IPv6 network-orientated detection method for counterfeit source address messages
An IP address, ipv6 network technology, applied in electrical components, transmission systems, etc., can solve problems such as denial of service attacks, endangering Internet security, and man-in-the-middle attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
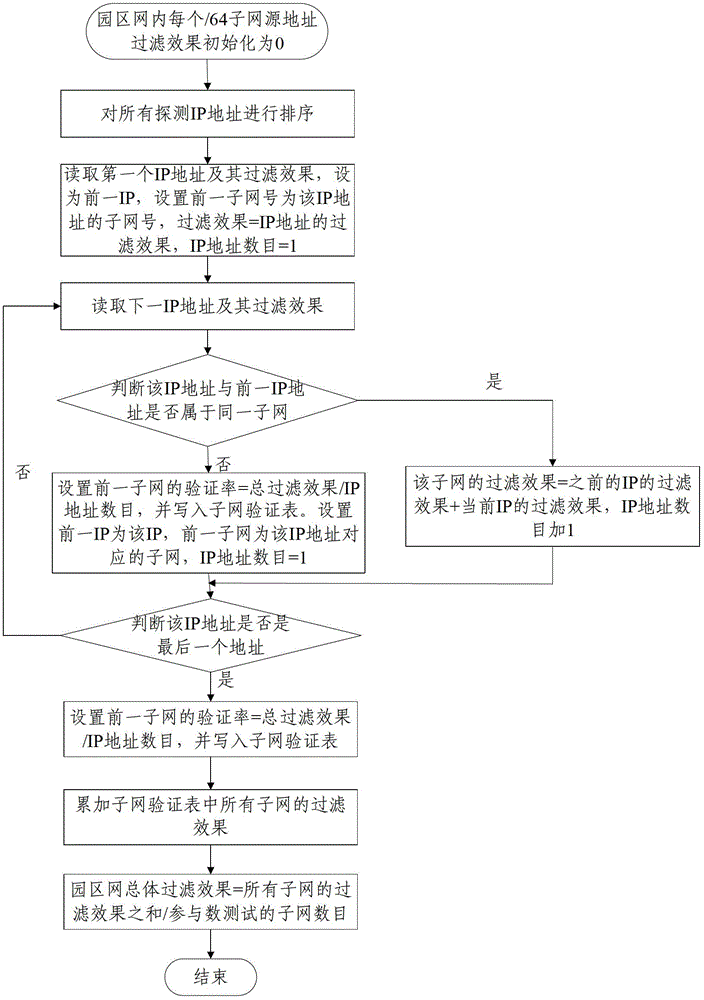
[0062] The embodiment of the present invention provides an IPv6 network-oriented method for detecting fake source address packets, and the steps are as follows: figure 1 As shown, it specifically includes the following steps:
[0063] Step S1: the client sends a normal packet to the server. The normal message here is for testing, so you can send a simple "hello" message to the server.
[0064] Step S2: the server sends a response command to the client. The server instructs the client to send a normal message with the specified source port and destination port by responding to the command.
[0065] Step S3: The client sends M normal packets to the server according to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com