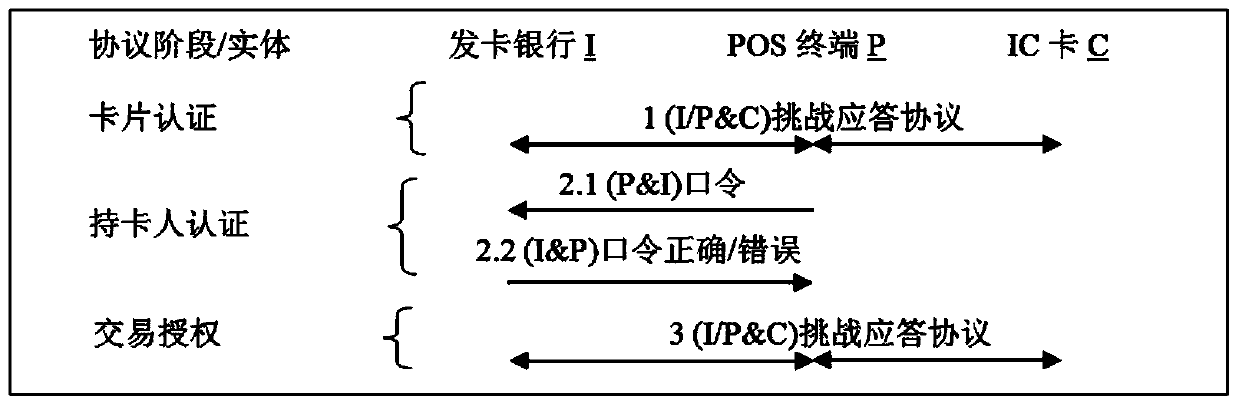
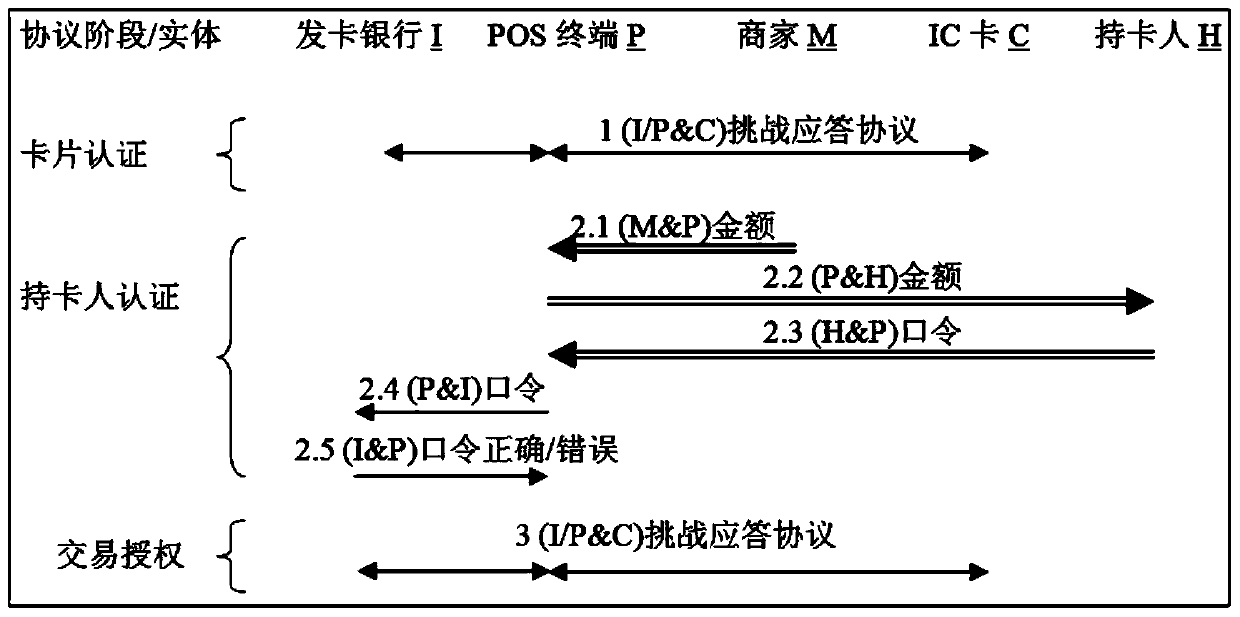
Trusted terminal, double-channel card, anti-cloning chip, chip fingerprint and channel attack resistance method
A dual-channel, terminal technology, applied in the security field, can solve problems such as leaks, chips that do not have anti-cloning capabilities, and side-channel attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
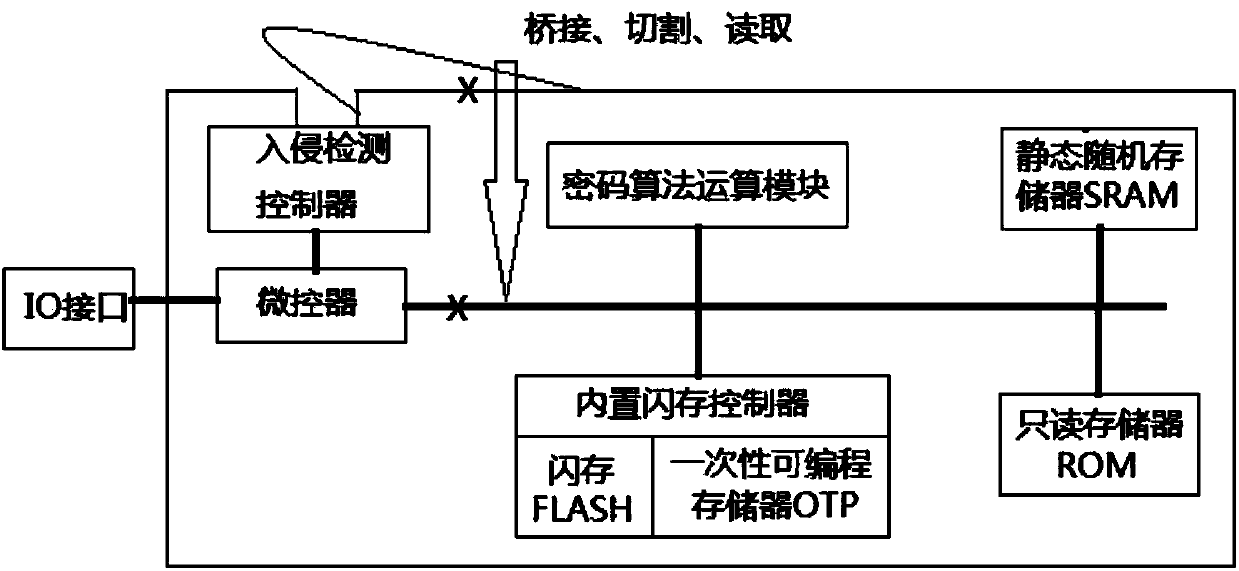
[0105] Such as Figure 7 As shown, a trusted terminal in this embodiment includes a main control chip, a dual-channel card slot, a channel isolation component and a communication interface;
[0106] The main control chip is directly connected to the first channel connector of the dual-channel card slot, directly or indirectly connected to the channel isolation component, and directly connected to the communication interface, for directly or indirectly controlling the channel isolation component and directly controlling the communication Interface and processing information; the direct connection refers to the connection through the channel connection line, without dual-channel card isolation in the middle; the indirect connection refers to the main control chip as a bridge and channel isolation component through the dual-channel card in the dual-channel card slot connected;
[0107] The dual-channel card slot includes a first channel connector and a second channel connector, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com