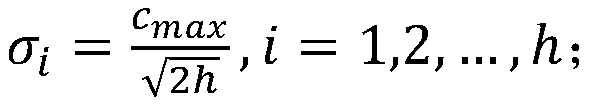Patents
Literature
60 results about "Adapter (computing)" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
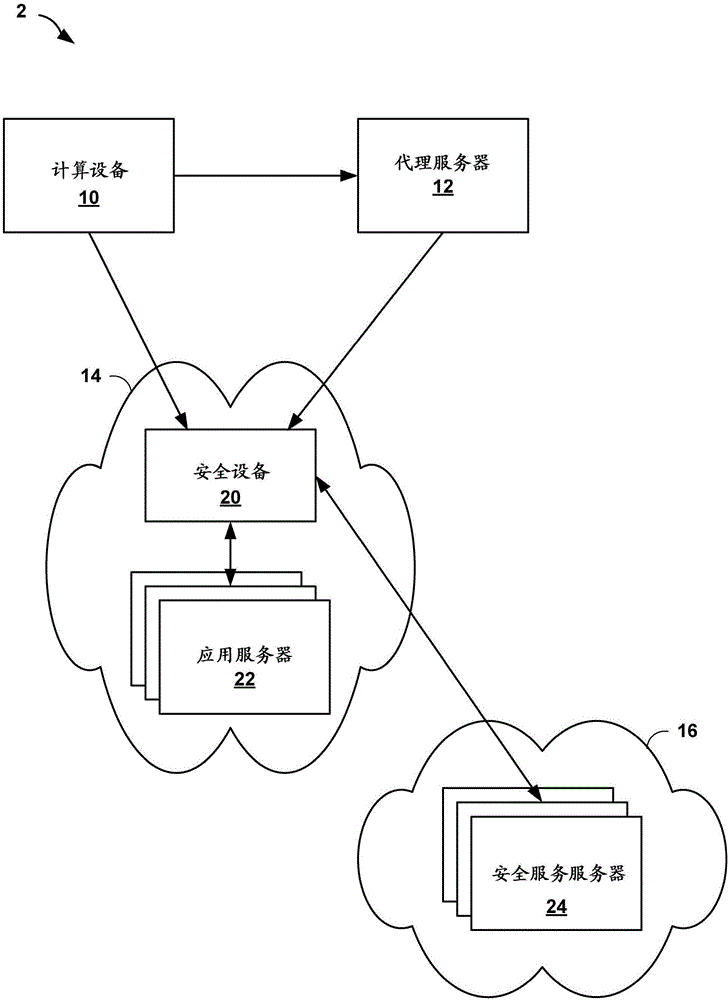
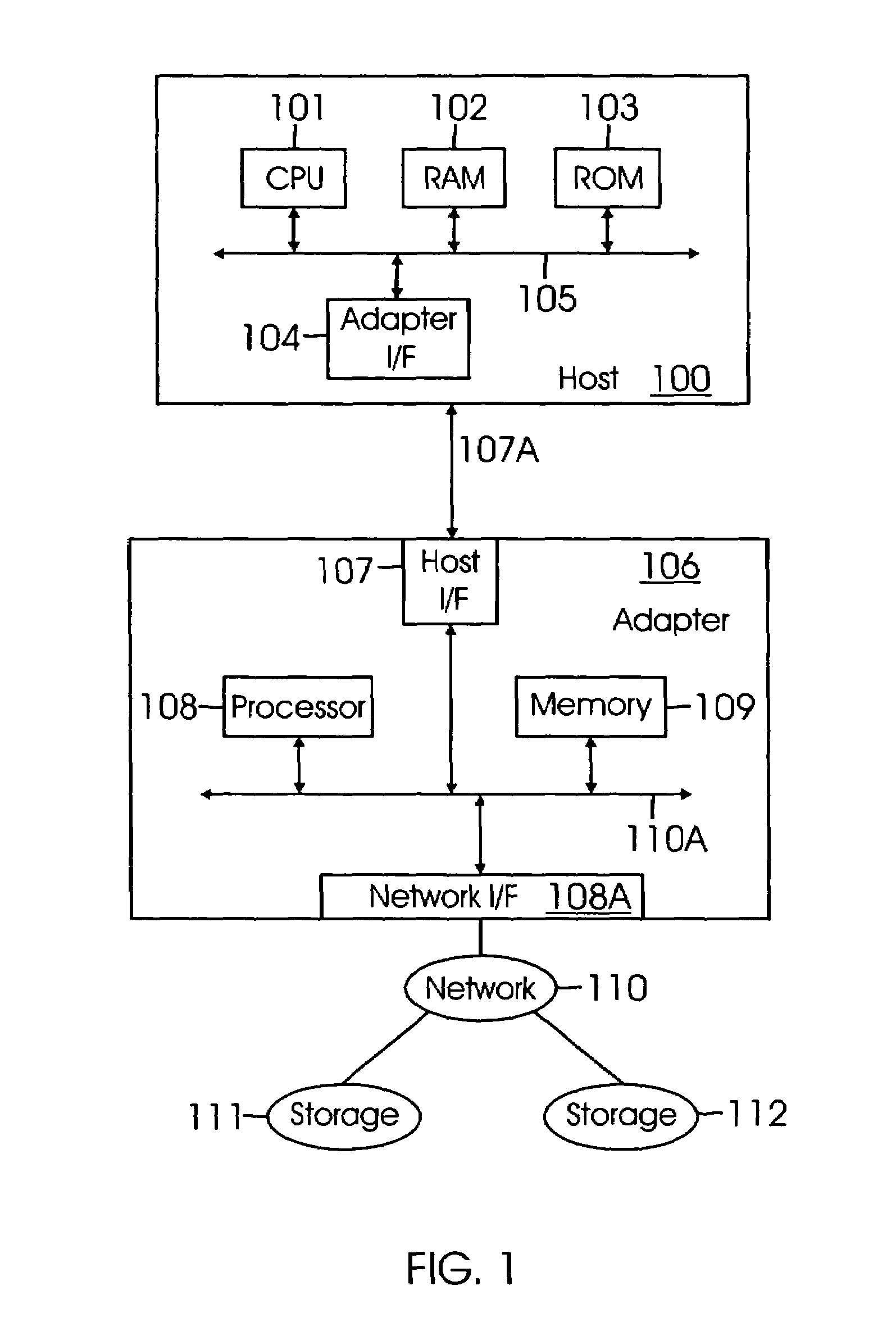
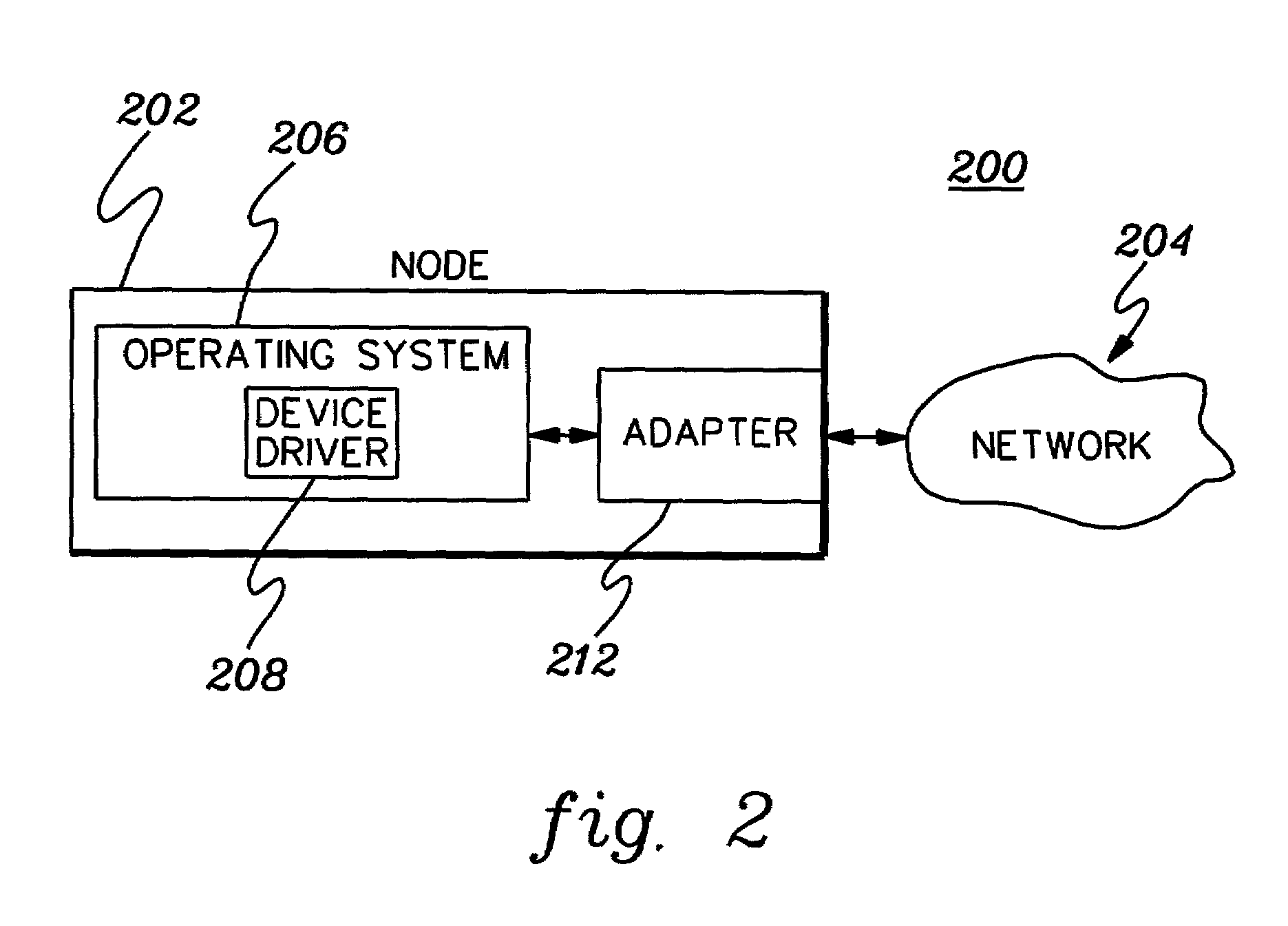
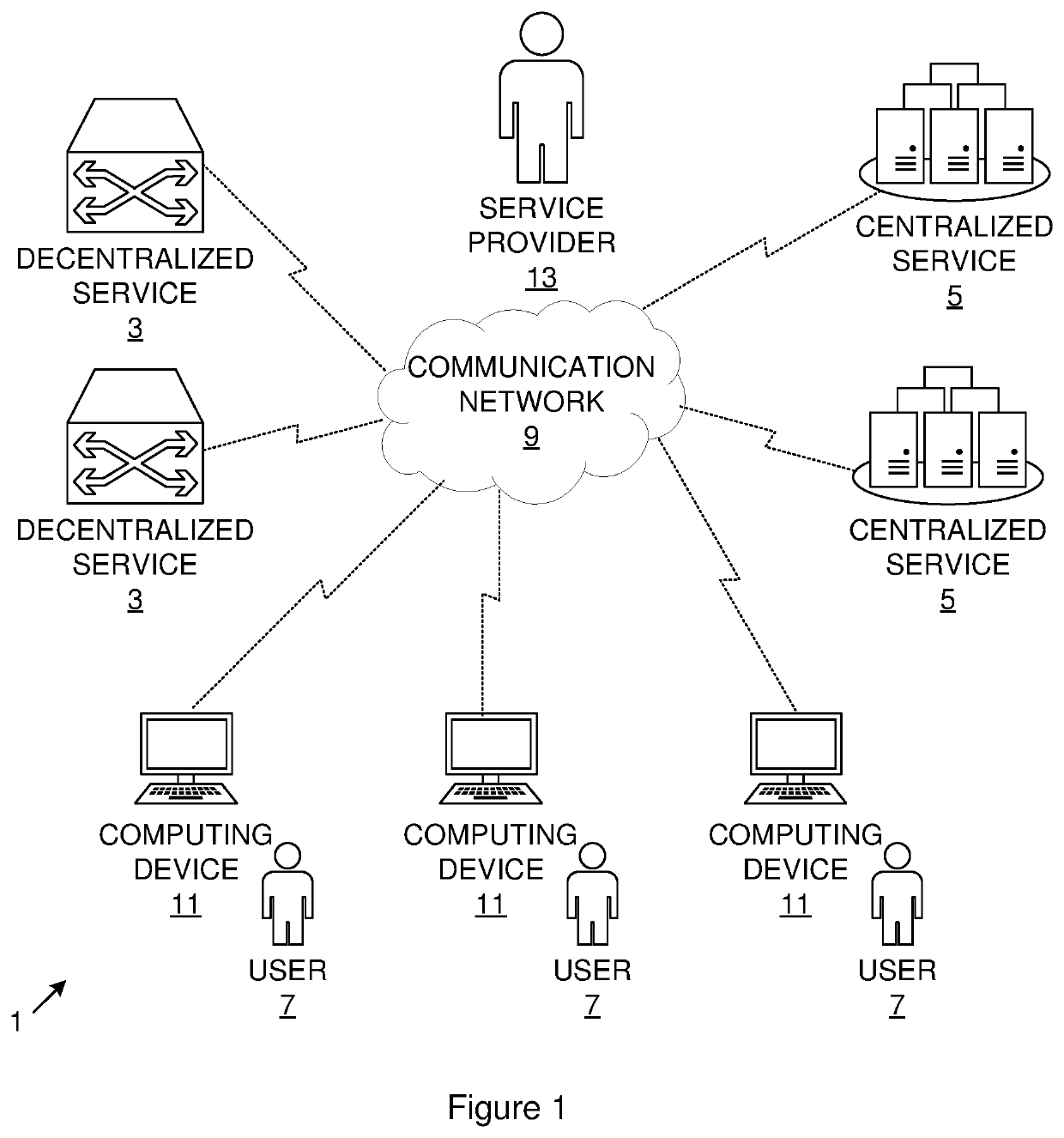
An adapter in regard to computing can be either a hardware component (device) or software that allows two or more incompatible devices to be linked together for the purpose of transmitting and receiving data. Given an input, an adapter alters it in order to provide a compatible connection between the components of a system. Both software and hardware adapters are used in many different devices such as mobile phones, personal computers, servers and telecommunications networks for a wide range of purposes. Some adapters are built into devices, while the others can be installed on a computer's motherboard or connected as external devices.
Network packet payload compression
ActiveUS8001278B2Energy efficient ICTMultiple digital computer combinationsPayload (computing)Term memory
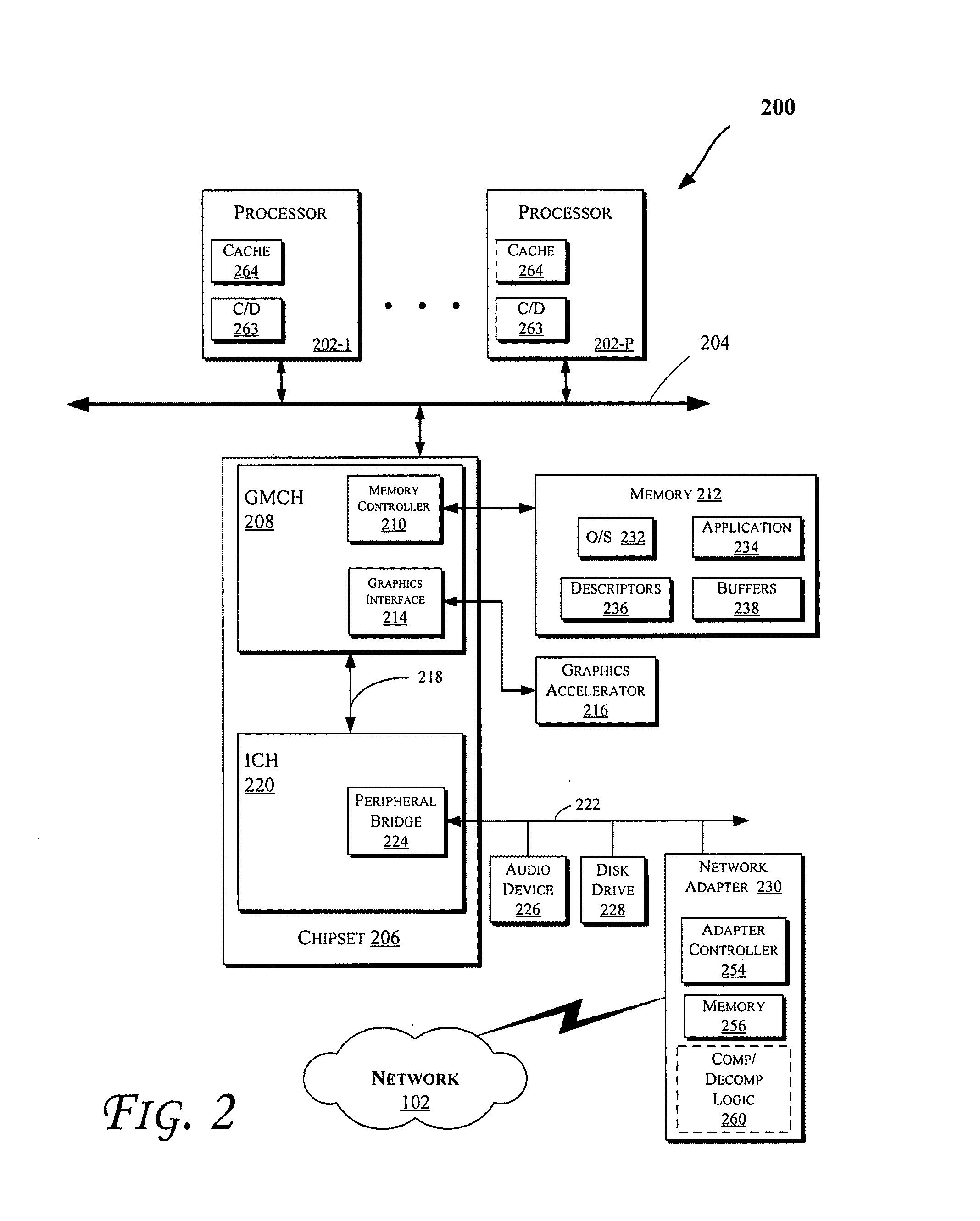
Methods and apparatus relating to network packet payload compression / decompression are described. In an embodiment, an uncompressed packet payload may be compressed before being transferred between various components of a computing system. For example, a packet payload may be compressed prior to transfer between network interface cards or controllers (NICs) and storage devices (e.g., including a main system memory and / or cache(s)), as well as between processors (or processor cores) and storage devices (e.g., including main system memory and / or caches). Other embodiments are also disclosed.
Owner:INTEL CORP
Method and system for quality of service in host bus adapters
Method and system for an adapter coupled to a network via a network link is provided. The method includes using a first selectable mode and a second selectable mode to provide quality of service to a plurality of applications executed by one or more computing system. In the first selectable mode, the quality of service is based on allocating bandwidth of the network link and dynamically adjusting an initial priority assigned to a plurality of queues, each queue being associated with an application from among a plurality of applications. In the second selectable mode, the quality of service is based on a user assigning a priority to each of the plurality of applications and the adapter determines a number of input / output (I / O) requests it needs to process within a duration and then transfers information based on the determined number of I / O requests and the assigned priority.
