A usbkey security authentication system and security authentication method
A technology for security authentication and secure communication, applied in the USBKey security authentication system and security authentication field, which can solve problems such as security risks and information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
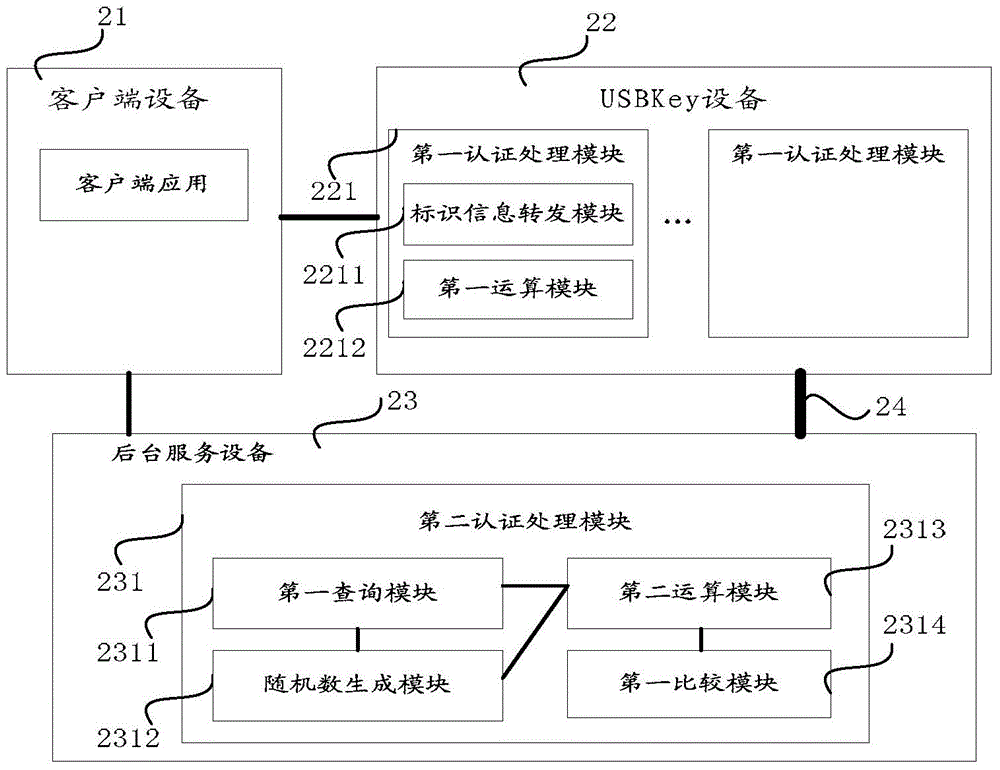
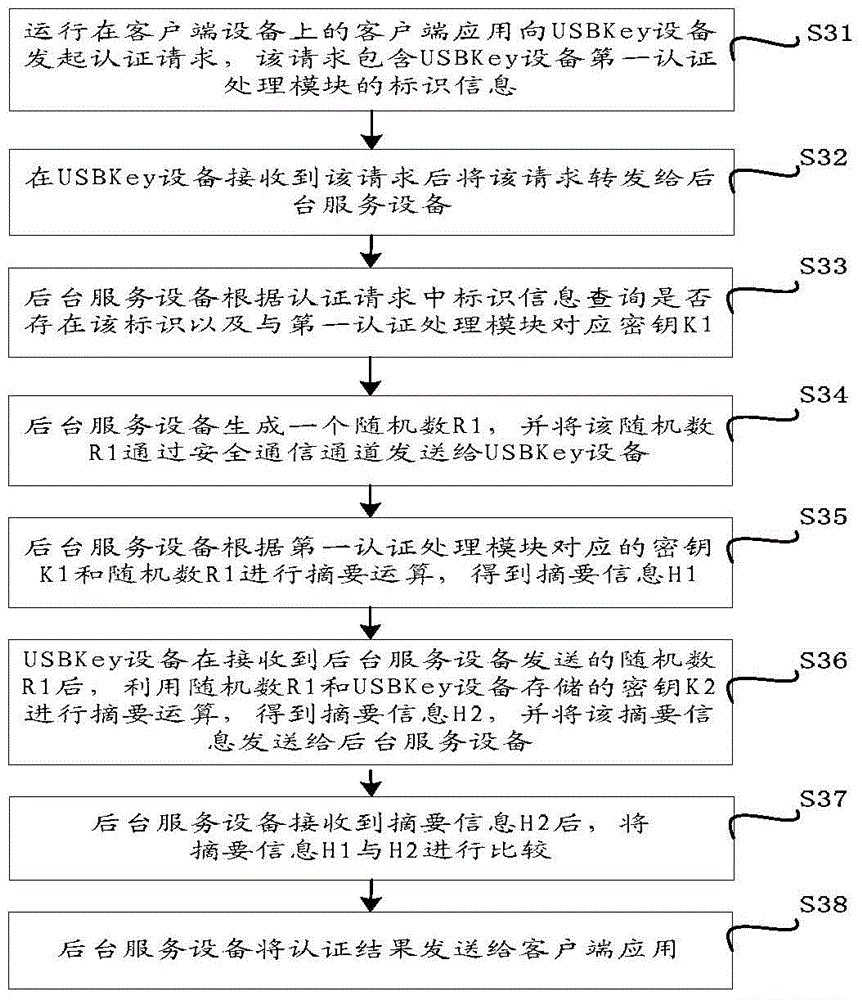
[0061] see figure 2 , which shows the structure of an embodiment of the USBKey security authentication system of the present application (Embodiment 1). The USBKey security authentication system of this embodiment includes: a client device 21, a USBKey device 22 and a background service device 23, and a secure communication channel 24 is established between the USBKey device 22 and the background service device 23, wherein:
[0062] The client device 21 has a first operating system, and a client application runs in the first operating system of the device. The client application can initiate an authentication request to the USBKey device, and can also receive the authentication result to implement authentication. In an embodiment, the authentication result may be sent by the USBKey device, or may be sent by the background service device, which depends to a certain extent on the currently used authentication mechanism, for example, if a "one-way" authentication mechanism is ad...
