Program protection method and device
A program protection and encryption algorithm technology, applied in program/content distribution protection, computer security devices, instruments, etc., can solve the problem that software programs cannot be effectively protected, and achieve the effect of increasing the difficulty of cracking, improving efficiency, and protecting source code
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
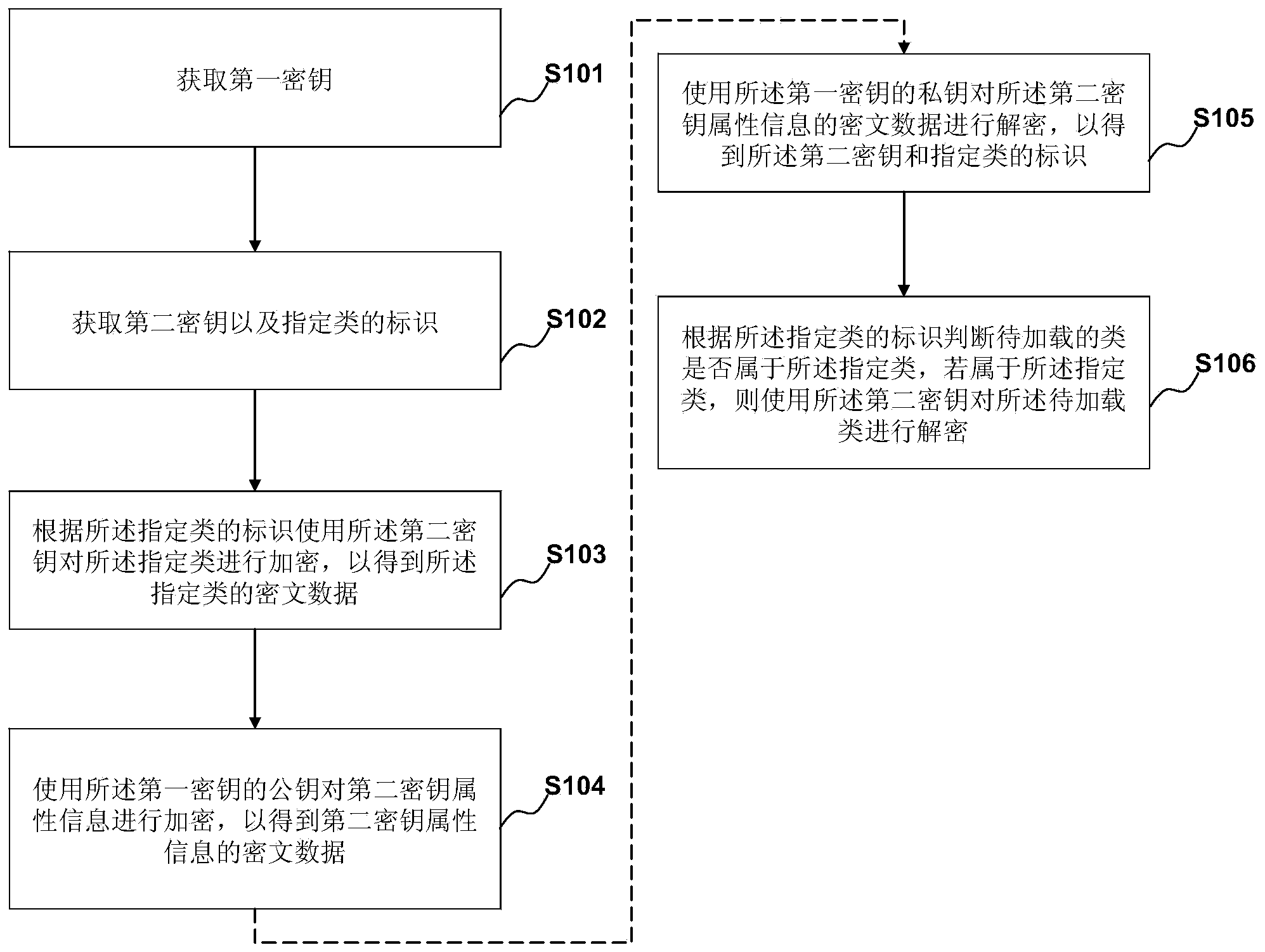
[0074] figure 1 It is an exemplary flow chart of a method in Embodiment 1 of the present invention. This embodiment provides a program protection method, the method may include:
[0075] During the program generation phase, the following encryption steps are performed:
[0076] S101. Acquire a first key, where the first password includes a public key and a private key.
[0077] The first key is used to encrypt and protect the second key. The first key belongs to a fixed asymmetric key, including a public key and a private key, encrypted with the public key and decrypted with the private key, where the private key is not public, such as using the RSA asymmetric encryption and decryption algorithm, the length of the key It can be 512, 1024, or 2048. The larger the key length, the closer to zero the possibility of being cracked.