Owner:MARVELL ASIA PTE LTD
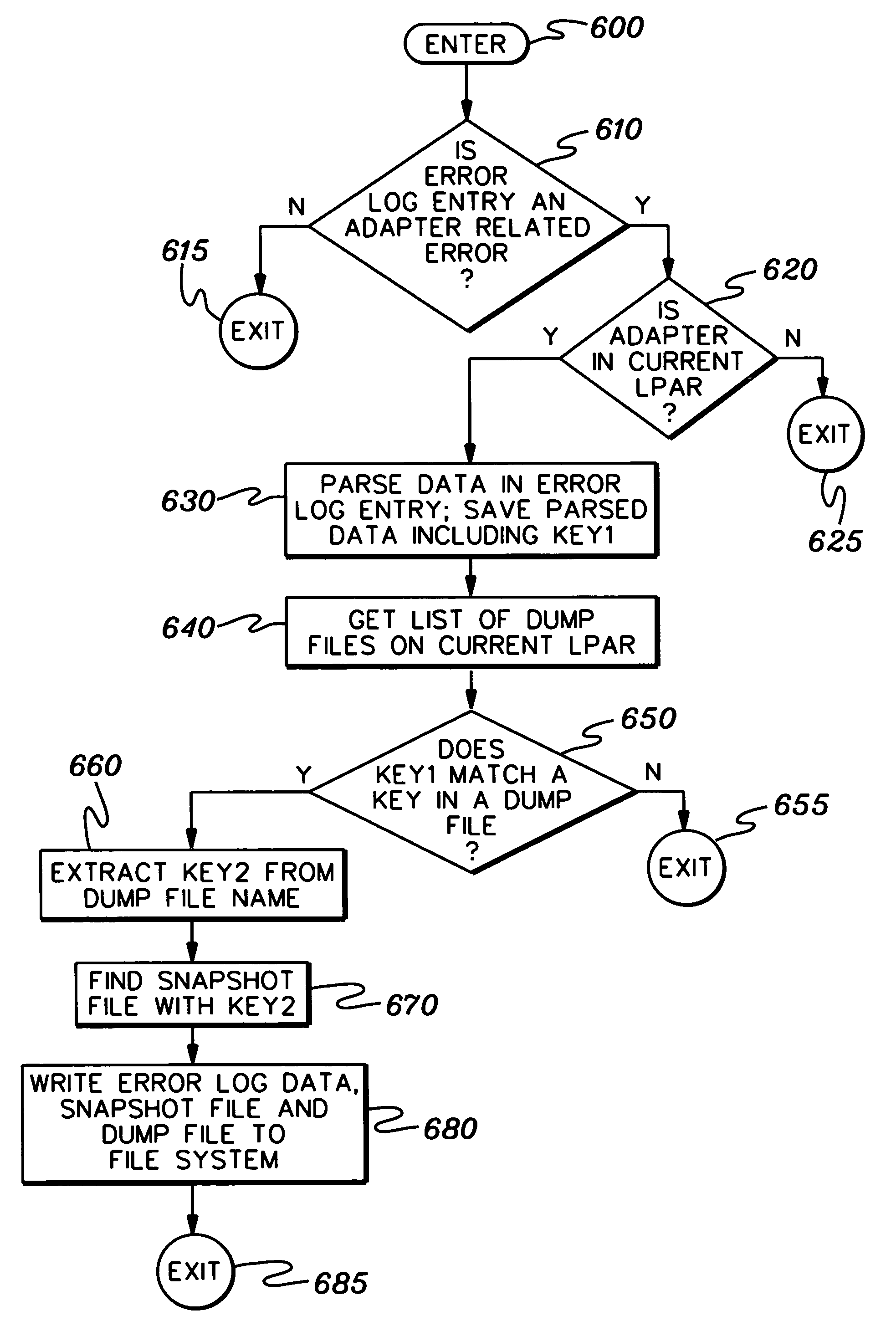
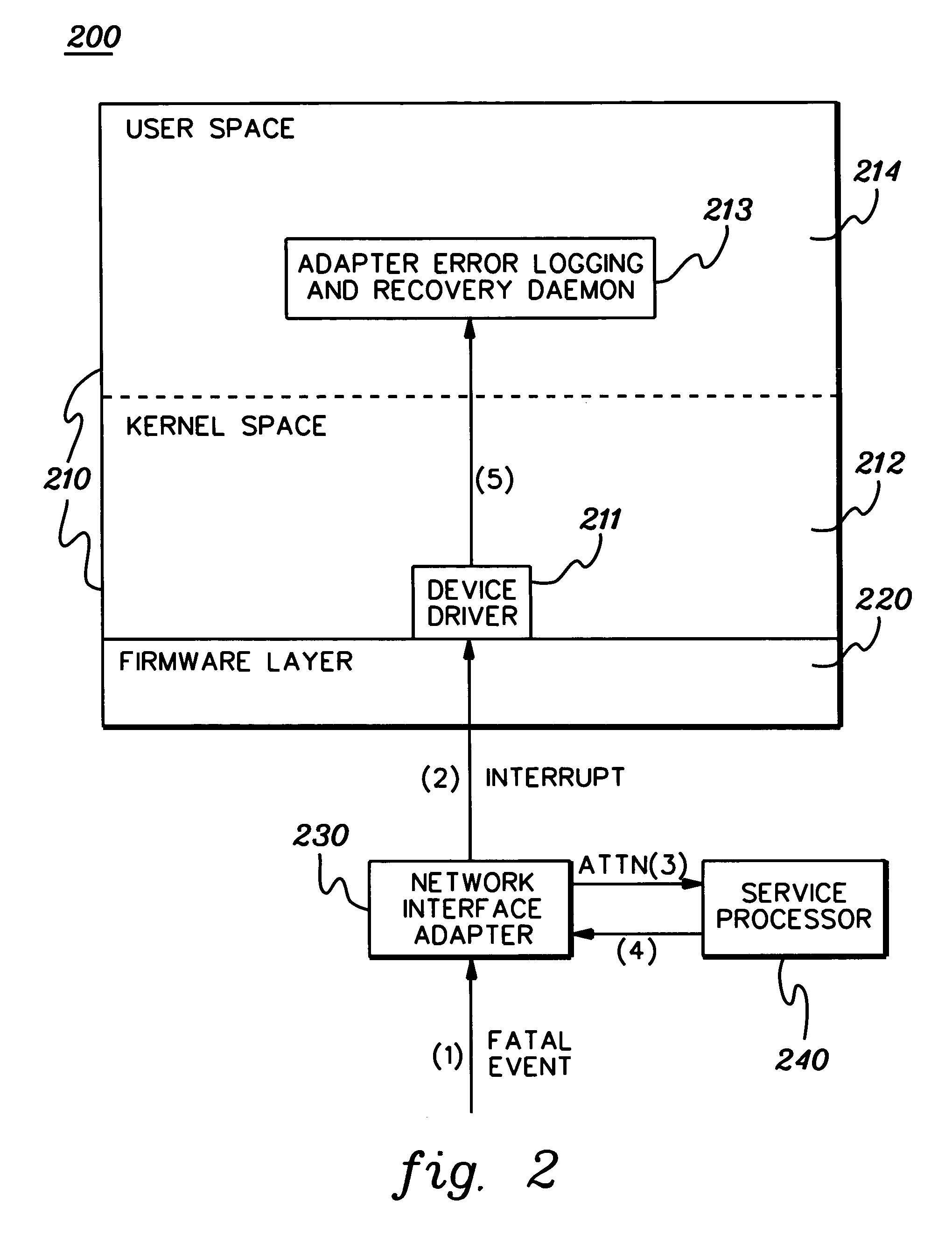
Method, system and program product for correlating data between operating environments
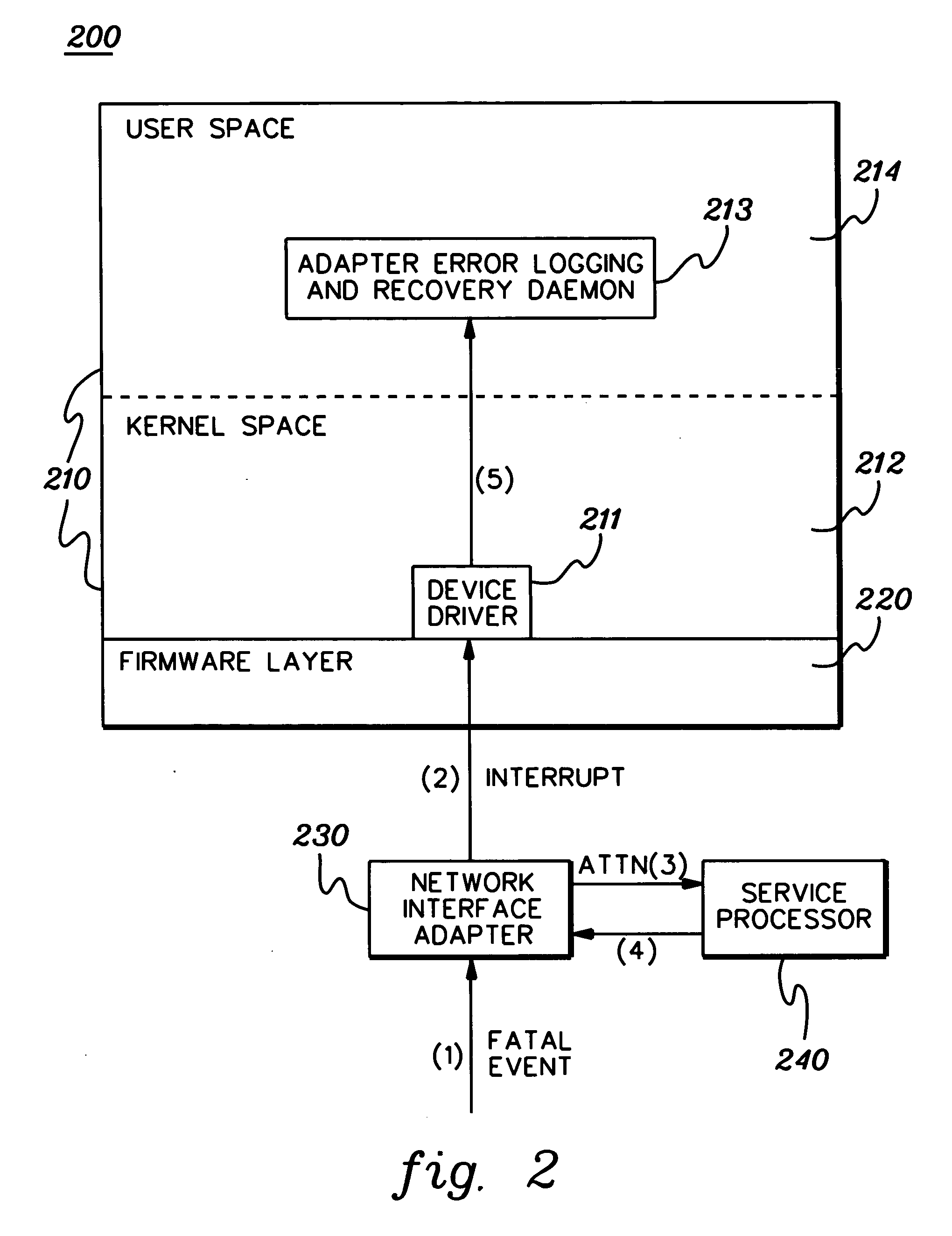
A data correlation technique is provided for a computing environment having multiple independent operating environments. The technique includes associating by a first operating environment a first key to a set of data to be obtained responsive to an identified event within the computing environment; obtaining by a second operating environment the set of data with the associated first key, and associating a second key therewith; and using the set of data with the associated first key and second key to match to the set of data at least one other set of data obtained by the first operating environment or the second operating environment responsive to the event. The at least one other set of data has only the first key or the second key associated therewith. In one implementation, the event is a fatal event at a network interface adapter.
