Secret key processing method and device
A technology for processing devices and keys, applied in security devices, electrical components, wireless communications, etc., can solve the problems of consuming AC or fat AP performance and network resources, and achieve cost-effective results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
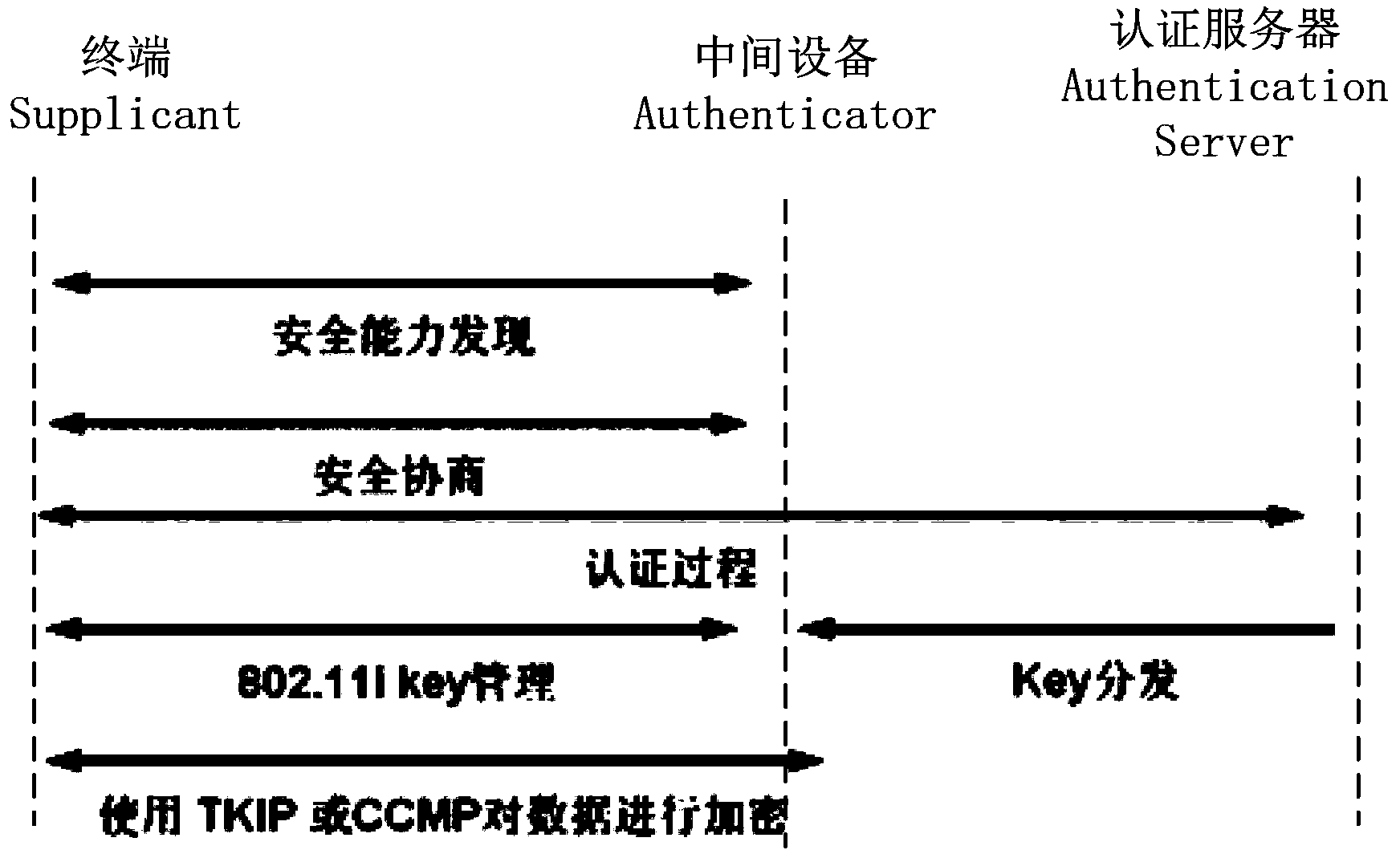
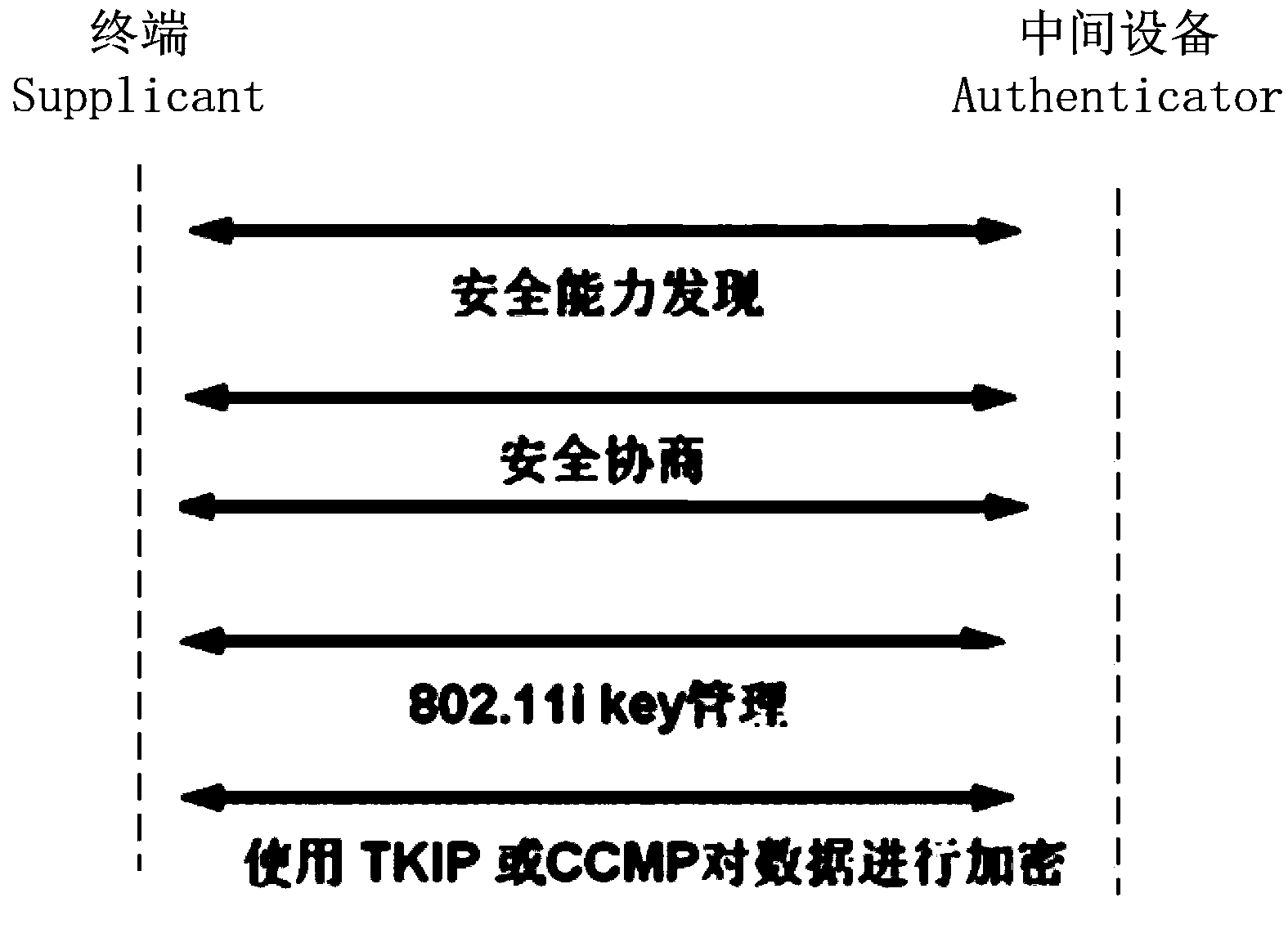
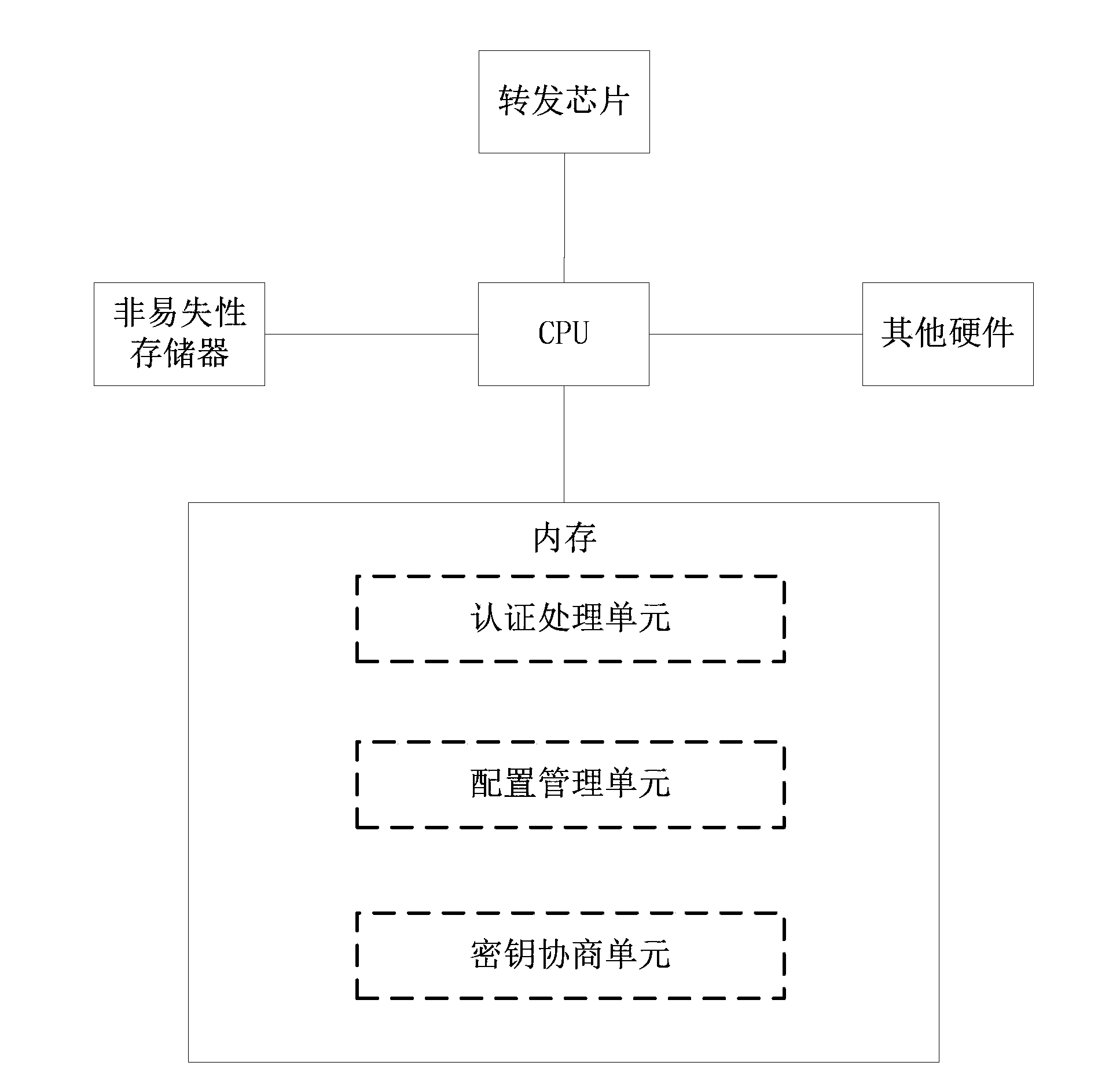
[0023] In the traditional WPA-PSK (Wi-Fi Protected Access Pre Shared Key) technology, users in a wireless local area network (WLAN) share a preset key to negotiate the encryption key used in the subsequent data transmission process, If a user's shared key is leaked, the security of the entire network will deteriorate as a whole. The integration of WPA-PSK and Portal authentication solves this problem. The key is no longer shared, but each user obtains it dynamically when the user approves it. This makes it possible for different users to have different keys. However, the Portal authentication process requires each wireless terminal (Station, STA) to be assigned an IP address first. In this way, even if the user Portal authentication fails, the IP address will be consumed as a relatively scarce network resource. In addition, because the Portal authentication process is to intercept the user's TCP request and implement it through HTTP redirection, these tasks are usually complet...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com