Safety authentication mechanism of remote password
A technology for authenticating passwords and remote devices, applied to electrical components, transmission systems, etc., can solve problems such as stealing and sending
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
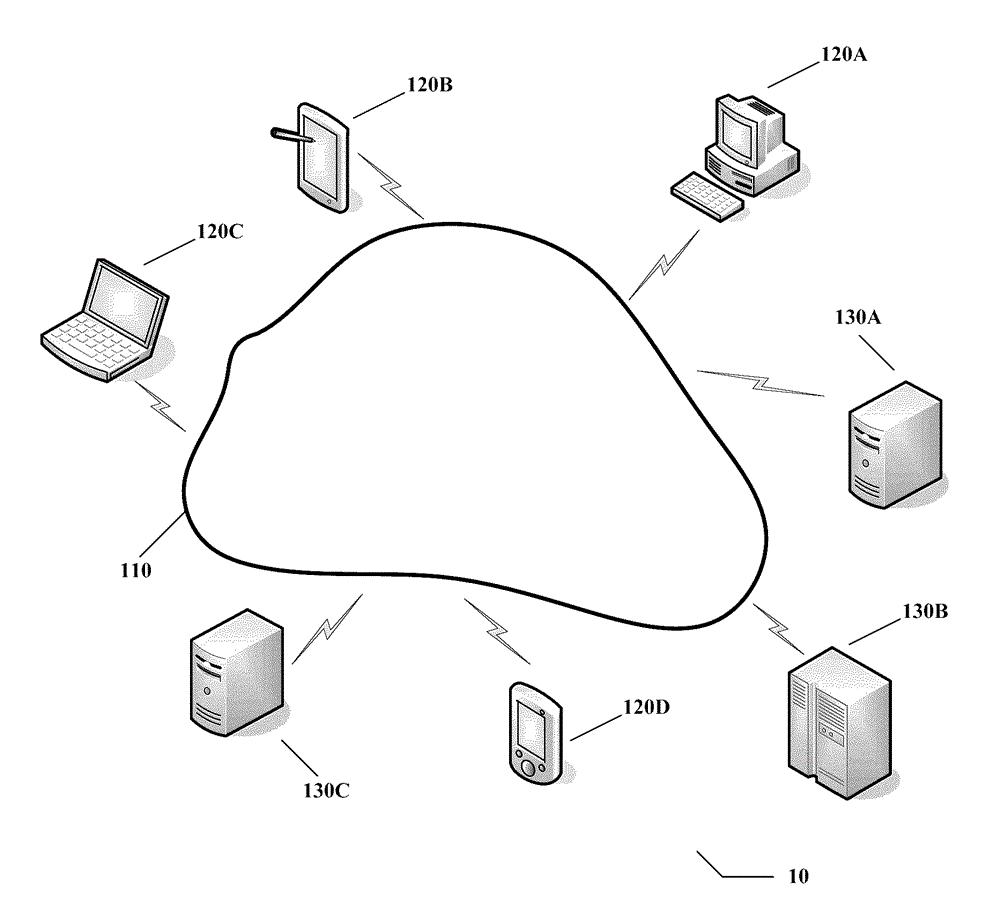
[0050] figure 1 A schematic diagram of a typical distributed processing environment. like figure 1 As shown, the distributed processing environment 10 includes a network 110 (which may be, for example, a wide area network, a metropolitan area network or a local area network), a plurality of terminals 120A, 120B, 120C, and 120D that access the network 110 in a wired or wireless manner (it should be understood that The number of terminals shown here is merely exemplary) and the plurality of servers 130A, 130B, and 130C (again, it should be understood that the number of servers shown here is only exemplary). The above-mentioned distributed processing environment can be based on client / server architecture, wherein the logical functions of the application system include display logic, application logic and data processing logic, wherein the display logic and application logic are implemented on the client side and the data processing logic is implemented on the server side. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com