Owner:IBM CORP
System and method for a process attribute based computer network filter
InactiveUS6868450B1Digital data processing detailsMultiprogramming arrangementsNetwork packetSystem call
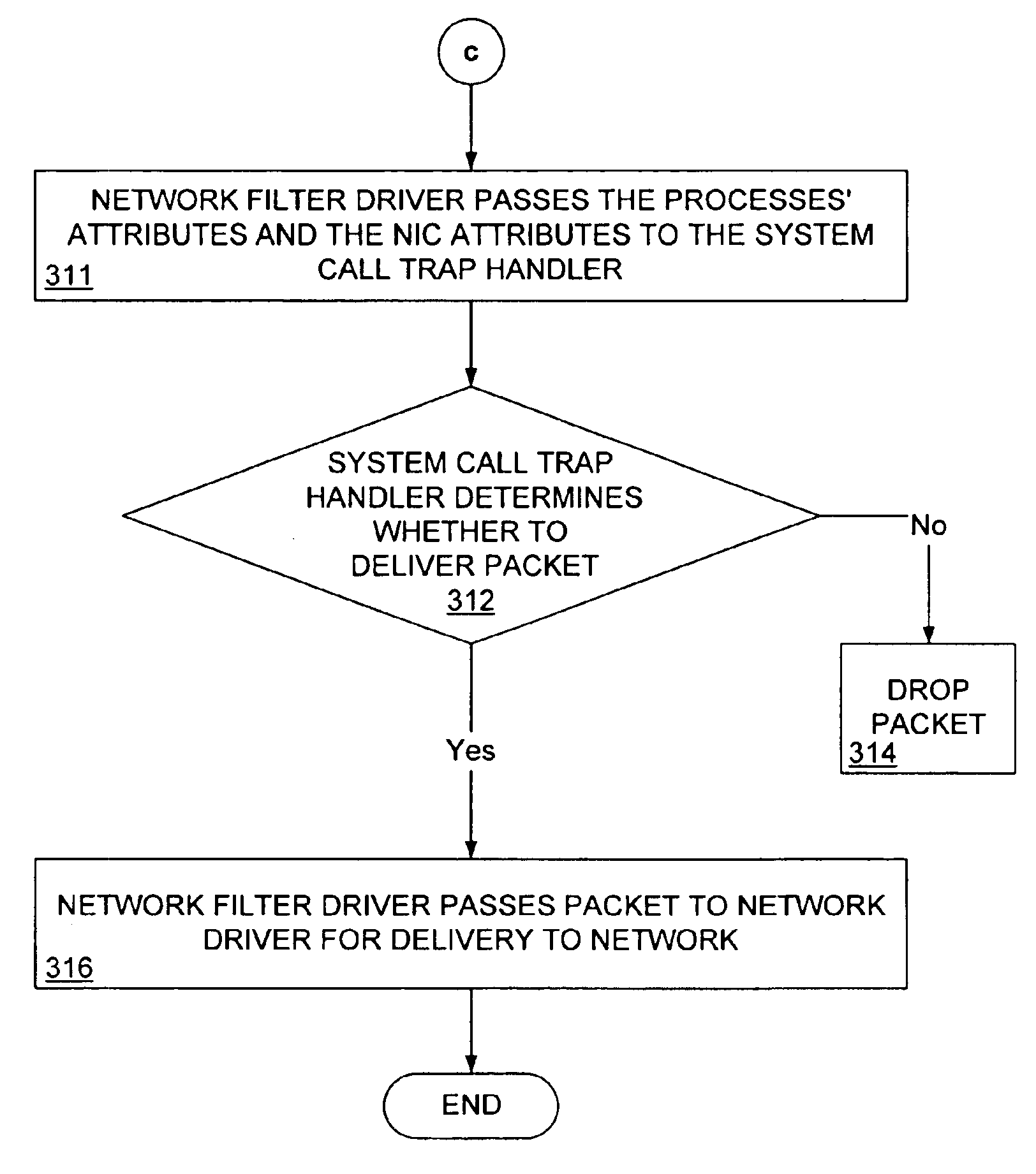
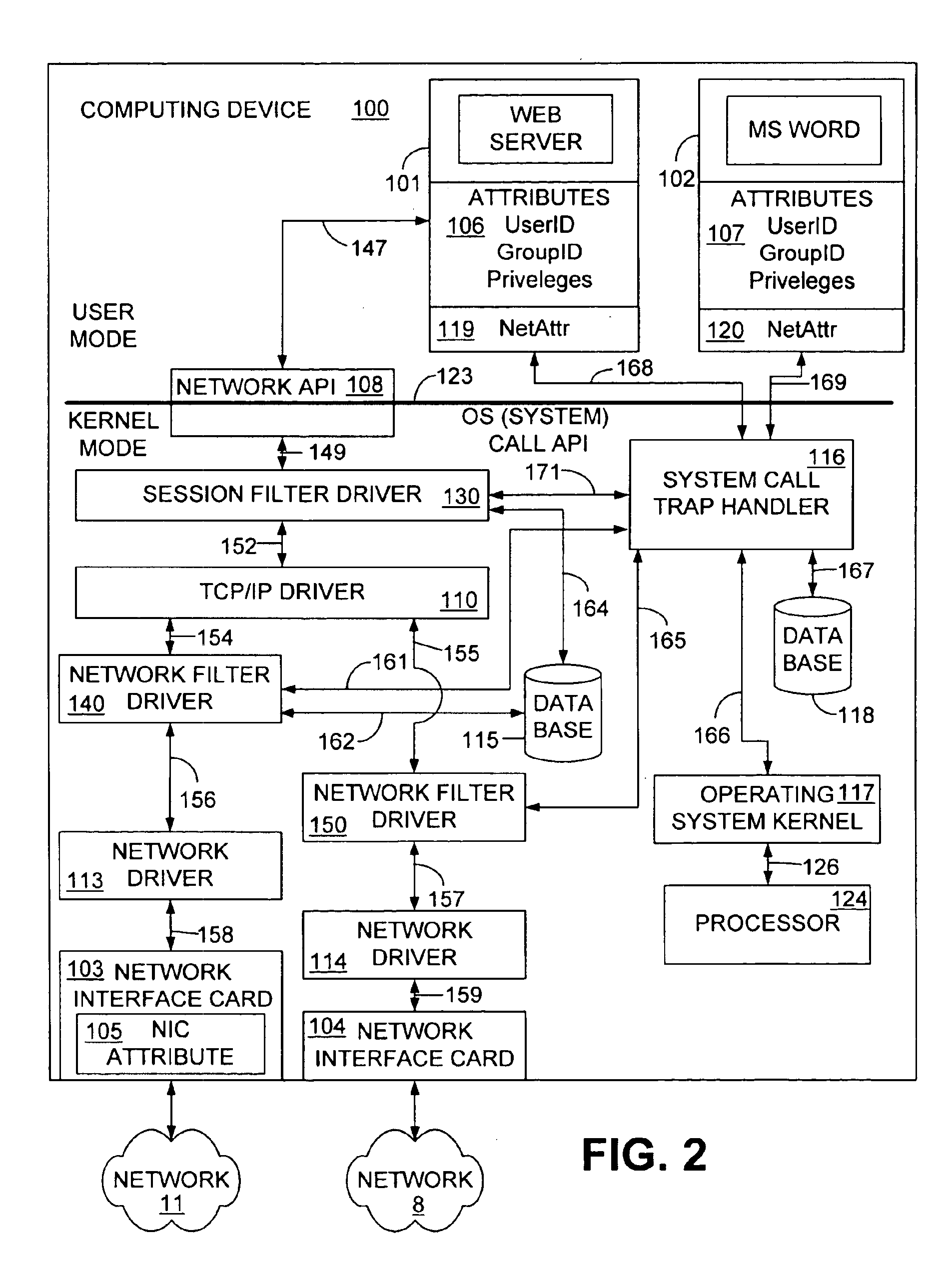
A system and method for a process attribute based computer network filter assigns a process attribute to a process executing on a computing device and assigns a network attribute to a network interface card (NIC) associated with the computing device. When the process desires to send a communication packet to another process on a different computing device over a network to which the NIC is connected, the process sends an application program interface (API) system call to the NIC. The API call is intercepted by a system call trap handler, which, in cooperation with a session filter driver and a network filter driver, determines the process attribute associated with the process and the network attribute associated with the NIC. If the session filter driver and the network filter driver, in cooperation with the system call trap handler, determine that the process attribute and the network attribute correspond, then the communication packet is allowed to pass to the network. Similarly, a packet received over the network is processed by the session filter driver and the network filter driver to determine whether the packet can pass to the process to which the received packet is destined.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
