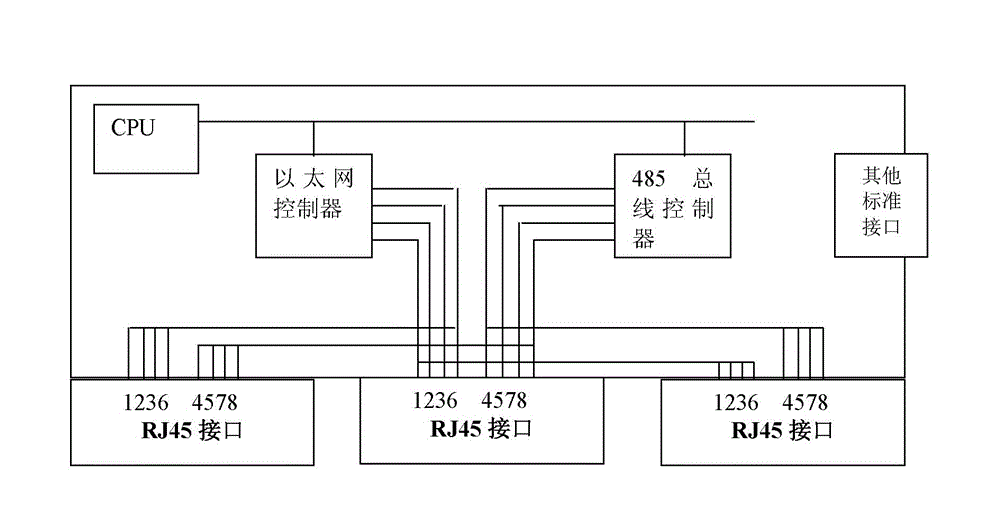
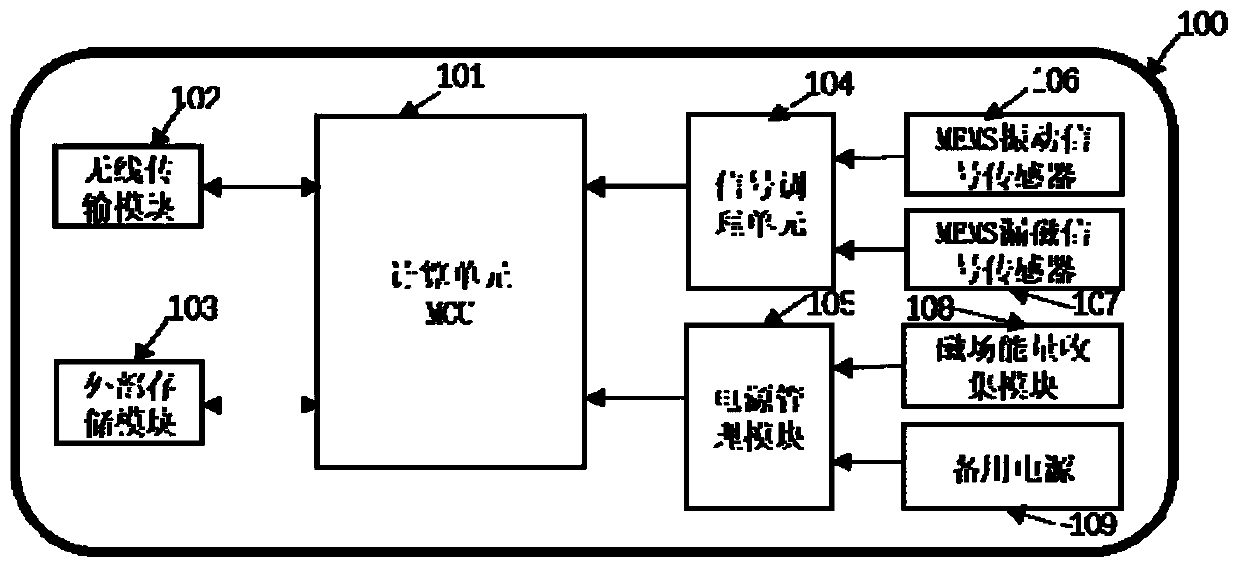
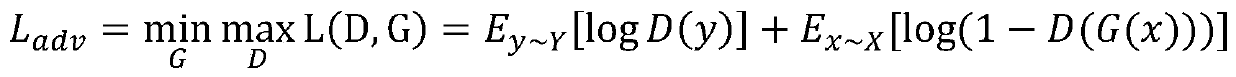Patents
Literature
280results about How to "Reduce the difficulty of deployment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
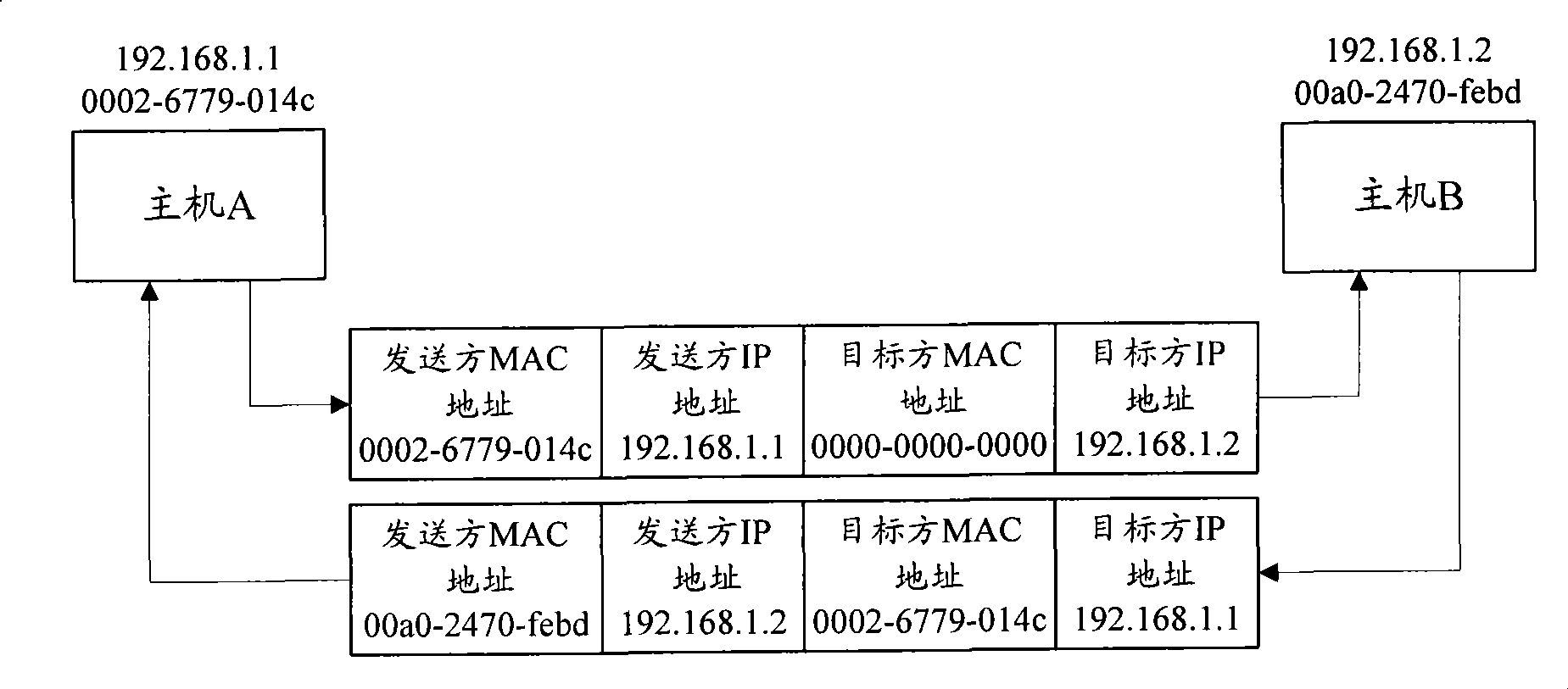
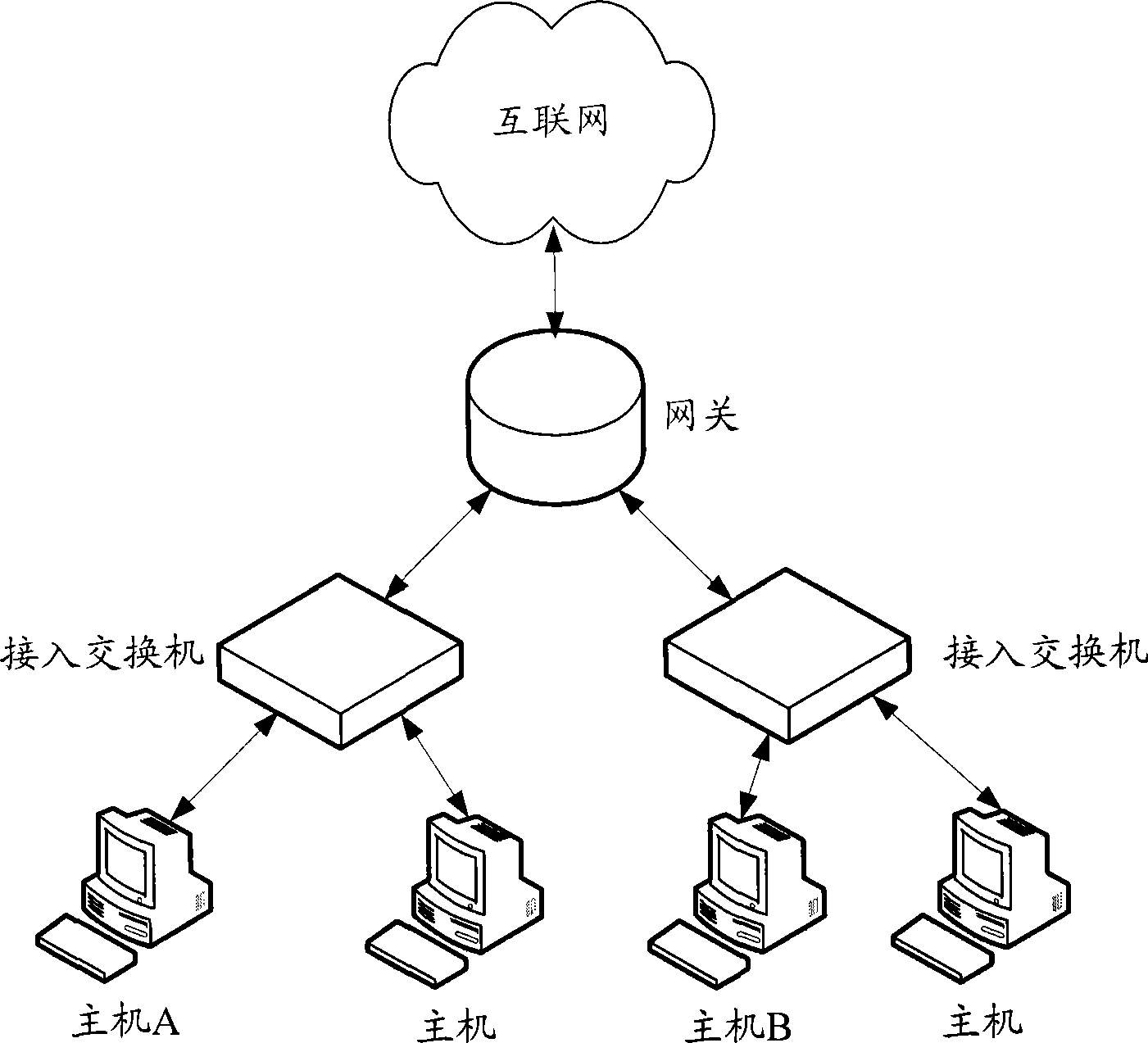
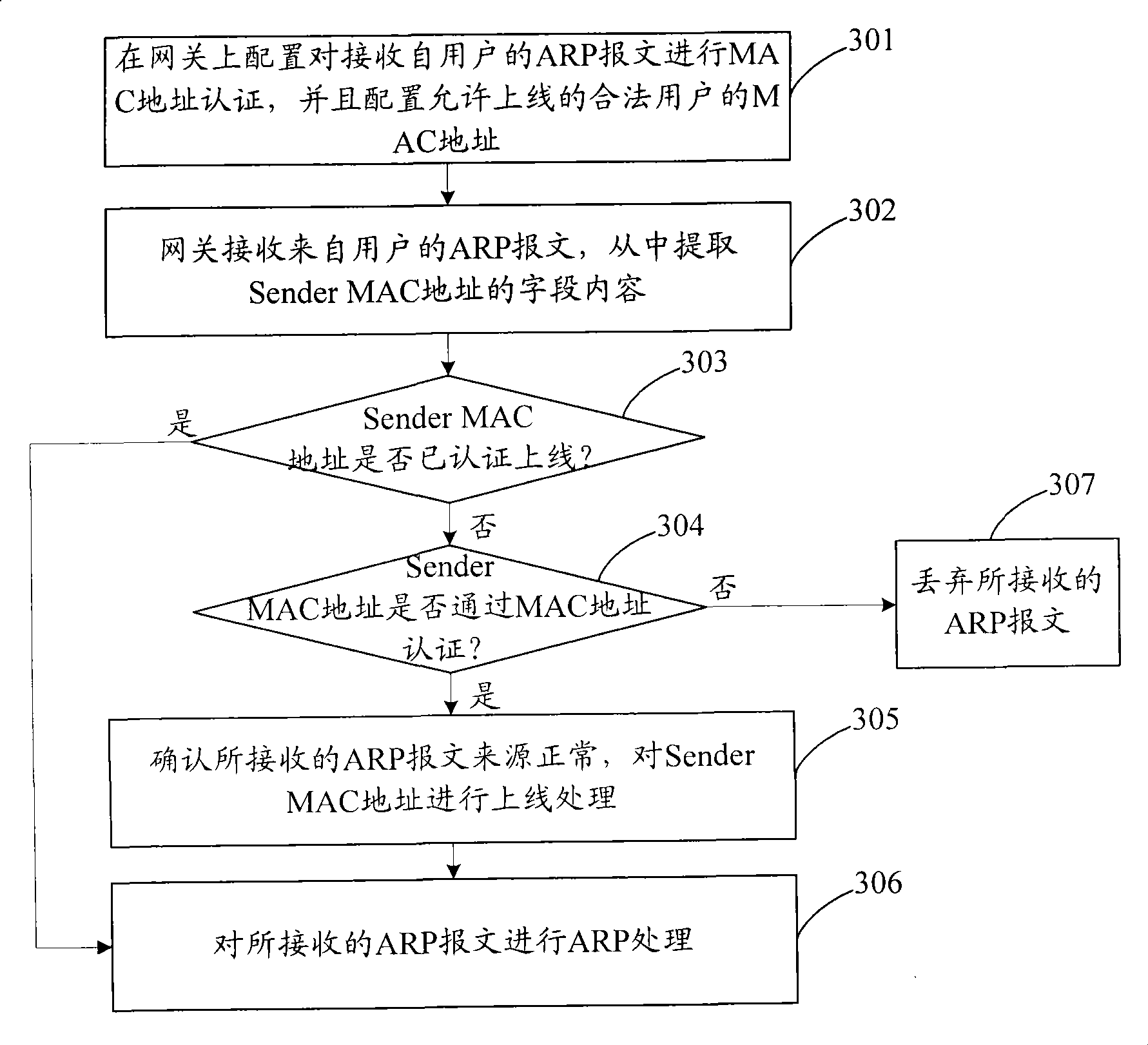
Method and system for defending address analysis protocol message aggression
InactiveCN101415012AEffective interceptionEffective attackData switching networksAddress Resolution ProtocolAddress resolution
The invention discloses a method used for defending address resolution protocol message attack, comprising the steps as follows: media access control MAC address of legal user is configured in advance; network equipment receives the address resolution protocol ARP message coming from the user; the field content of the MAC address of the sender is extracted out of the received ARP message; whether the extracted MAC address of the sender is the MAC address of the legal user configured in advance or not is judged; if not, the received ARP message is abandoned. The invention also discloses a system which can defend the address resolution protocol message attack. The method and the system are suitable for the users which adopt all types and do not need to modify the network equipment greatly.
Owner:NEW H3C TECH CO LTD
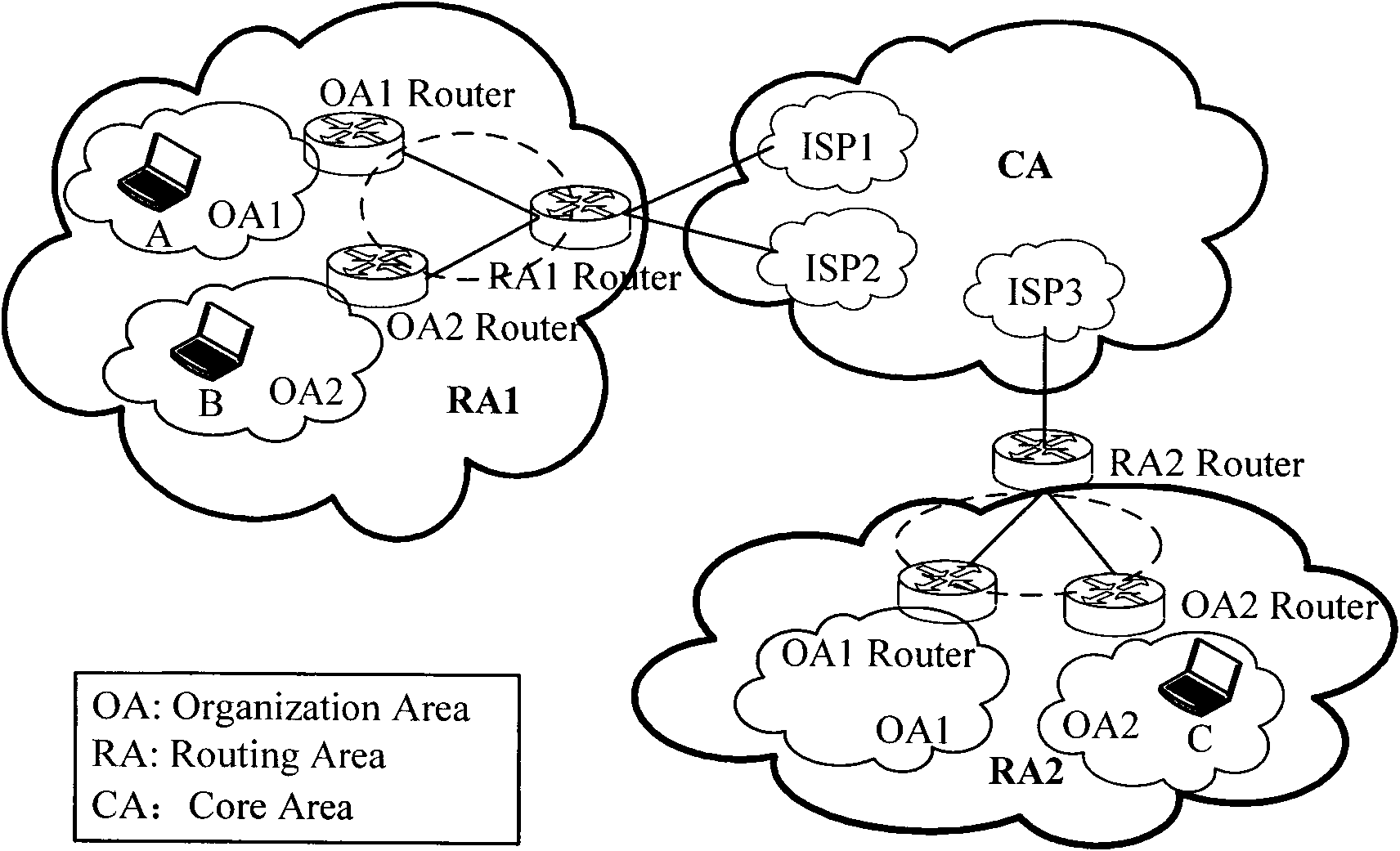
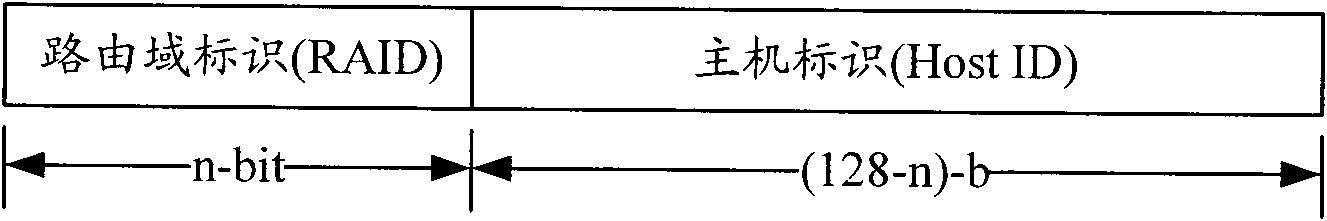
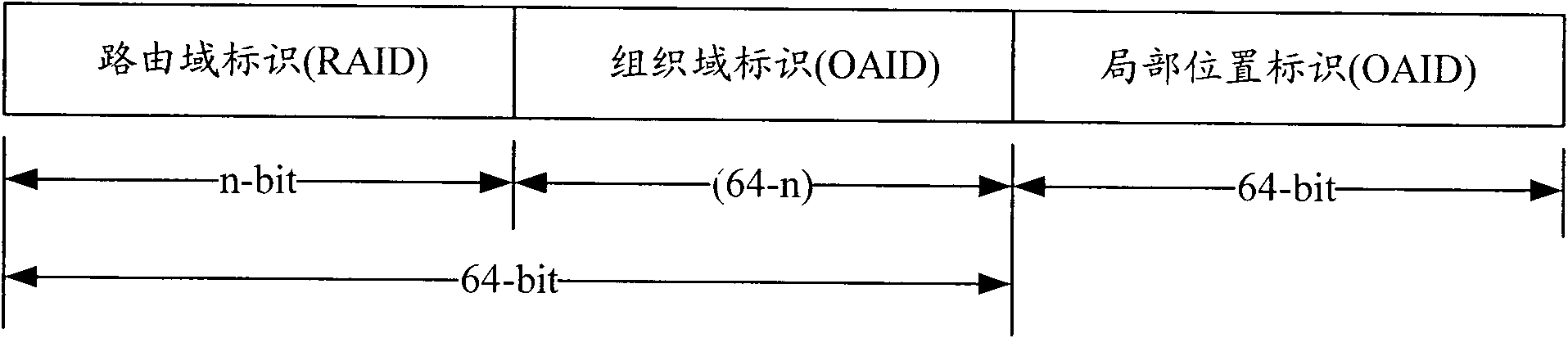
Location identifier and host identifier separation-based system and mobility management method thereof
InactiveCN102075420ASolve triangular routing problemsSupport multicastData switching networksRouting domainNetworked system
The invention provides a location identifier and host identifier separation-based network system and a mobility management method thereof. The system consists of a core area CA, a routing area RA formed by an organization area OA, a routing area router (RA Router), an organization area router (OA router), a mapping server in the routing area, and various terminals. To simplify the system, functional modules of the mapping server are distributed in routers in the routing area, including the RA router and the OA router, namely a distributed Hash table is used to organize the all RA routers and OA routers in the routing area to store the mapping information between a terminal location identifier, a location identifier of the OA Router connected with the terminal currently, and a host identifier; and from the terminal perspective, the router storing the mapping information of a terminal is called a mapping router Router-M of the terminal. The invention also provides an improved mobility management method on the basis of the network, which supports mobile conversation on the basis of solving the problem of routing expansibility. Furthermore, the invention can be compatible with Internet to reduce the deployment difficulty.
