PMIPv6 network bidirectional access authentication system and method based on classification identity signature
A technology of identity signature and two-way access, which is applied in network data management, electrical components, wireless communication, etc., can solve the problems of poor handover authentication, low authentication efficiency, and large communication delay, and solve the problem of key management, The effect of improving certification efficiency and reducing certification time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
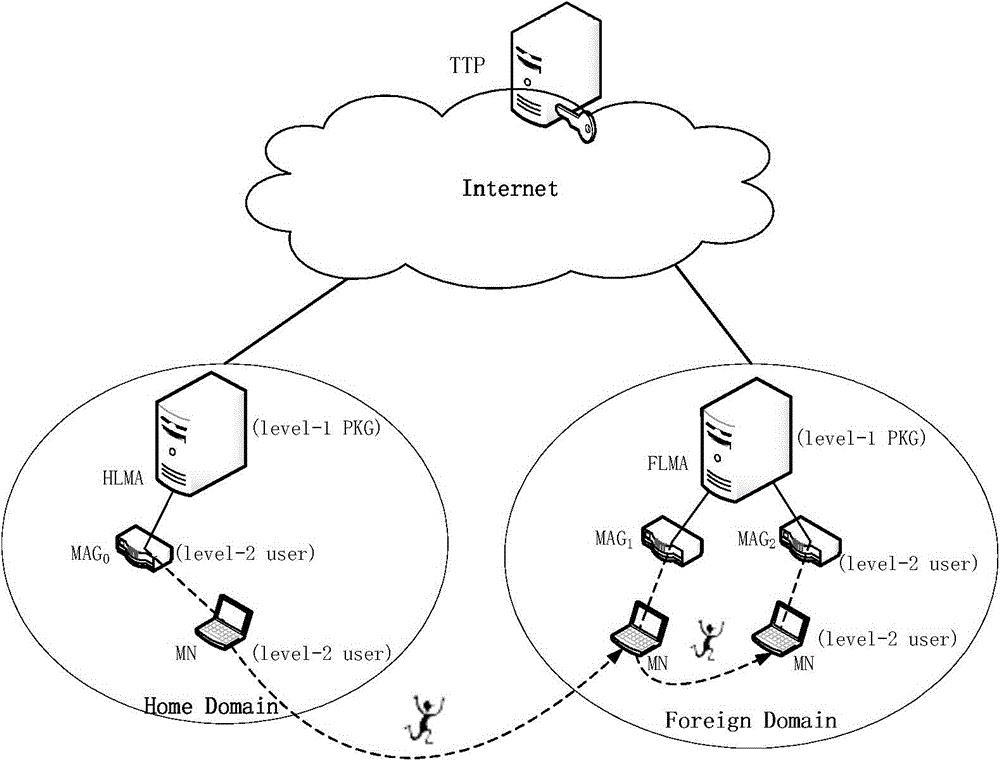
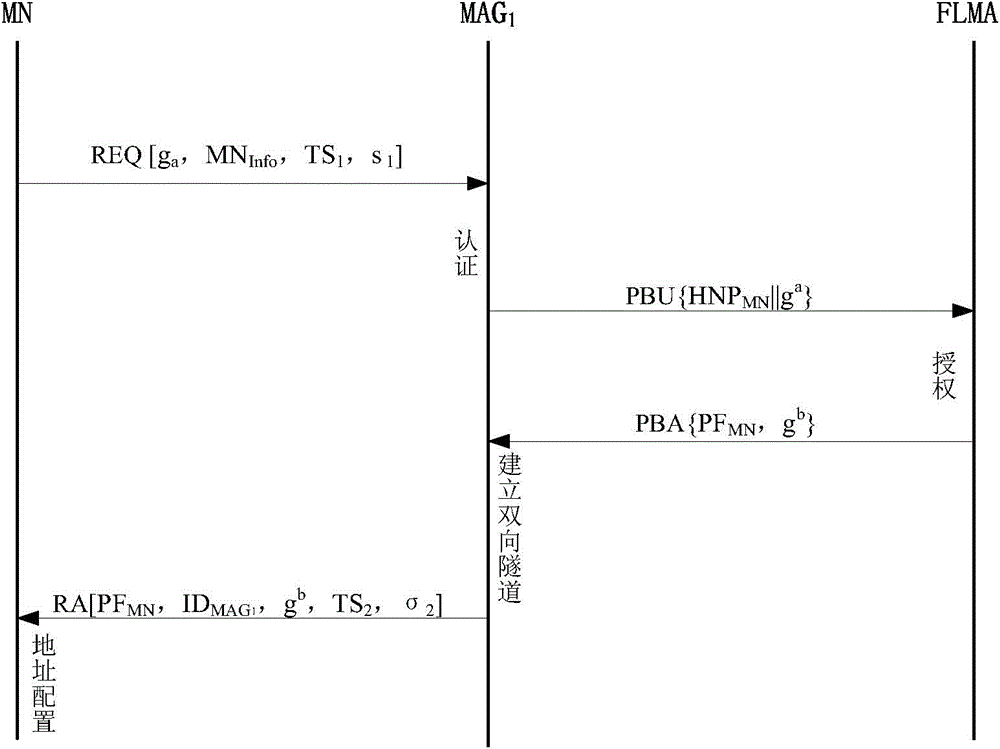
[0059] In this embodiment, the hierarchical identity signature-based PMIPv6 network two-way access authentication system and method are applied to