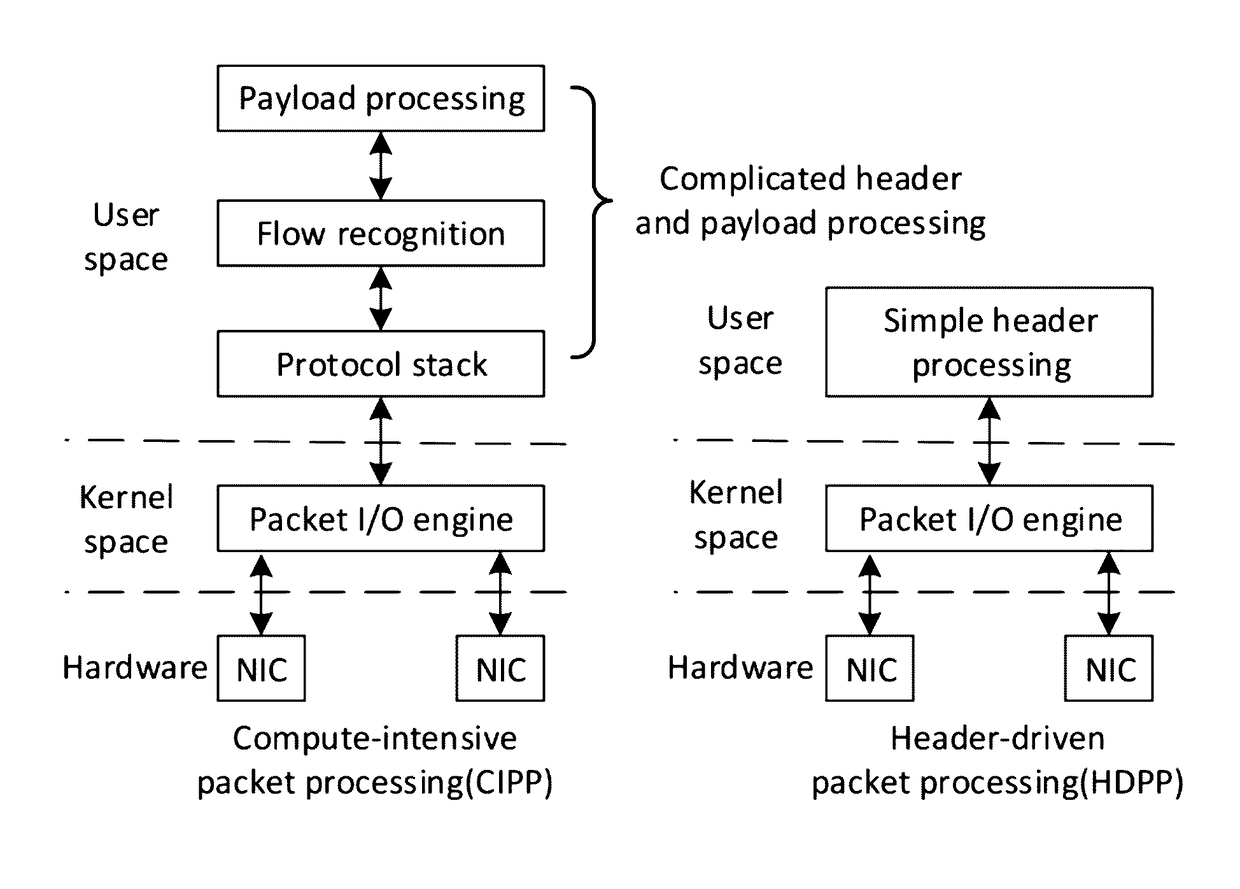
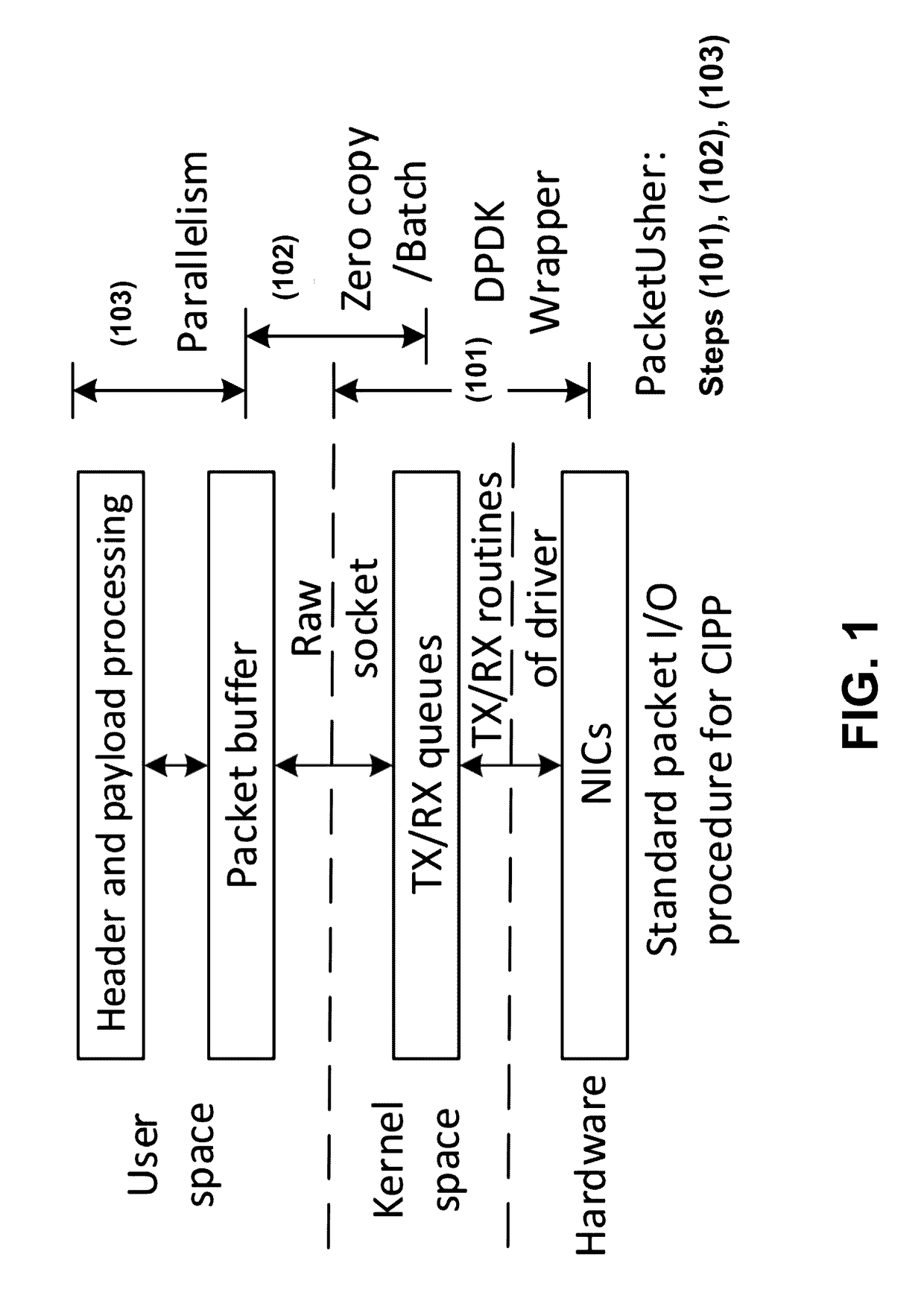
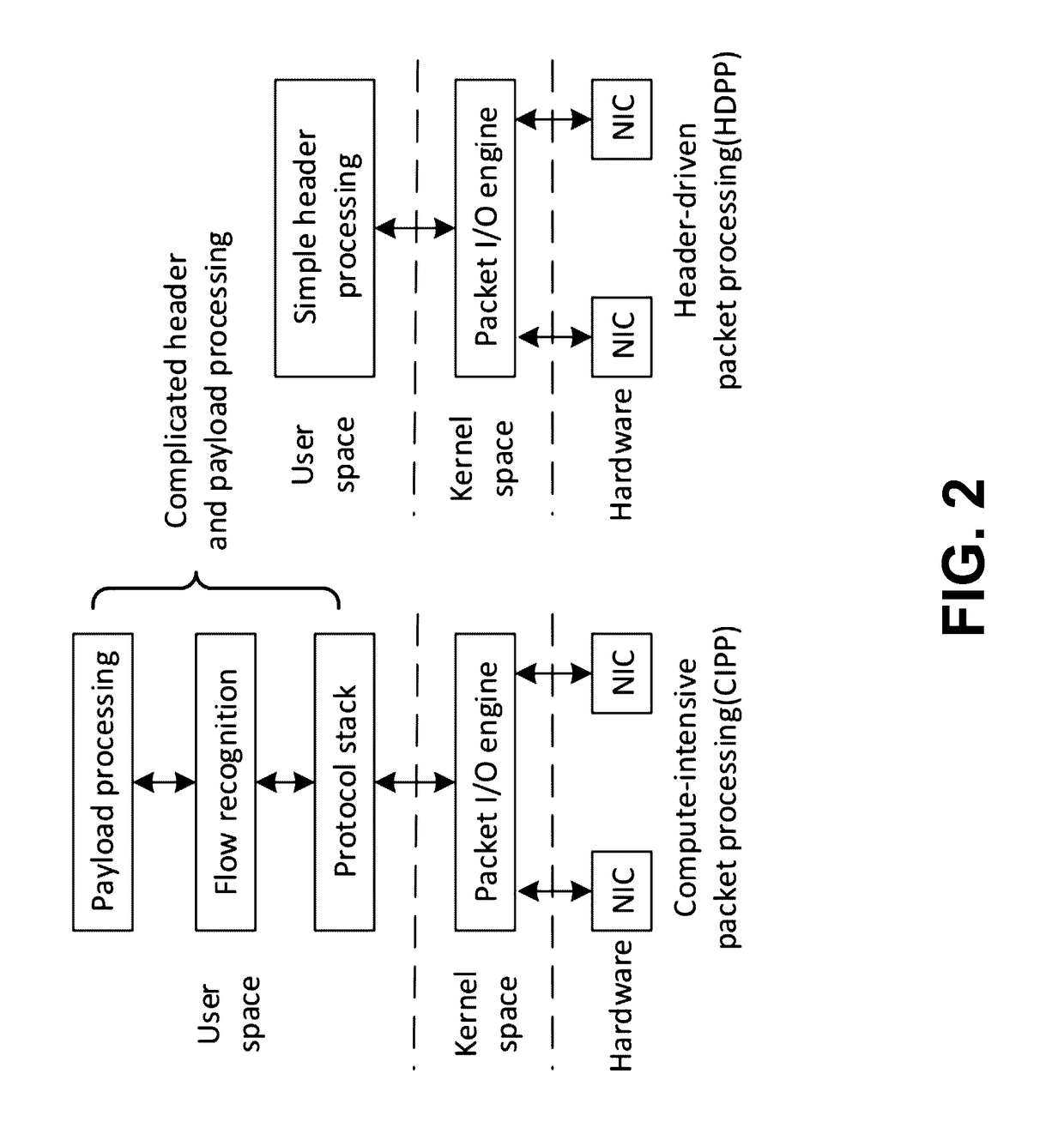
PacketUsher: Accelerating Computer-Intensive Packet Processing
Compute-intensive packet processing (CIPP) in a computer system comprising a programmable computing platform is accelerated by using a packet I / O engine, implemented on the platform, to perform packet I / O functions, where the packet I / O engine is configured to achieve direct access to a network interface card (NIC) from a user application. For a Linux-based computer system, standard I / O mechanisms of Linux are bypassed and only the packet I / O engine is used in performing the I / O functions. Furthermore, the computer system is configured to: process a batch of packets, instead of packet by packet, in every function call; and when moving a packet between a buffer of an individual user application and a queue of the packet I / O engine, copy a packet descriptor of the packet instead the entire packet. In addition, workflows across different working threads are balanced and parallelism is exploited to fully utilize resources of the platform.