Owner:BEIJING UNIV OF POSTS & TELECOMM
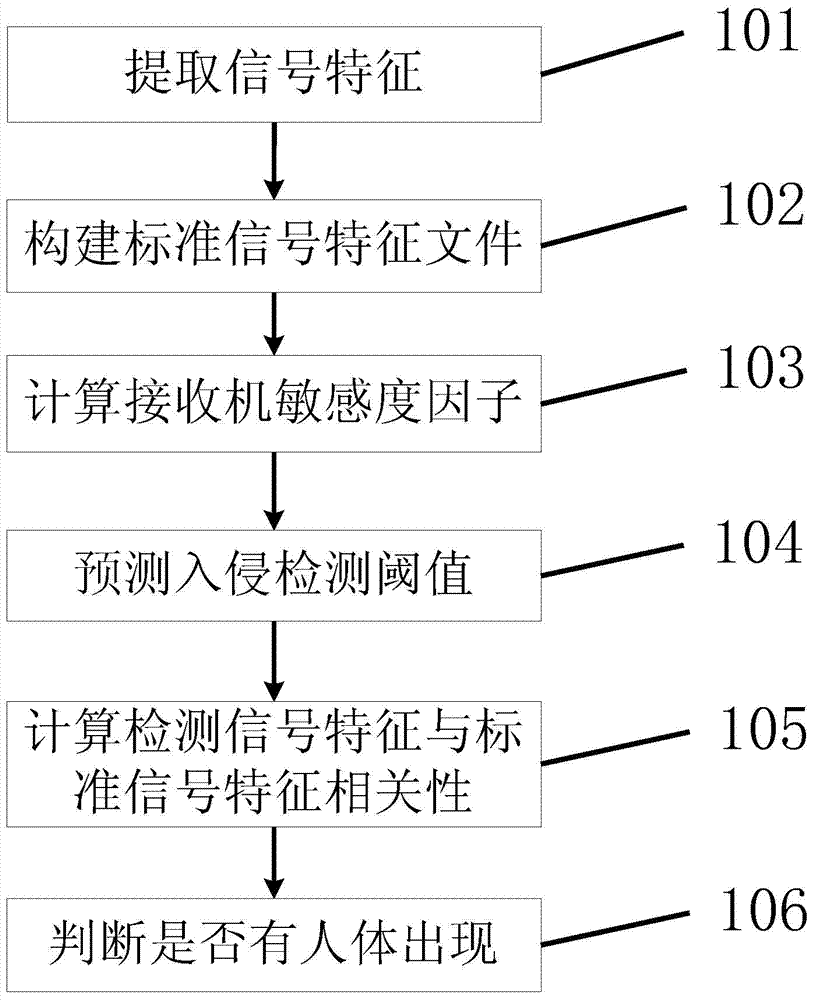
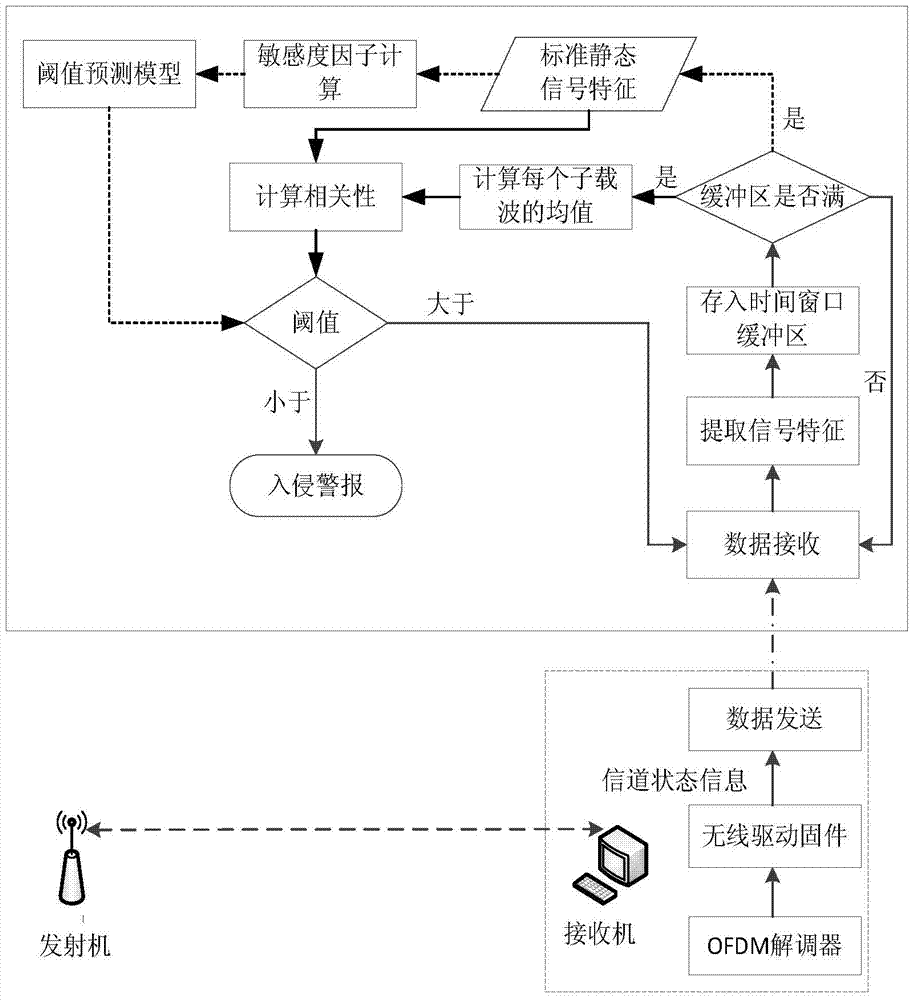
Indoor passive human-body detection method with free checking of fine granularity
ActiveCN104502982AFlexible scalabilityReduce the difficulty of deploymentDetection using electromagnetic wavesHuman bodyChannel state information
The invention discloses an indoor passive human-body detection method with free checking of fine granularity. The indoor passive human-body detection method comprises the following steps of: constructing a standard signal characteristic file; calculating a receiver sensitivity factor according to the standard signal characteristic file; estimating an intrusion detection threshold according to the receiver sensitivity factor; by a receiver, collecting channel state information of the current detecting signal in real time, extracting a detecting signal characteristic from the channel state information, and calculating the correlation between the detecting signal characteristic and a standard signal characteristic; judging whether the correlation between the detecting signal characteristic and the standard signal characteristic is less than the detection threshold, if so, obtaining a result that an intruding human body appears, otherwise obtaining a result that no person appears. The indoor passive human-body detection method disclosed by the invention has the advantages that the dependency on manual labor is less and the deployment is fast and convenient.
Owner:HARBIN ENG UNIV
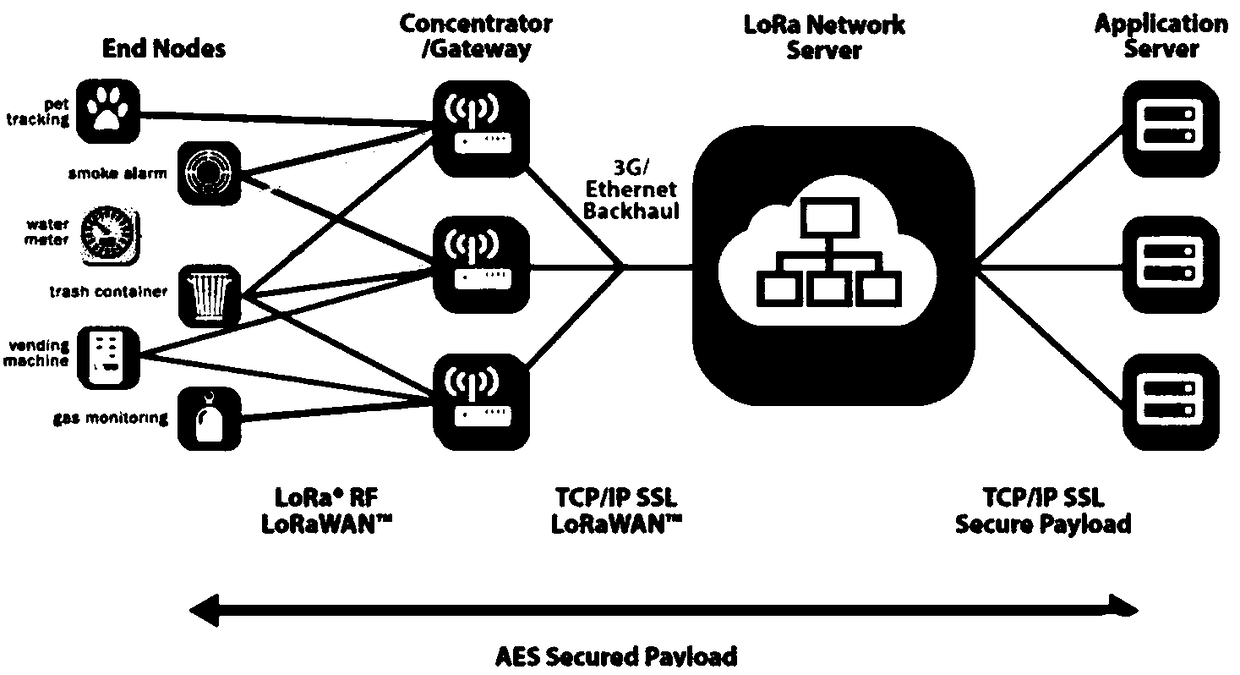
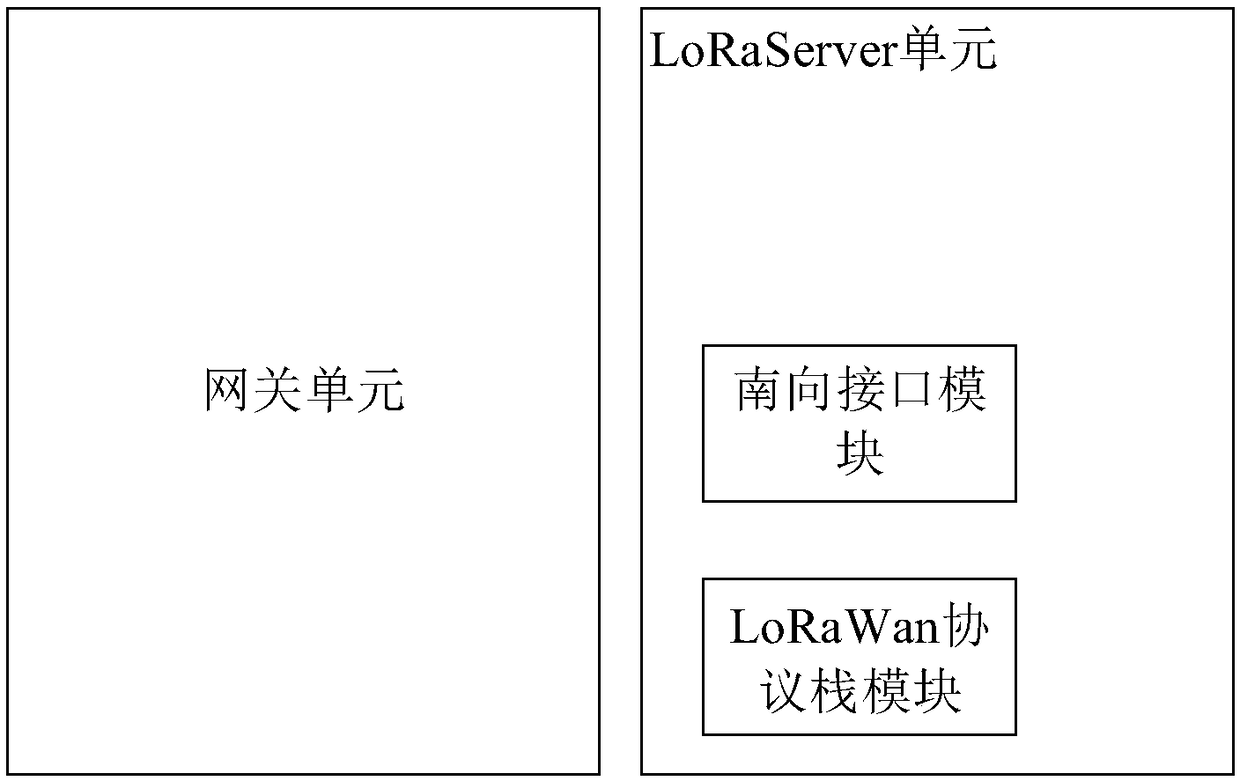
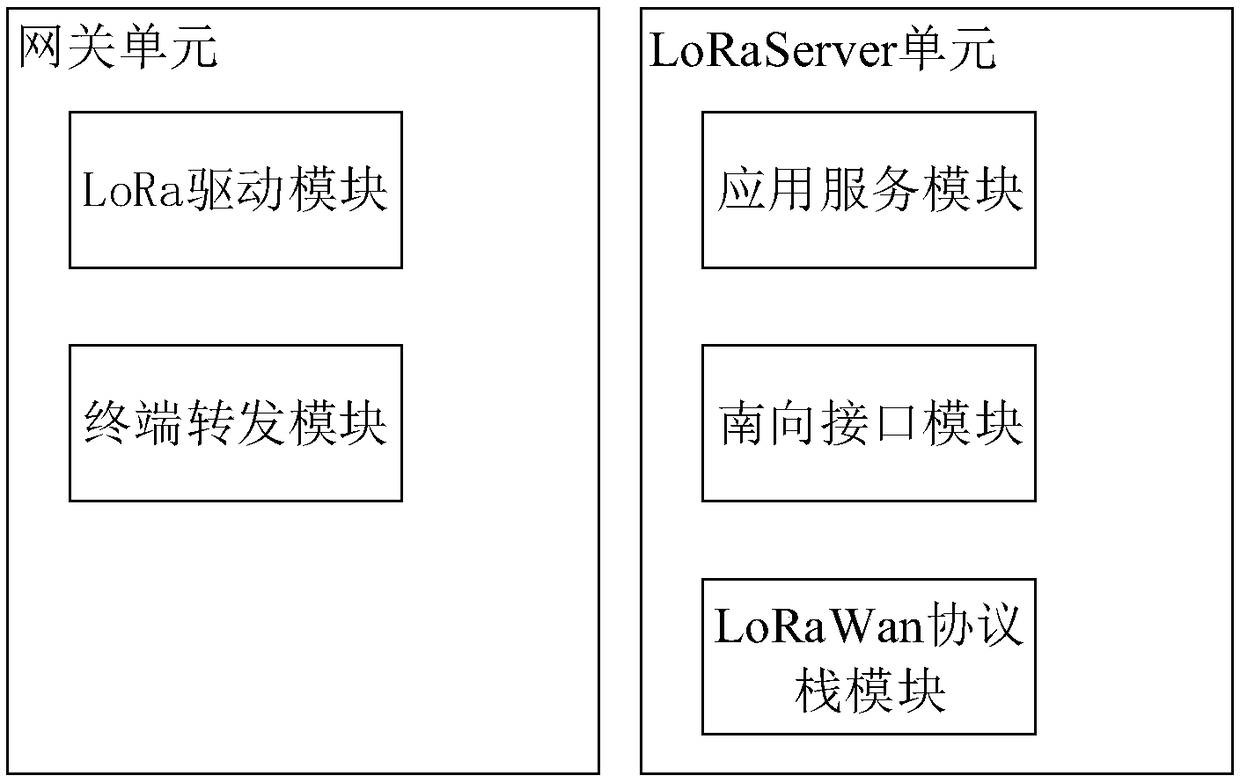
Gateway, LoRa (Long Range) network system, gateway running method and storage medium
ActiveCN109412937AReduce the difficulty of deploymentNetwork connectionsWireless communicationPlaintextApplication server
The application relates to a gateway, a LoRa (Long Range) network system, a gateway running method and a storage medium. The gateway includes a gateway unit and a LoRaServer unit. The LoRaServer unitincludes a southbound interface module and a LoRaWan protocol stack module. The gateway unit transmits a received terminal message to the southbound interface module. The terminal message is a networkaccessing request message or a terminal data message. The southbound interface module transmits network accessing request plaintext, which is obtained by processing the network accessing request message, to the LoRaWan protocol stack module, and carrying out protocol conversion on the terminal data message to obtain a terminal data network message used to be uploaded to an application server. TheLoRaWan protocol stack module obtains a terminal address according to the network accessing request plaintext, and obtains a network accessing response message, which is used to be issued to a terminal, on the basis of the terminal address. Functions of a LoRa network server are integrated in the gateway of the application, then no LoRa network server needs to be additionally deployed in application to the LoRa network system, the LoRa network system is simplified, and deployment difficulty is reduced.
Owner:COMBA TELECOM SYST CHINA LTD
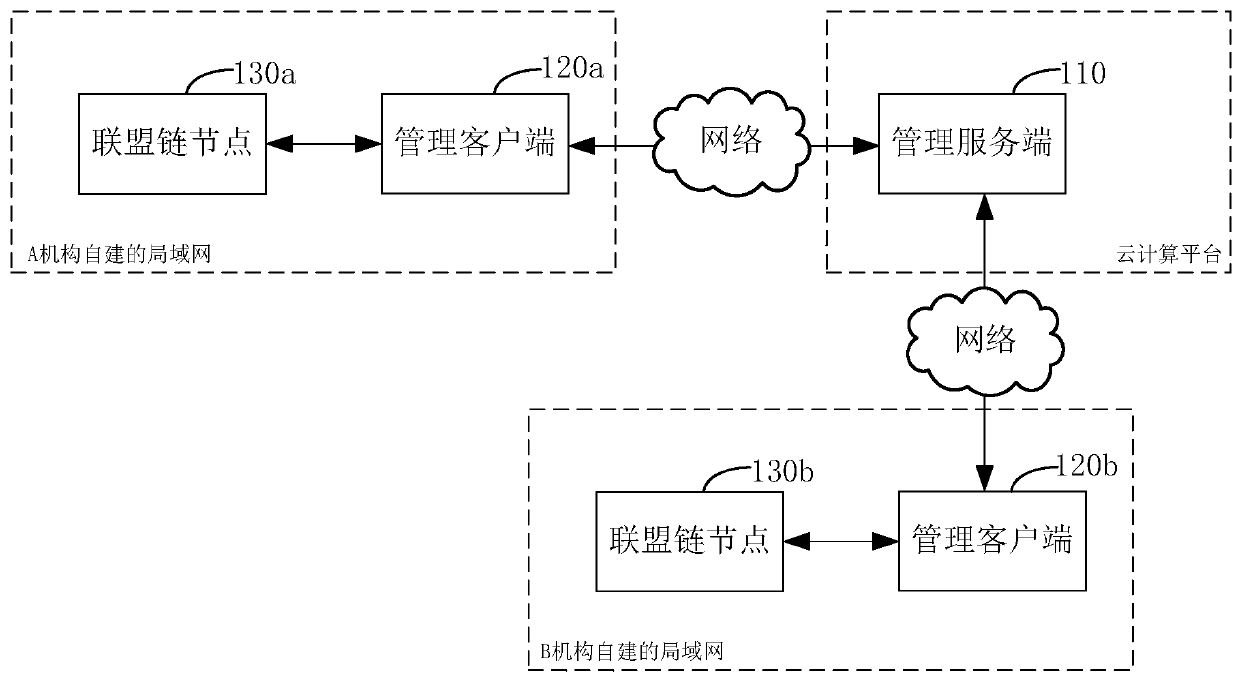
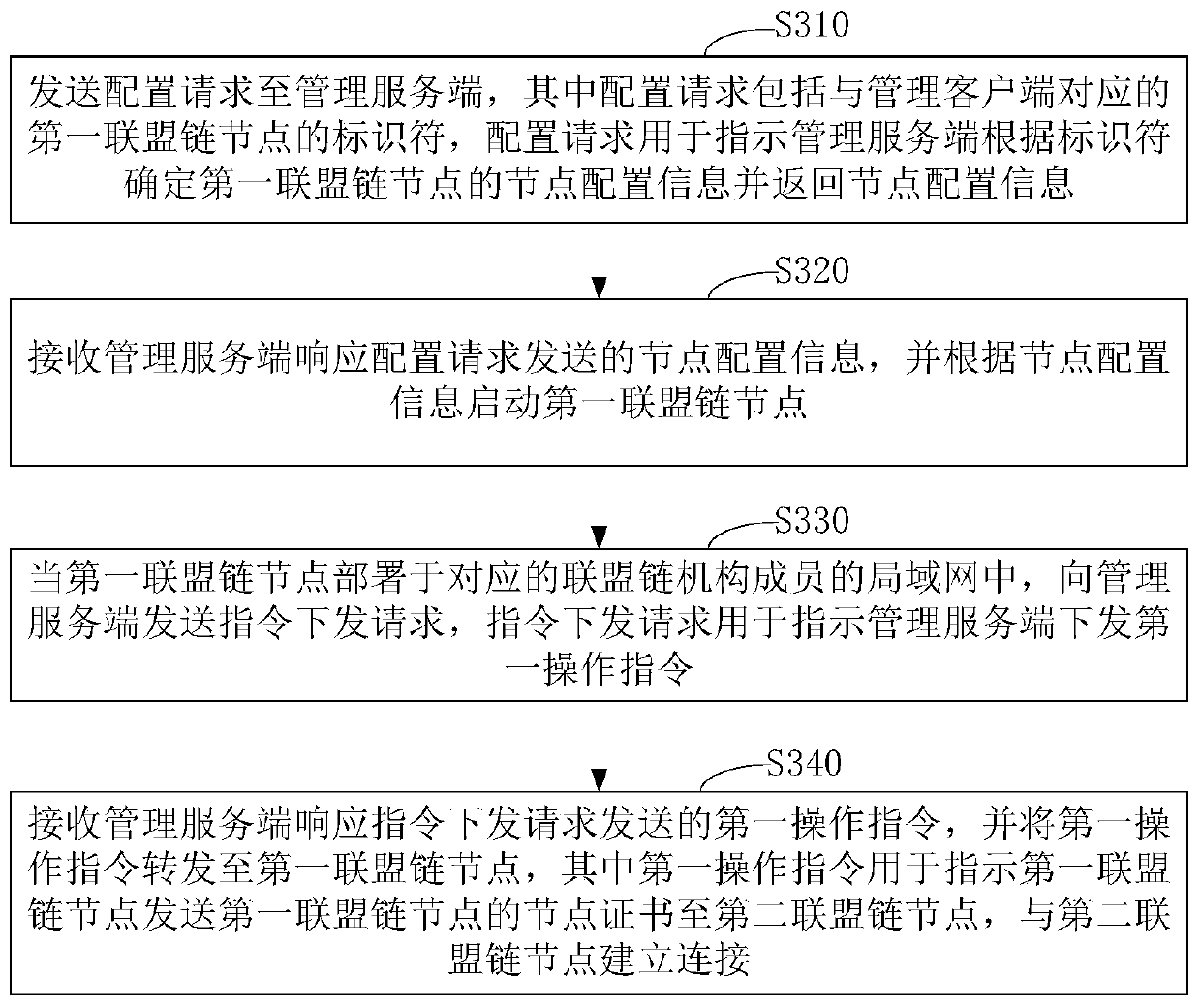
An alliance chain node management system and method
ActiveCN109728954AReduce the difficulty of deploymentReduce management difficultyData switching networksSecuring communicationClient-sideComputer science
The invention relates to an alliance chain node management system and method. The alliance chain node management system comprises a management server and a management client. Wherein the management client acquires node configuration information from the management server through the identifier of the alliance chain node, and starts the alliance chain node, obtainis a first operation instruction from a management server, forwards the first operation instruction to an alliance chain node, enables the alliance chain node to execute the first operation instruction, sends a node certificate of thealliance chain node to other alliance chain nodes, and establishes a connection with the other alliance chain nodes. The method is based on a block chain technology. Under the condition that each alliance chain mechanism member operates the respective alliance chain node in a self-built local area network, the alliance chain management system composed of the management server side and the management client side is utilized to realize unified operation maintenance and management of the alliance chain node of each mechanism member, so that the implementation deployment and management difficultyof the alliance chain is reduced.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
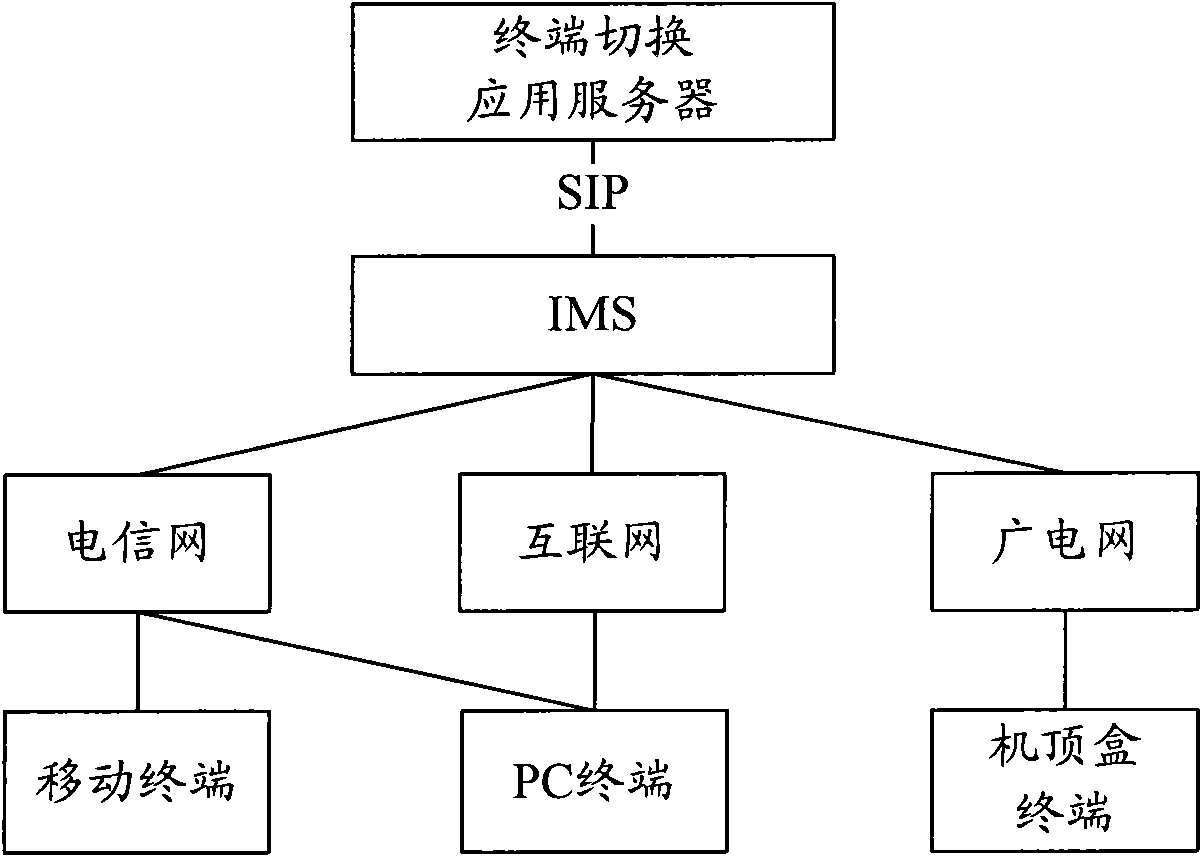
Communication system and method for realizing terminal switching by crossing networks and operators
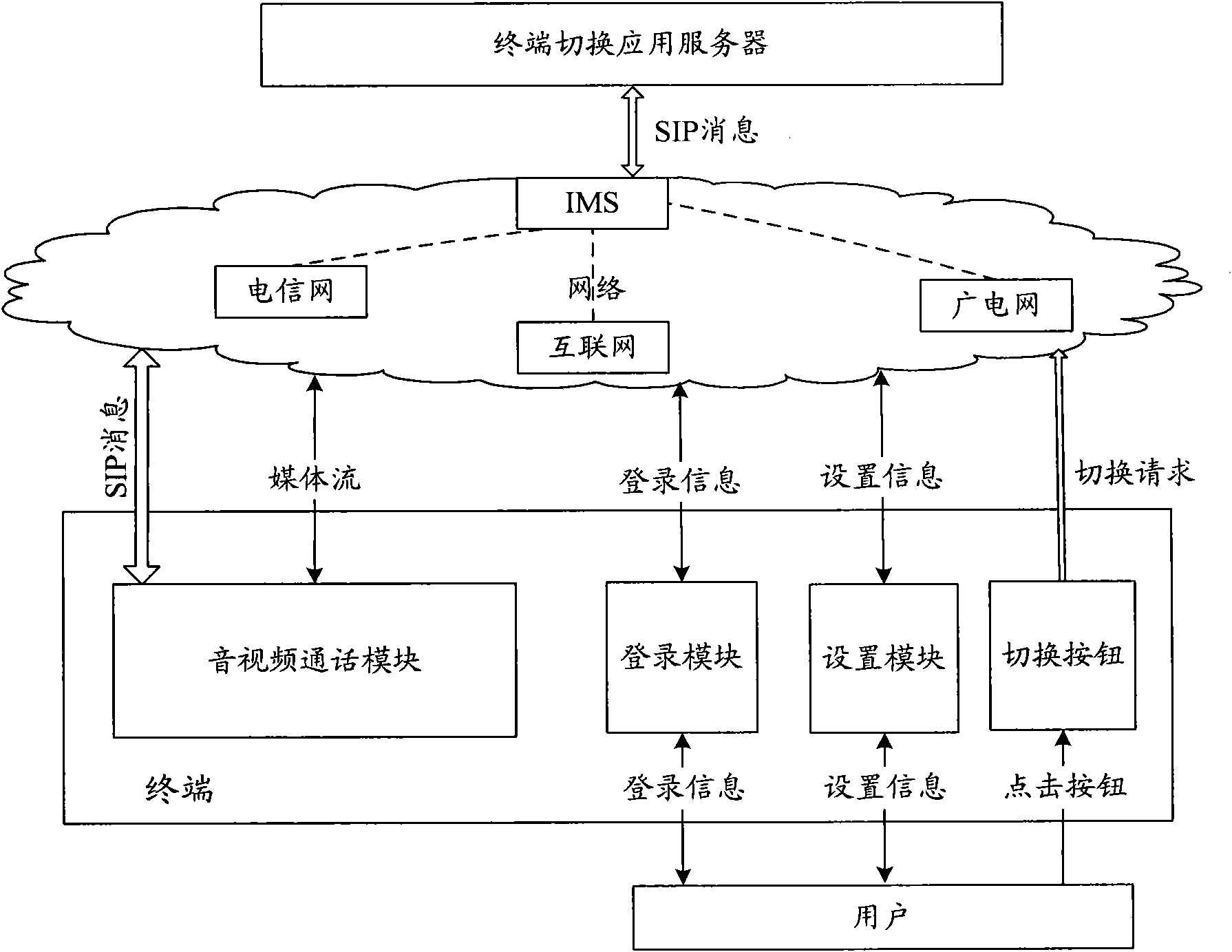
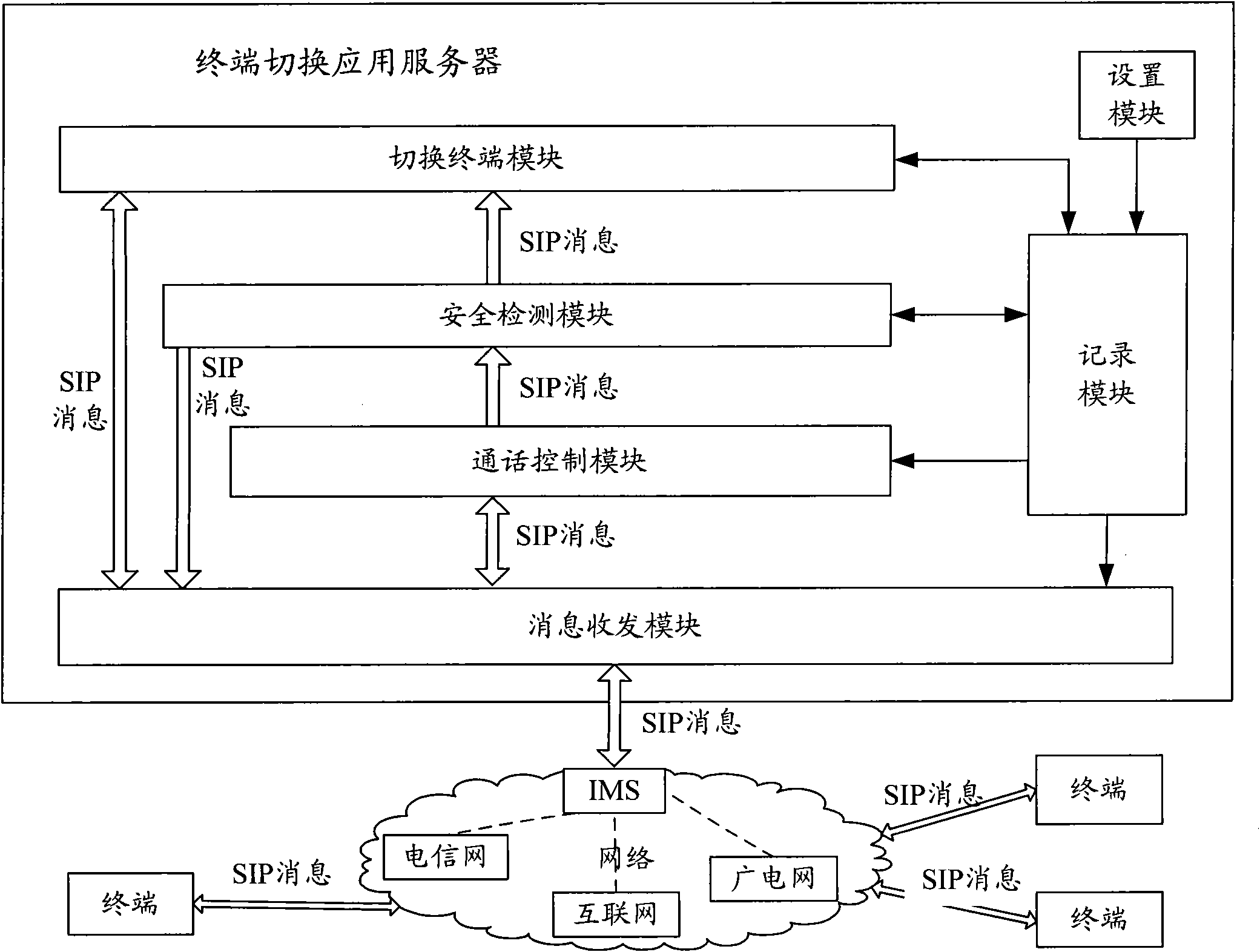
InactiveCN101888381ASimple structurePractical structureInterconnection arrangementsTransmissionSession Initiation ProtocolThe Internet