a wireless local area network access authentication link. In the implementation process, the hierarchical identity-based signature technology is used to sign the relevant messages of the communication, and the HMAC operation is performed on the messages with the pre-negotiated key when switching authentication.
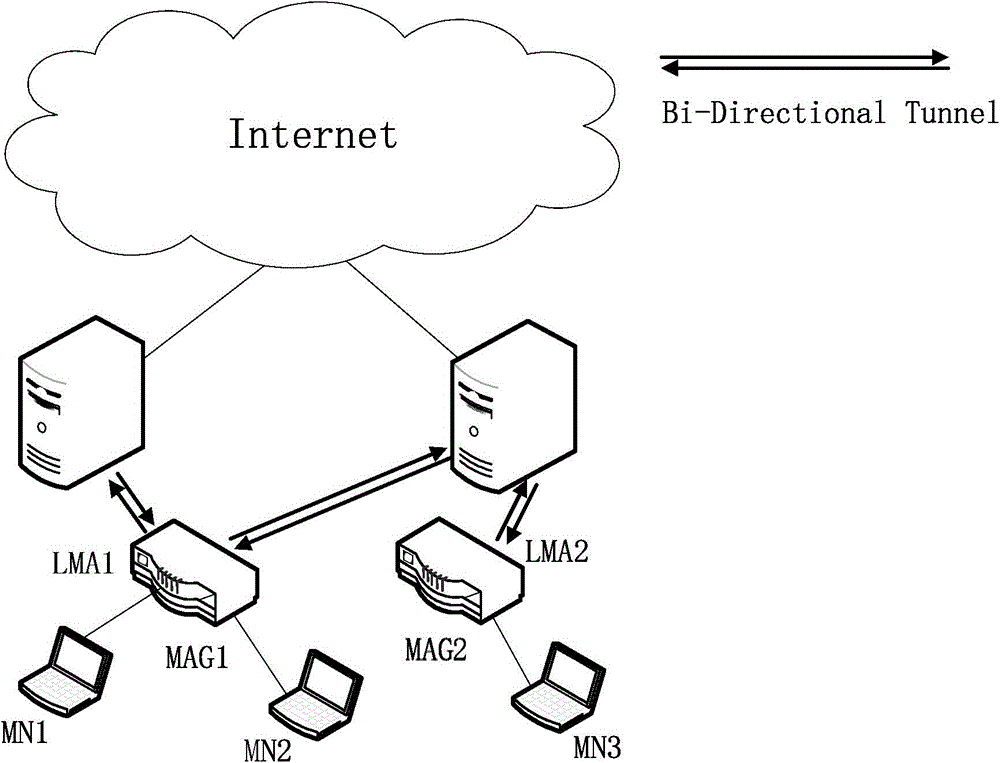
[0060] Such as figure 1 As shown, two new functional entities have been introduced into the PMIPv6 network - Local Mobility Anchor (Local Mobility Anchor, LMA) and Mobile Access Gateway (Mobile Access Gateway, MAG).
[0061] The local mobility anchor is the home agent of the mobile node in the PMIPv6 network. It is used to manage the network connection status of the mobile n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com