[0078] There are many ways to obtain the first key. For example, you can directly preset a first key, or receive the first key input from the outsi...
Embodiment 2
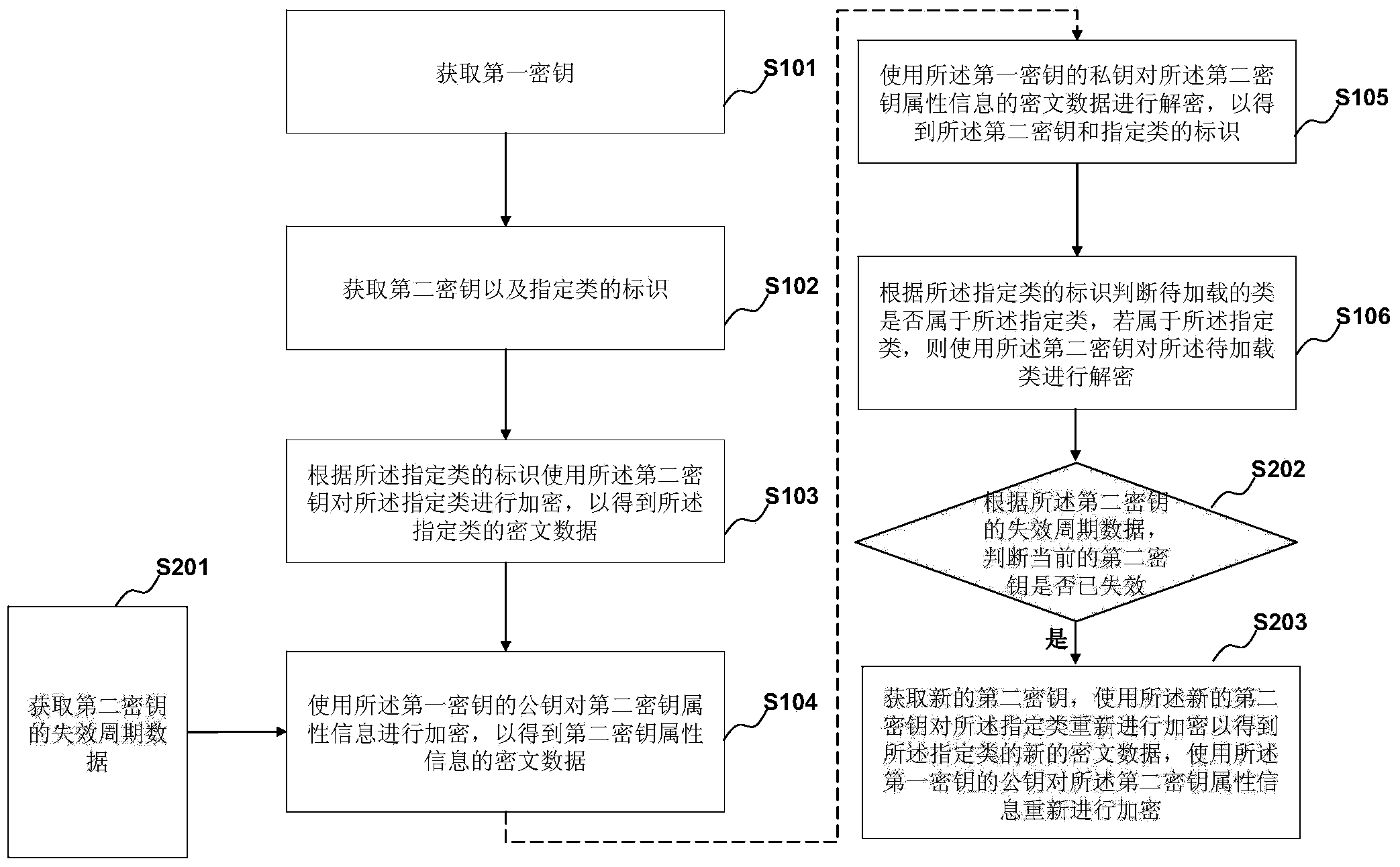
[0102] figure 2 It is an exemplary flow chart of the method in Embodiment 2 of the present invention. This embodiment is based on the foregoing embodiments, and is a further supplement and improvement on the basis of the foregoing embodiments. In principle, on the basis of the previous embodiment, this embodiment adds a dynamic update mechanism for the second key and introduces an expiration period for the second key, thereby further improving security.
[0103] In this embodiment, the second key attribute information further includes expiration period data of the second key;
[0104] Before using the public key of the first key to encrypt the attribute information of the second key, it further includes:
[0105] S201. Acquire expiration period data of the second key.
[0106] The expiration period data of the second key may include the expiration period of the second key and the next expiration time of the second key (that is, the termination time of the current validity ...
