D2D (Device-to-Device) device identification label processing method and D2D device identification label processing device
A technology of identity identification and processing method, which is applied in the field of communication and can solve the problem of high security risk in the communication process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
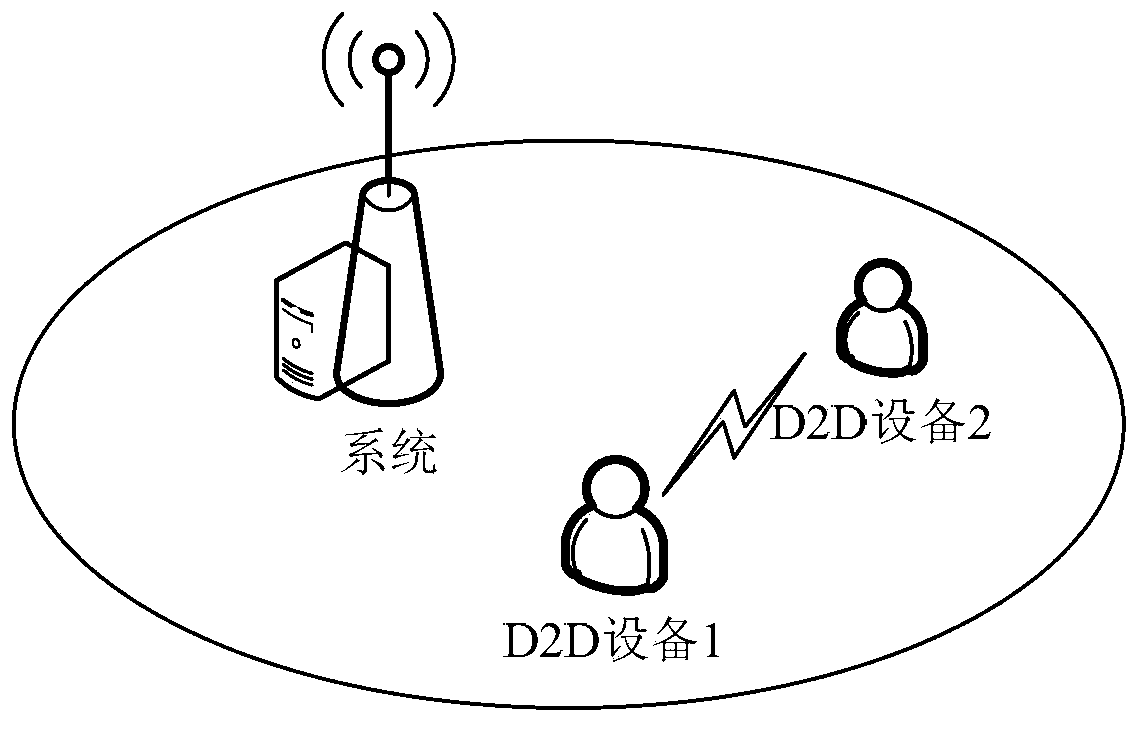
[0185] The present invention provides a method for identity marking and identification in D2D discovery, which includes using two or three types of identity marks to implement identity marking and identification of discovered devices and / or their users.
[0186] In this preferred embodiment, the two types of identities are D2D temporary identities and D2D long-term identities respectively, and the above three types of identities are D2D temporary identities, D2D long-term identities and D2D application layer identities respectively. .
[0187] Preferably, the D2D temporary identity is used to mark the D2D temporary identity of the discovered end device and / or its user, and carry its temporary identity information. D2D temporary identity information also includes simple information such as the type of the discovery device, the purpose and type of the application, and the type of service provided.
[0188] Preferably, the D2D temporary identity is only valid within a certain pe...
Embodiment 2
[0196] This preferred embodiment provides an identity labeling and identification method in D2D discovery, Figure 14 It is the flow of the user identity labeling and identification method on the side of the discovered end device in D2D discovery according to the embodiment of the present invention Figure 1 ,Such as Figure 14 As shown, the method includes the following steps S1402 to S1410.