Owner:MACAU UNIV OF SCI & TECH
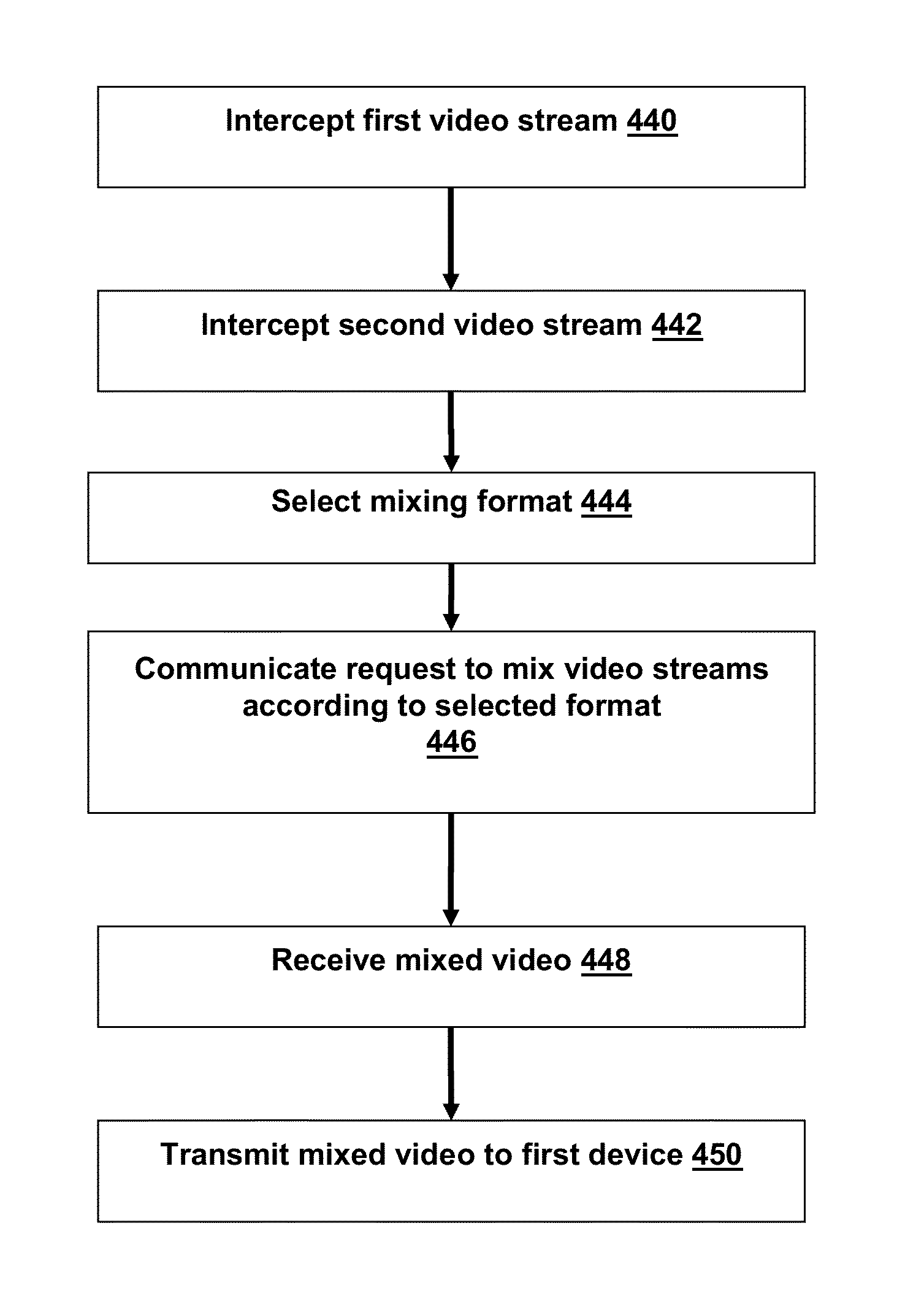
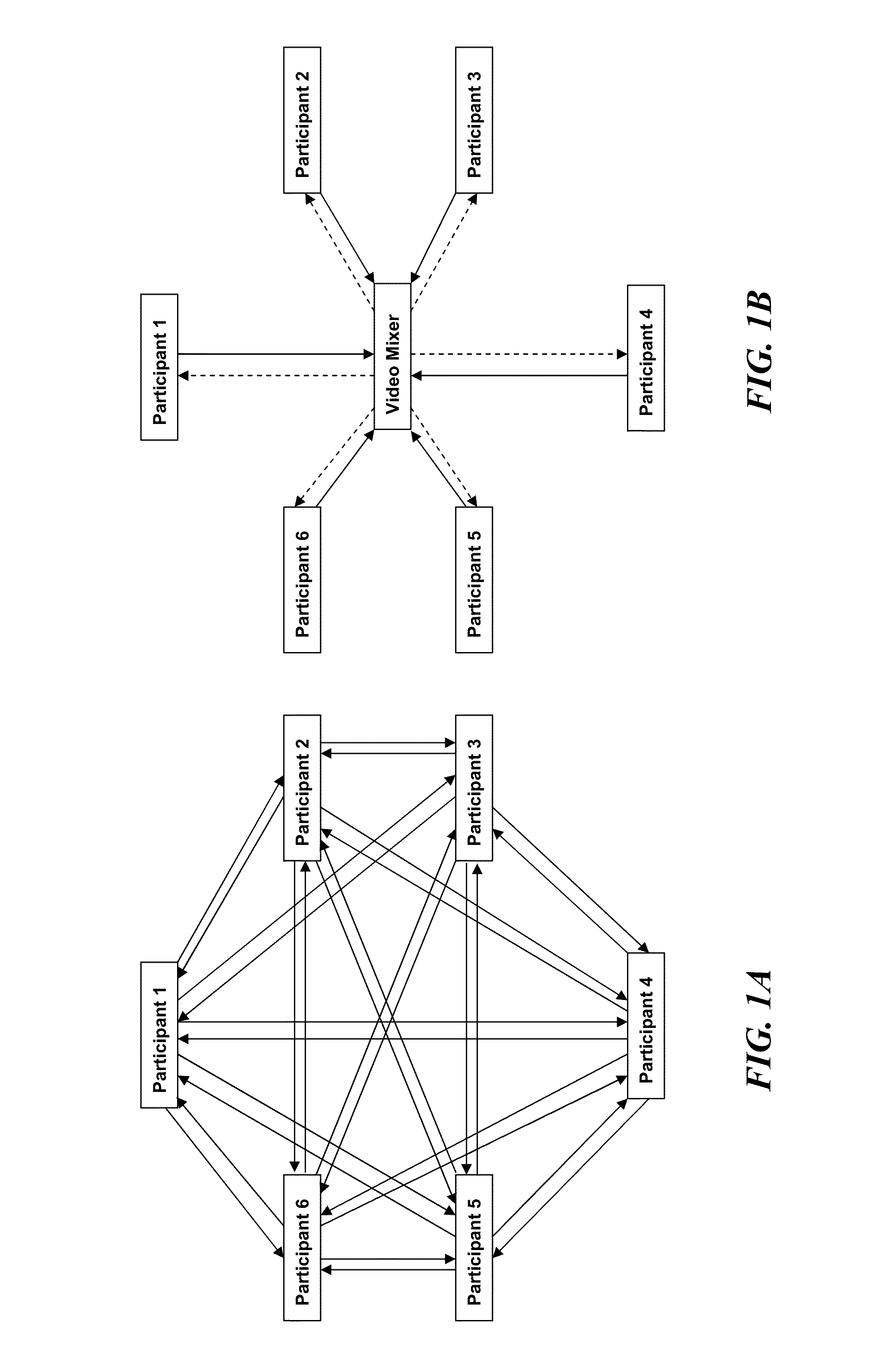
Systems and methods for providing video conferencing services via an ethernet adapter
InactiveUS8994778B2Reduce processing costsAttenuation bandwidthTelevision conference systemsAnalogue secracy/subscription systemsStandard formEthernet
The present application is directed towards systems and methods for providing video conference services via a single device installed as an Ethernet adapter on a computing device. A device, based around a standard form factor such as a PCI card, with a CPU, operating system, and memory may be installed in a server or other computing device and utilize power from the computing device while operating independently. The device may comprise an audio / video media processor for mixing a plurality of video streams to generate one or more mixed video streams, which may be provided to video conference participants. In some embodiments, the device may select a mixing format or arrangement for the mixed video streams based on the number of participants or identified roles of one or more participants.