The invention relates to a communication system and a method for realizing terminal switching by crossing networks and operators, which are used for converged networks and can realize the terminal switching by crossing different networks such as a telecommunication network, the internet or a radio and television network and the like, or crossing a plurality of different operators. The system is provided with an IP multimedia subsystem (IMS)-based switching terminal application server and three terminals, namely mobile equipment, a computer or a television set provided with a set-top box, wherein the switching terminal application server and the terminals establish or remove a calling by using a session initiation protocol (SIP) and transmit a signaling required by terminal switching. In the method, a switching request initiator is not limited by the network in which the terminal is positioned, and the switching mode is particularly flexible; and the method can realize the switching among different (same)-network same-number terminals or different (same)-network different-number terminals, wherein the switching operation can be performed on any party in a call (a calling party, a called party or a certain party in a multi-party calling), and both a two-party voice-frequency or video call and the terminal switching during the multi-party voice-frequency or video call controlled by a multimedia server are supported.
Owner:BEIJING UNIV OF POSTS & TELECOMM
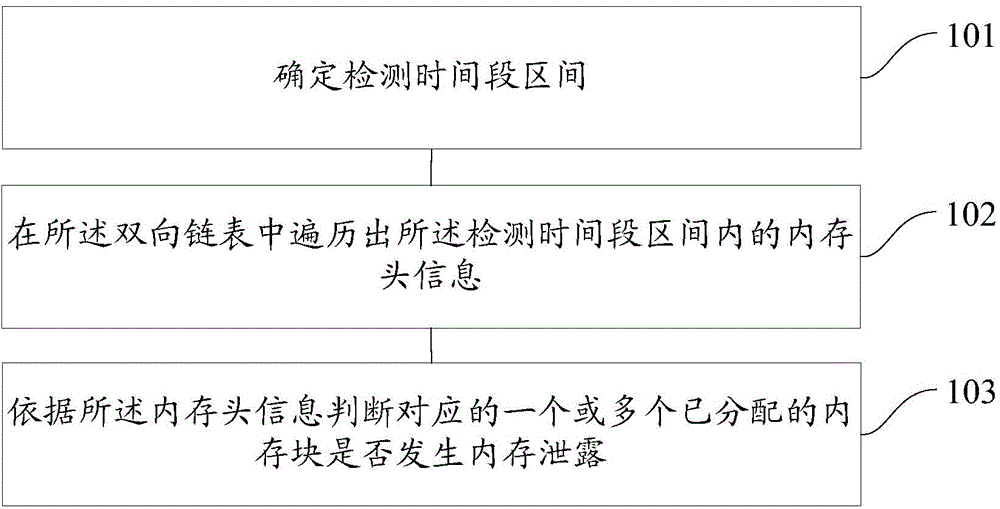
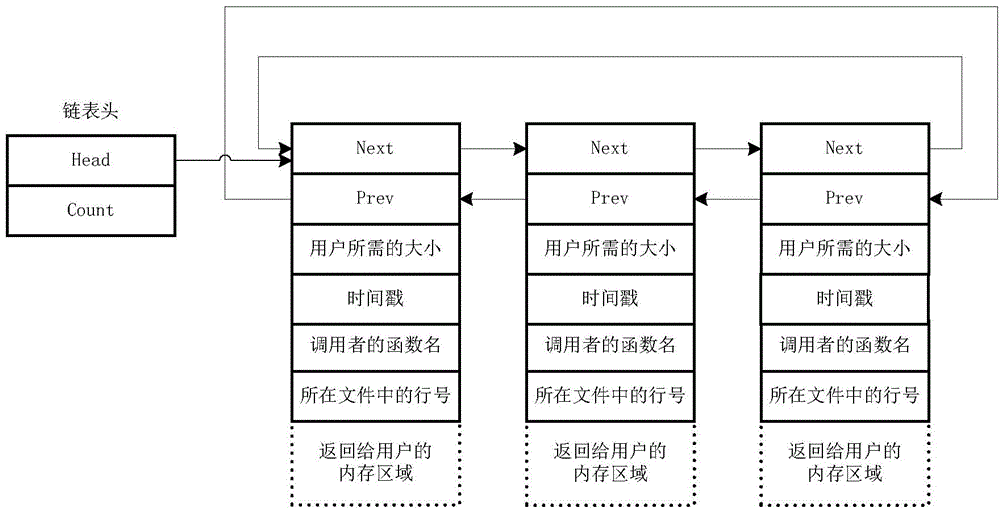
Memory leak detecting method and memory leak detecting device
InactiveCN104572460AImprove accuracySmall scaleSoftware testing/debuggingMemory leakDoubly linked list
The embodiment of the invention provides a memory leak detecting method and a memory leak detecting device. A memory comprises a doubly linked list of an allocated memory; and the doubly linked list comprises memory header information of one or more allocated memory blocks. The method comprises the steps of: determining a detection time interval; traversing the header information in the detection time interval in the doubly linked list; and in accordance with the memory header information, determining whether the corresponding one or more allocated memory blocks are subject to memory leak. By the memory leak detecting method and the memory leak detecting device, memory leak can be visually detected in real time, the software performance is improved, and manual operation is reduced or avoided, so that the method and the device are labor-saving and time-saving, the operation difficulty is reduced, the working efficiency is improved, the cost is reduced, the accuracy of the detection of memory leak is improved, and the leaked memory can be recycled in the entity life cycle.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Data storage and reading method and device and equipment
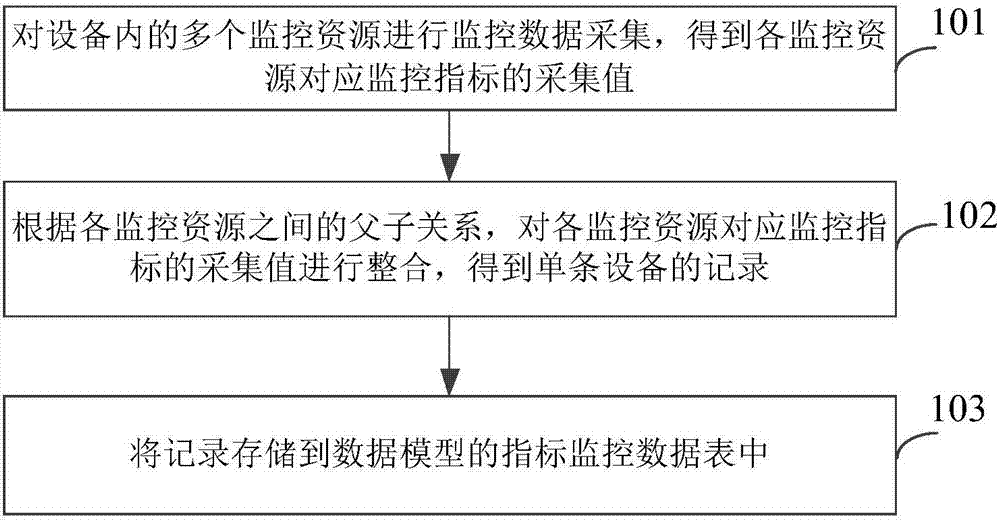
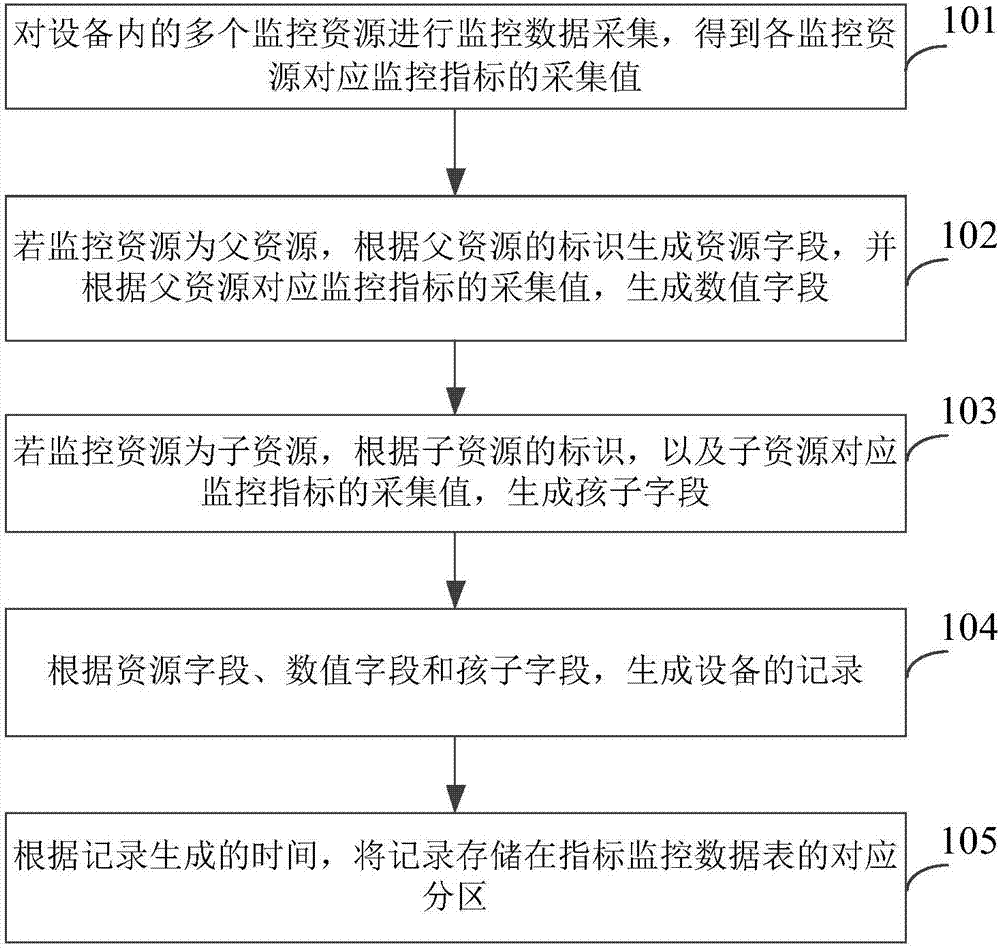
ActiveCN107391744AImprove storage efficiencyLower deployment costsDatabase queryingRelational databasesData storeMonitoring data
The invention provides a data storage and reading method and device and equipment. The data storage method includes: collecting the monitoring data of multiple monitoring resources in the equipment to obtain the collecting values of the corresponding monitoring indexes of the monitoring resources; integrating the collecting values of the corresponding monitoring indexes of the monitoring resources according to the parent-child relationships among the monitoring resources to obtain single equipment records; storing the records into the index monitoring data table of a data model. By the method, the collecting values of the corresponding monitoring indexes of the monitoring resources are integrated, processed and stored according to the parent-child relationships among the monitoring resources after the data is collected, database deployment cost and difficulty are lowered greatly, storage space is saved, and data storage efficiency is increased.
Owner:NEUSOFT CORP
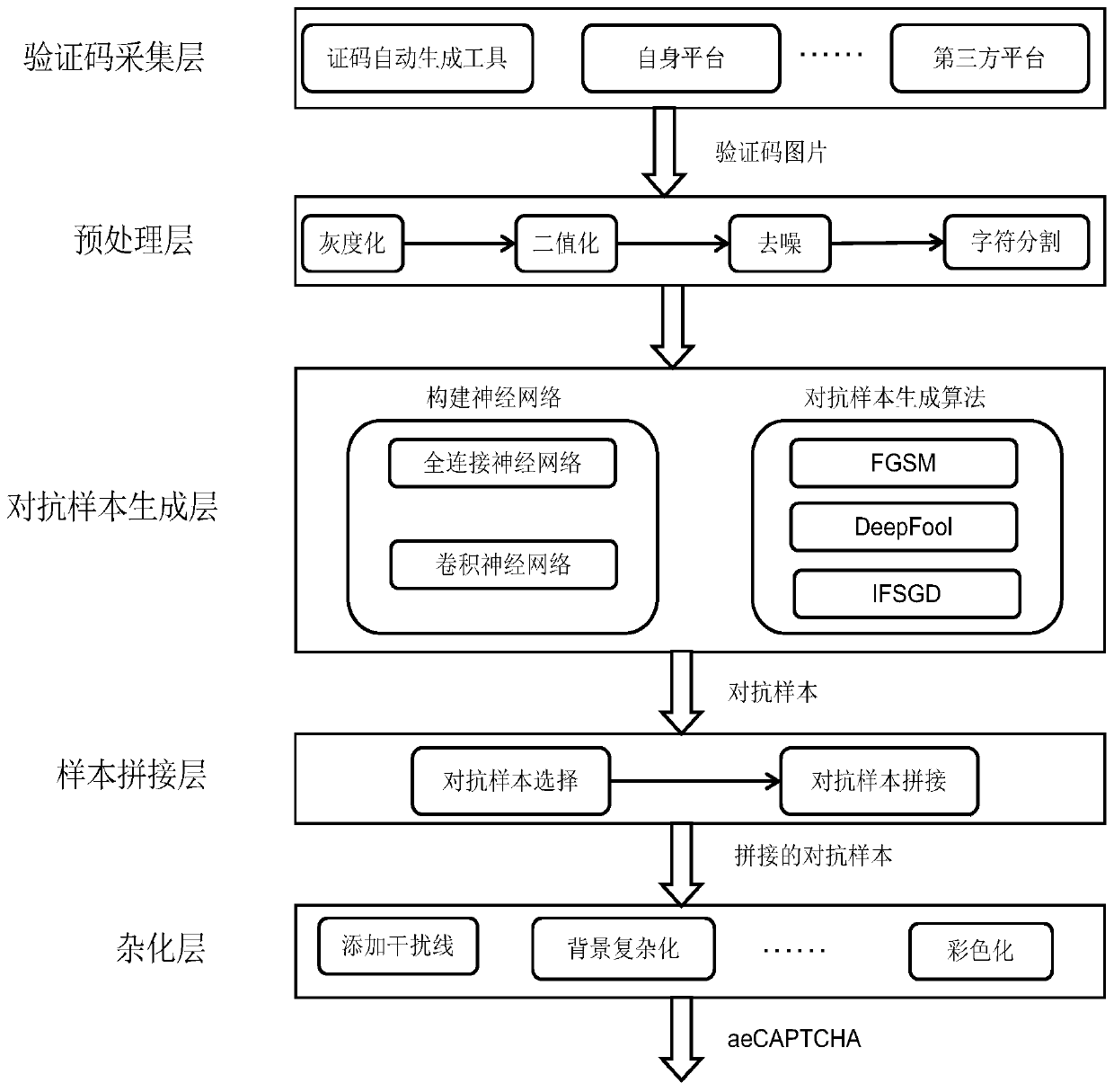
Adversarial sample-based verification code generation system and method
ActiveCN110008680ALow costReduce the difficulty of deploymentImage enhancementGeometric image transformationData setComputer architecture
The invention discloses an adversarial sample-based verification code generation system and method. The system comprises a verification code collection layer, a preprocessing layer, an adversarial sample generation layer, a sample splicing layer and a hybridization layer. The verification code acquisition layer transmits a collected verification code data set to the preprocessing layer, the preprocessing layer converts verification code pictures into a plurality of black and white character pictures through graying, binaryzation, denoising character segmentation and the like, and a constructedneural network and an adversarial sample algorithm are randomly selected from the adversarial sample generation layer to directionally generate adversarial samples. the sample splicing layer is usedfor splicing the single adversarial sample into verification codes with different lengths, and finally, the verification codes are reversedly preprocessed by the hybridization layer and are restored into colors, so that the verification codes aeCAPTCHA based on confrontation samples are generated. The system has the characteristics of low cost, low deployment difficulty and high attack resistance.The network attack can be more effectively resisted under the condition that the website does not need to replace an existing verification code system.
