Security architecture system for realizing software definition security and security controller
A technology for security controllers and network controllers, applied in transmission systems, electrical components, etc., which can solve problems such as inapplicability of security products, blurring and virtualization of network boundaries, and complex anti-DDoS attack strategies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The safety controller and the safety framework system provided with the safety controller provided by the embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
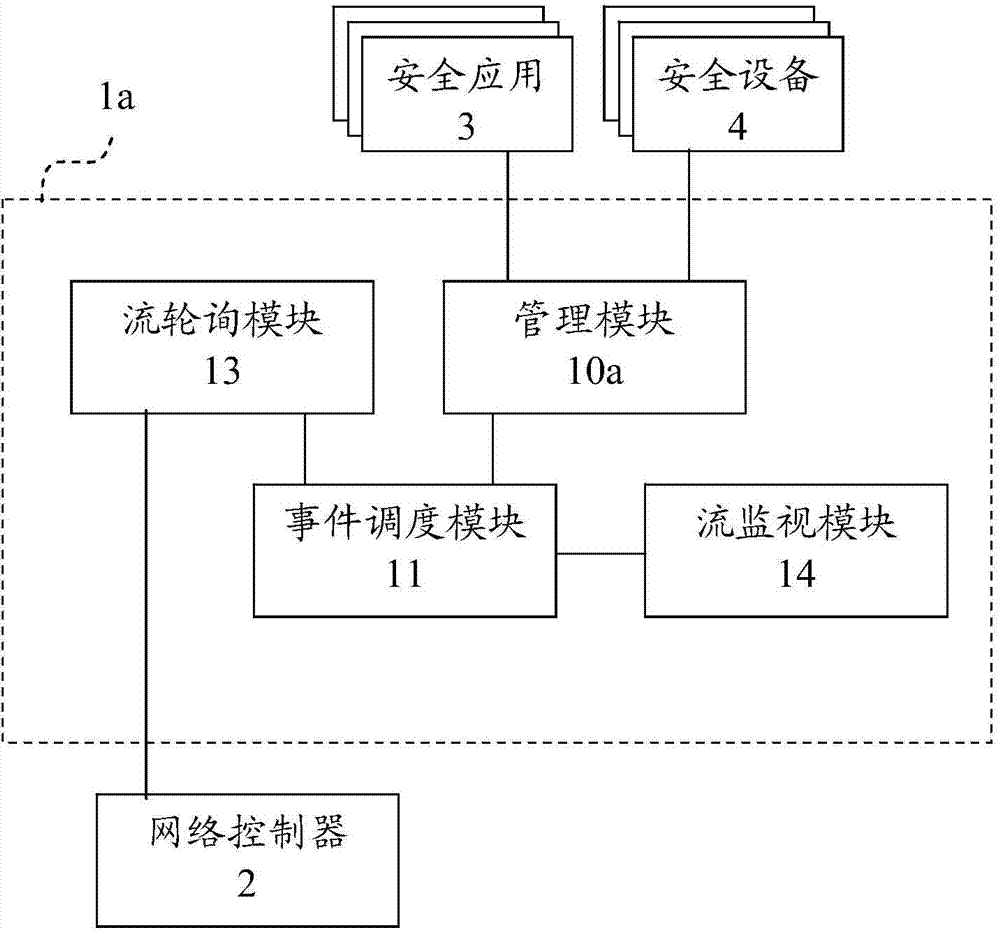
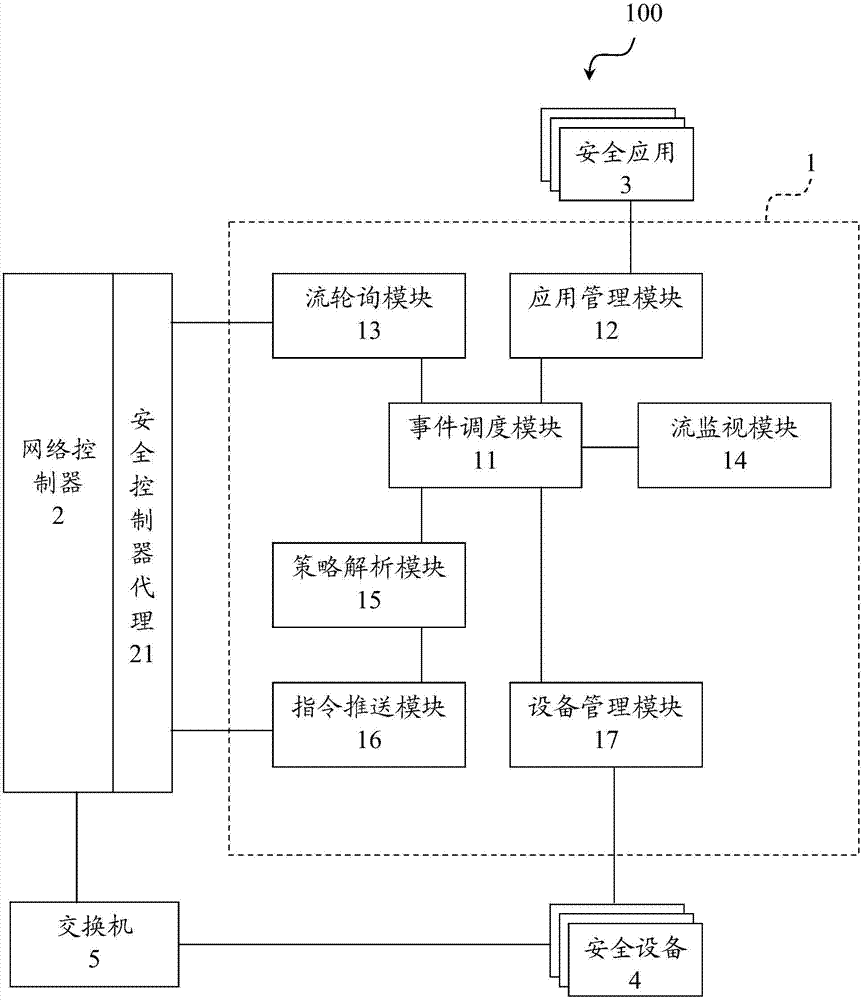
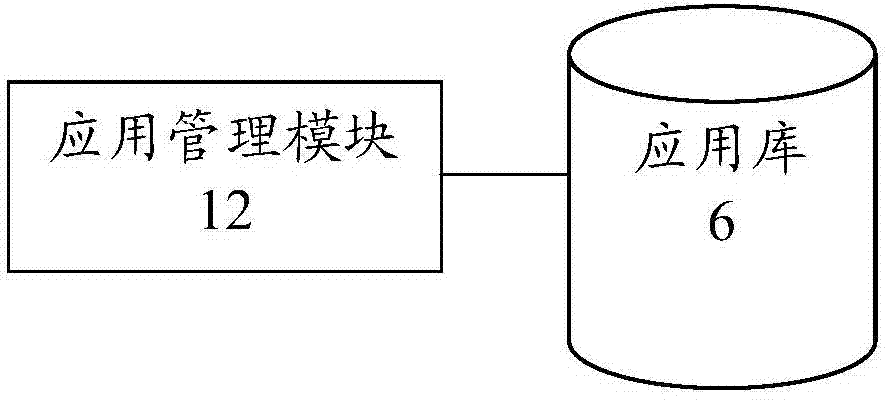
[0028] Please refer to figure 1 , a security controller 1 a of the present invention, which includes a management module 10 a, an event scheduling module 11 , a stream polling module 13 and a stream monitoring module 14 . The management module 10a provides at least one security device 4 or at least one security application 3 for registration. The event scheduling module 11 generates a subscription trigger condition according to the at least one registered security application. The stream polling module 13 polls a network controller 2 to obtain data streams. The flow monitoring module 14 detects the acquired data flow according to the subscription trigger condition. The event scheduling module 11 generates an execution policy event according to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com