Owner:POSITRON INTPROP LLC
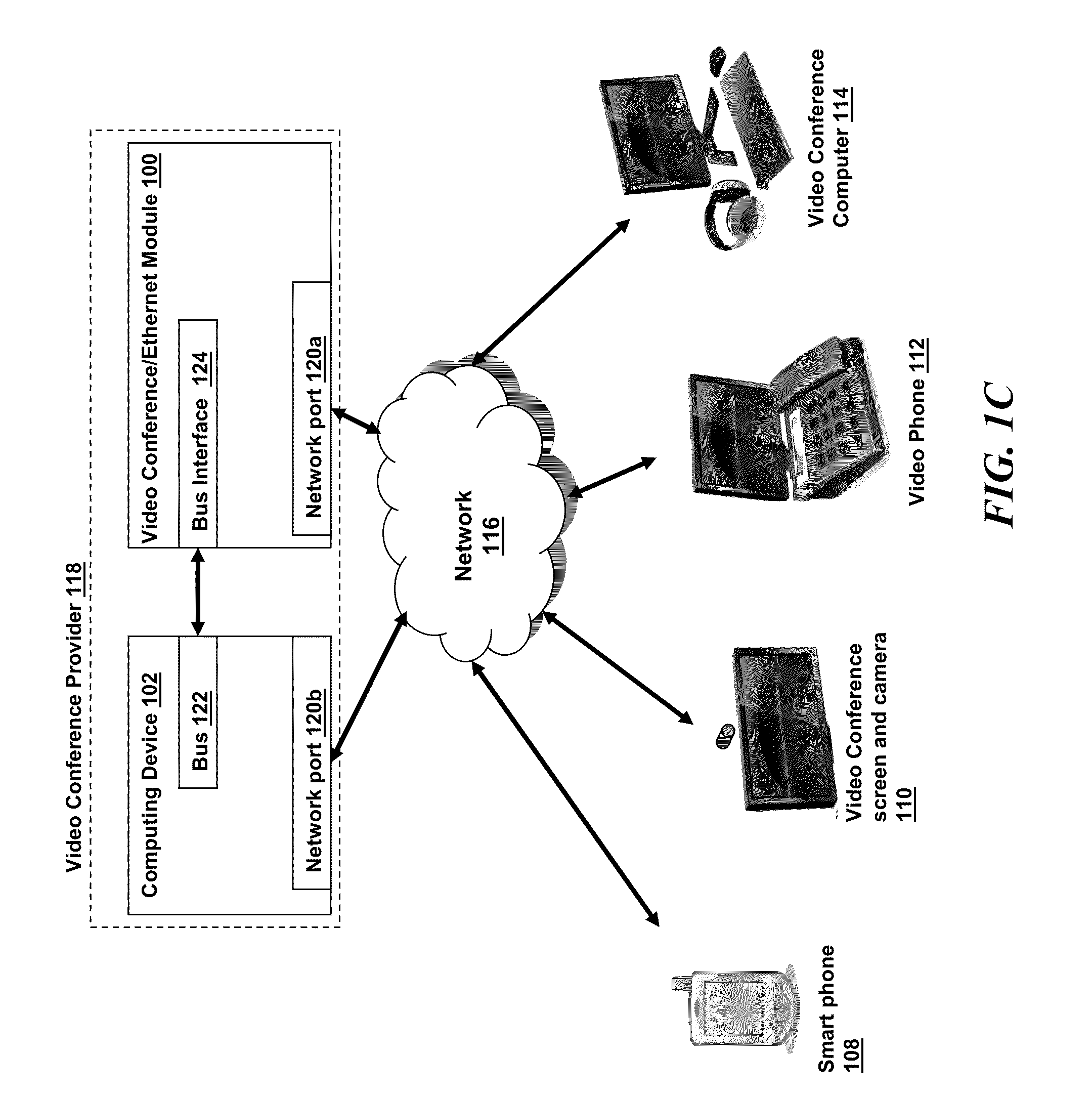
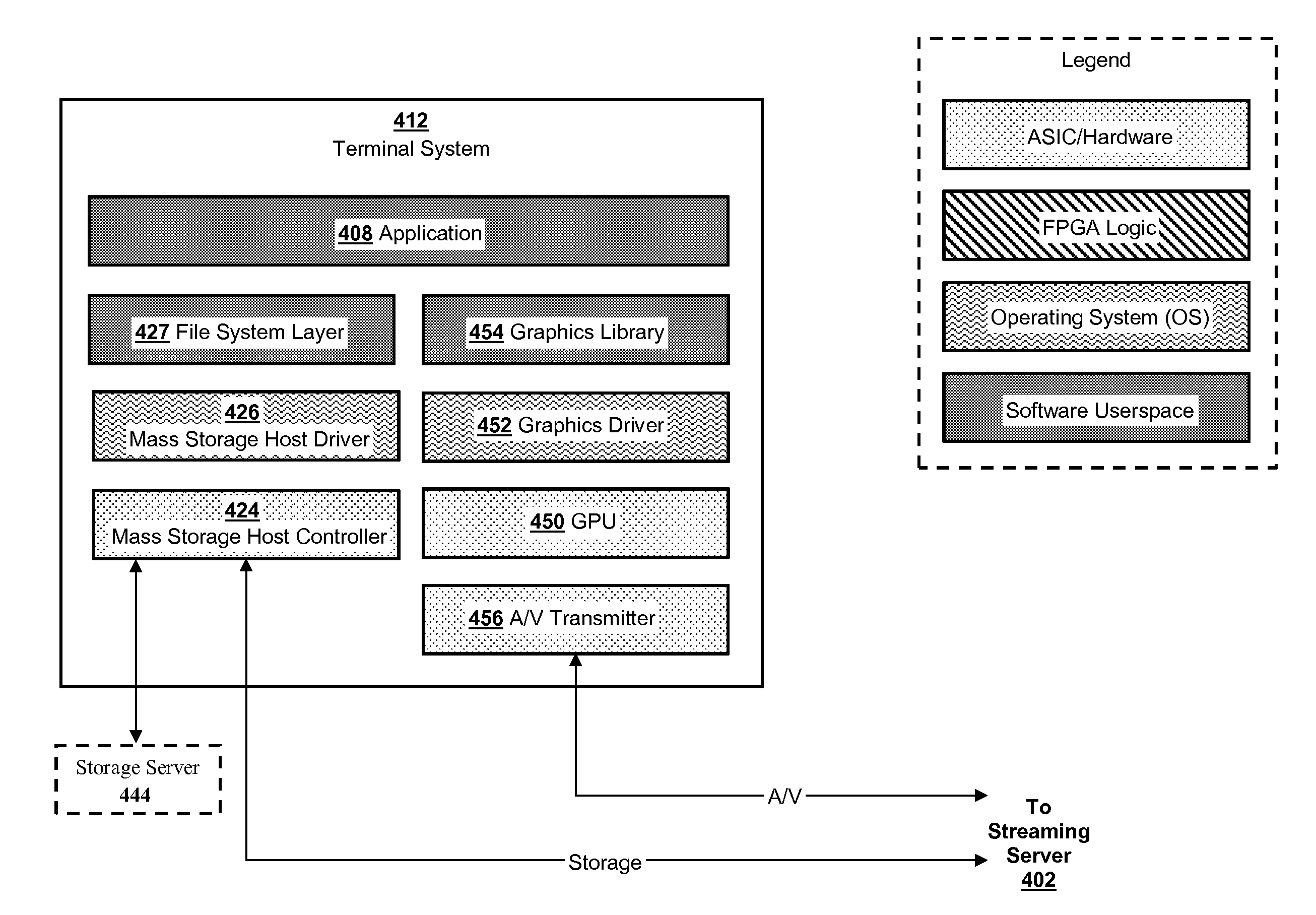
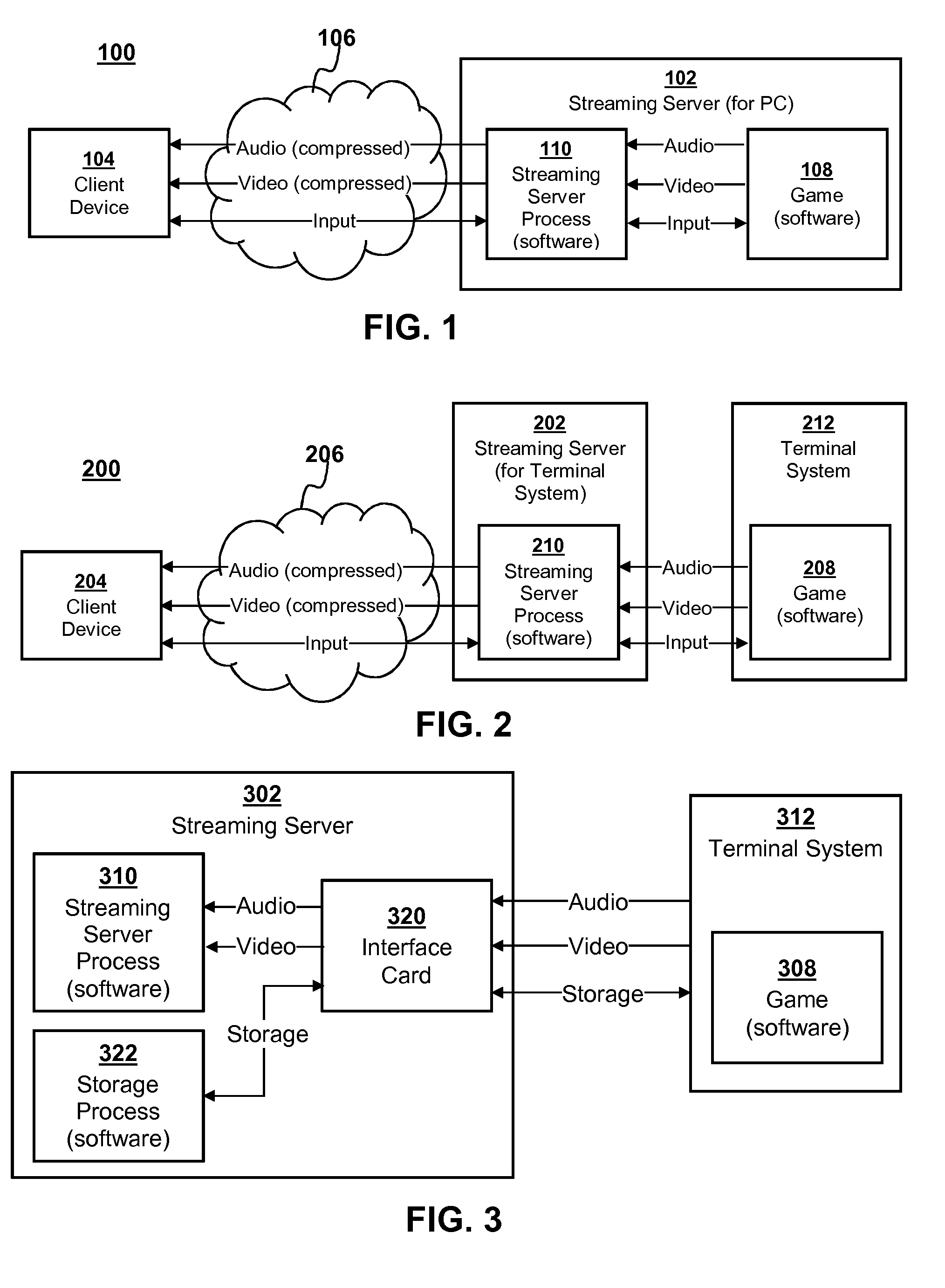
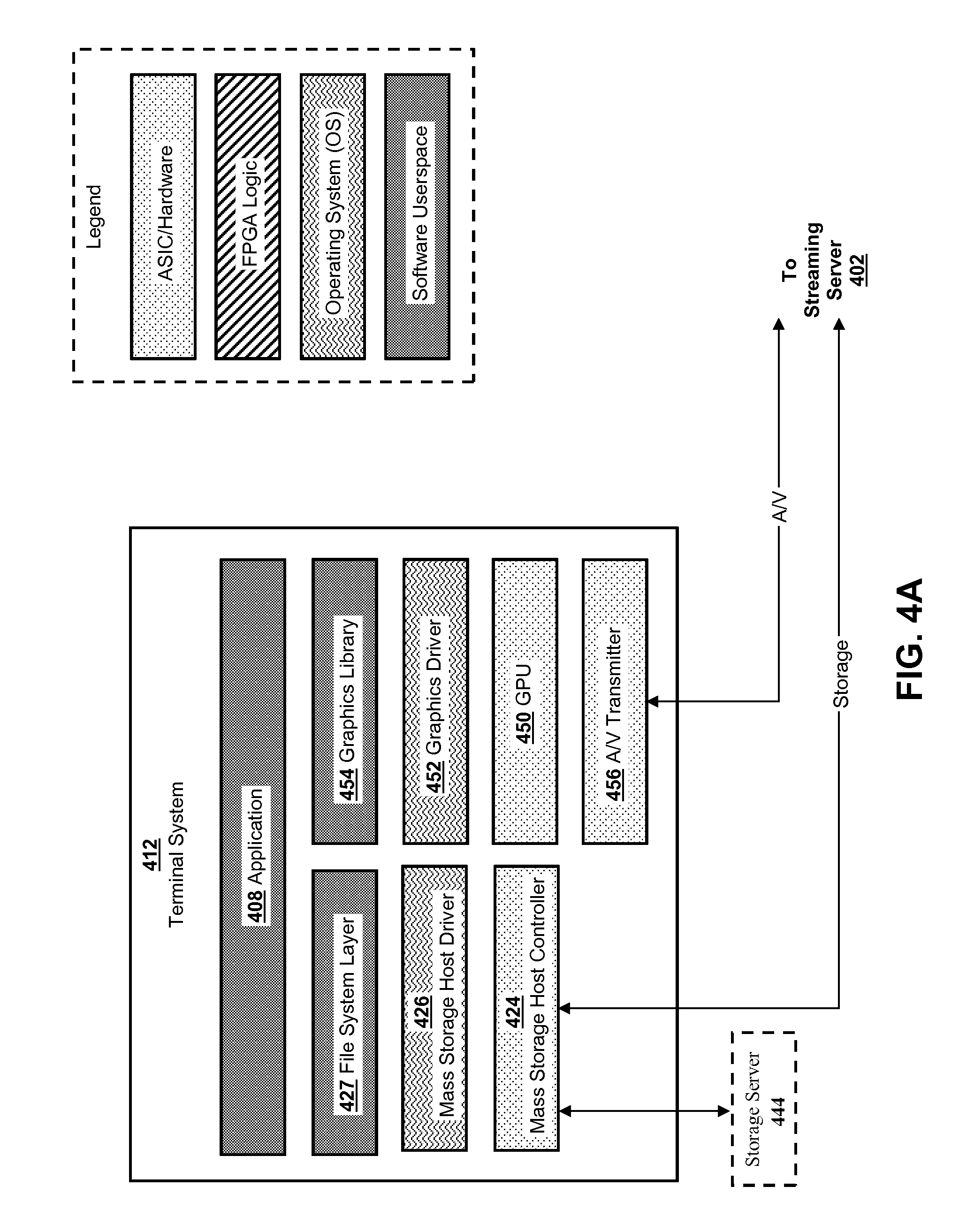
Mass storage virtualization for cloud computing
Aspects of the present disclosure relate to systems and methods for virtualizing mass storage using an interface card, or other special hardware unit, operatively coupled to a host system. In various implementations, the interface device and host system may