Owner:SOUTH CHINA NORMAL UNIVERSITY
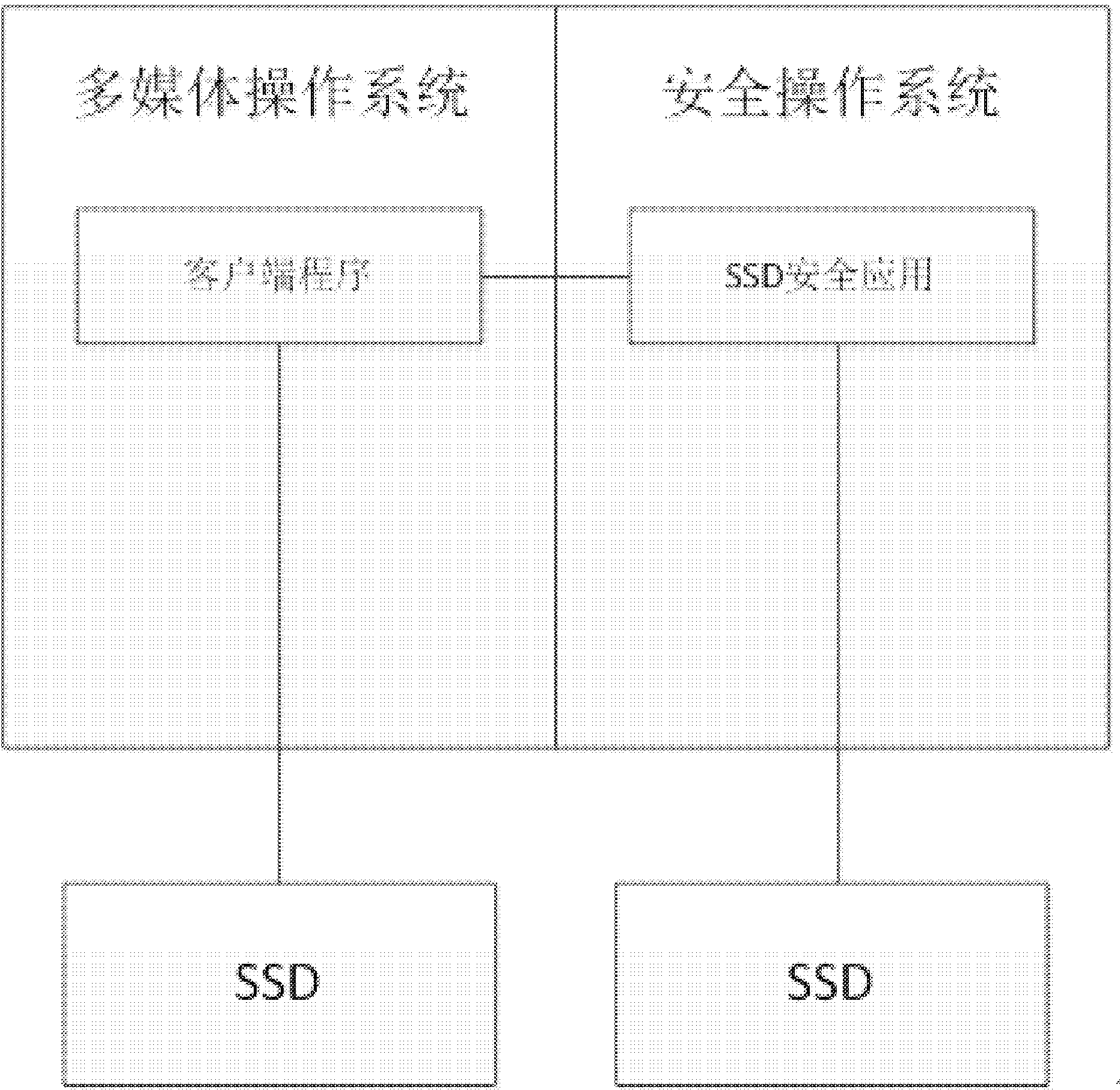
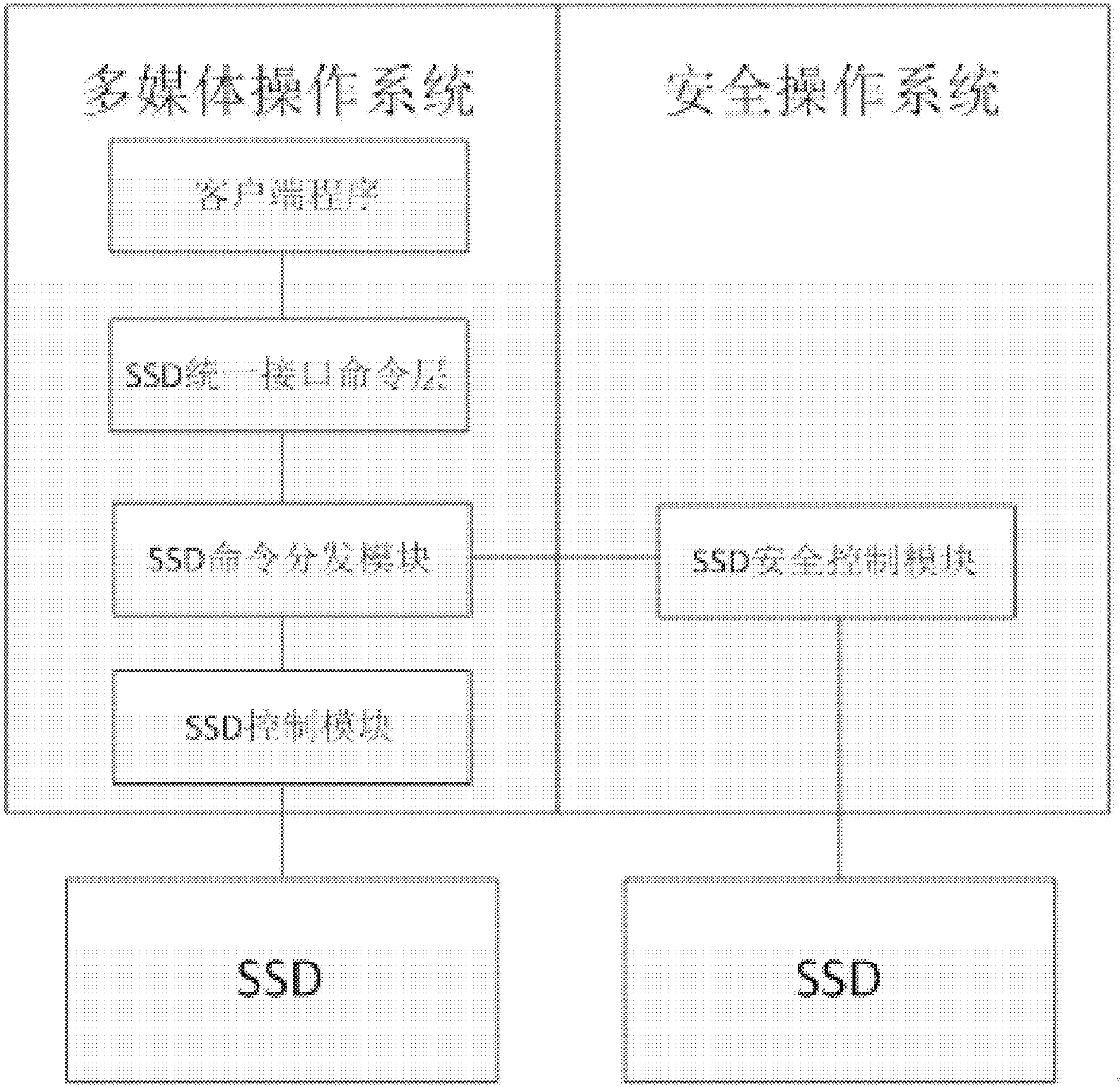
Apparatus for security information interaction
ActiveCN104301289ASimple designReduce complexityInternal/peripheral component protectionData switching networksSystems managementControl engineering
The present invention discloses an apparatus for security information interaction, the apparatus comprising a first system management device and a second system management device; the first system management device is used for providing an operation environment in a normal mode for an application and is composed of: a unified interface command module used for providing a unified command interface for the application; a command distribution module for determining to which external secure carrier the command is to be sent according to the command received from the unified interface command module; and a first control module used for performing command interaction with the external secure carrier in a normal mode; and the second system management device is used for providing an operation environment in a secure mode and is composed of: a second control module used for performing command interaction with the secure carrier in a secure mode, wherein the command distribution module is configured to invoke the first control module when the external secure carrier is determined to be in the normal mode and is configured to invoke the second control module when the external secure carrier is determined to be in the secure mode.
Owner:CHINA UNIONPAY
Distributed container cluster service discovery method based on homebred CPU and operation system
InactiveCN108040079ASupport health monitoringImplement service discoveryTransmissionDomain nameContainerization
The invention discloses a distributed container cluster service discovery method based on a homebred CPU and operation system. According to the method, a service discovery function is provided in a DNS mode, domain names are allocated to services, names and information of the services are organized into the domain names to register into containerization software, the domain names and the service information are mapped mutually into a database, and in the process of accessing the services, corresponding IP addresses and port information are acquired by the service names so as to achieve the service discovery function. The method disclosed by the invention supports to operate on a distributed container cluster management platform based on the homebred CPU and operation system, and can achieve the service discovery function of a distributed container cluster; a problem of dependence of containers and service release on a sequence is solved, the services are not required to be released before the containers are started, and the deployment difficulty is reduced; and a discovered service set is a universal set of the services in the distributed container cluster, and is the same for eachcontainer, no matter when the containers are started.
Owner:SHANDONG INSPUR CLOUD SERVICE INFORMATION TECH CO LTD
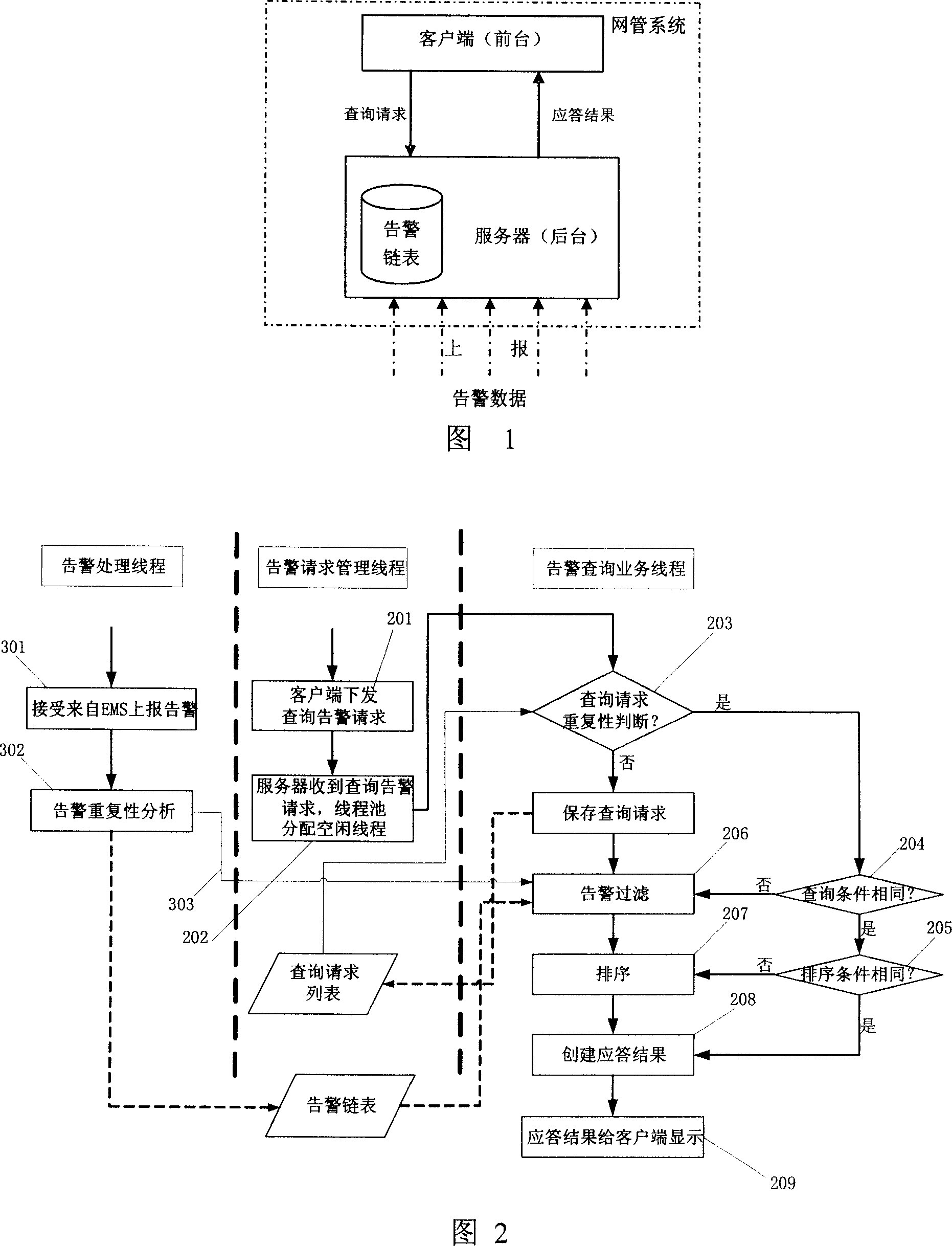
Quick query warning method for telecommunication management network
InactiveCN1937658AReduce configuration requirementsReduce the difficulty of deploymentSupervisory/monitoring/testing arrangementsData informationNetwork management
The invention discloses a fast alarm inquiring method for telecom management network, applied to a system comprising server and client ends, where the server is used to receive and store alarm data reported by lower-layer network management system. And it comprises the steps of: (a) client end sends alarm inquiring request to the server, where the inquiring request parameters include unique request tag, inquiring conditions and appointed page information; (b) the server receives the alarm inquiring request and filters and obtains the corresponding alarm data information according to the inquiring conditions, and then generating alarm data of user appointed page as inquired results according to the appointed page information; (c) the server communicates with the client end and issues the inquired results to the client end, and the client end displays these alarm data. And it remarkably raises the efficiency of user's inquiring alarm information, reduces transmission of network data quantity, and can meet the requirements of parallel processing inquiring request, arranging alarm data in the whole network, etc.
Owner:ZTE CORP
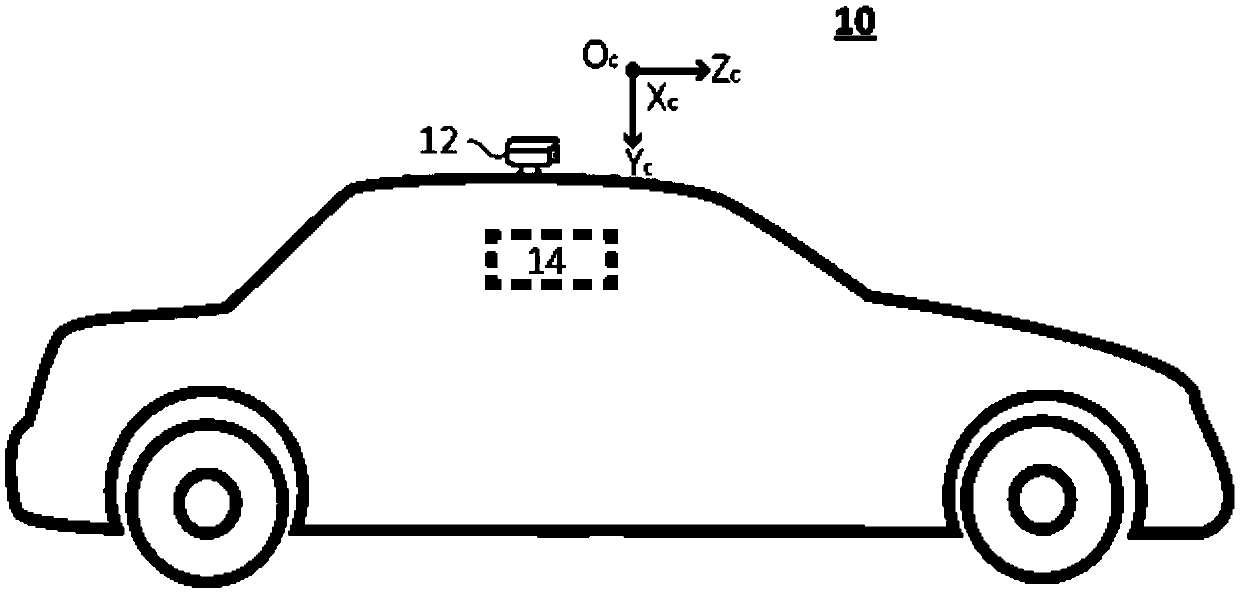
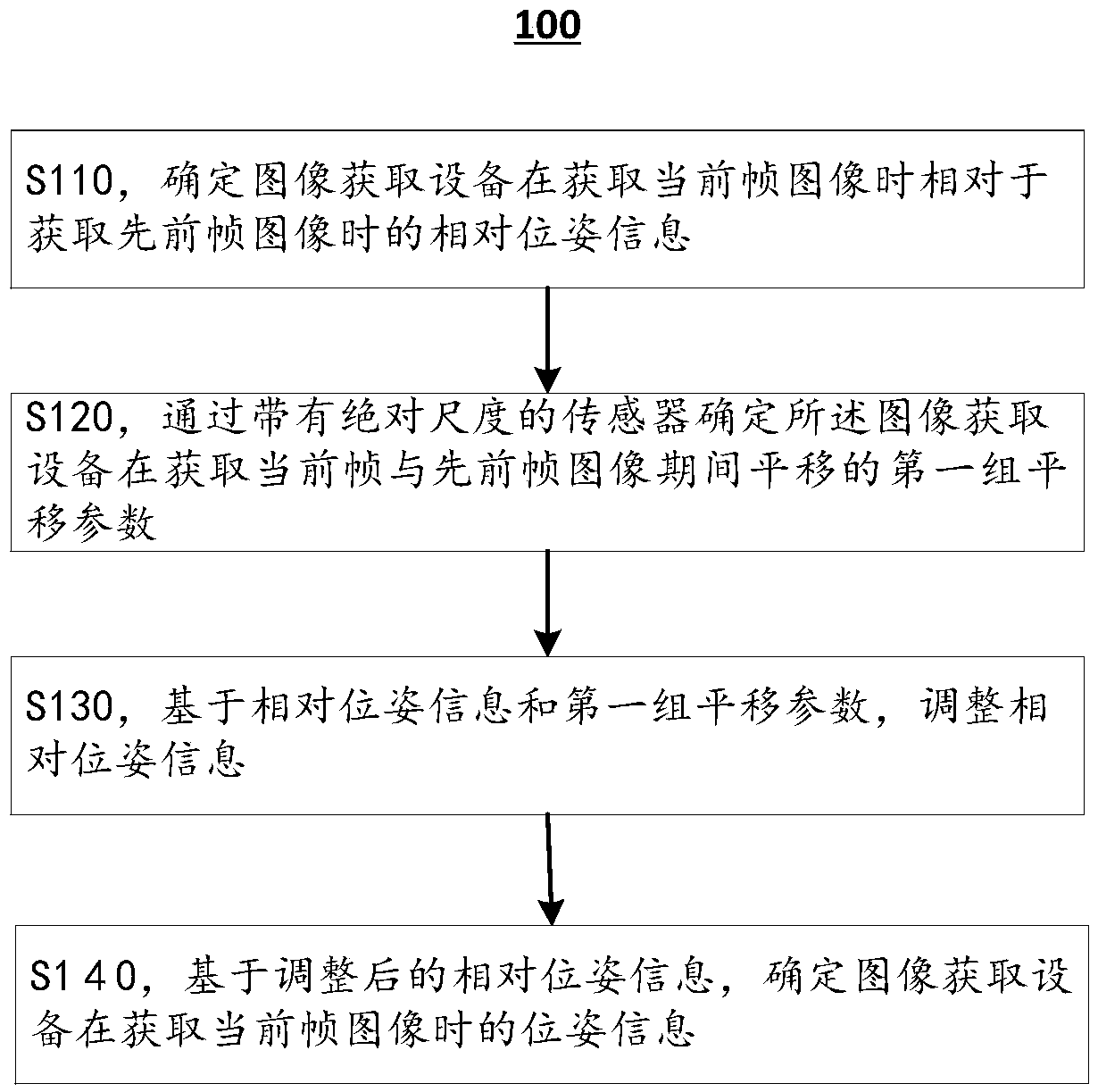
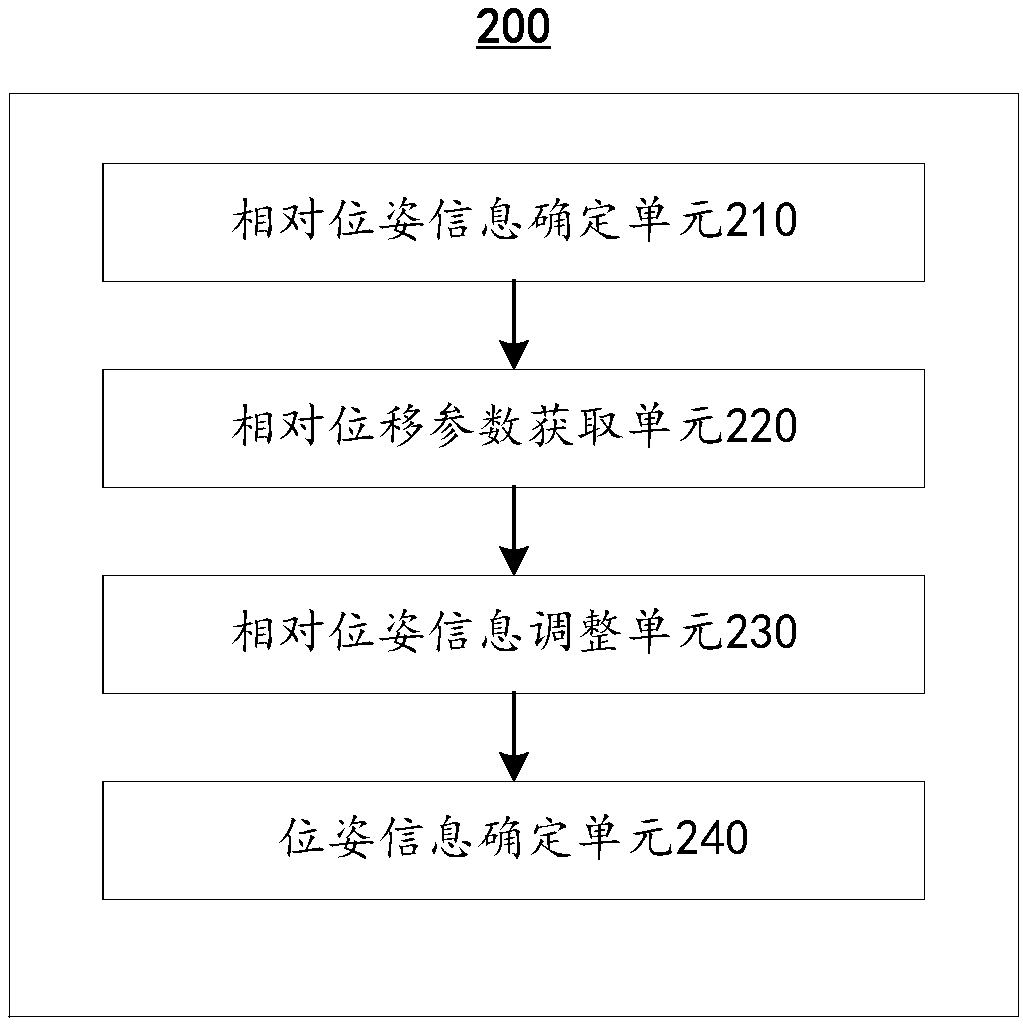
Posture information determination method and apparatus, visual point cloud construction method and apparatus
ActiveCN109544630ALow costReduce computing costImage enhancementImage analysisPoint cloudFrame based
Disclosed are a posture information determination method and determination device, a visual point cloud construction method and a visual point cloud construction device. The posture information determination method includes determining relative posture information of an image acquisition device when acquiring an image of a current frame relative to when acquiring an image of a previous frame; Determining, by a sensor with an absolute scale, a first set of translation parameters for movement of the image acquisition device during acquisition of images of the current and previous frames; Adjusting the relative posture information based on the relative posture information and a first set of translation parameters; And determining posture information of the image acquisition apparatus when acquiring an image of a current frame based on the adjusted relative posture information. In order to obtain more accurate posture information, the translation vector of the camera posture information isdirectly calibrated by the scale of the external sensor using the posture information determination method.
