User behavior based cross-cloud authentication service method
A service method and cloud certification technology, which is applied in the field of cloud service security certification, can solve problems such as hazards and trust evaluation results that are not stable and representative, and achieve the effect of improving security assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention is described in detail below in conjunction with accompanying drawing
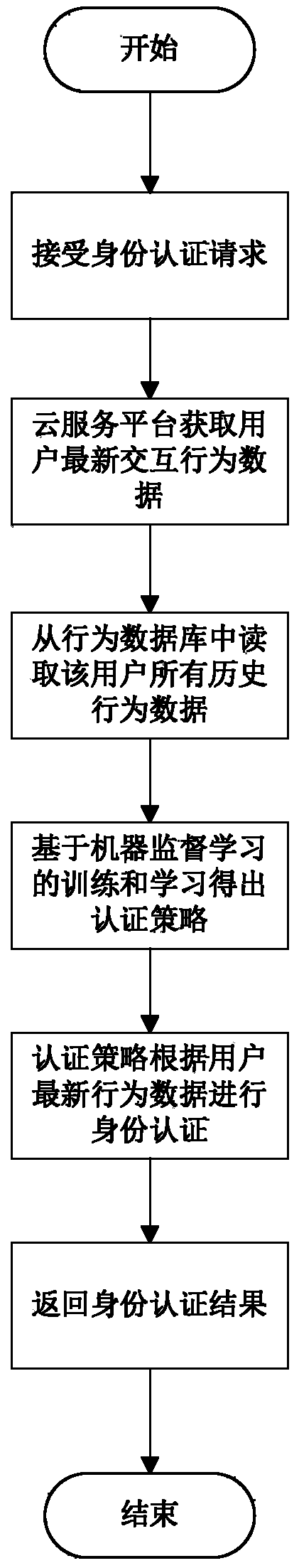
[0040] like figure 1 As shown, the whole authentication process of the user behavior-based identity authentication service of the present invention is as follows:
[0041] (1) Accept identity authentication requests by providing user authentication interfaces for each cloud service platform;
[0042](2) Obtain the latest behavior data of the user, and send a request to the cloud service platform to collect the latest behavior data of the specified user, and each cloud service platform analyzes the user's latest interactive behavior and extracts its real-time behavior data and uses it as the legality judgment of the user's identity According to, the real-time behavior data of the user is pushed to the user authentication interface module, and the interface analyzes and processes the received user behavior data;
[0043] (3) The user authentication module classifies and organiz...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com