Identifying malicious devices within a computer network
A computing device and device technology, applied in the field of computing systems, can solve problems such as signature failures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
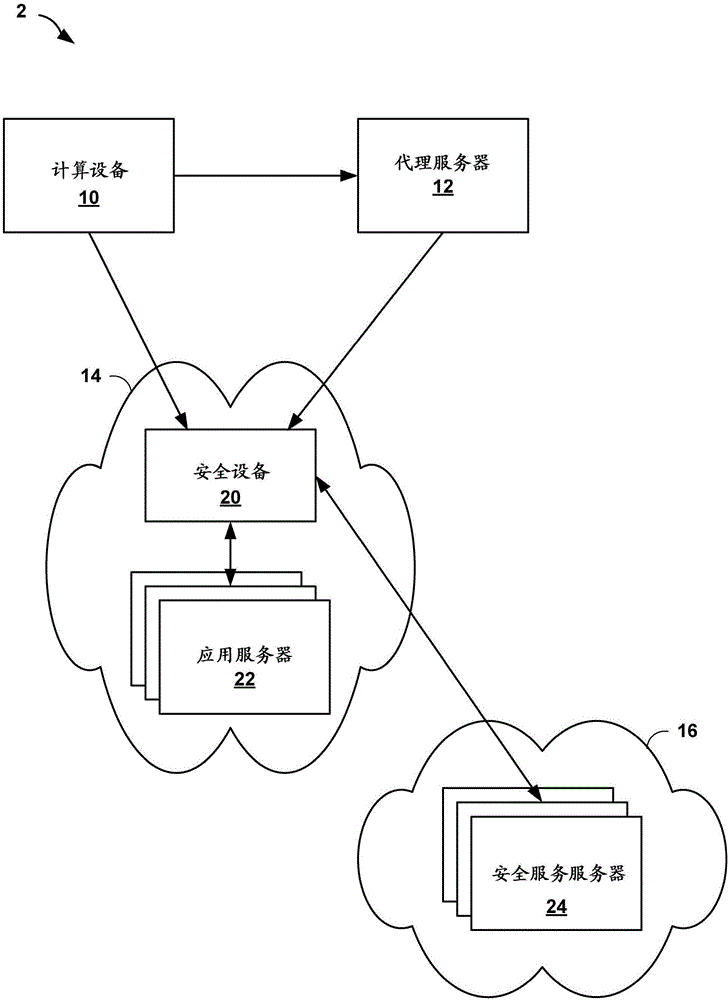
[0014] figure 1 is a block diagram illustrating an example rogue device identification network system 2 in accordance with one or more aspects of the present disclosure. like figure 1 As shown in , network system 2 includes computing device 10 , proxy server 12 , target network 14 , and security service 16 . Computing device 10 is one example of a computing device that may be used to attack network resources of a target network or data center. In some examples, computing device 10 is a mobile station, laptop computer, desktop computer, or server computing system, or may include multiple computing devices. For example, computing device 10 may be a group of computing devices over which an attacker has control (eg, because the attacker previously hijacked those computing devices). In some examples, computing device 10 is a virtual machine or software application (eg, web browser, attacker tool, script, etc.) executed by one or more computing devices.
[0015] Computing device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com