A vulnerability detection method and system for Ponzi schemes in smart contracts
A smart contract and vulnerability detection technology, applied in data processing applications, instruments, calculations, etc., can solve problems such as fast update frequency, difficulty in supporting contract operation, and investors coming from, and achieve excellent detection accuracy and timeliness. The effect of fast update frequency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] In order to facilitate the understanding and implementation of the technical means and effect of the present invention by those of ordinary skill in the art, the present invention will be further described in detail below with reference to the embodiments and accompanying drawings. It should be understood that the embodiments described herein are only used to illustrate and explain the present invention, but not to limit the present invention.
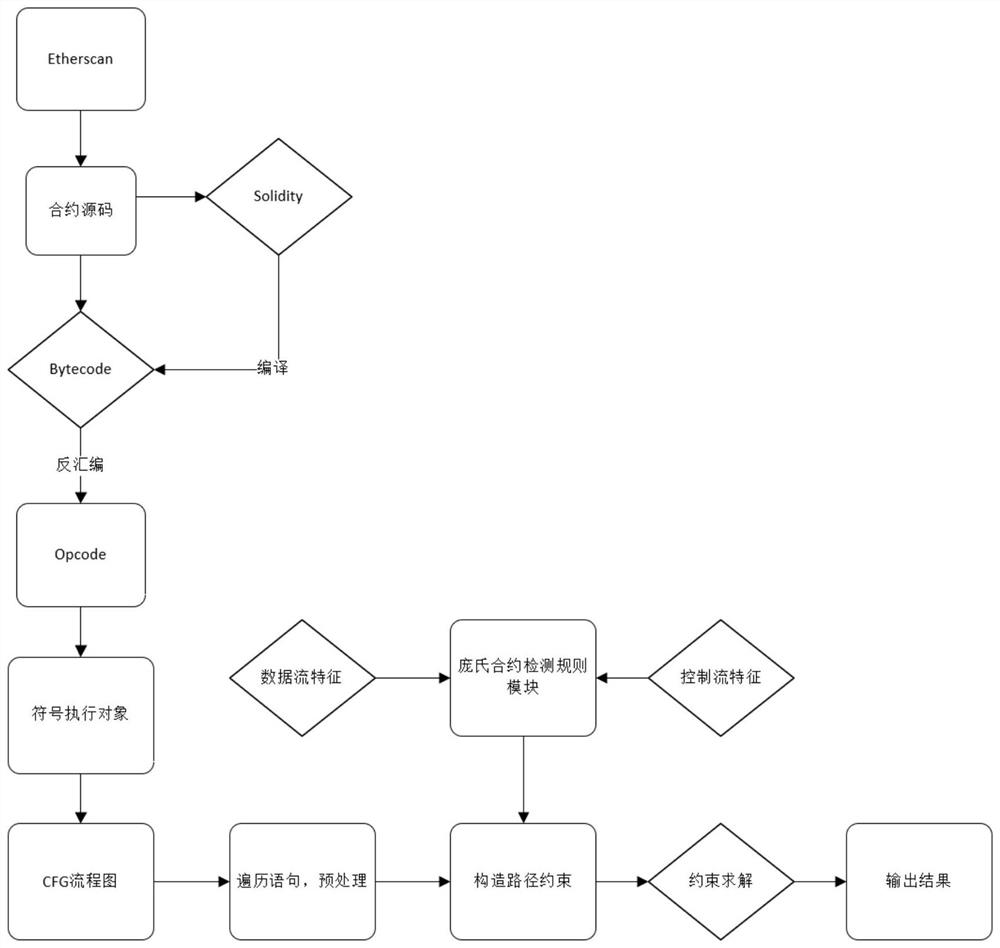
[0072] see figure 1 , the present invention provides a vulnerability detection method for Ponzi schemes in smart contracts, comprising the following steps:
[0073] Step 1: Obtain the source code of the smart contract. If the source code is bytecode, disassemble it into bytecode Opcode; if the source code is Solidity, compile it in the remix IDE to generate bytecode, and then reverse the bytecode. Assemble to generate bytecode Opcode;
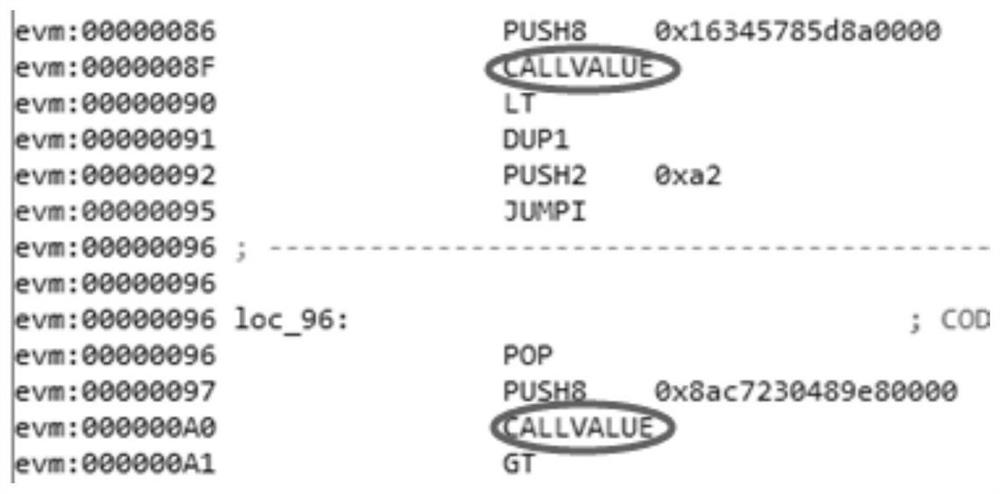
[0074] Step 2: Use the Ethereum virtual machine EVM to split the bytecode, and split the cr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com