Owner:NANJING INST OF ADVANCED ARTIFICIAL INTELLIGENCE LTD
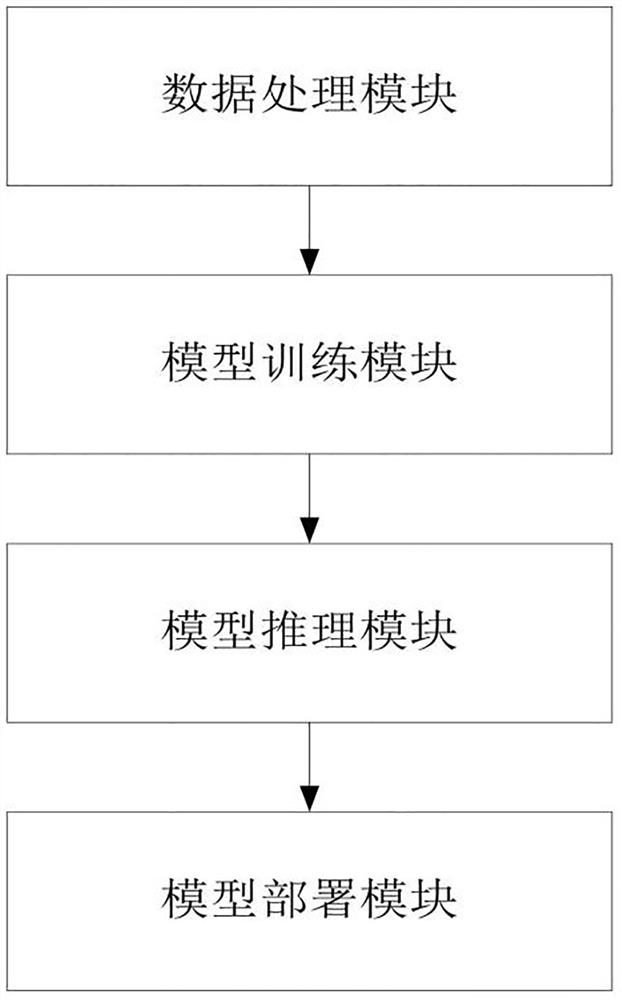
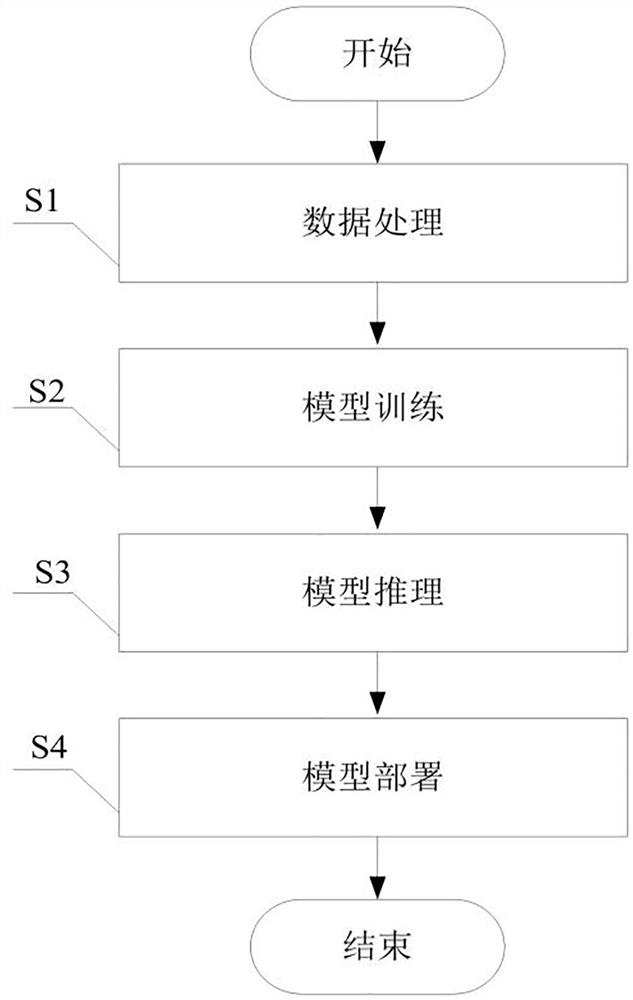
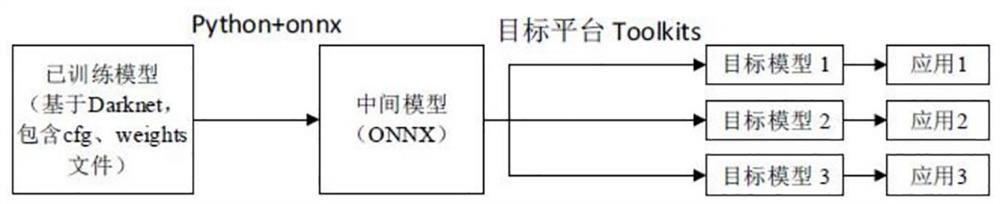
Mask detection and deployment system and method based on image recognition
ActiveCN112085010AEasy to deployImplement a full-stack development processCharacter and pattern recognitionNeural architecturesData acquisitionEngineering
The invention provides a mask detection and deployment system and method based on image recognition, and belongs to the technical field of biological recognition. The system comprises a data processing module which is used for collecting a face image and a mask image, and carrying out the labeling of the face image and the mask image, a model training module used for training a face mask detectionmodel by utilizing the marked face image and mask image, a model reasoning module used for detecting the positions of the human face and the mask by using a non-maximum suppression algorithm according to the human face mask detection model, and a model deployment module used for deploying the face mask detection model according to the detection result. The method comprises complete and unified processes of image data acquisition, data labeling, model training, model deployment and application integration, and core multi-structure and multi-target detection models and automatic target platformreasoning engine deployment characteristics of the method can meet the requirements of different scenes, hardware configuration, detection precision and pedestrian flow.
Owner:CHENGDU UNIV OF INFORMATION TECH
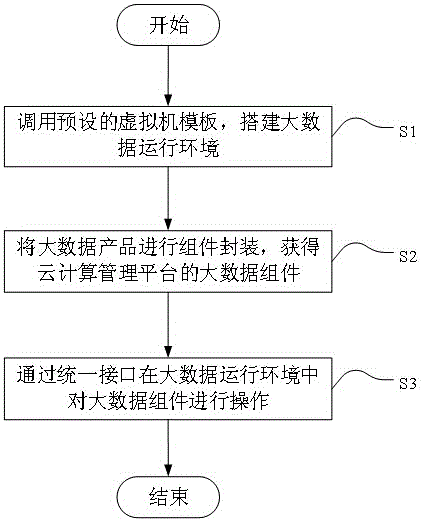
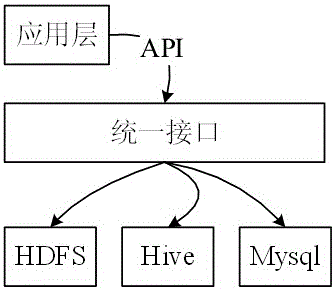
Automatic deployment method and device for big data nodes under cloud computing environment
InactiveCN105787117ALower performance requirementsImprove compatibilityDatabase management systemsDatabase distribution/replicationComputer compatibilityInterface protocol
An embodiment of the invention discloses an automatic deployment method and device for big data nodes under a cloud computing environment. The method comprises steps as follows: a preset virtual machine template is called, and a big data operation environment is established; big data products are subjected to assembly packaging, and a big data assembly of a cloud computing management platform is obtained; the big data assembly is operated through a uniform interface in the big data operation environment. According to the automatic deployment method and device, a uniform interface protocol is defined in different big data products, a uniform deployment, monitoring, maintenance and operation page is provided for big data, the big data maintenance and deployment difficulty and workload under the cloud computing environment are reduced, version compatibility between nodes is improved, operation time is shortened, capacity requirements for operators is reduced, and manual misoperation is avoided.
Owner:SANMENG TECH CO LTD
Extraction method of collagen polypeptide and active calcium in walleye pollock bone
ActiveCN106047970AIncrease profitAdd flavorConnective tissue peptidesOrganic compound preparationHigh pressureCalcium EDTA
The invention discloses an extraction method of collagen polypeptide and active calcium in walleye pollock bone. The method comprises the following steps: (I) pretreating the raw material; (II) preparing bone collagen polypeptide through the substeps of (1) soaking fish bone in a NaOH solution and then carrying out high-temperature and high-pressure treatment, (2) extracting the bone collagen, (3) carrying out treatment via a high-voltage pulsed electric field, and (4) carrying out enzymolysis by firstly adding composite collagen protease for enzymolysis, then adding flavor protease for enzymolysis, decolorizing and deordorizing, carrying out spray drying to obtain the collagen polypeptide; and (III) preparing active calcium in fish bone through the substeps of (1) extracting tartaric acid, (2) extracting tartaric acid again, and (3) combining the extracted tartaric acids to prepare the active calcium in the fish bone. Through the extraction method, the disadvantages of thick fishy smell, bitter taste and unfavorable peculiar smells of the marine source collagen polypeptide can be overcome; the collagen polypeptide of the walleye pollock bone which is free of pungent smell, delicious and moderate in taste can be prepared; meanwhile, the bone dreg can be economically and efficiently used for preparing active tartaric acid chelated calcium; the utilization rate of the walleye pollock bone is increased; the high-value utilization is achieved.
Owner:SHANDONG ORIENTAL OCEAN SCI TECH
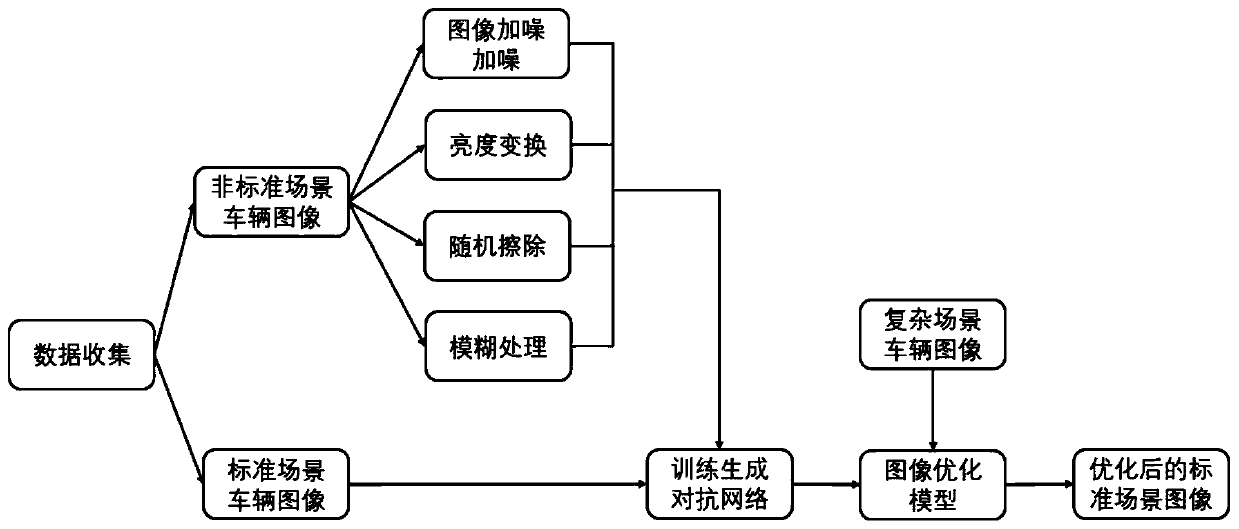
Vehicle image optimization method and system based on adversarial learning
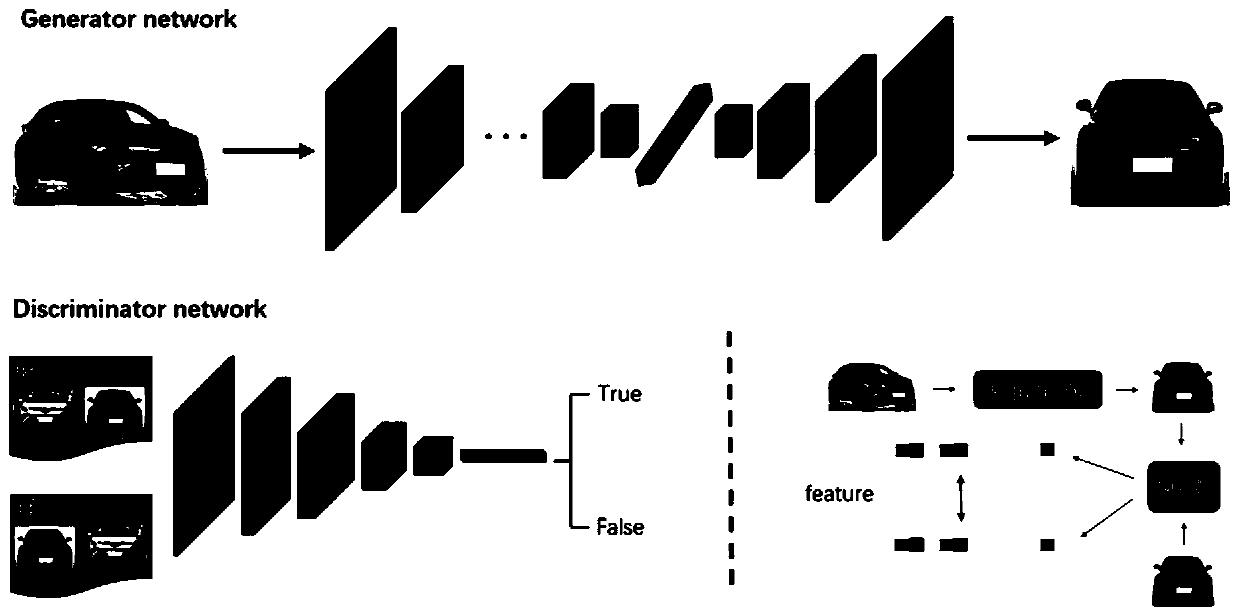
InactiveCN110458060AImage optimization process is simple and efficientReduce labor burdenInternal combustion piston enginesCharacter and pattern recognitionDiscriminatorFeature extraction
The invention discloses a vehicle image optimization method and system based on adversarial learning. The vehicle image optimization method comprises the steps: collecting vehicle images photographedat different angles, and dividing the vehicle images into a standard scene image and a non-standard scene image; carrying out image preprocessing on the non-standard image to obtain a low-quality dataset; constructing a vehicle image optimization model based on the generative adversarial network, wherein the model is composed of a generator, a discriminator and a feature extractor; training a vehicle image optimization model based on the generative adversarial network, setting a loss function, calculating a network weight gradient by adopting back propagation, and updating parameters of the vehicle image optimization model; and after the vehicle image optimization model is trained, reserving the generator as a final vehicle image optimization model, inputting multi-scene vehicle images, and outputting optimized standard scene images. According to the invention, migration from complex scene vehicle images to standard scene vehicle images is realized, and the purpose of optimizing the image quality is achieved, and the vehicle detection and recognition accuracy is improved.
Owner:JINAN UNIVERSITY
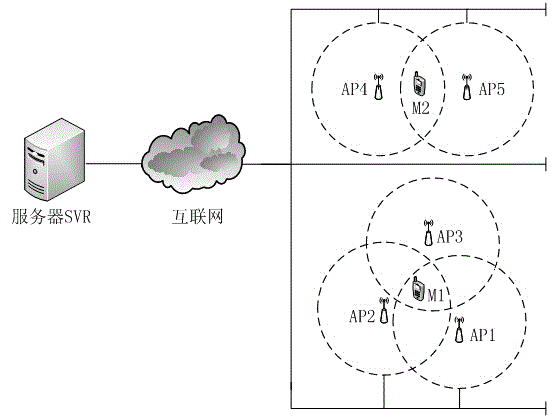
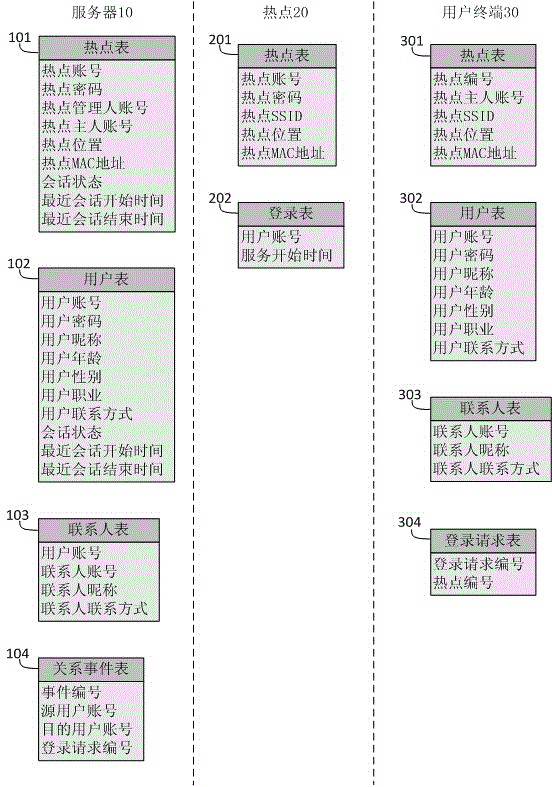
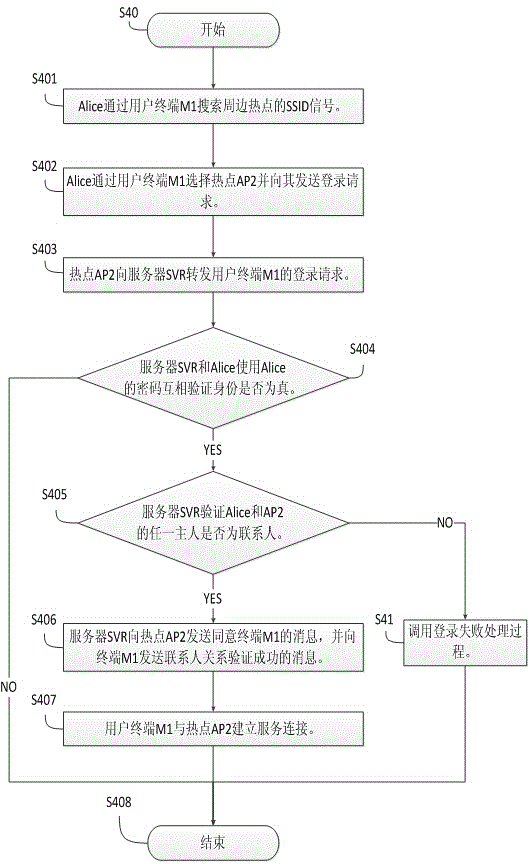
WiFi hot spot login method and system
ActiveCN104468565AEasy to operateImprove efficiencyTransmissionSecurity arrangementUser inputThe Internet
The invention discloses a WiFi hot spot login method and system. A server located in the Internet, WiFi hot spots for providing the Internet access service, a terminal and users are involved in the method, wherein the users use the service provided by the system when the terminal is in communication with the WiFi hot spots or the server. By establishing the contact person relation between the users requesting for logging into the hot spots and hot spot owners, the automatic access control of the hot spots is achieved, two users who are contact persons for each other can automatically log into the WiFi hot spots owned by the opposite sides, the complex operation that the users input and manage account numbers, keywords and the like manually is avoided, and the use efficiency is improved.
Owner:SUN YAT SEN UNIV
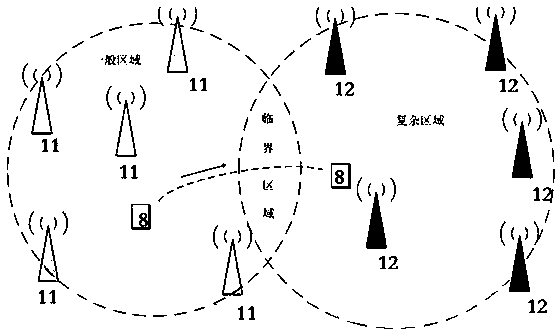
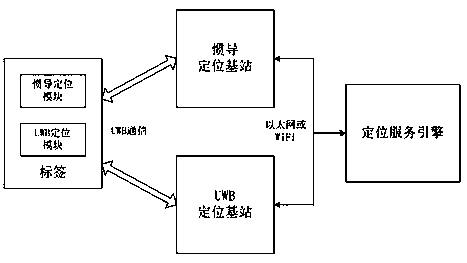
Plant area high-accuracy person positioning method and positioning system
ActiveCN109115211AHigh positioning accuracyReduce the impactNavigation by speed/acceleration measurementsPosition fixationAgricultural engineeringComputer vision
The invention discloses a plant area high-accuracy person positioning method. In the method, the interior region of a plant area is divided into a complex environment region and an ordinary region according to the plant area shielding condition, an inertial navigation positioning base station is arranged in the complex environment region, a UWB positioning base station is arranged in the ordinaryregion, 4-6 positioning base station attributes at the periphery are acquired through positioning labels, and positioning is performed through the positioning base station attributes; when 4 positioning base station attributes or more belong to the UWB positioning base station, positioning is performed through a UWB module; when the amount of the positioning base station attributes, belonging to the UWB positioning base station, is 3, the position of a current positioning label is determined by adopting a Kalman filtering method according to acquired UWB module positioning coordinate values and inertial navigation positioning coordinate values; and in other cases, an inertial navigation module is adopted to perform positioning. Through seamless combination of the two of UWB positioning andinertial navigation positioning, the plant area high-accuracy person positioning method provided by the invention solves the problem of poor positioning accuracy for positioning a blind area and a complex environment of the traditional positioning system.
Owner:NANJING SCIYON AUTOMATION GRP
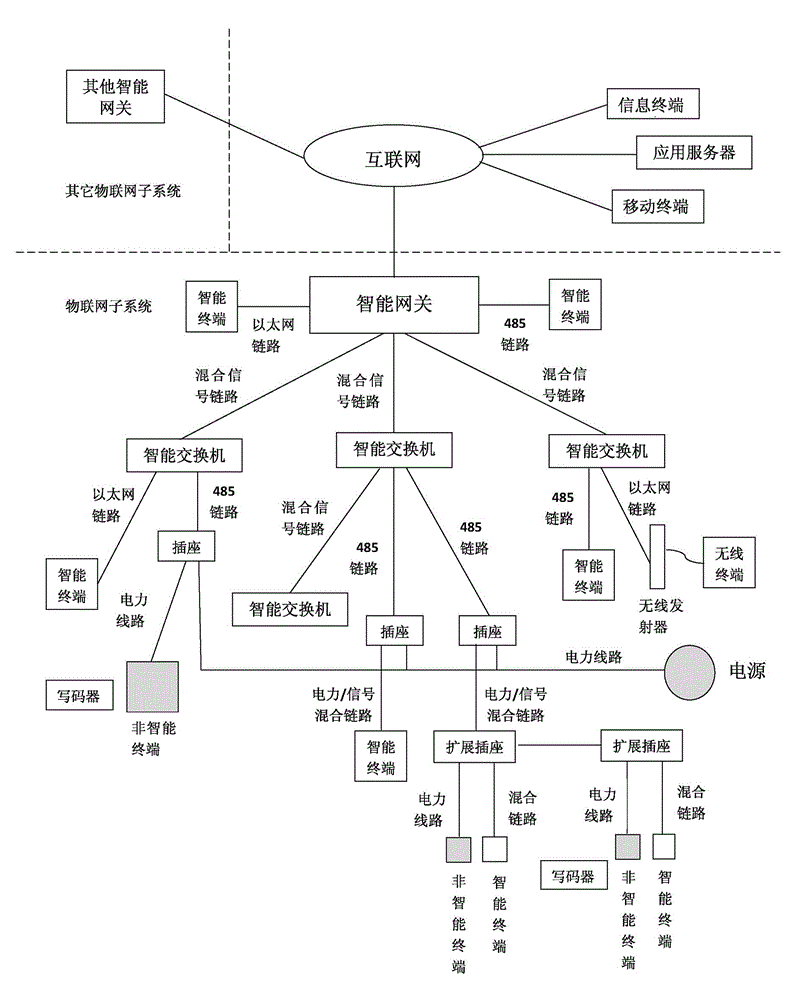
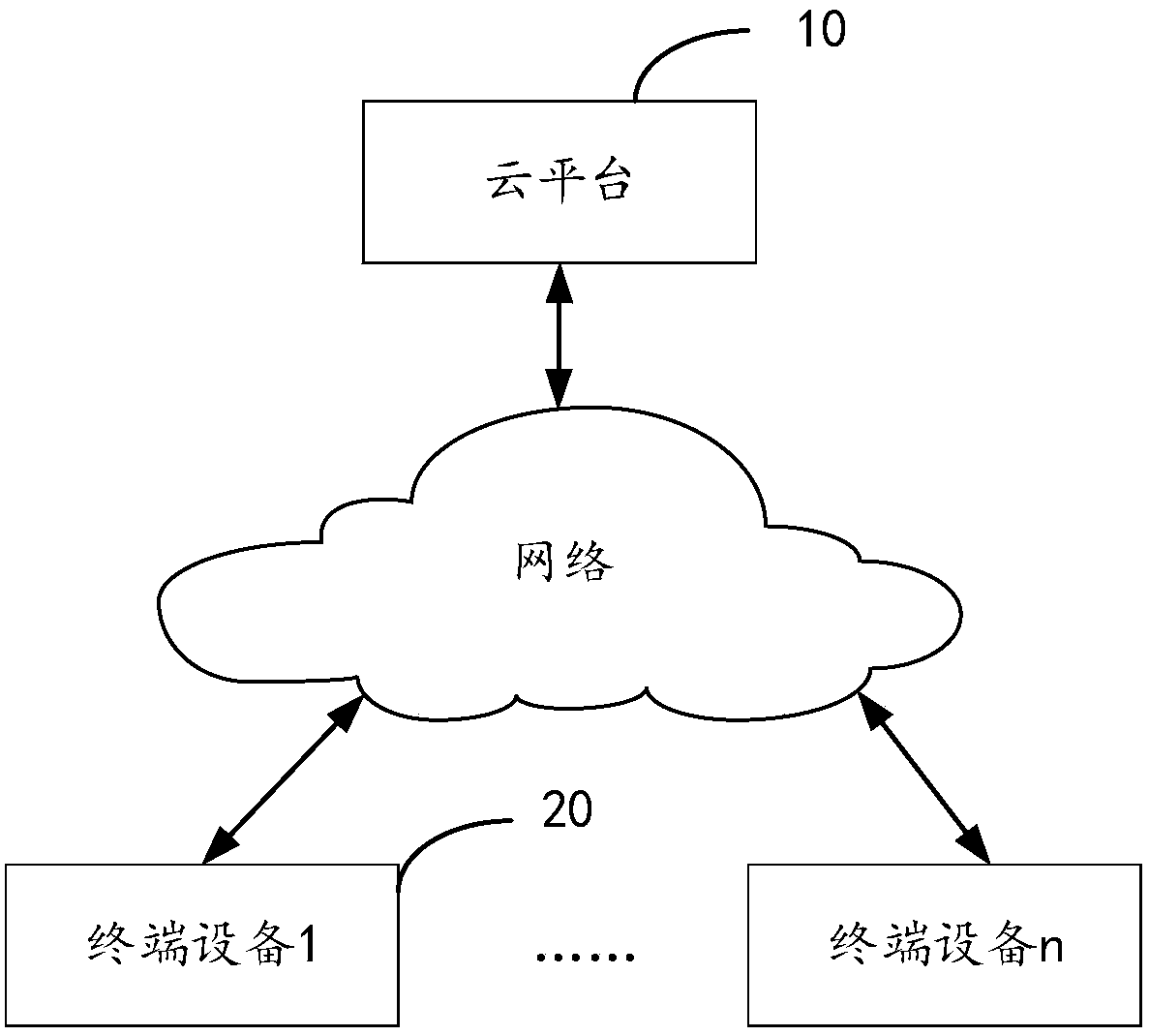
Internet-of-things system
ActiveCN104811357AImprove communication efficiencyReduce the difficulty of deploymentData switching by path configurationIntelligent NetworkNetwork connection
The invention relates to an Internet-of-things system comprising multiple Internet-of-things subsystems. The Internet-of-things subsystems can be connected with one another through an external network, and each Internet-of-things subsystem can be connected with other equipment including a server and a terminal through an external network. Each Internet-of-things subsystem includes three parts, namely, an intelligent gateway, an intelligent switch, and a piece of terminal equipment, wherein the terminal equipment can be either intelligent equipment or non-intelligent equipment, and the intelligent gateway can assign an address for both the intelligent equipment and the non-intelligent equipment. By adopting the Internet-of-things system, the problem of complex IP address assignment is avoided, and the intelligent equipment and the non-intelligent equipment can be compatible. Therefore, the efficiency of Internet-of-things communication is improved, and the difficulty in Internet-of-things deployment is reduced.
