Internet identity authentication method based on incoming calls
An identity authentication, Internet technology, applied in the fields of electronics, Internet, trusted authentication, and communication, can solve the problems of not being particularly convenient, insecure, operating costs and convenience, reducing security standards, etc., to shorten the physical location and reduce the convenience. , the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
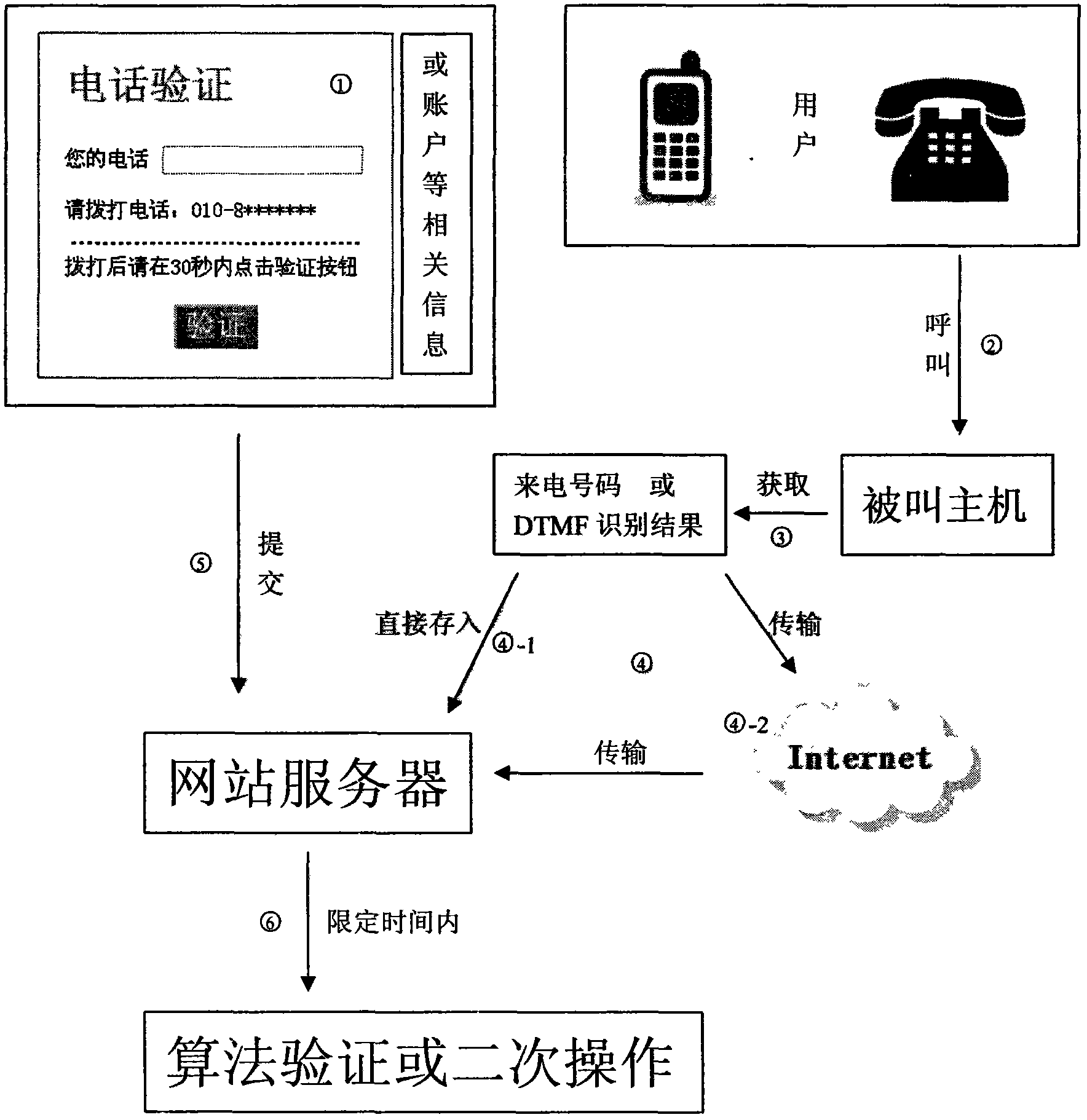
[0017] The specific implementation mode, the website server end of the present invention realizes easier and has ready-made technology more, mainly enumerates several called host end implementation modes below:
[0018] 1. The designated number of the website is the mobile phone number method 1. Directly use the mobile phone as the called host, write the corresponding mobile phone software to obtain the incoming call number and send it to the website server through GPRS and other methods. Currently popular mobile operating systems such as Android can support this software Law.
[0019] 2. The designated number on the website is the mobile phone number Method 2, use the single-chip microcomputer to control the GSM module to obtain the incoming call number, and then use the GPRS function to send the incoming call number to the server.
[0020] 3. Using the LAN method to replace the above-mentioned GPRS method can increase the speed and concurrent operation.
[0021] 4. The desi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com