Embodiment 2
[0072] see Figure 4 , which shows the composition structure of another embodiment of the USBKey security authentication system of the present application (embodiment 2). The USBKey security authentication system of this embodiment includes: a client device 41, a USBKey device 42 and a background service device 43, and a secure communication channel 44 is established between the USBKey device 42 and the background service device 43, wherein:
[0073] The client device 41 has a first operating system, and a client application runs in the first operating system of the device. The client application can initiate an authentication request to the USBKey device, and can also receive the authentication result to implement authentication, similar to the foregoing embodiments Preferably, the authentication result may come from the USBKey device, or from the background service device.
[0074] The USBKey device 42 has a second operating system, the device may include at least one first...
Embodiment 3
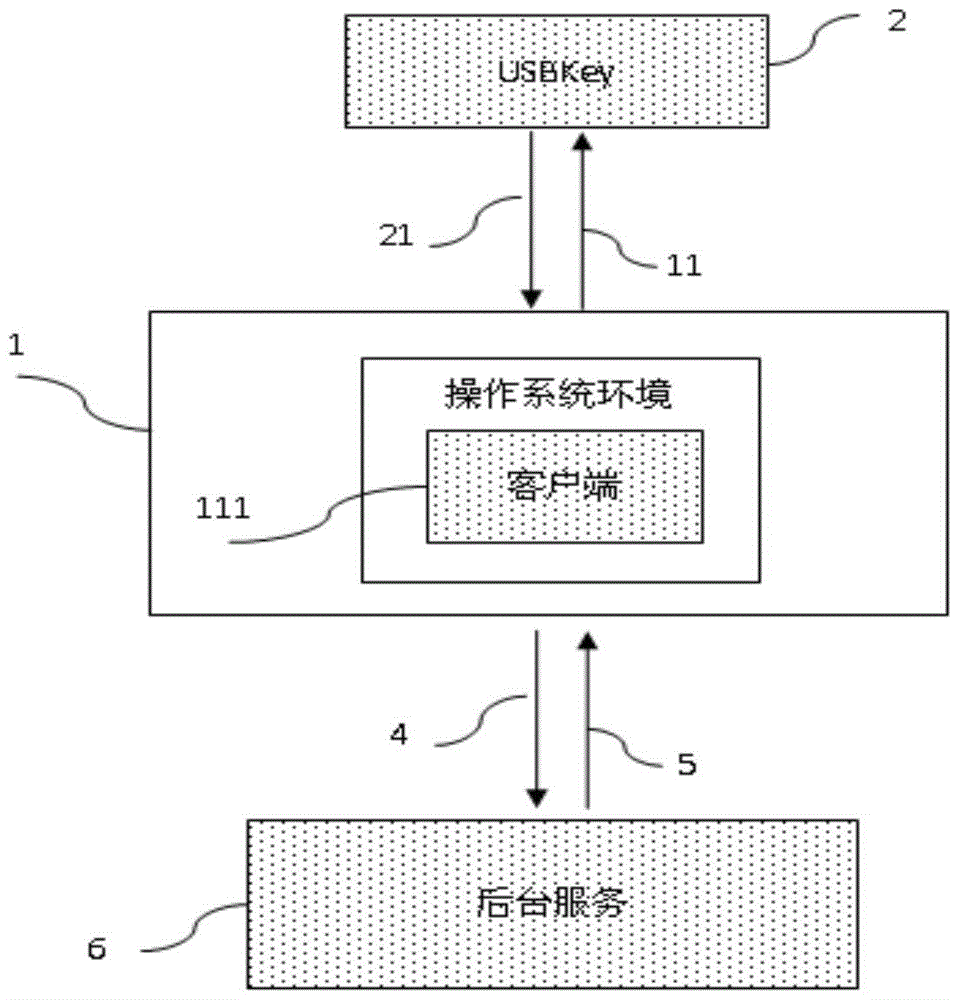
[0083] The above two embodiments both mention the client device and the USBKey device, and these two devices together with other devices constitute the USBKey security authentication system, and the positional relationship between the two devices is not particularly limited here. However, in some cases, clarifying the positional relationship between them may bring more technical effects. see Figure 8 , in this figure, the client device and the USBKey device are integrated into one device, which can appear as a smart device. In this integrated mode, the first operating system where the client device is located is isolated from the second operating system where the USBKey device is located, so that the environment where the client device is located is different from the environment where the USBKey device is located, For the sake of safety, this application sets the environment where the client device is located as a rich execution environment, which is a non-installation envi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com