Protection method, device and system for voice-over-internet-protocol service
A technology for voice services and equipment, applied in the field of optical communication, can solve the problems of high configuration requirements of call access equipment and poor protection effect, and achieve the effect of guaranteeing call quality, simplifying complexity, and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
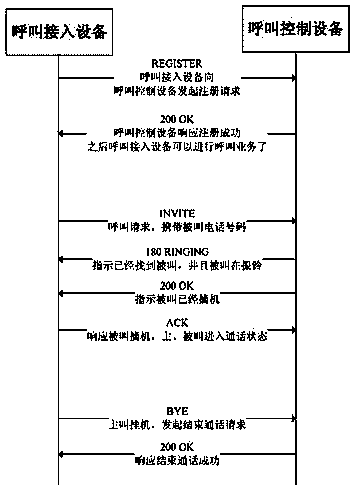
[0023] Embodiment 1: The embodiment of the present invention provides a method for protecting the voice over IP (VOIP) service of the call access device, such as figure 1 shown.
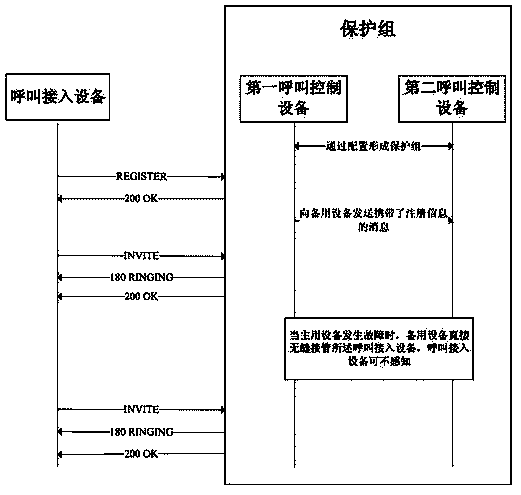
[0024]The protection method can be applied in a protection group, the protection group includes at least a first call control device and a second call control device connected to each other, and all call control devices in the protection group are connected to the call access device. A protection group is also called a backup group, and it consists of an active call control device and a backup call control device, or it can also consist of an active call control device and multiple backup call control devices. The protection group can be connected to the call access device through the convergent switching device, at the same time, the protection group is connected to the network, and the call control devices in the protection group are connected to each other. Usually, multiple call access devices a...
Embodiment 2
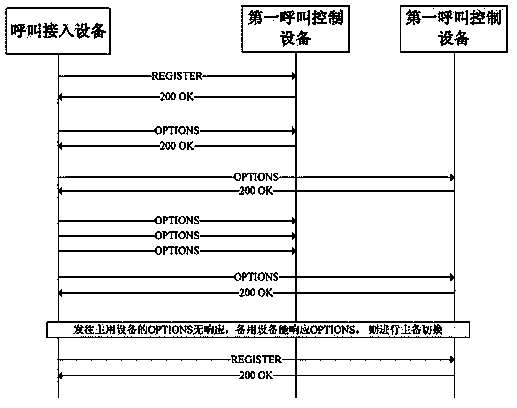
[0042] Embodiment 2: The embodiment of the present invention provides a call control device, such as image 3 shown. A receiving module, configured to receive messages; a storage module, configured to store first registration information carried in the messages received by the receiving module, where the first registration information is the first call interface connected to the call control device Enter the registration information of the device in the protection group, the protection group is the protection group where the call control device is located; the processing module is used to judge whether the call control device needs to change from the standby state to the active state, and if so, then Using the IP address of the protection group as an IP address of the call control device, sending a free address resolution protocol message carrying the MAC address of the protection group to the first call access device, and sending the call The control device is set to the act...
Embodiment 3
[0047] Embodiment 3: The embodiment of the present invention also provides a network device, as attached Figure 4 As shown, it includes a processor, a memory, and a transceiver, wherein the processor is coupled with the latter two. The network device can be used to execute the method in the first embodiment. Specifically, the transceiver is used to receive messages from the outside of the network device and send messages to the outside, and the function of the transceiver can also be replaced by a receiver and a transmitter, wherein the receiver is used to receive messages, and the transmitter is used to The message is sent; the memory is used to store information; the processor is used to process the received message, specifically, it has the function of the processing module in the second embodiment.
[0048] The processor can be a general-purpose processor, such as an integrated circuit IC, and the program executed by it is stored in the memory; the processor can also be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com