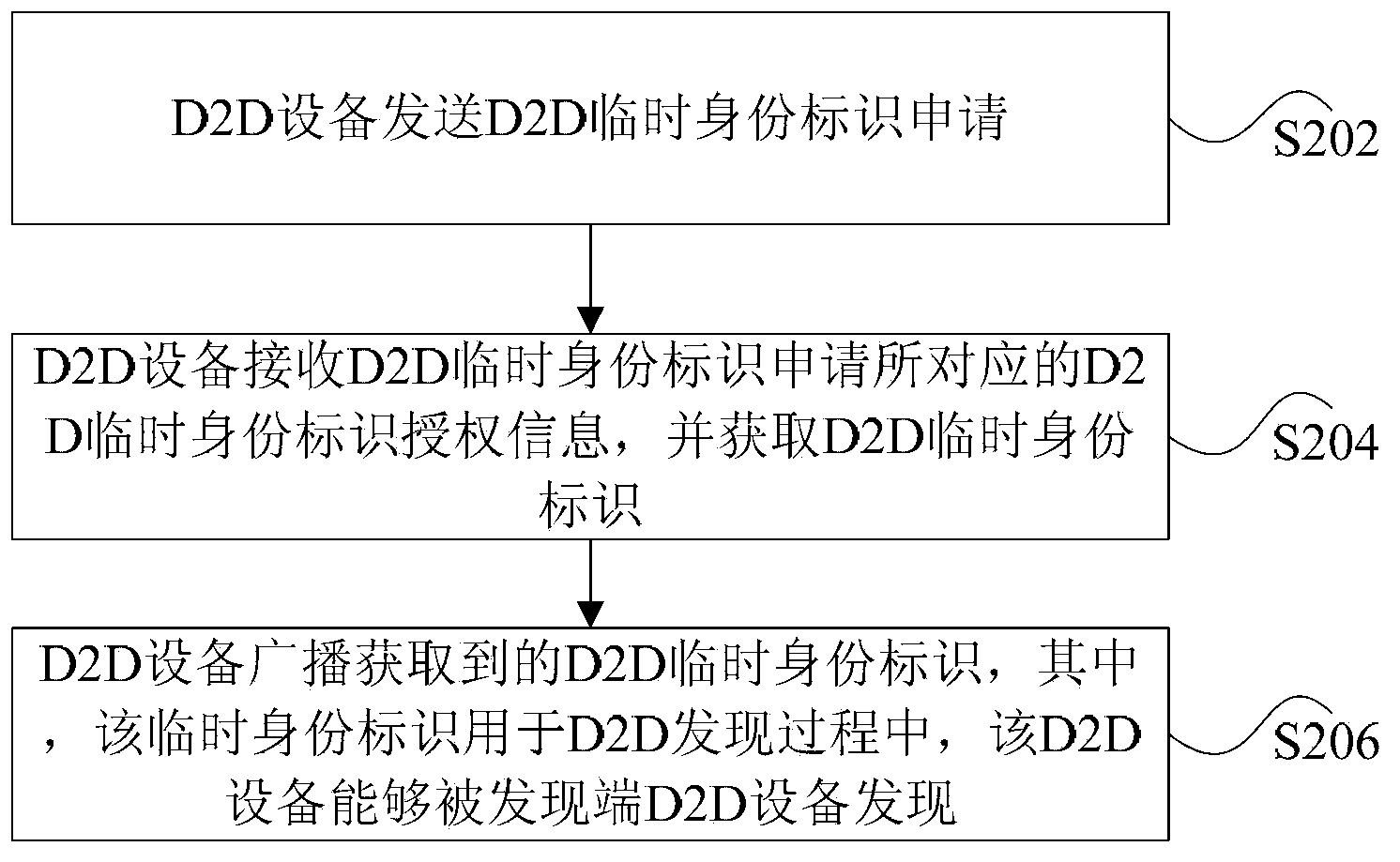
[0197] Step S1402: The discovered end device sends a D2D temporary identity application.
[0198] Step S1404: The D2D discovery system feeds back the authorization of the D2D temporary identity.
[0199] Step S1406: The discovered device sends the D2D temporary identity to the discovering device.
