Apparatus for security information interaction
A technology of security information and equipment, applied in the field of security information interaction equipment, can solve problems such as difficult proactive and thorough solutions, increased difficulty of application deployment, unfavorable promotion, etc., to reduce complexity, reduce deployment difficulty and Difficulty of management and effect of reducing maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The following introduces some of the possible embodiments of the present invention, which are intended to provide a basic understanding of the present invention, but are not intended to identify key or decisive elements of the present invention or limit the scope of protection. It is easy to understand that, according to the technical solution of the present invention, those skilled in the art may propose other alternative implementation manners without changing the essence and spirit of the present invention. Therefore, the following specific embodiments and drawings are only exemplary descriptions of the technical solution of the present invention, and should not be regarded as the entirety of the present invention or as a limitation or restriction on the technical solution of the present invention.
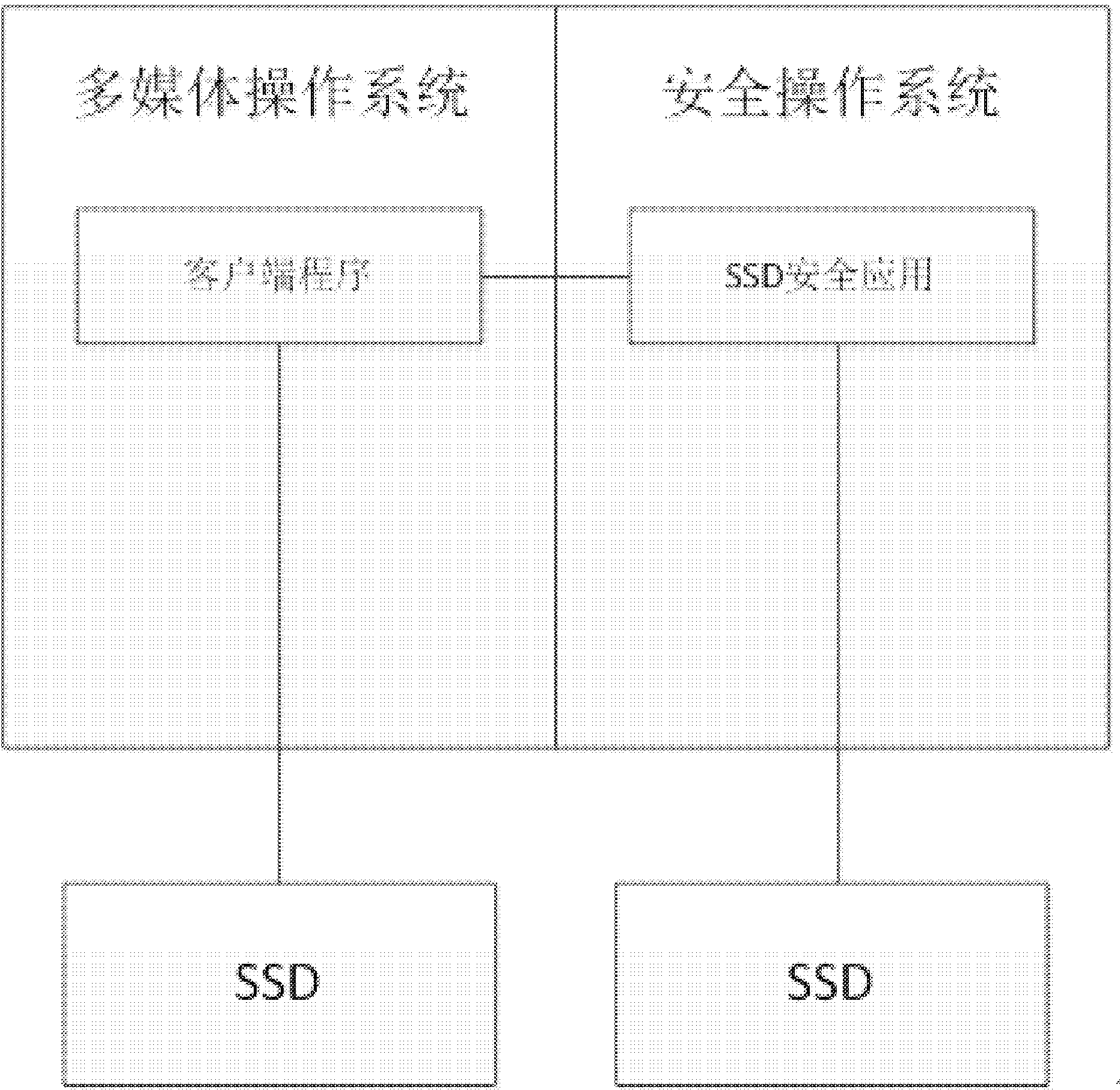
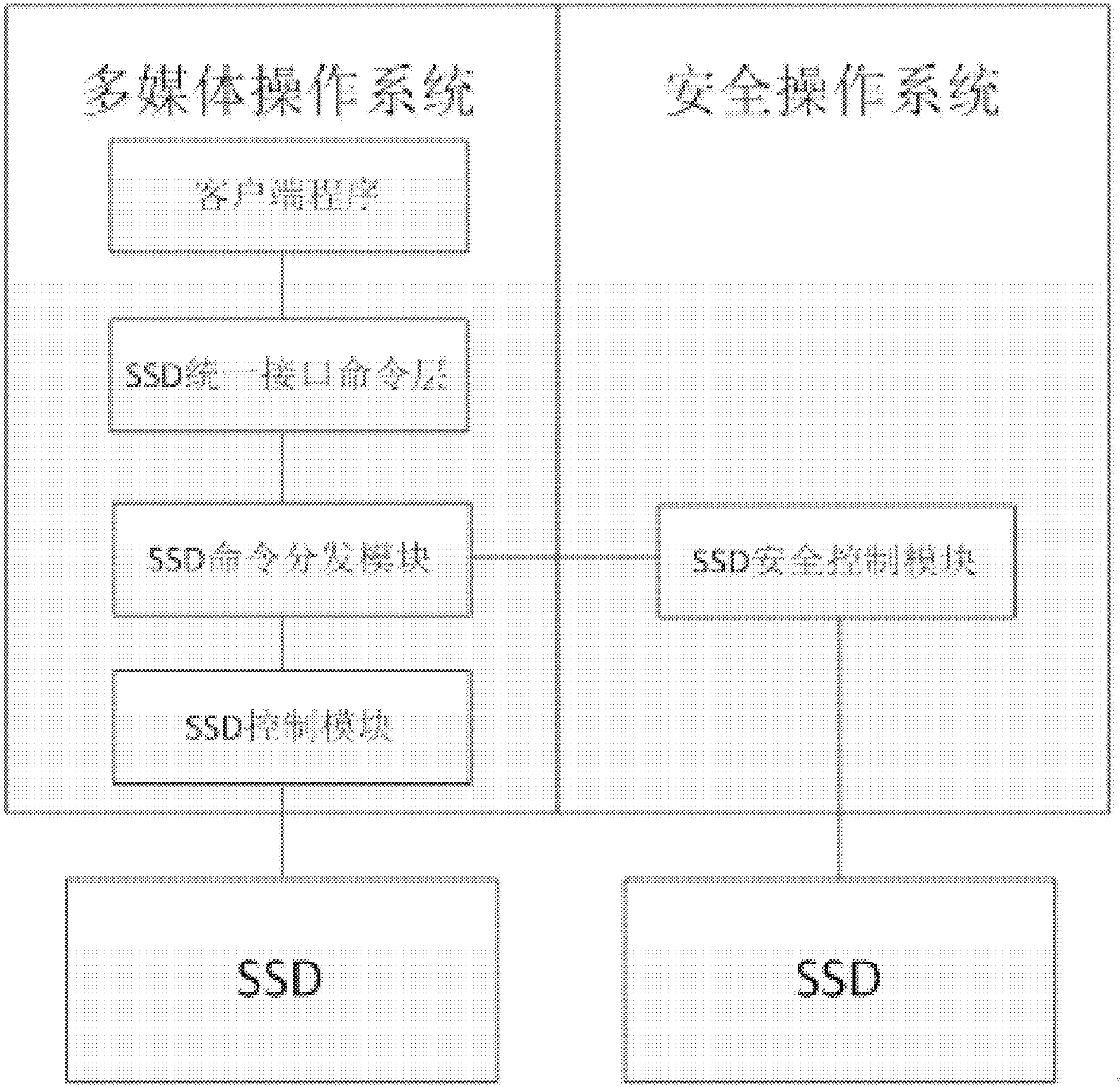
[0028] In the following and accompanying drawings, "REE" indicates a multimedia operating system running in normal mode, "TEE" indicates a secure operating system ope...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com