Owner:广东夏野日用电器有限公司
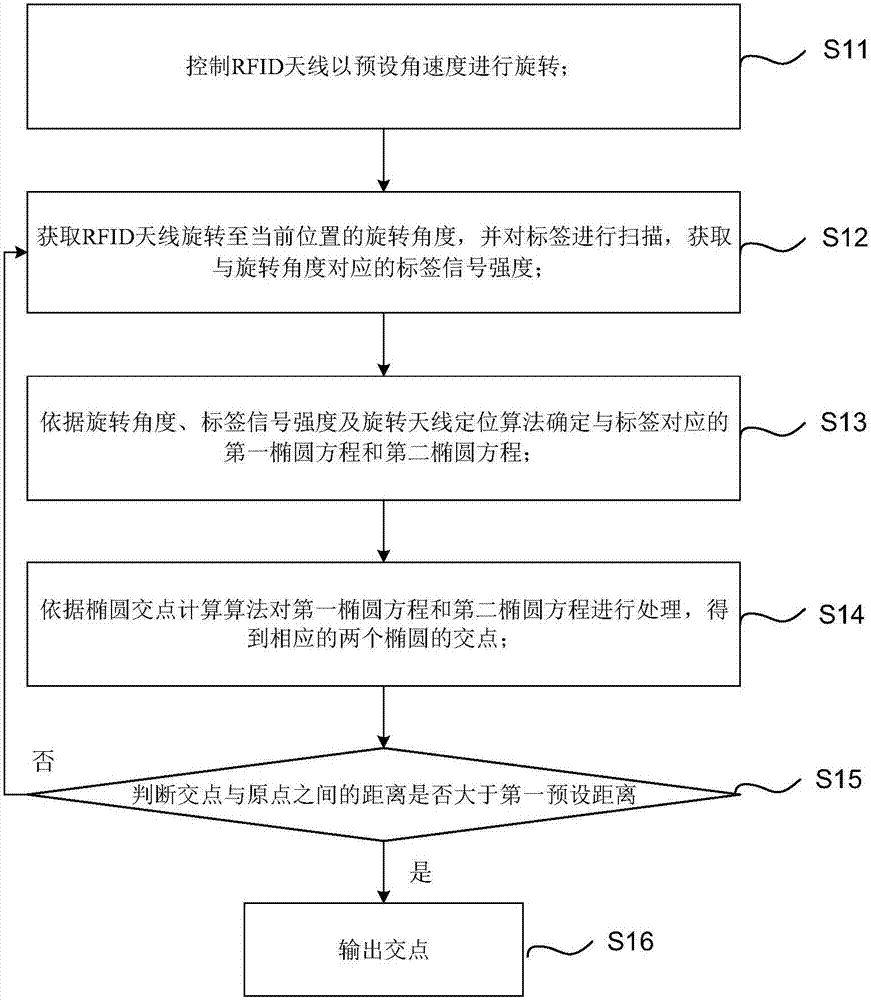
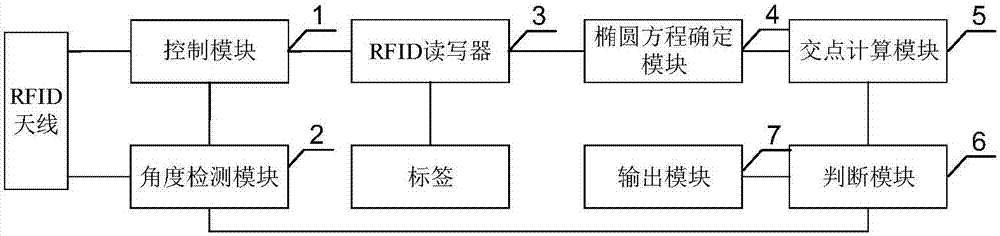
Indoor positioning method, device and system based on RFID (radio frequency identification)
ActiveCN107462249ASimple structureLow costNavigational calculation instrumentsPosition fixationSystem structureComputer science
The embodiment of the invention discloses an indoor positioning method, device and system based on RFID (radio frequency identification). The method comprises the following steps of controlling an RFID antenna to rotate at the preset angle; obtaining the rotating angle of the RFID antenna for rotating to the current position; scanning a label; obtaining the label signal intensity corresponding to the rotating angle; determining a first elliptic equation and a second elliptic equation corresponding to the label according to the rotating angle, the label signal intensity and the rotating antenna positioning algorithm; processing the first elliptic equation and the second elliptic equation according to the elliptic intersection point calculation algorithm to obtain the corresponding two elliptic intersection points; whether the distance between the intersection point and the origin is greater than the first preset distance or not; if so, the intersection point is output; otherwise, the rotating angle when the RFID antenna rotates to another position is continuously obtained, and the cyclic operation is performed until the final intersection point is obtained. The embodiment of the invention has the advantages that only one RFID antenna is used; the advantages of simple system structure, low cost, low deployment difficulty and high hardware utilization rate are realized.
Owner:GUANGDONG UNIV OF TECH
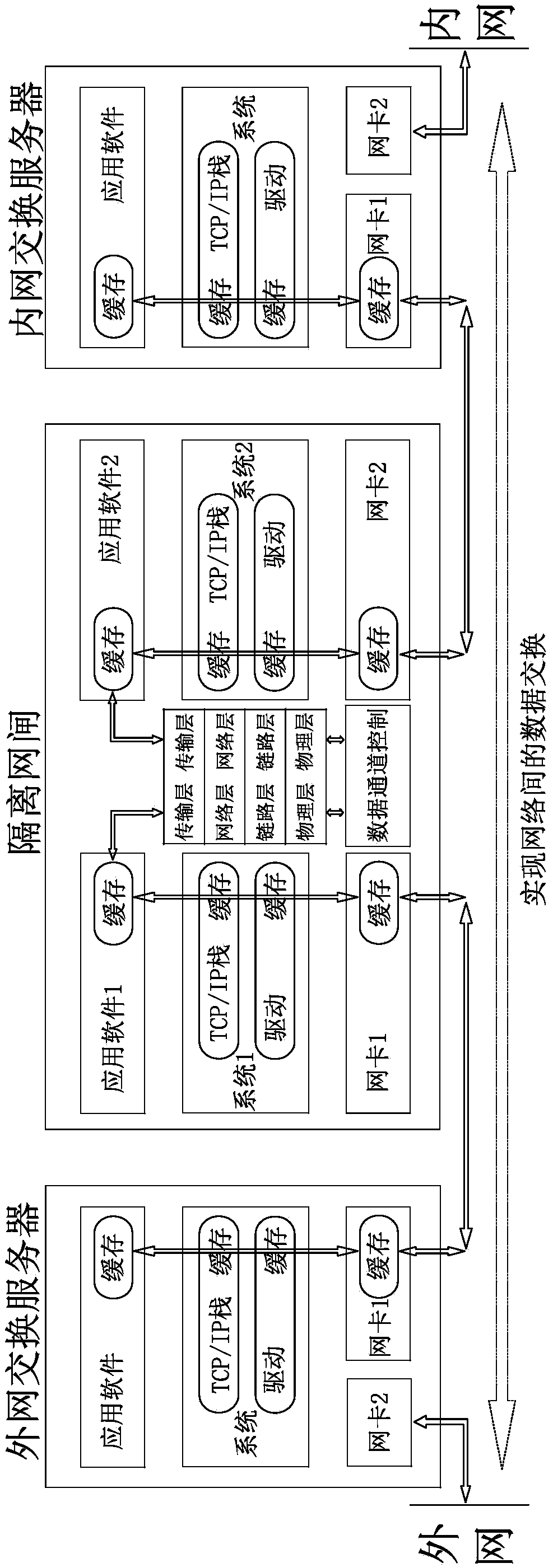
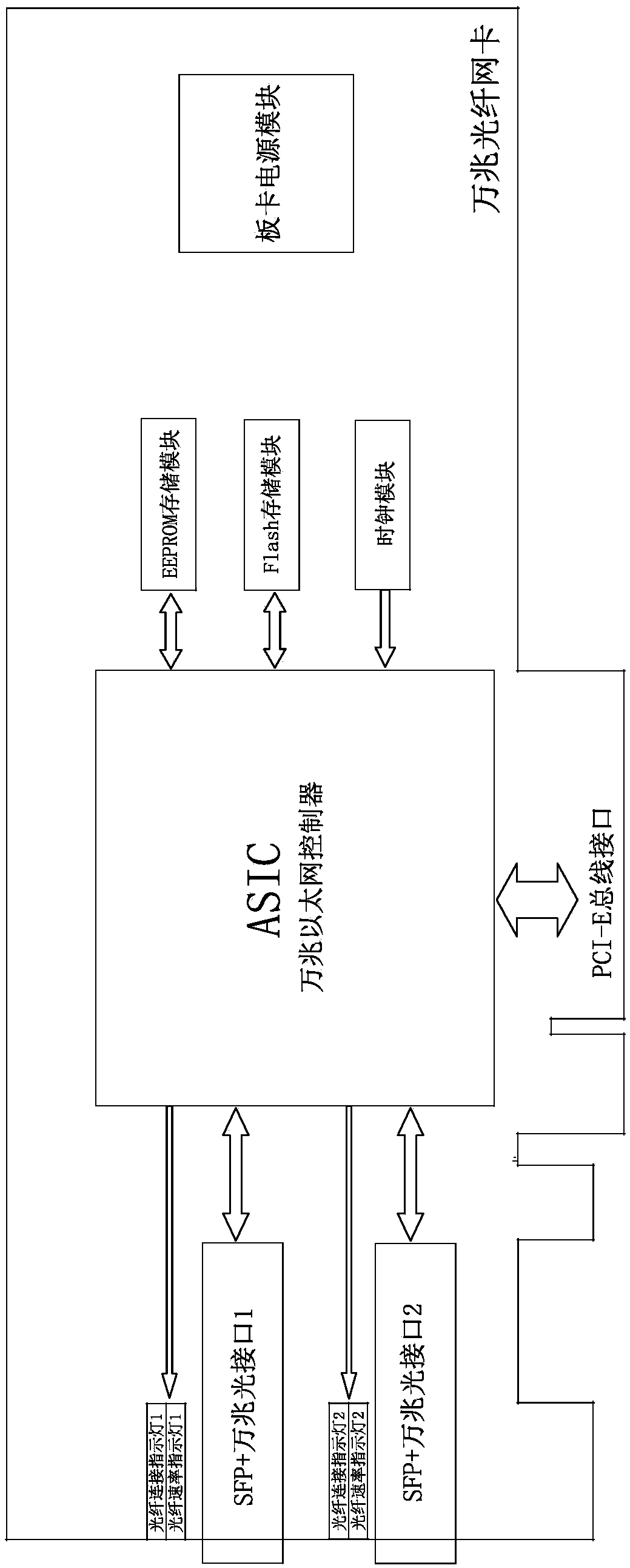
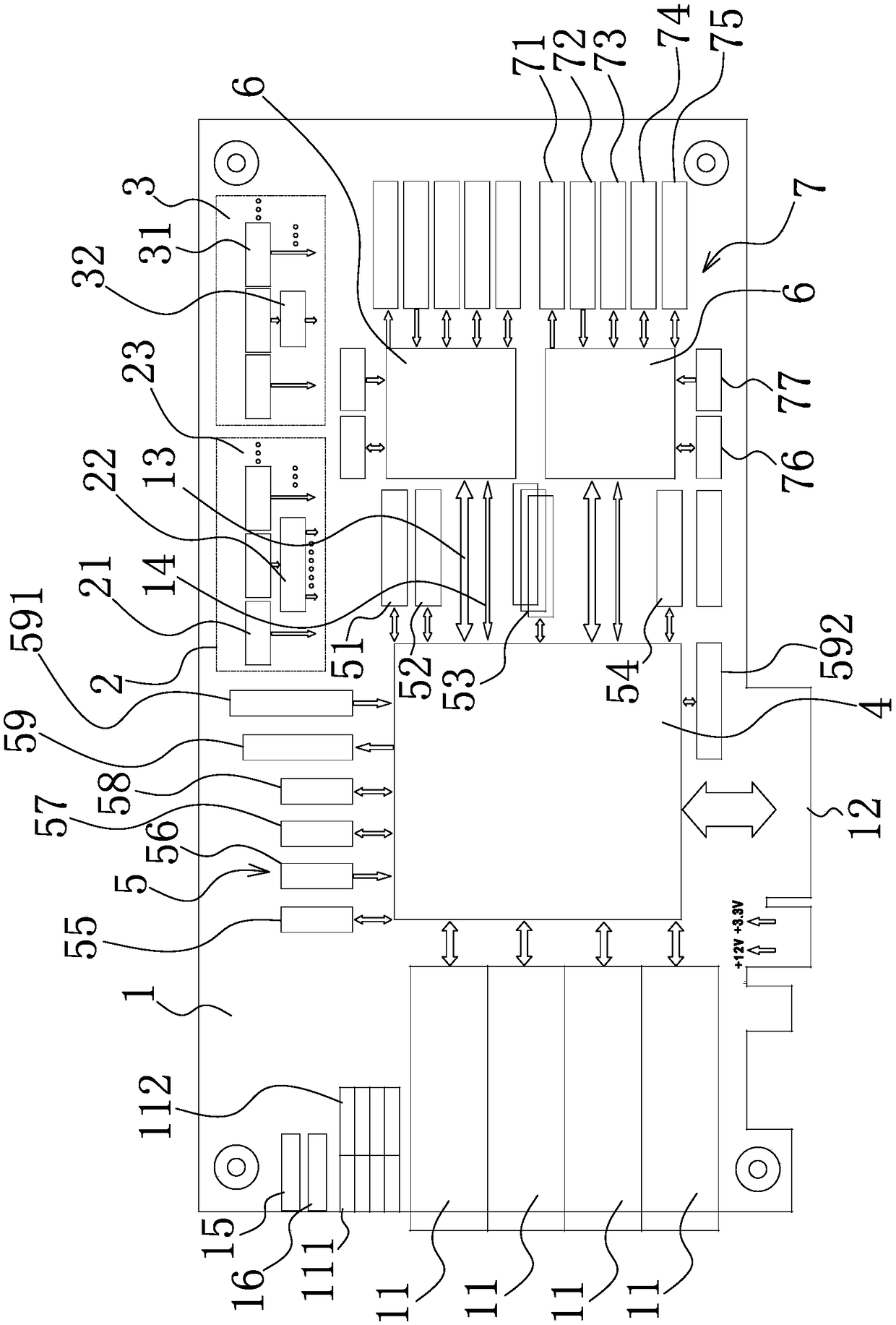
National Bureau encryption security video data exchange card and exchange method based on FPGA and DSP
PendingCN109286492AReduce consumptionImprove compatibilityKey distribution for secure communicationSelective content distributionControl setBus interface
The invention relates to a National Bureau encryption security video data exchange card and an exchange method based on FPGA and DSP, and solves the problems that an existing method is not reasonable.The National Bureau encryption security video data exchange card comprises a PCB circuit board; the PCB circuit board is provided with a clock generation and management module and a power conversionand management module; the PCB circuit board is provided with a FPGA chip that is connected with a FPGA peripheral circuit; the PCB circuit board is provided with a plurality of SFP+10 gigabit opticalports and at least one PCI-E bus interface; the FPGA chip is connected with at least two DSP processors that are connected with a DSP peripheral circuit. The advantages are that the FPGA, DSP, DMA, 10 gigabit fiber data transmission, DSP national bureau algorithm and many key technologies that support safety video stream and data exchange formats are organically combined on a security video dataexchange card; the exchange card is centralized in control, simple in structure, efficient in transmission, compatible in data formats, good in file expandability, safe and reliable in data exchange,can support an existing one-way optical gate, and can isolate a gateway system function.
Owner:BEIJING ZHONGKE FUXING INFORMATION TECH
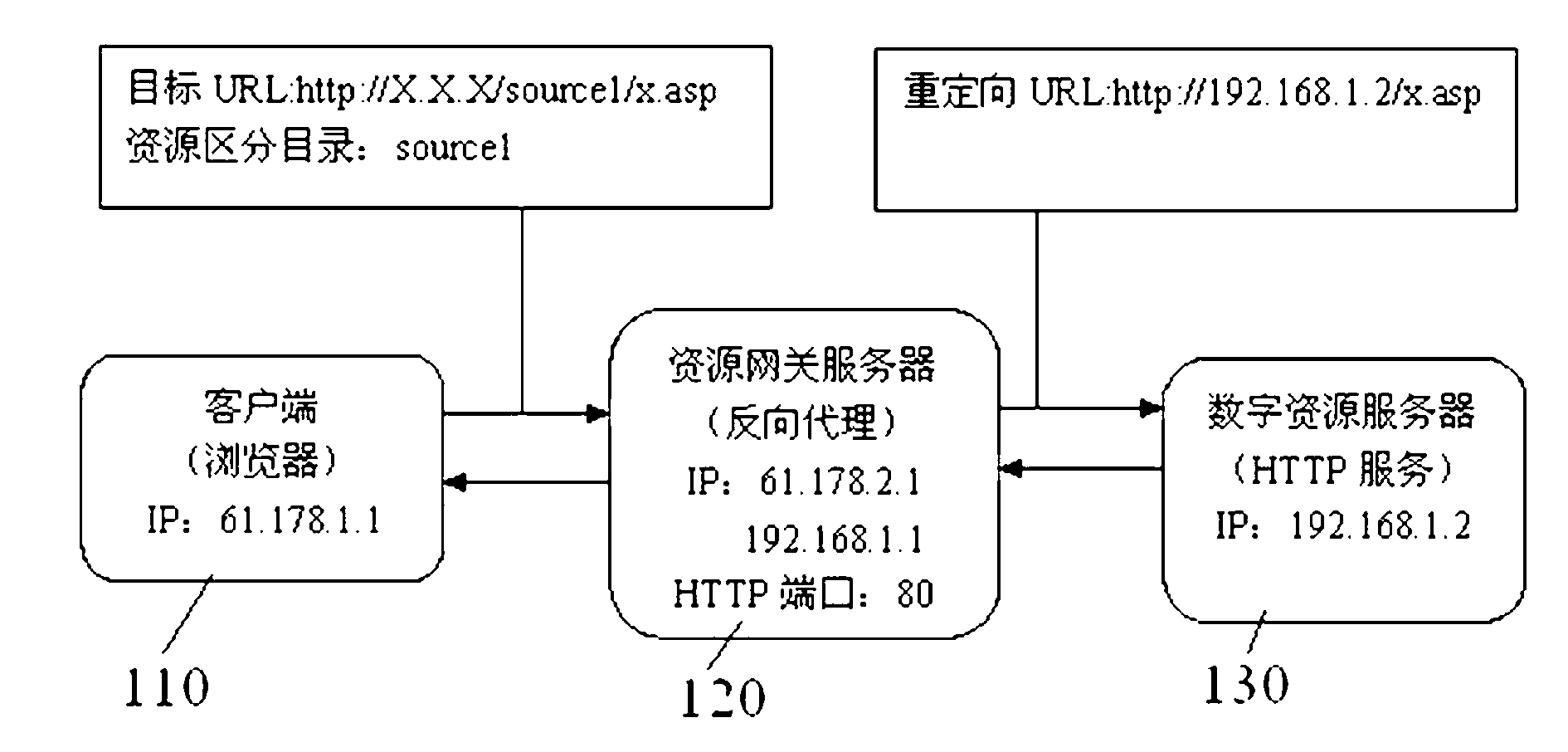
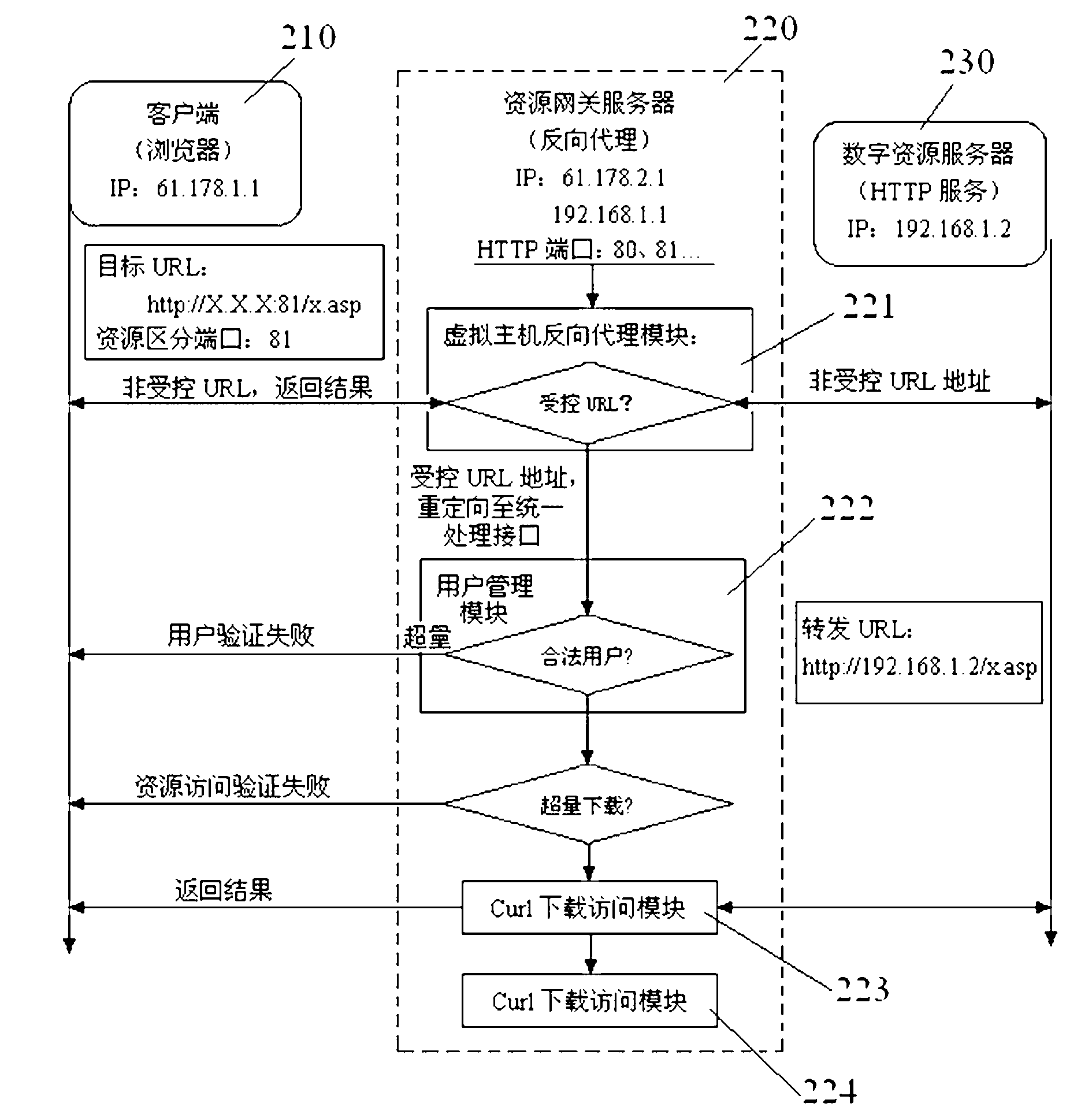
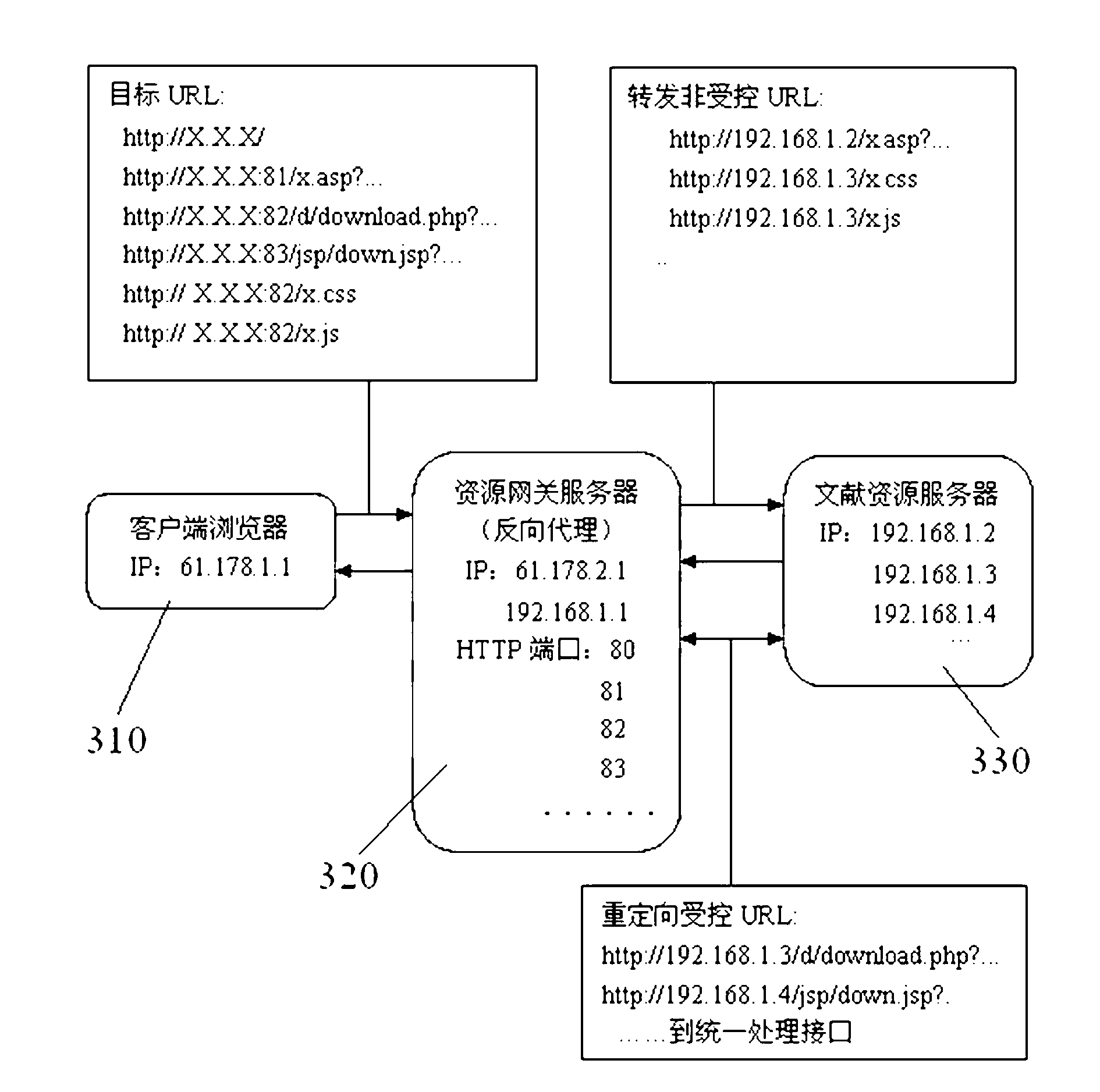
Resource gateway implementation method of digital literature adopting reverse-proxy technology
InactiveCN102710559AReduce performance lossImprove stabilityNetwork connectionsReverse proxyEngineering
The invention provides a resource gateway implementation method of digital literature adopting a reverse-proxy technology. The resource gateway implementation method of digital literature adopting the reverse-proxy technology comprises the following steps: arranging a resource gateway HTTP (Hyper Text Transfer Protocol) server provided with reverse- proxy service between a client and an internal server; establishing a virtual host allocated with a unique HTTP port for each literature resource server respectively; establishing controlled URL lists for access of each literature resource on the resource gateway HTTP respectively, unified performing redirection of addresses of the key URL addresses contain download contents according to a regular expression; determining a user download resource whether exceeds a excessive download threshold value or not, and reminding the user of no download permision if the user download resource exceeds the excessive download threshold; and performing resource download and sending the resource to the user if the user download resource is determined legal. According to the resource gateway implementation method of digital literature adopting the reverse-proxy technology, performance loss caused by the server continually redirecting addresses and the system deployment difficulty are lowered, the stability and efficiency of the resource gateway are improved, and control aging for excessive download resource is improved.
