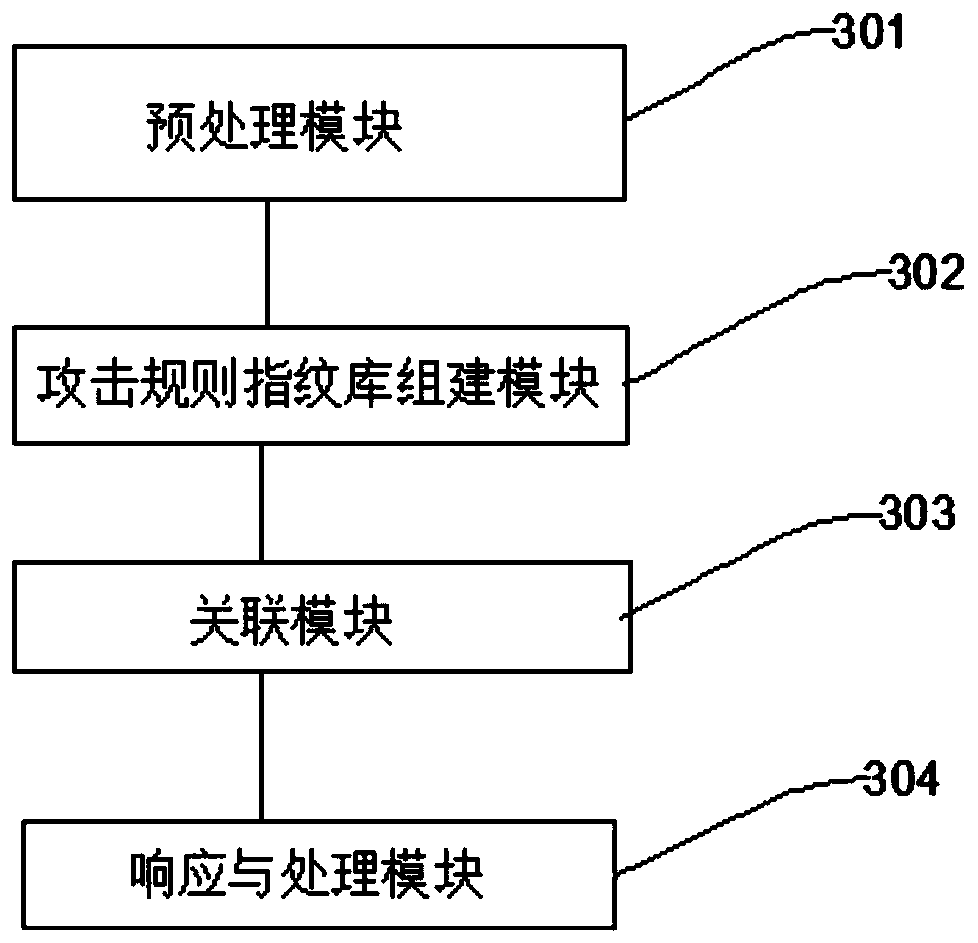
[0130] figure 2 A schematic structural diagram of the network attack event analysis device associated with the alarm log provided in Embodiment 2 of the present invention, as shown in figure 2 , an analysis device adopting a method for analyzing network attack events associated with alarm logs, comprising:
[0131] The preprocessing module is used to obtain the original file; and preprocess the original file;
[0132] The attack rule fingerprint library building module is used to judge and analyze the abnormality of the preprocessed original file; according to the judgment and analysis results, build the attack rule fingerprint library, and then improve and update the attack rule fingerprint library;
[0133] The association module is used to associate the attack rule fingerprint library with the events of the alarm log; it is used to summarize and merge the linked events to form an alarm event library;
[0134] The response and processing module is used to perform event r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com