Embodiment 3
[0124] On the basis of the foregoing embodiments, the present invention will be further described below in conjunction with specific scenarios.
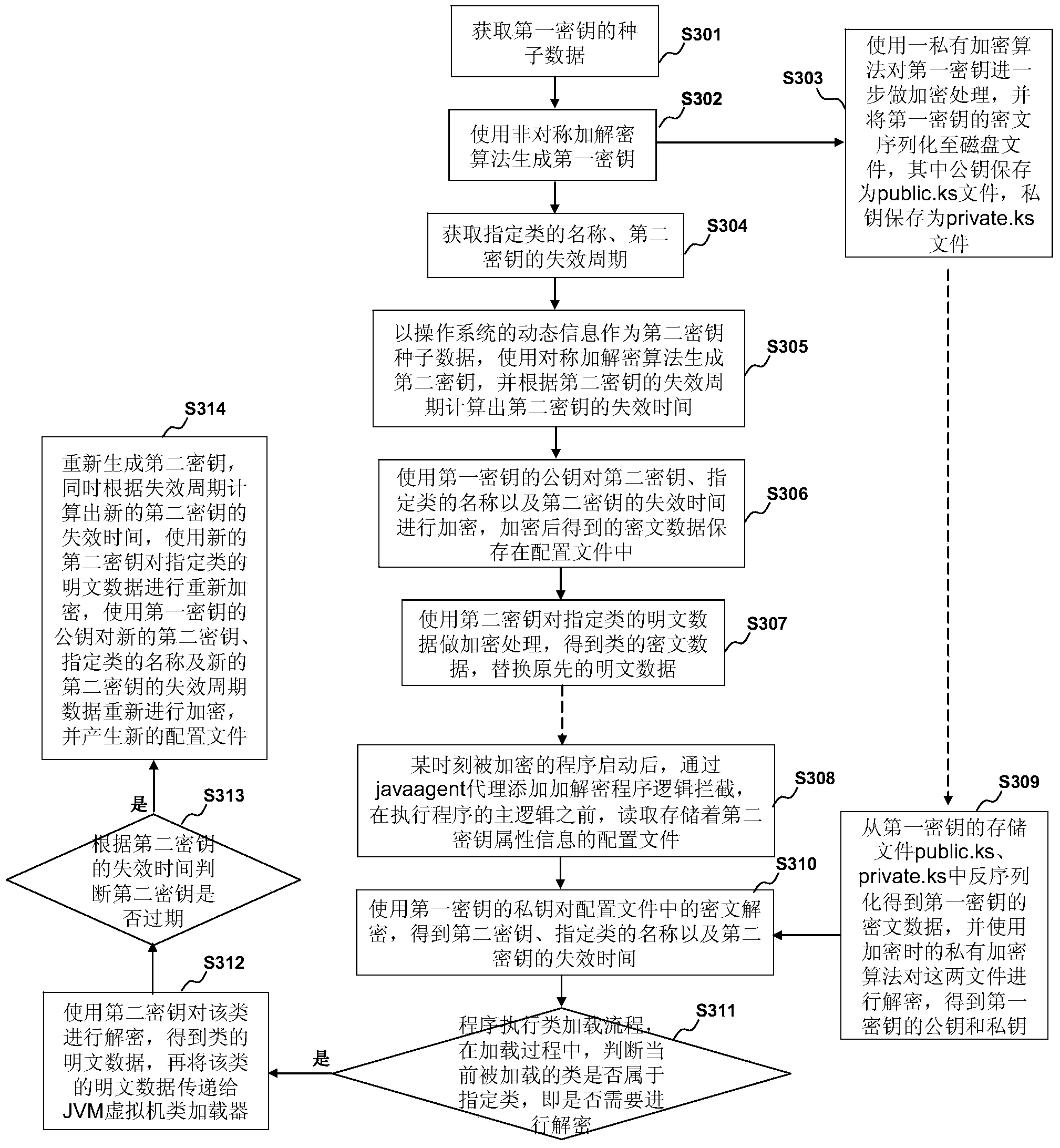
[0125] image 3 It is an exemplary flow chart of the method in Embodiment 3 of the present invention.
[0126] S301. Acquire seed data of the first key. For example, it may be obtained based on data input by the user.
[0127] S302. Generate a first key (including a public key and a private key) using an asymmetric encryption and decryption algorithm (such as RSA).
[0128] S303. Use a private encryption algorithm to further encrypt the first key, and serialize the ciphertext of the first key to a disk file, wherein the public key is saved as a public.ks file, and the private key is saved as a private.ks file .
[0129] S304. Obtain the name of the specified class and the expiration period of the second key (for example, 90 days). For example, it may be obtained based on data input by the user.
[0130] S305. Use the dynamic in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com