Method and system for realizing trusted path of mobile communication intelligent terminal
A smart terminal and mobile communication technology, applied in the field of mobile communication, can solve problems such as few physical buttons and inability to fully protect user account and password leaks, and achieve the effect of monitoring system status and protecting user information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
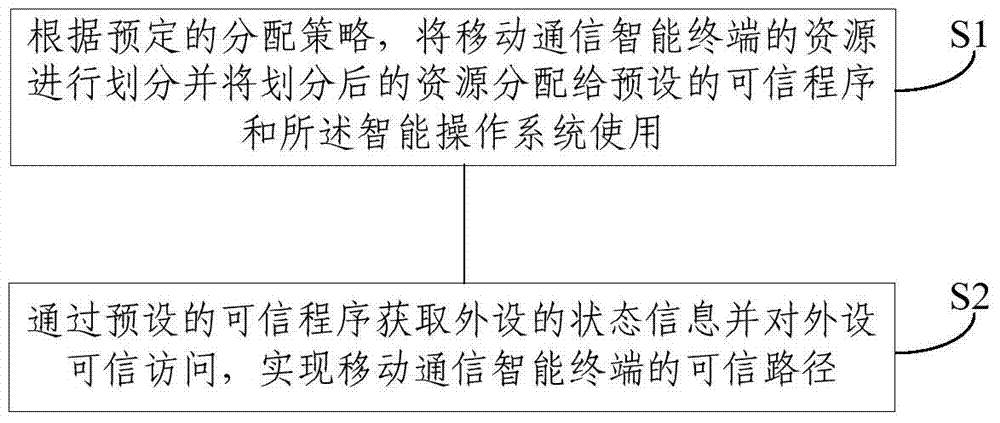
[0038] This embodiment discloses a method for realizing a trusted path of a mobile communication intelligent terminal, such as figure 1 As shown, the method includes:
[0039] S1. According to a predetermined allocation strategy, divide the resources of the mobile communication intelligent terminal and allocate the divided resources to the preset trusted program and the intelligent operating system, so as to realize the resource isolation of the mobile communication intelligent terminal; trusted The resources of the program and the intelligent operating system are separated, and the two cannot access each other;
[0040] S2. Obtain the status information of the peripheral device through the preset trusted program and access the peripheral device trustedly, so as to realize the trusted path of the mobile communication intelligent terminal.
[0041] Preferably, the method further includes:
[0042] S3. Authenticate the user password and the smart operating system of the mobile...
Embodiment 2
[0052] This embodiment discloses a method for realizing a trusted path of an intelligent mobile communication terminal, the method including:
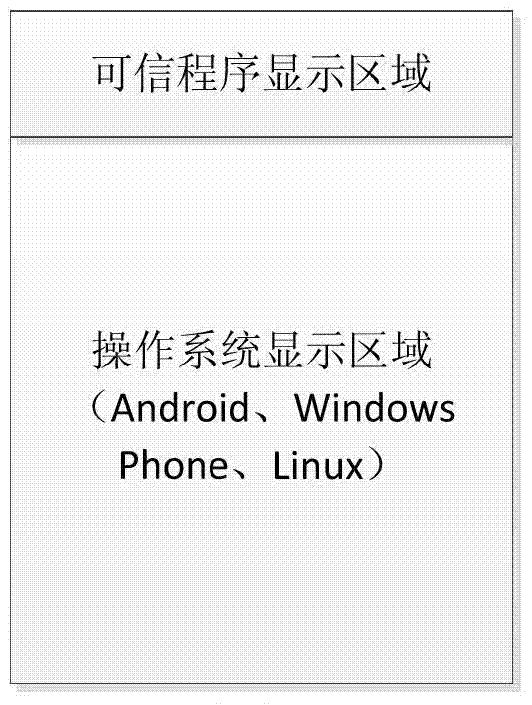
[0053] S1. According to a predetermined allocation strategy, divide the display touch screen of the smart terminal into different areas to obtain different areas of the display touch screen and assign the divided different areas of the display touch screen to the preset trusted program and the smart operating system for use, Such as figure 2 shown. The trusted program and the Android smart operating system can only access the specific screen resources assigned by the resource management framework, and receive information input by the user on the corresponding touch screen area. Both the trusted program and the Android smart operating system cannot directly access each other's screen resources, nor can they obtain the user's input information in the other's area.
