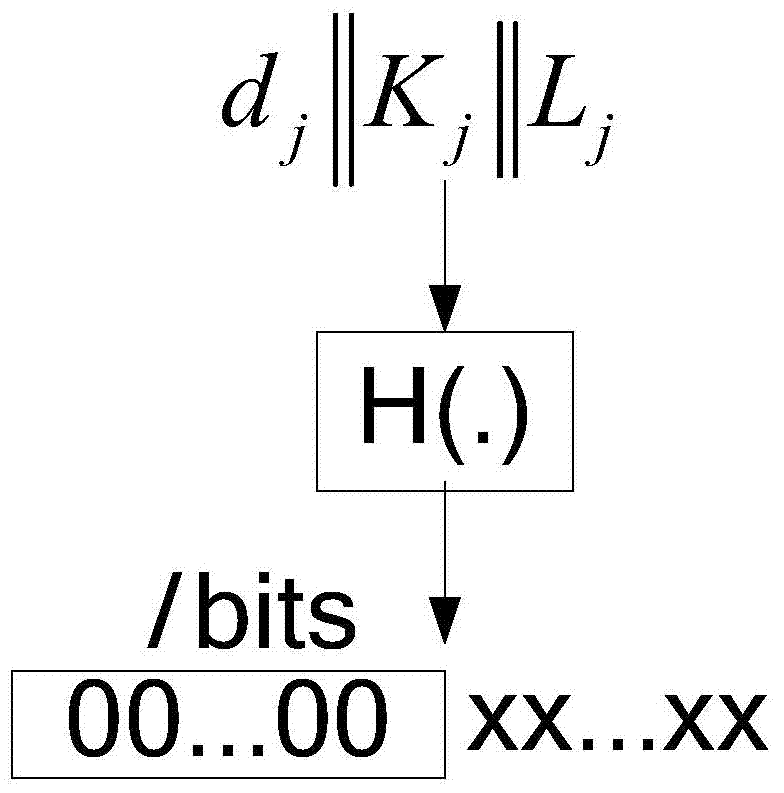Lightweight wireless sensor network safety small data distribution method
A wireless sensor and network security technology, applied in security devices, network topology, wireless communication, etc., can solve the problems of high computing and storage overhead, unsuitability, etc., and achieve the effect of low storage overhead and resistance to malicious attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
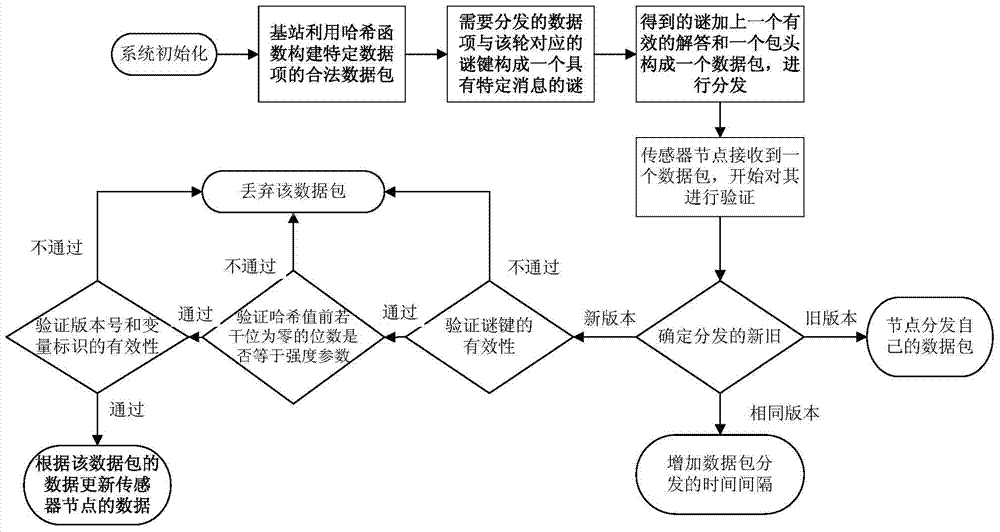
[0048] Such as figure 1 As shown, this protocol is divided into three stages: system initialization, pre-processing of data packets, and data packet verification, as follows:
[0049] The first stage: the system initialization stage, the base station generates a one-way key chain, and adds the key chain commitment value to the sensor node before the deployment of each sensor node;
[0050] The second stage: the pre-processing stage of the data packet, the base station uses the hash function to construct a legal data packet of a specific data item;
[0051] The third stage: the data packet verification stage, the sensor node verifies the received data packet, if the received data packet is a legal data packet, then accept the data packet and update the sensor node, otherwise directly discard the data packet .
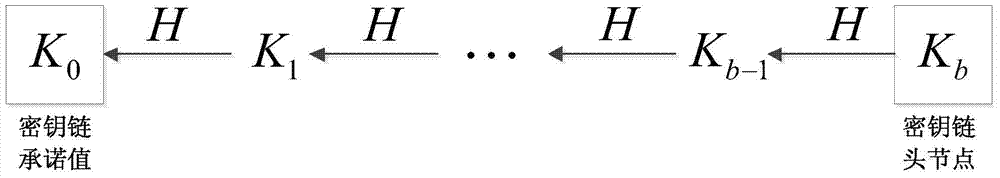
[0052] During the system initialization phase, such as figure 2 As shown, the base station picks a random number K b , and then generate a one-way key chain, by K ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com