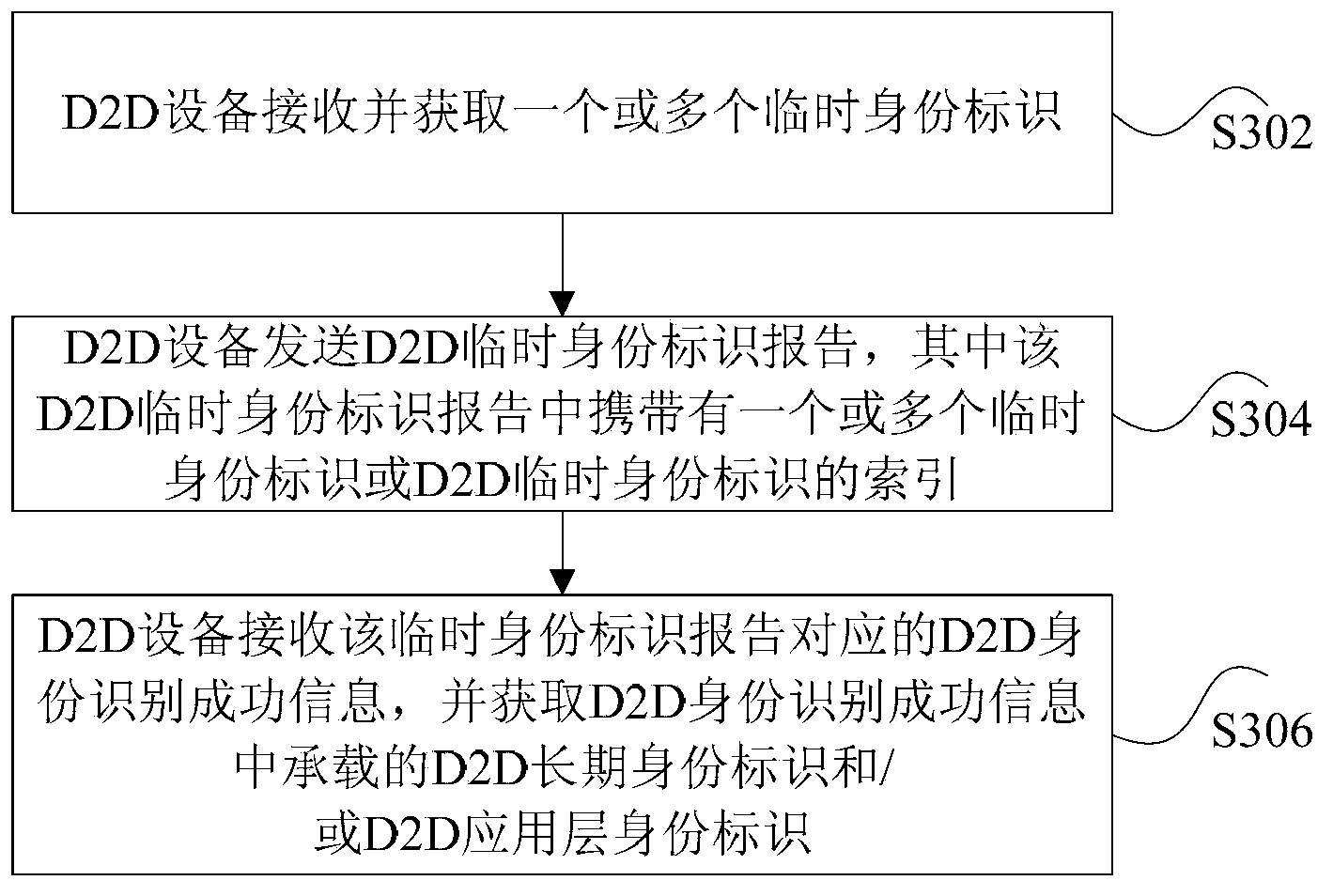
[0200] Step S1408: The discovering device sends a D2D temporary identity report to the D2D system.
[0201] Step S1410: the D2D discovery system feeds back the D2D identification information to the discovery device.
Embodiment 3
[0203] This preferred embodiment provides an identity labeling and identification method in D2D discovery, Figure 15 It is the flow of the user identity labeling and identification method on the side of the discovered end device in D2D discovery according to the embodiment of the present invention Figure II ,Such as Figure 15 As shown, the method includes the following steps S1502 to S1504.
[0204] Step S1502: The discovered end device sends a D2D temporary identity application.
[0205] Step S1504: The D2D discovery system feeds back D2D temporary identity authorization rejection information.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com