A VPN multi-party connection method based on ipsec
A connection method and IP address technology, applied in the communication field, can solve problems such as difficult adaptation, video service delay, increased operation and maintenance costs, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
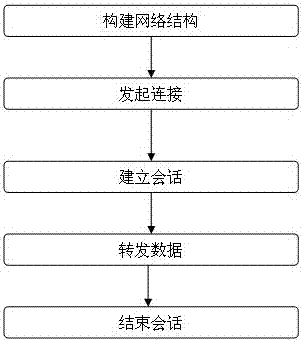
[0032] Embodiment 1 of the present invention provides a kind of VPN connection method based on IPSec, it is characterized in that, comprises the following steps:
[0033] Step 202, building a network structure, specifically including:
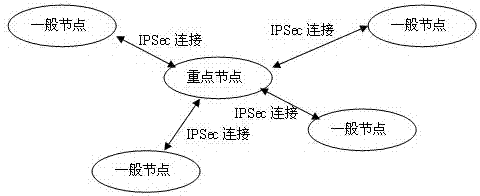
[0034] Step 2021, classify the nodes that may need to be connected, and divide the nodes into a key node and several general nodes according to specific needs;
[0035] Step 2022, determine the affiliation relationship between key nodes and general nodes, and the key nodes are subordinate to several general nodes;
[0036] Step 2023, configure a node relationship routing table on the key node, the table at least includes the ID, IP address and MAC address of the key node, and the ID, IP address and MAC address of the general nodes subordinate to the key node;
[0037] Step 2024, configure a node relationship routing table on all general nodes, the table at least includes the general node's own ID, IP address and MAC address, and the key node's...
Embodiment 2
[0052] Before the step 2041, it also includes:
[0053] Step 2040, the first general node receives the session request initiated by the user, and judges whether the session to be connected is a two-party session or a multi-party session, if it is a two-party session, use the general IPSec VPN connection process to connect;
[0054] Those of ordinary skill in the art can understand that all or part of the processes in the method of the above-mentioned embodiments can be completed by instructing related hardware through a host program. The program can be stored in a host-readable storage medium. The program During execution, it may include the processes of the embodiments of the above-mentioned methods. Wherein, the storage medium may be a magnetic disk, an optical disk, a read-only memory (Read-Only Memory, ROM) or a random access memory (Random Access Memory, RAM) and the like.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com