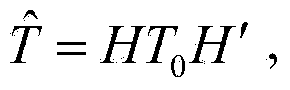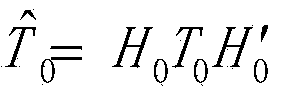Security multicast communication method based on chaotic neural network
A neural network and secure multicast technology, applied in the field of information security, can solve problems such as application limitations of multicast communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be further described below with reference to the accompanying drawings and specific embodiments.
[0018] A method for secure multicast communication based on chaotic neural network: the symmetric cryptographic algorithm based on chaotic neural network and the centralized group key management protocol LKH are combined and applied to multicast communication;
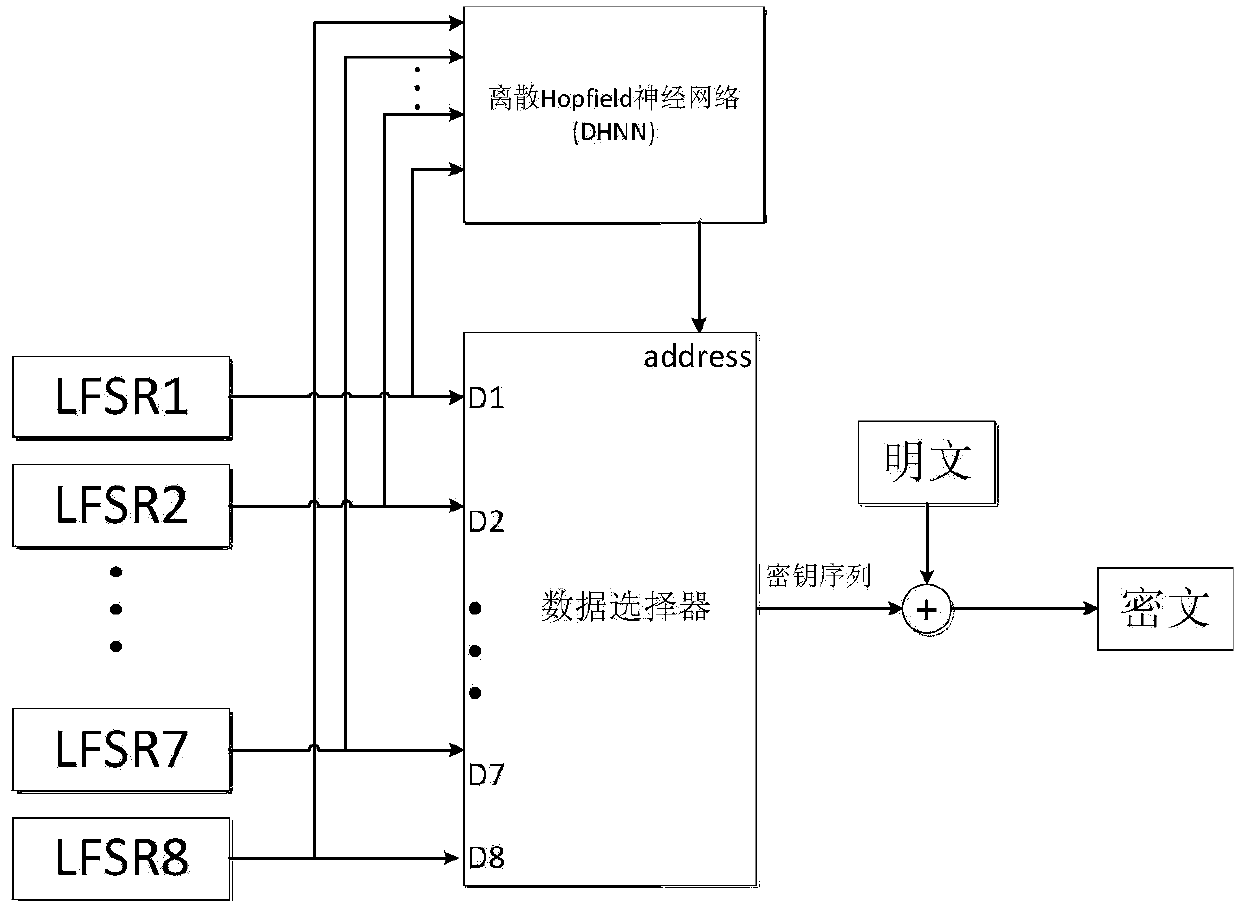
[0019] The chaotic neural network refers to the introduction of chaos into the neural network, so that the artificial neural network has rich nonlinear dynamic characteristics and high computational complexity, and many neural network models can achieve chaotic characteristics, such as improved discrete with chaotic characteristics. Hopfield neural network; the symmetric cryptographic algorithm of the chaotic neural network uses the output of the parallel LFSR as the input of the discrete Hopfield neural network with chaotic characteristics, and uses the nonlinear dynamic characteristics a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com