Owner:甘肃省科学技术情报研究所
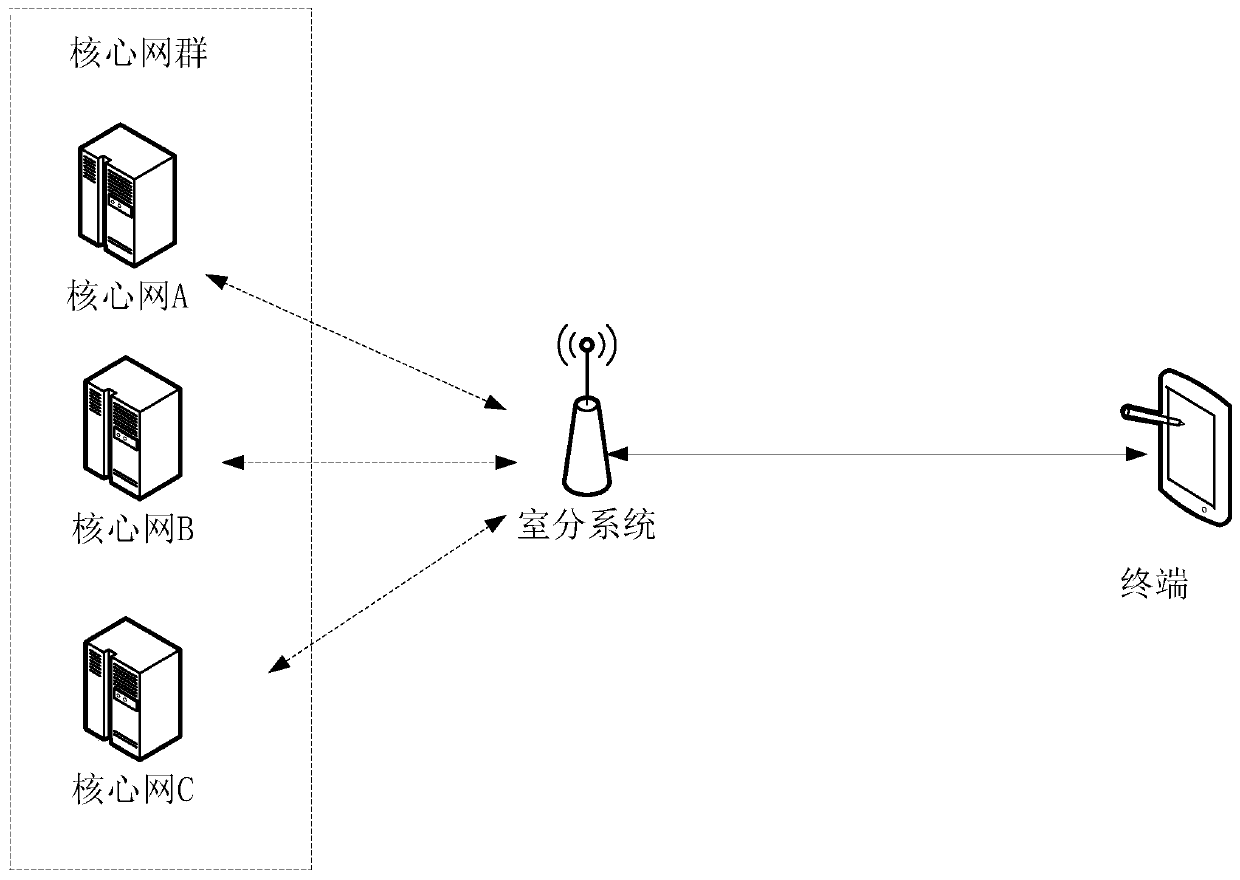
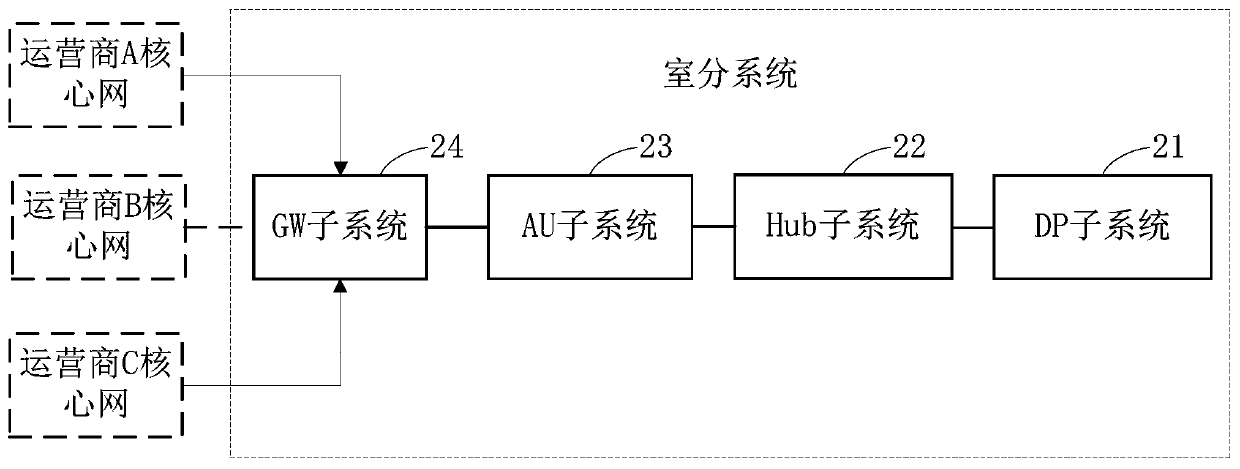
Indoor distribution system
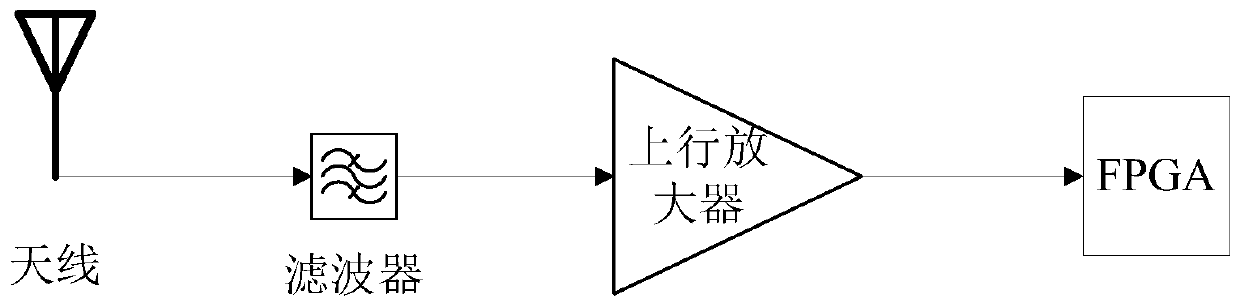
ActiveCN110417452AIncrease data transfer rateImprove stabilityRadio transmissionNetwork planningAudio power amplifierRadio frequency signal
The invention relates to an indoor distribution system, and the system comprises a DP subsystem which is used for receiving an uplink radio frequency signal transmitted by a terminal, converting the uplink radio frequency signal into a first uplink baseband digital signal, and transmitting the first uplink baseband digital signal to a Hub subsystem; an uplink radio frequency link of the DP subsystem comprises an antenna, an uplink amplifier and an uplink FPGA which are connected in sequence. The Hub subsystem is connected with the DP subsystem and used for converting the first uplink basebanddigital signal into a second uplink baseband digital signal and sending the second uplink baseband digital signal to the AU subsystem; the AU subsystem is connected with the Hub subsystem and used foranalyzing the second uplink baseband digital signal to obtain an uplink baseband signal and sending the uplink baseband signal to the GW subsystem; and the GW subsystem is connected with the AU subsystem, is connected with at least one core network of each operator in the plurality of operators, and is used for determining a target core network corresponding to the uplink baseband signal and sending the uplink baseband signal to the target core network. By adopting the indoor distribution system, co-construction and sharing of multiple operators can be realized, and the deployment difficultyand cost are reduced.
Owner:COMBA TELECOM SYST CHINA LTD +1
Information sharing platform and method thereof
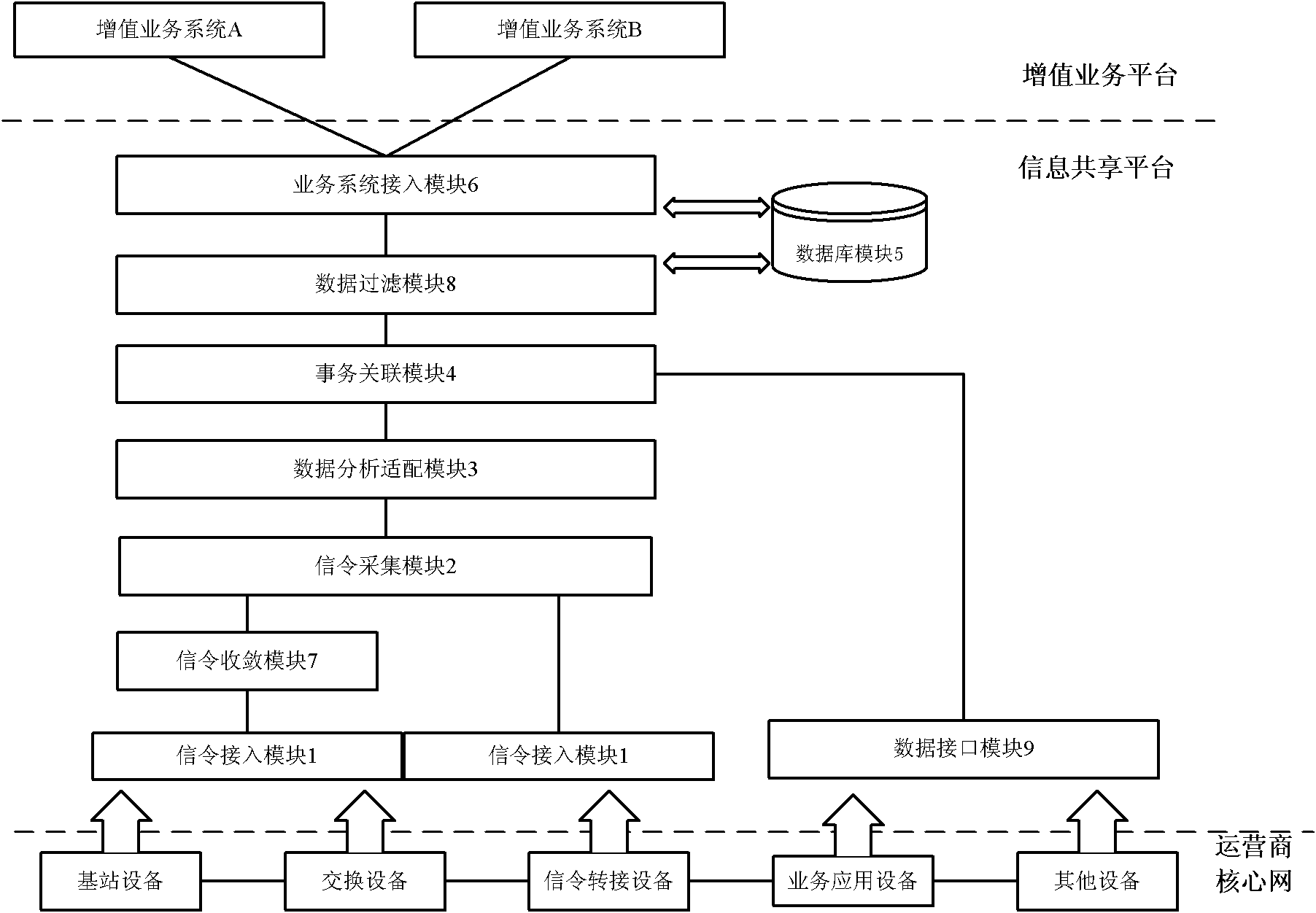
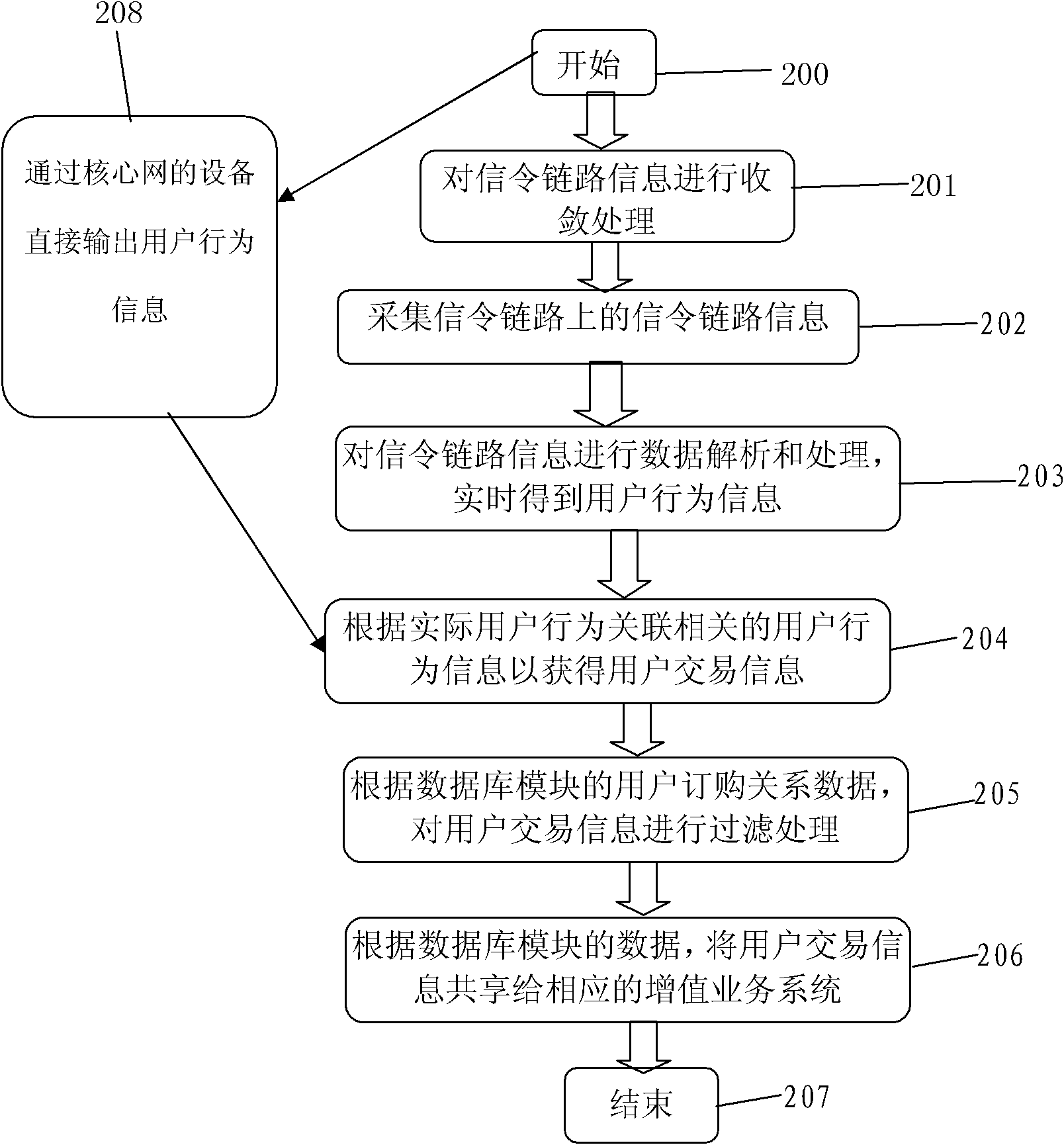
ActiveCN102378151AReduce the difficulty of deploymentEnsure minimal impactNetwork data managementInformation sharingData acquisition
The invention relates to an information sharing platform and an information sharing method. The information sharing platform comprises a signaling access module, a signaling converging module, a signaling acquiring module, a data analyzing and adapting module, an affair associating module, a data filtering module, a database module and a service system access module. The signaling access module is used for accessing the information sharing platform into a core network; the signaling converging module is used for converging signaling link information and transmitting the signaling link information to the signaling acquiring module to acquire data; the data analyzing and adapting module is used for analyzing and processing the data of the signaling link information to obtain user behavior information; the affair associating module is used for associating the related user behavior information to obtain user transaction information; and the data filtering module and the service system access module are used for sharing the user transaction information to a corresponding value added service system according to data of a database module. By the information sharing platform and the information sharing method, the value added service is complexly separated from the core network, so that the deployment difficulty of the value added service can be reduced; and the original system can be minimally influenced by adopting a safe and reliable access mode.
Owner:SHENZHEN YETUOXUN COMM TECH
Induction motor electrical fault diagnosis method based on magnetic leakage signal
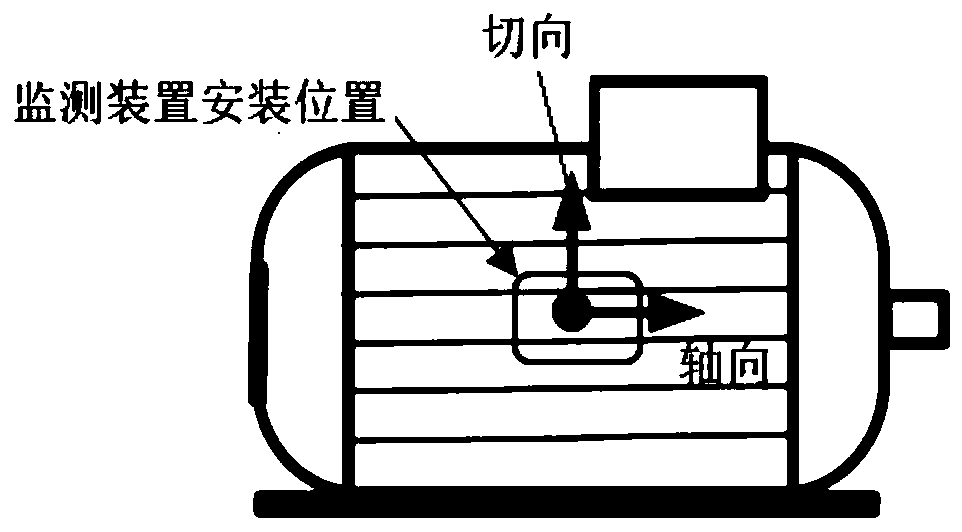
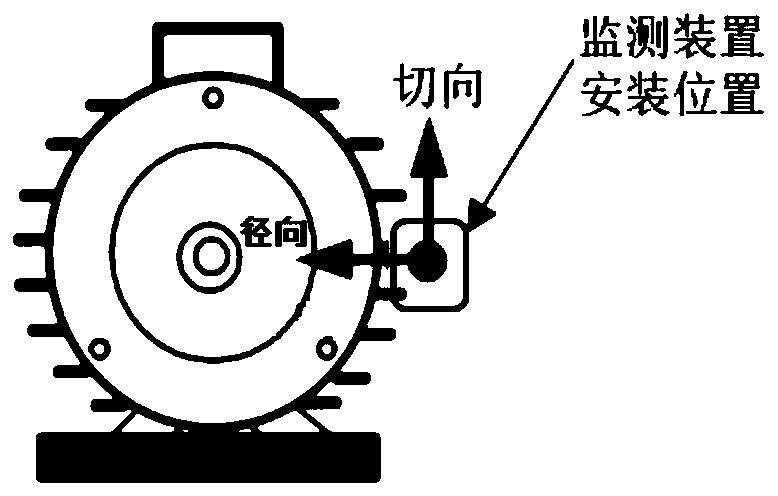
ActiveCN110531259AReduce deployment difficulty and system costSensitive to electrical faultsDynamo-electric machine testingDiagnosis methodsFailure diagnosis
The invention discloses an induction motor electrical fault diagnosis method based on a magnetic leakage signal. A magnetic leakage sensor is adopted to collect the three-axis magnetic leakage signalof an induction motor; a vibration sensor is adopted to collect a motor shell vibration signal of the motor; then the collected signals are analyzed to judge whether the motor breaks down or not; thefault type of the motor is judged; the magnetic leakage signal indirectly reflects the change condition of an air gap magnetic field and is sensitive to an electrical fault; compared with current monitoring, the magnetic leakage monitoring method also has the advantages of convenience in signal acquisition, low acquisition cost and the like; under the condition that normal operation of the motor is not affected, the magnetic leakage signal outside the motor shell is collected to identify the electrical fault of the motor; and therefore, the method has the advantages of convenience in signal acquisition, low signal acquisition cost and the like.
