Remote network attack and defense virtual simulation system based on virtualization and cloud technology
A virtual simulation, remote network technology, applied in transmission systems, electrical components, etc., can solve the problem of inability to remotely share network topology attack and defense scenarios, single and other problems, to avoid repeated investment in construction, improve utilization, and achieve the effect of remote sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
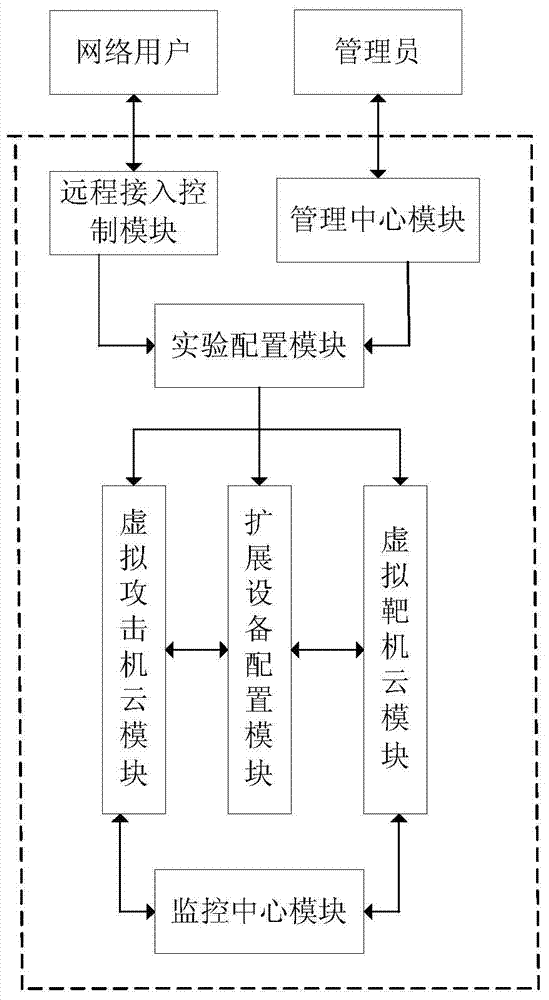
[0017] Specific implementation mode 1. Combination Figure 1 to Figure 3 Describe this embodiment, the remote network attack and defense virtual simulation system based on virtualization and cloud technology, including a remote access control module, a virtual attack machine cloud module, a virtual target machine cloud module, a monitoring center module, a management center module and an experiment configuration module;
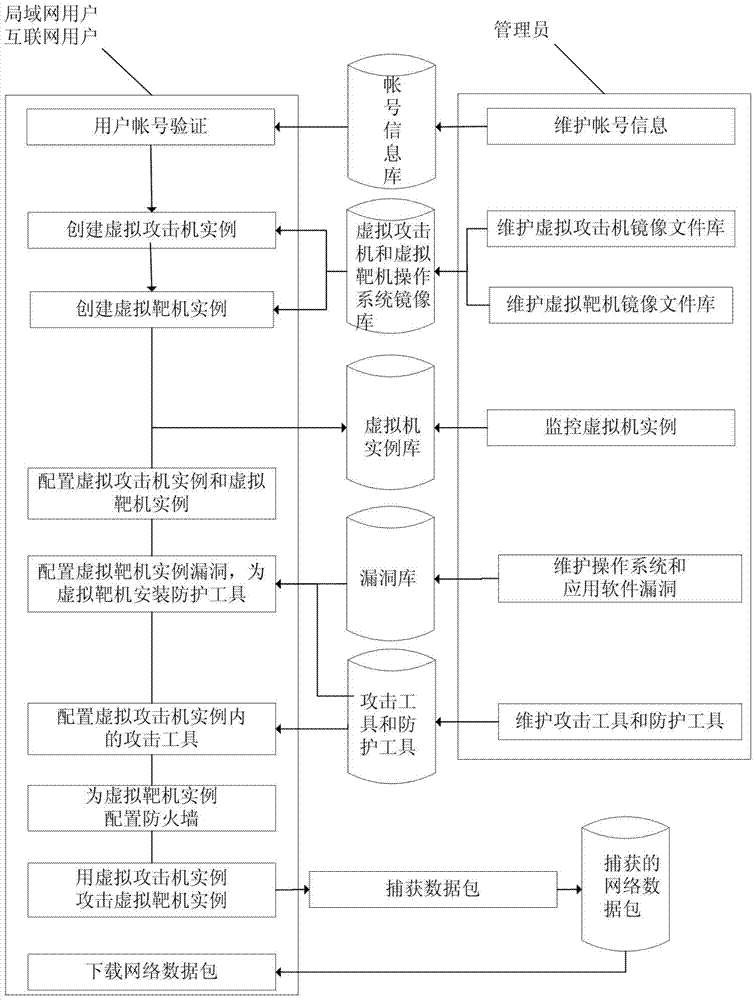
[0018] The management center module allows administrators to maintain account information that can be connected to the virtual simulation system, including user name, initial password and operable experiment category; maintain Windows and Linux operating system images located in the virtual attack machine cloud module according to the experiment category File and port scanning tools, SQL injection tools, network sniffer, Trojan horse implantation tools, remote control tools, cross-site scripting attack tools, DDos attack tools and password cracking attack tool...