[0054] S2. Obtain the status information of the peripheral device thr...
Embodiment 3
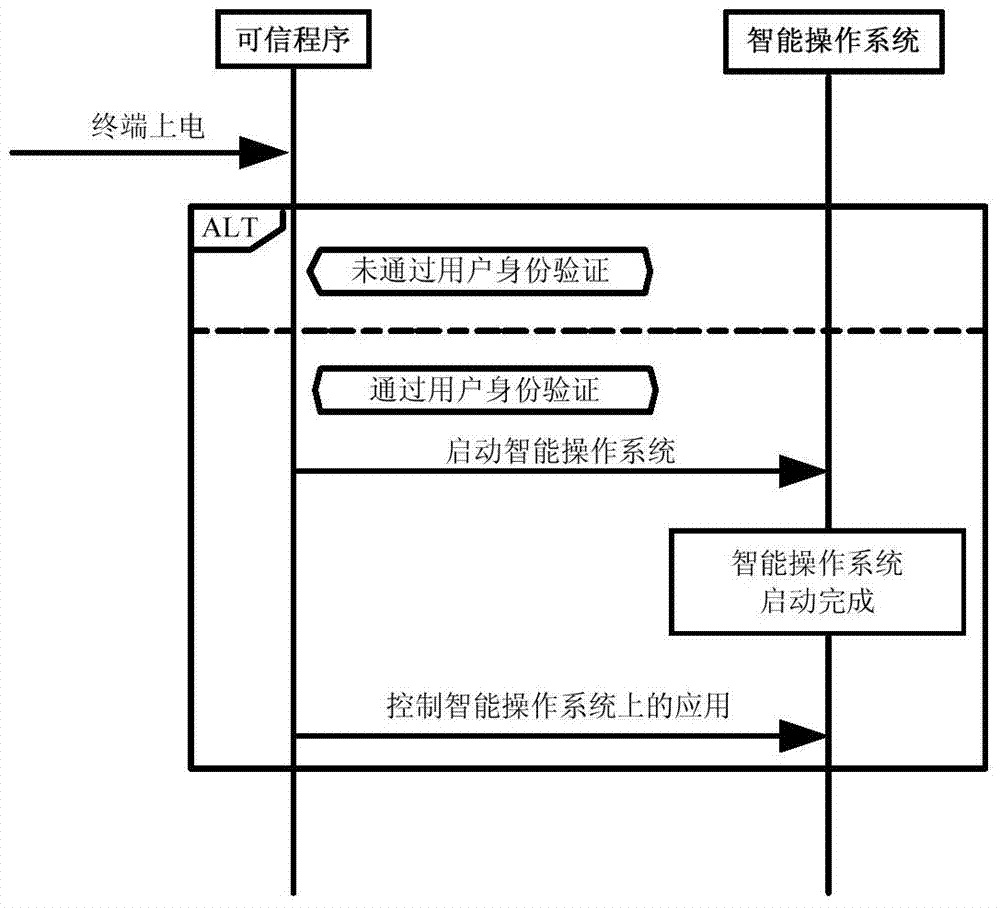
[0064] This embodiment discloses a system for realizing a trusted path of a mobile communication intelligent terminal, such as Figure 4 As shown, the system includes:
[0065] The resource division and allocation module is used to divide the resources of the mobile communication intelligent terminal according to a predetermined allocation strategy and allocate the divided resources to the preset trusted program and the intelligent operating system for use;
[0066] The authentication and judgment module is used to authenticate the user password and the intelligent operating system of the mobile communication intelligent terminal through a preset trusted program, and judge whether to start the intelligent operating system of the mobile communication intelligent terminal according to the authentication situation;
[0067] The trusted path implementation module is used to obtain the status information of the peripheral device through a preset trusted program and to access the pe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com