Security isolation file transmission control method
A file transmission and security isolation technology, applied in transmission systems, electrical components, etc., can solve problems such as the inability to meet efficient and reliable two-way communication, lack of data two-way communication, and security isolation devices that cannot deploy application layer protocols, and improve work efficiency. , improve the quality of user experience, improve the effect of controllability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention is described in further detail below in conjunction with accompanying drawing:
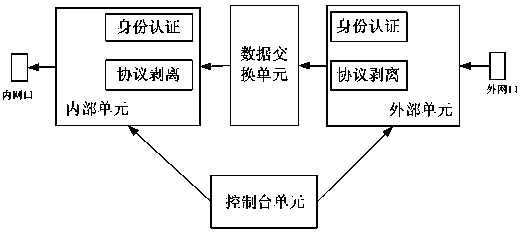
[0043] figure 1 It is a schematic diagram of a unidirectional network security isolation device in the prior art, which consists of four parts: a console unit, an internal unit, an external unit and a data exchange unit. Among them: the internal unit and the external unit are composed of an identity authentication unit and a protocol stripping unit, which are responsible for the interaction with the internal network and the external network; the data exchange unit is an intermediary unit not based on network transmission, and is responsible for the data exchange between the internal unit and the external unit; The console controls the configuration information of the internal unit and the external unit, and determines the security policy of the network isolation device. The one-way network security isolation device ensures that it is connected to one of the internal n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com