specific Embodiment approach 2
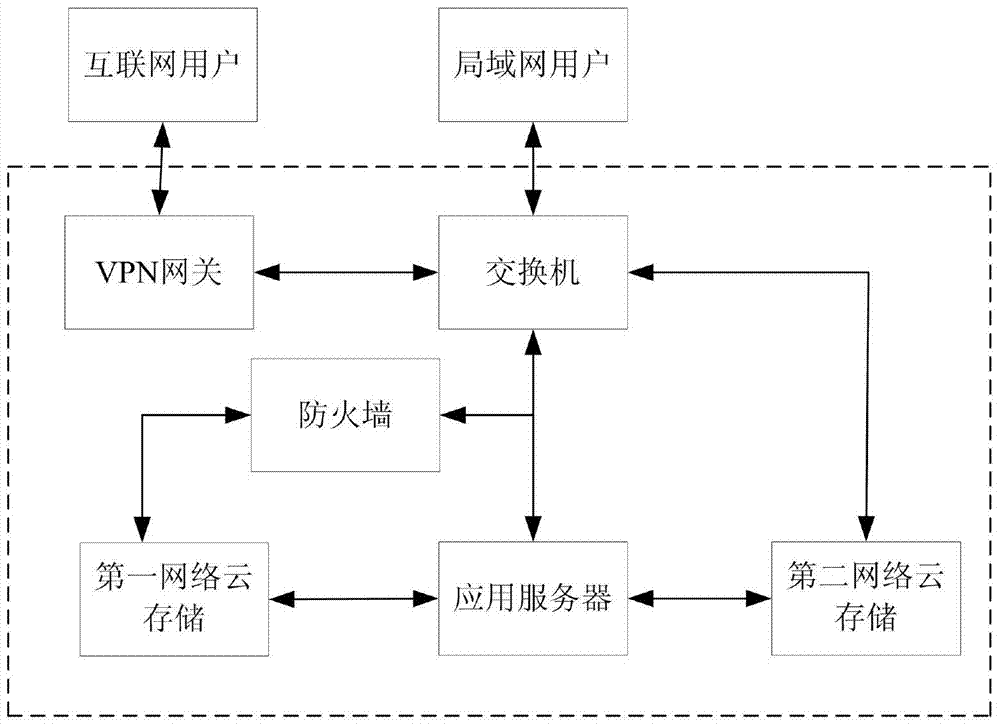
[0025] Specific embodiment two, combine figure 2 and image 3 Describe this embodiment, this embodiment is an embodiment of the virtual simulation system based on remote network attack and defense described in the first embodiment: the hardware equipment involved in this embodiment includes a VPN gateway, a switch, a firewall, an application server, a first network Cloud storage and second network cloud storage.
[0026] The application server is connected to the first network cloud storage, the second network cloud storage and switches, installed Ubuntu operating system, Openstatck, JDK, ApacheTomcat and Mysql, and deployed JSP / Servlet programs, including figure 1 The shown remote access control module, virtual attack machine cloud module, virtual target machine cloud module, monitoring center module, management center module, experiment configuration module and extended device configuration module.
[0027] The first network cloud storage is connected to the switch throug...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com