A Decoding Method of Binary Cipher Decoder Based on Optimal Enumeration Algorithm
A decoding method, binary technology, applied to encryption devices with shift registers/memory, etc., can solve problems such as time wasted in sending repetitive passwords, achieve the effects of reduced data volume, low complexity, and shortened decoding time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] According to the inventive method, take decoding 24 passwords as an example, specifically as follows:
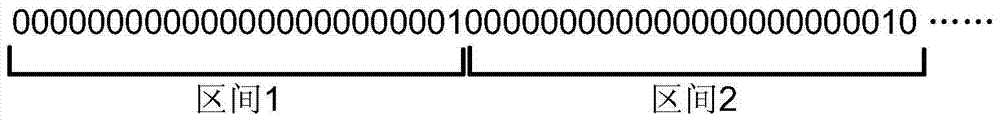
[0014] Enumerate and send all numbers from 1 to 16777216 in the password set one by one. A total of 16777216 24-digit binary passwords need to be sent. Taking the time interval between each 2-digit binary data as being limited to greater than or equal to 2 milliseconds as an example, the password set It takes a total of 0.002s×24×16777216=805306.368 seconds ≈ 223.7 hours for all the data to be sent. Such as figure 1 As shown, the existing enumeration method is to send the next 24-bit binary number (shown in section 2) every time all the bits of the previous 24-bit binary data (shown in section 1) are completely sent, until the password set All data is enumerated and sent once and ends.
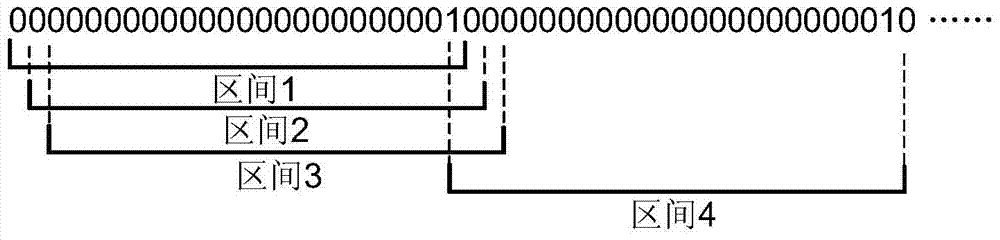
[0015] Since the decoded device receives a bit of binary data every time, it will combine the bit data with the latest 23-bit data received before to form a new 24-bit number, and c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com