Method for achieving key management in wireless mobile ad hoc network based on identities
A mobile ad hoc network and key management technology, which is applied in the field of identity-based key management in wireless mobile ad hoc networks, can solve problems such as imperfect computing efficiency and security, strong security assumptions, etc., to achieve less computing overhead, The effect of wide application range and less network bandwidth overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046]In order to describe the technical content of the present invention more clearly, further description will be given below in conjunction with specific embodiments.
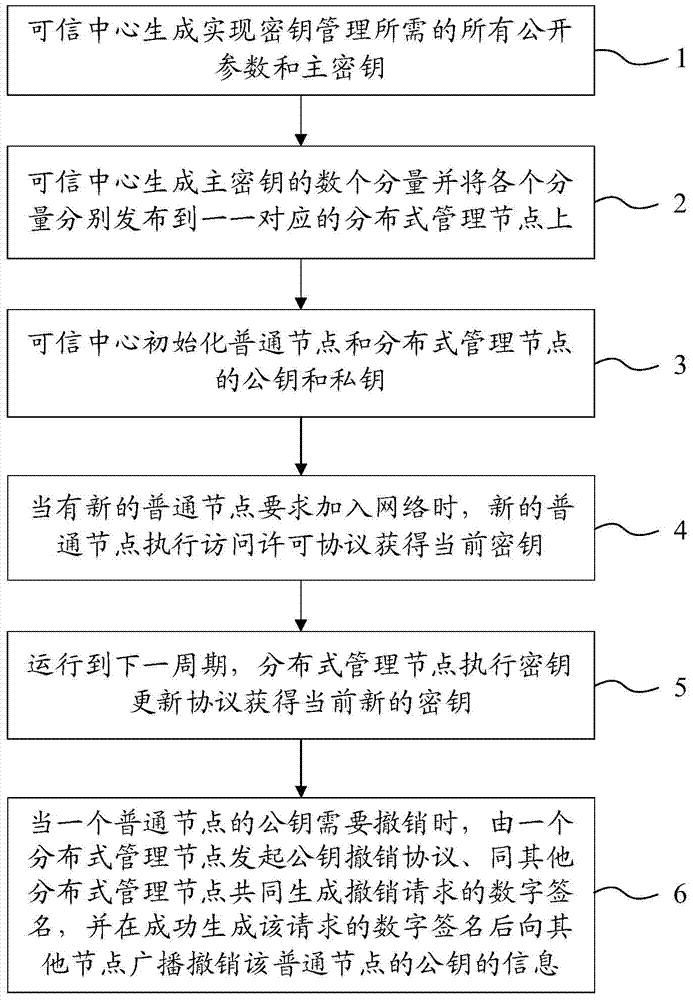
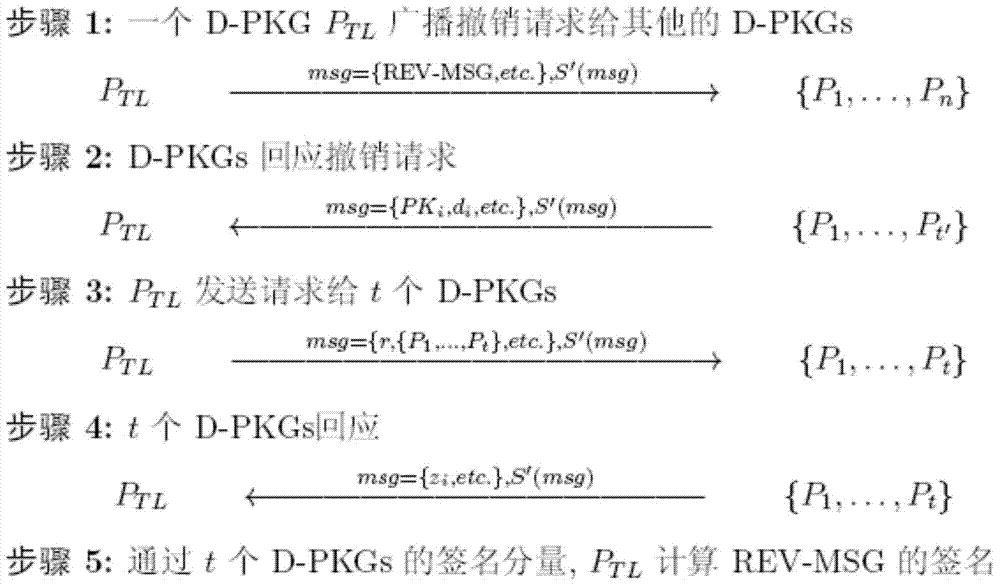
[0047] Aiming at the deficiencies of the above-mentioned existing schemes and technologies, the present invention proposes an identity-based key management scheme under the wireless mobile ad hoc network environment, and realizes safe and efficient key management. Security means that the key management scheme has: the updated key is unforgeable (adaptive chosen-plaintext attack under the random oracle model).
[0048] The efficiency of the scheme is reflected in: (1) the adoption of Schnorr digital signature (Schnorr C P. Efficient identification and signatures for smart cards. Advances in Cryptology CRYPTO89 Proceedings. Lecture Notes in Computer Science. Springer Berlin / Heidelberg. 252) constructed identity-based signature technology (Liu J K, Baek J, Zhou J, et al. Efficient online / offline identity-based ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com