Security information interaction system, device and method
A security information and interactive system technology, applied in the payment system, payment system structure, discount/reward, etc., can solve the problems of cumbersome operation, time consumption and high cost, and achieve the effect of simple operation, time consumption and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
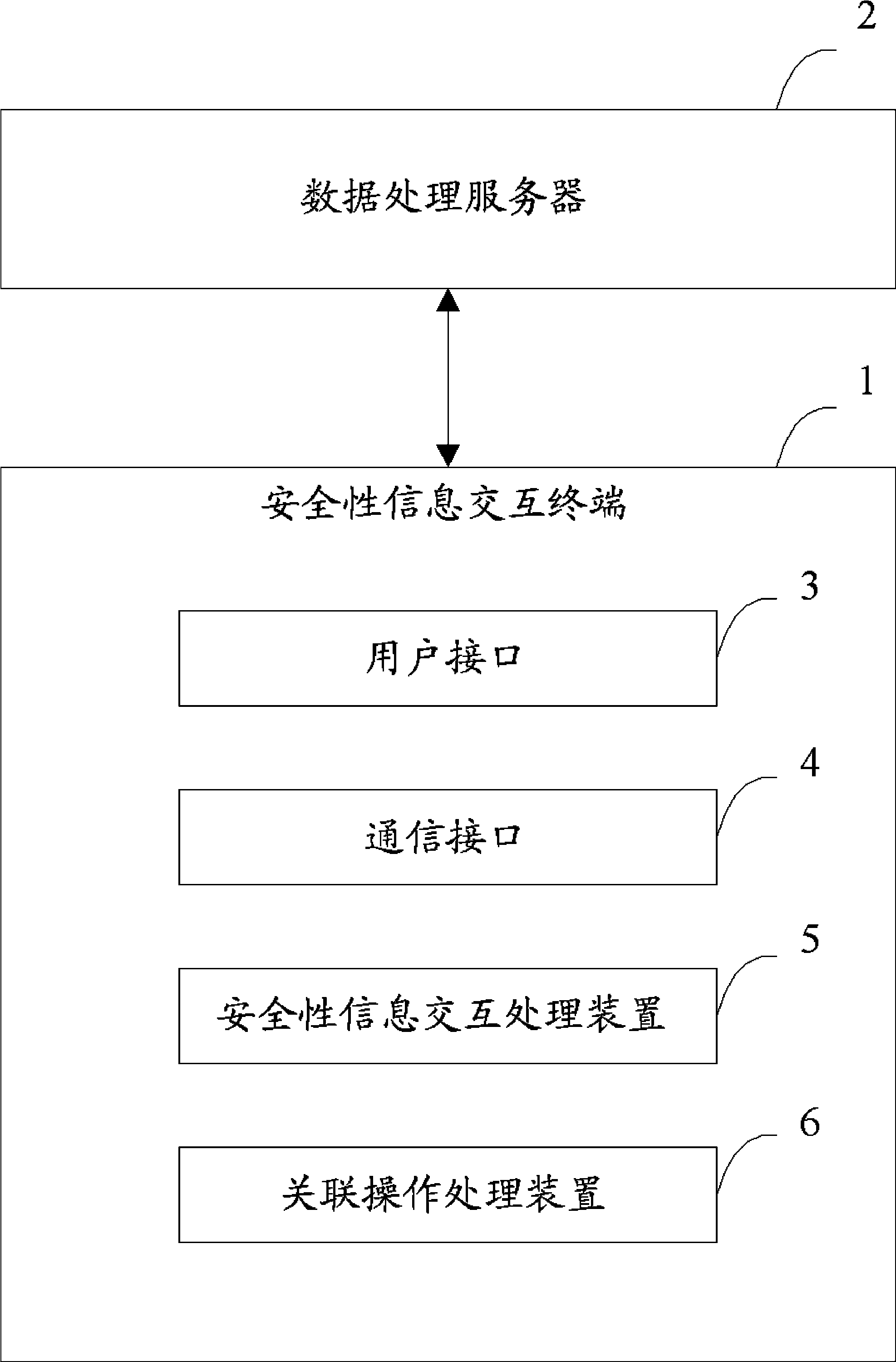
[0037] figure 1 is a schematic structural diagram of a security information interaction system according to an embodiment of the present invention. Such as figure 1 As shown, the security information interaction system disclosed in the present invention includes a security information interaction terminal 1 and a data processing server 2 . Wherein, the security information interaction terminal 1 (such as a POS machine) completes the security information interaction process based on the security information interaction instruction from the user and through data interaction with an external security carrier (such as a bank card) and a data processing server 2 ( For example, a payment transaction operation), and automatically execute operations associated with the security information interaction process after the security information interaction process is completed. The data processing server 2 completes the security information interaction process and the operations associat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com