Owner:XI AN JIAOTONG UNIV
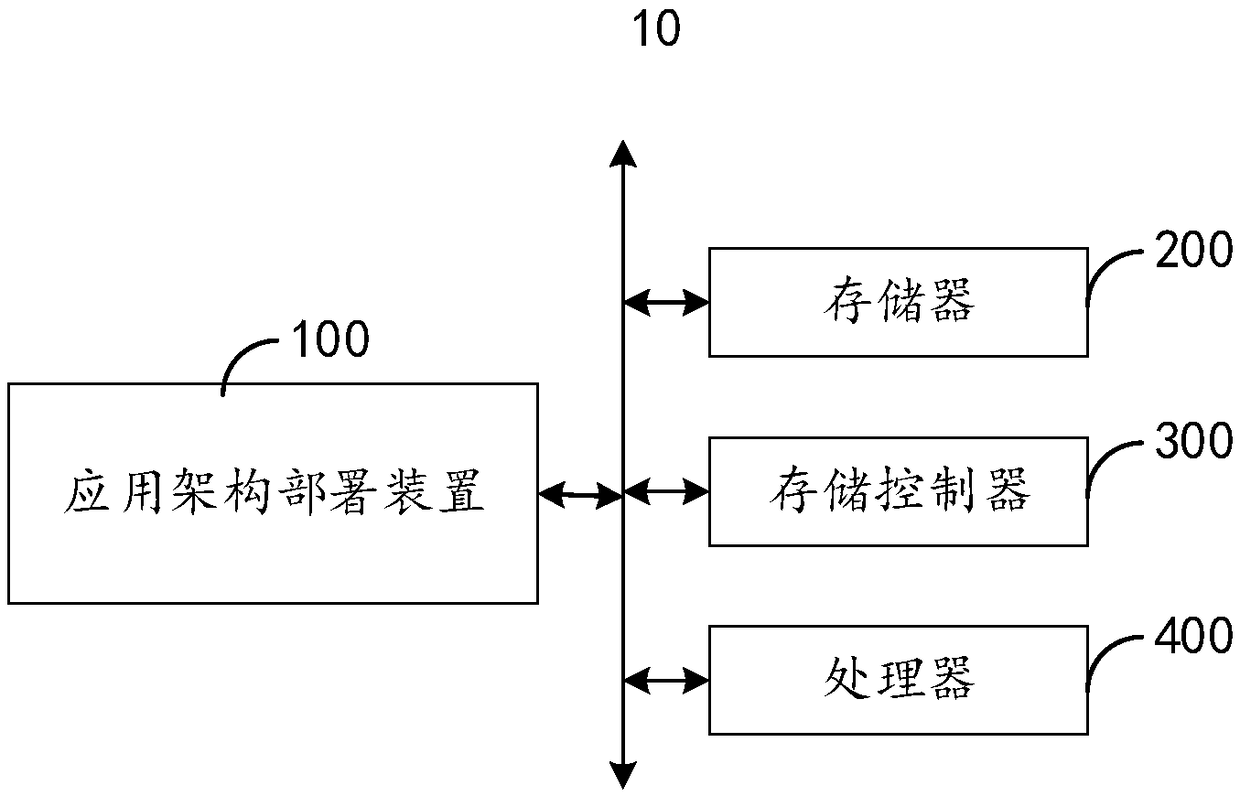
Application framework deployment method, apparatus and system, and cloud platform
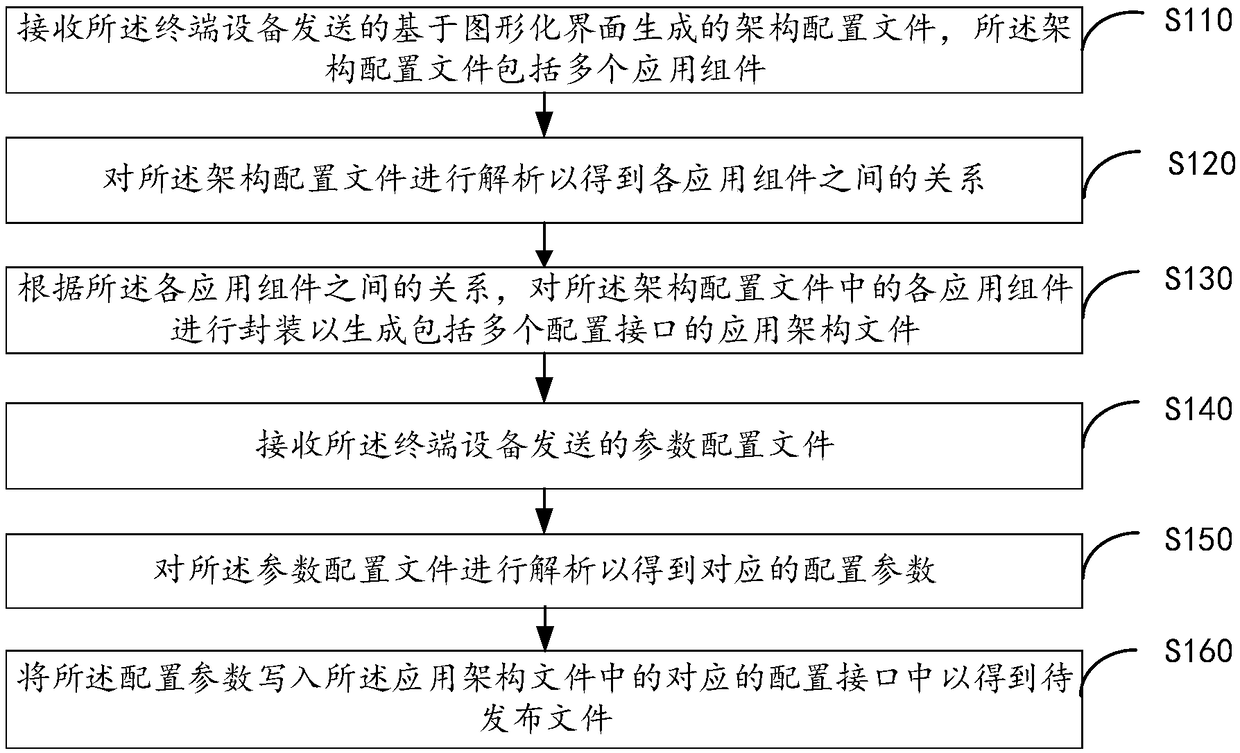
InactiveCN108196764AReduce the difficulty of deploymentReduce the difficulty of operation and maintenanceSoftware deploymentInput/output processes for data processingTerminal equipmentOperating system
Embodiments of the invention provide an application framework deployment method, apparatus and system, and a cloud platform. The method comprises the steps of receiving a framework configuration filegenerated according to application components in an initial application framework and sent by a terminal device; analyzing the framework configuration file to obtain a relationship among the application components; and according to the relationship among the application components, packaging the application components in the framework configuration file to generate an application framework file comprising multiple configuration interfaces. Therefore, the application framework deployment and maintenance difficulty can be effectively lowered; and the application framework deployment demands in different business scenes can be met.
Owner:CHINAUMS
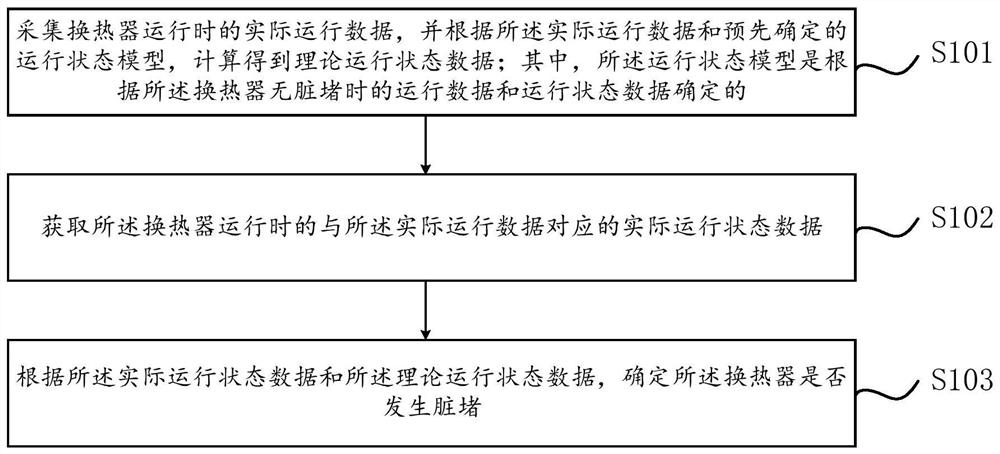
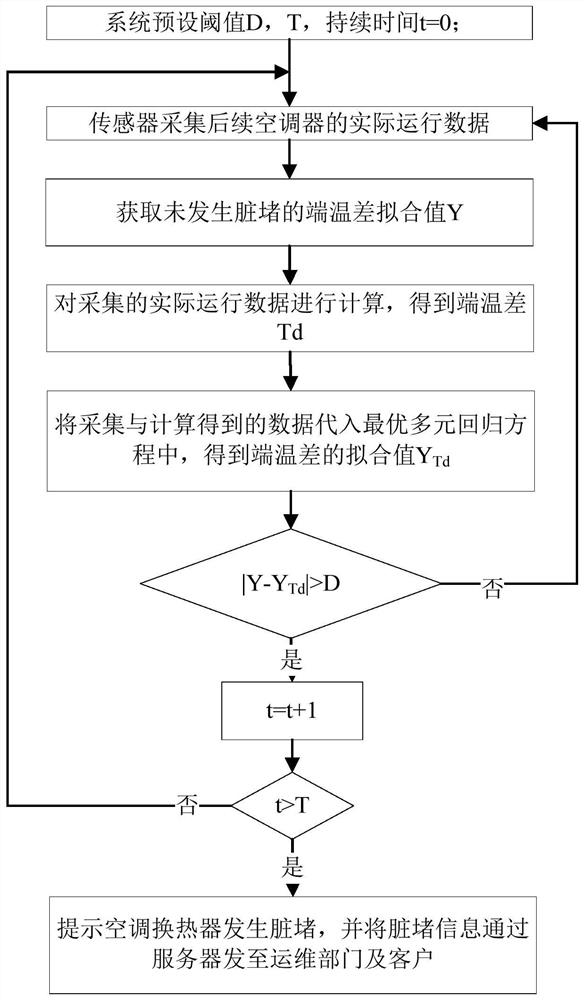
Heat exchanger filth blockage detection method and device
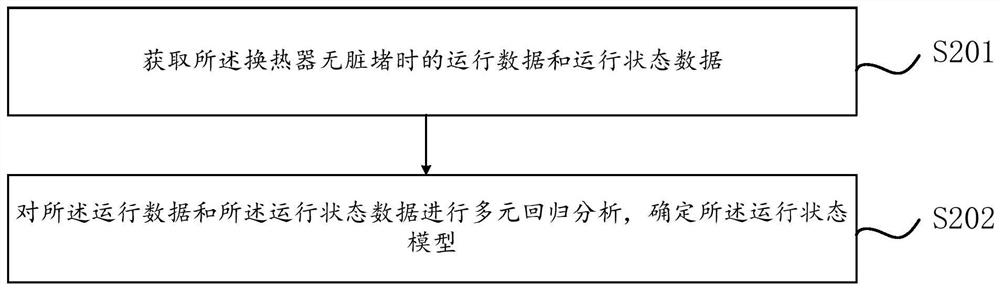
ActiveCN111811108AReduce configuration requirementsReduce time complexityMechanical apparatusProcess engineeringHeat exchanger
The invention relates to a heat exchanger filth blockage detection method and device. The method comprises the steps of collecting the actual operation data of a heat exchanger during operation, and obtaining the theoretical operation state data through calculation according to the actual operation data and a predetermined operation state model, wherein the operation state model is determined according to operation data and operation state data when the heat exchanger is not blocked by dirt; acquiring actual operation state data corresponding to the actual operation data when the heat exchanger operates; and according to the actual operation state data and the theoretical operation state data, determining whether filth blockage occurs to the heat exchanger. According to the method, the filth blockage degree of the unit heat exchanger can be judged based on historical data, the judgment effect and the detection speed are improved, the problems of too large algorithm error and insufficient stability caused by few monitored operating parameters are solved, the accuracy of filth blockage judgment of the heat exchanger is improved, and the development trend can be summarized through historical operation data and real-time operation data, so that the filth blockage condition of the heat exchanger in the future is accurately predicted.
Owner:GREE ELECTRIC APPLIANCES INC
Method and device for realizing terminal called service restoration
ActiveCN106488475AReduce overheadReduce the difficulty of deploymentTransmissionWireless communicationComputer terminalService restoration
The invention discloses a method and a device for realizing terminal called service restoration. Triggering of a terminal to re-register a standby P-CSCF via a PCRF is not needed, deployment difficulty is reduced, and resource is saved. The method comprises steps in that, a standby P-CSCF / SBC receives a request message sent by an S-CSCF, and the request message is generated when a fault of the P-CSCF / SBC appears, wherein the P-CSCF / SBC is registered by a user terminal corresponding to a called request received by the S-CSCF; the standby P-CSCF / SBC determines a home gateway of the user terminal according to a mapping relationship between pre-established gateways and user terminals belonging to the gateways; and the standby P-CSCF / SBC sends a trigger message to the home gateway via a TWAMP link between the standby P-CSCF / SBC and the home gateway, and the trigger message is used to trigger the user terminal to re-register to the standby P-CSCF / SBC to carry the called service of the user terminal.
Owner:HUAWEI TECH CO LTD
Temperature measurement method and device, server and temperature measurement system
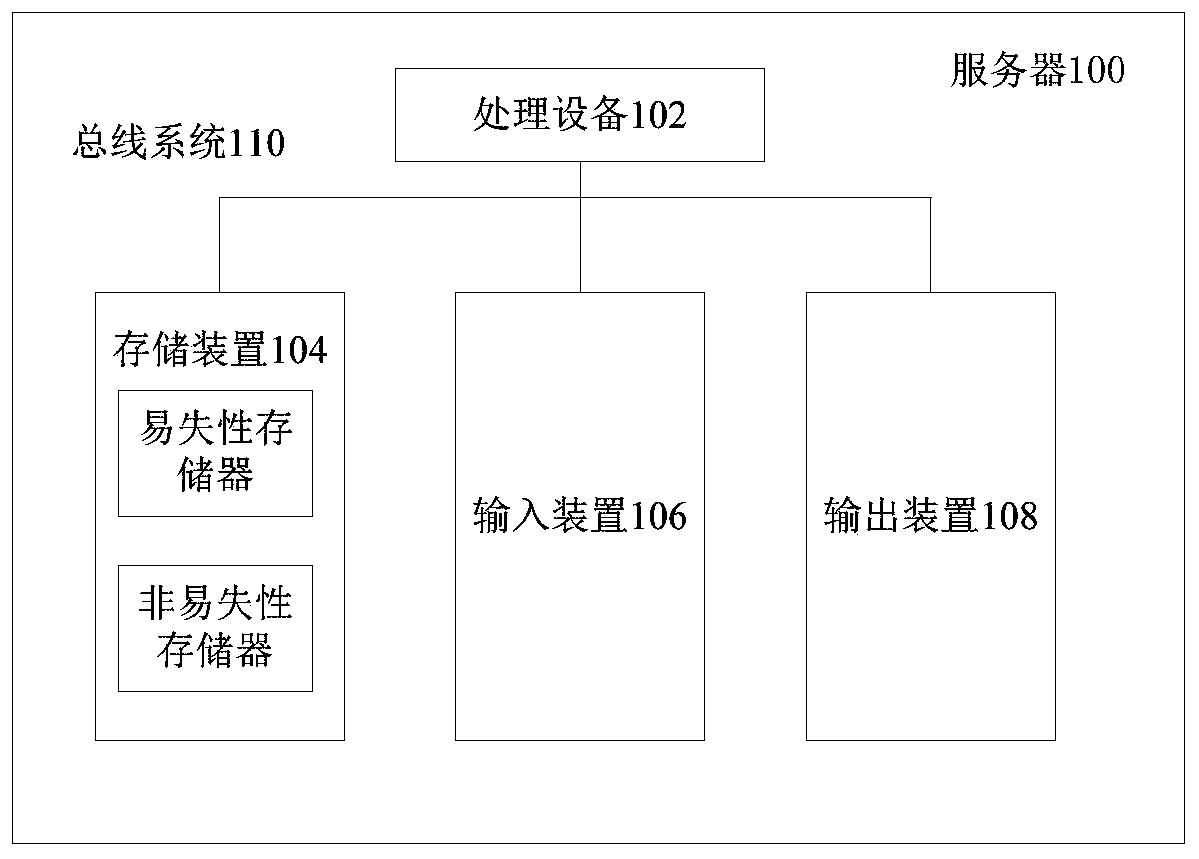
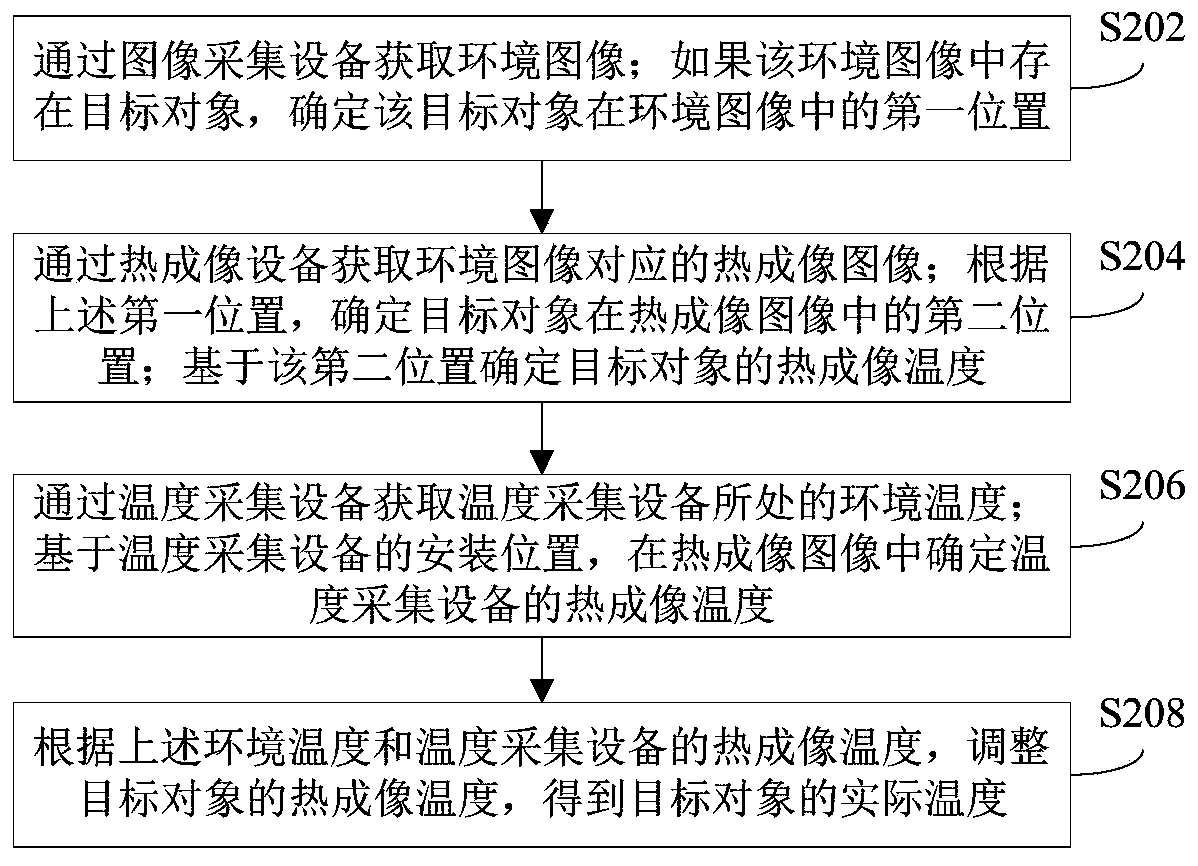
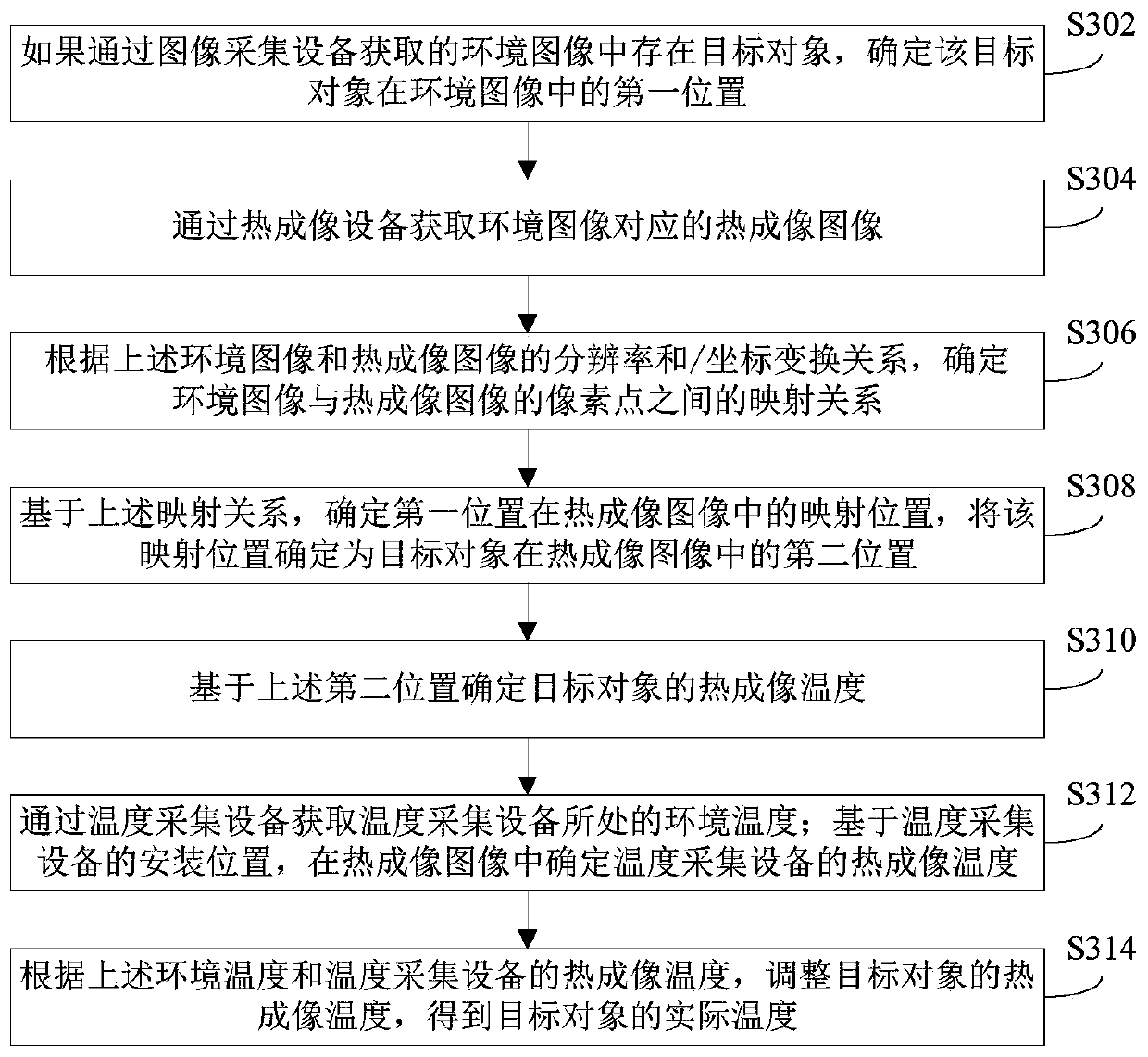
PendingCN111157123AAvoid defectsGuaranteed temperature measurement accuracyRadiation pyrometryImage pairImaging equipment
The invention provides a temperature measurement method and device, a server and a temperature measurement system. The method comprises the steps of detecting a target object from an environment imageobtained by image acquisition equipment, and determining a first position of the target object; obtaining a thermal imaging image corresponding to the environment image through thermal imaging equipment, and determining a thermal imaging temperature of the target object based on the first position; acquiring an environment temperature through temperature acquisition equipment; and adjusting the thermal imaging temperature of the target object according to the environment temperature and the thermal imaging temperature of the temperature acquisition equipment in the thermal imaging image to obtain the actual temperature of the target object. According to the method, the temperature drift of the thermal imaging equipment is corrected through the environment temperature and the thermal imaging temperature of the temperature acquisition equipment, and the accurate actual temperature of the target object can be obtained based on the thermal imaging temperature of the target object. In addition, the method employs the temperature acquisition equipment to replace a conventional black body so as to avoid defects of the black body, so that the method improves the robustness and reduces thedeployment difficulty while guaranteeing the temperature measurement precision.
Owner:MEGVII BEIJINGTECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com