collectively emulate a mass storage device for another “terminal” computing system in a manner that is transparent to the terminal system. Moreover, in various implementations, a mass storage device may be emulated in a manner that is transparent to the terminal system, without requiring modifications to the terminal platform's hardware or software architecture.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
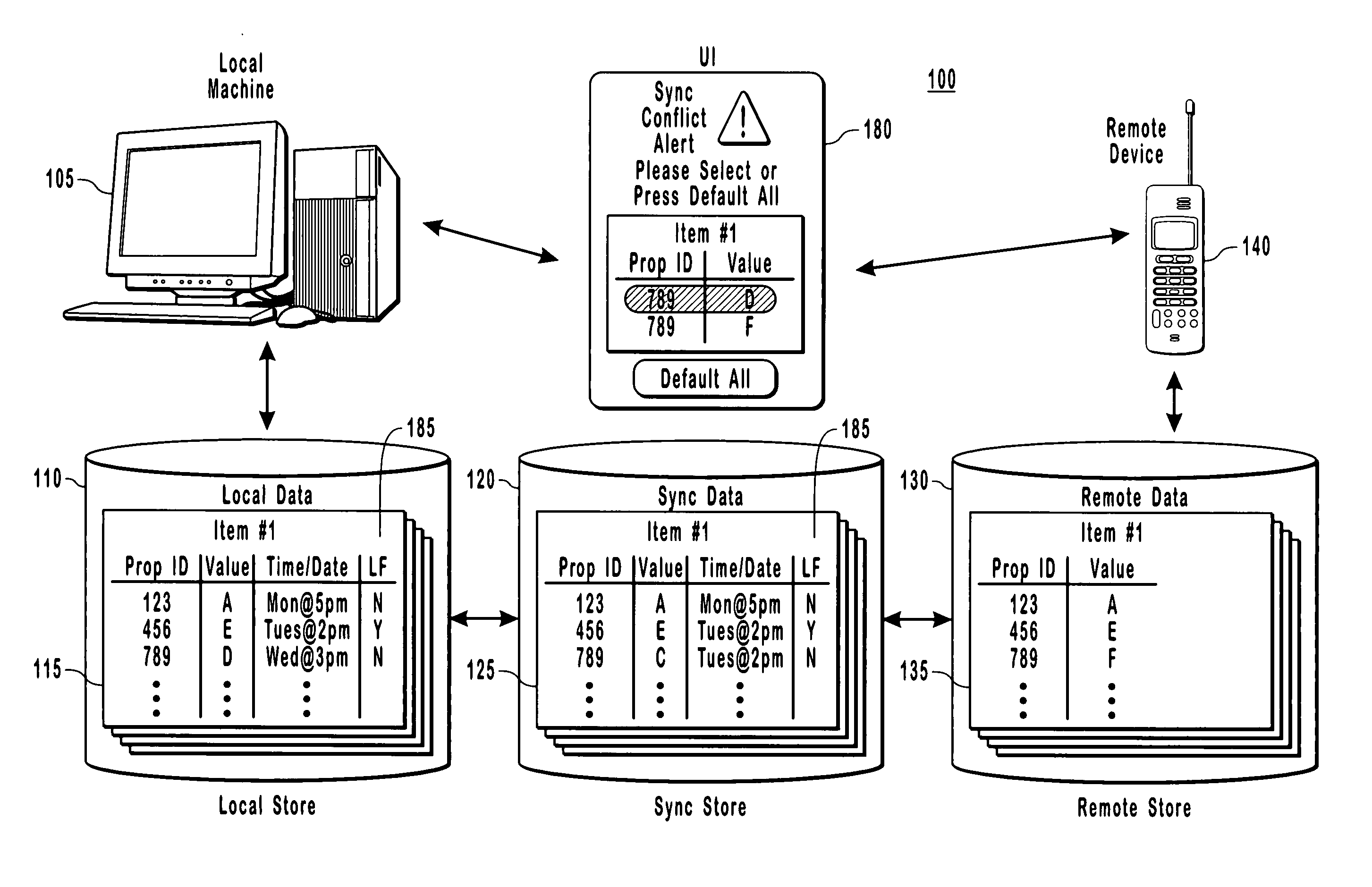
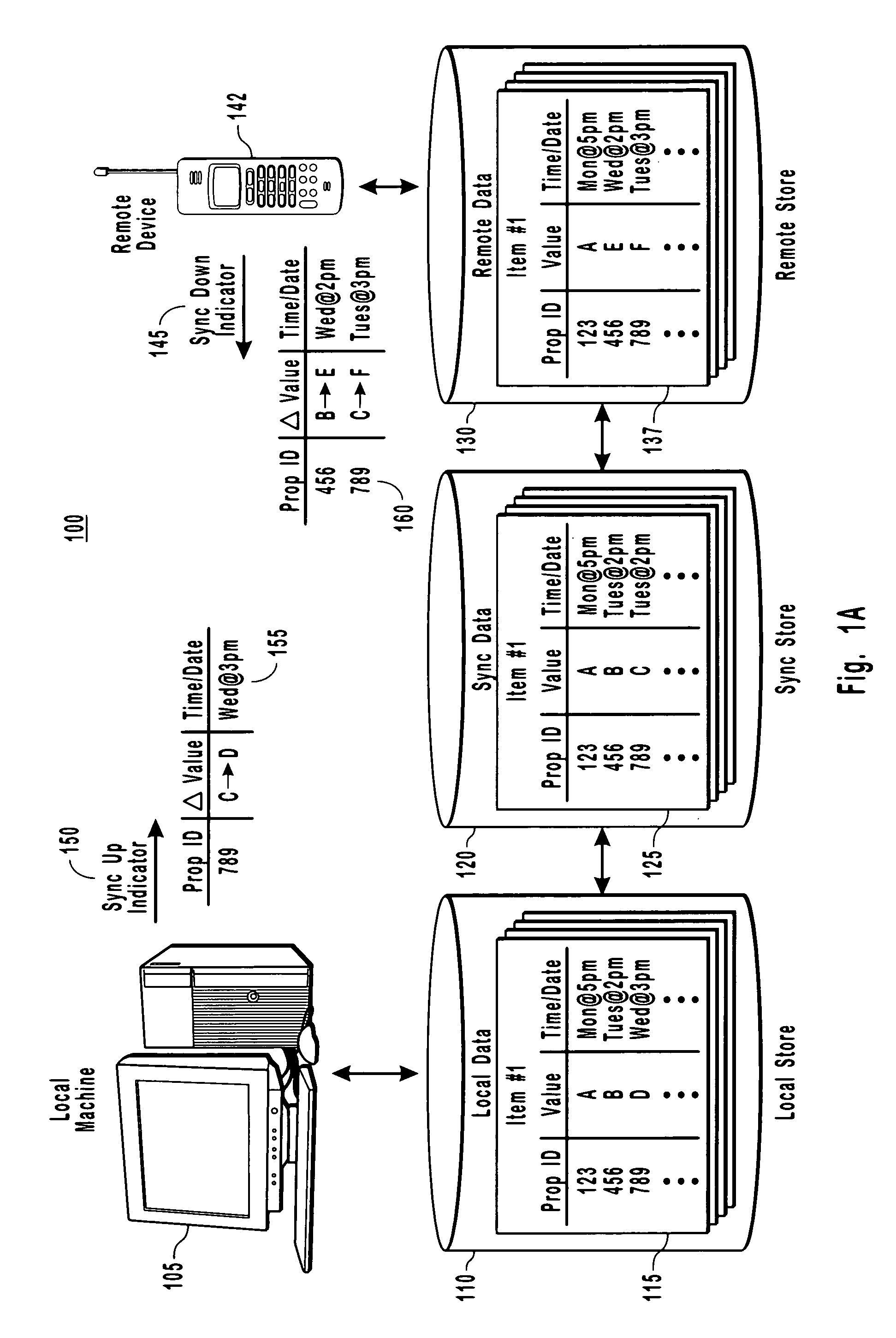
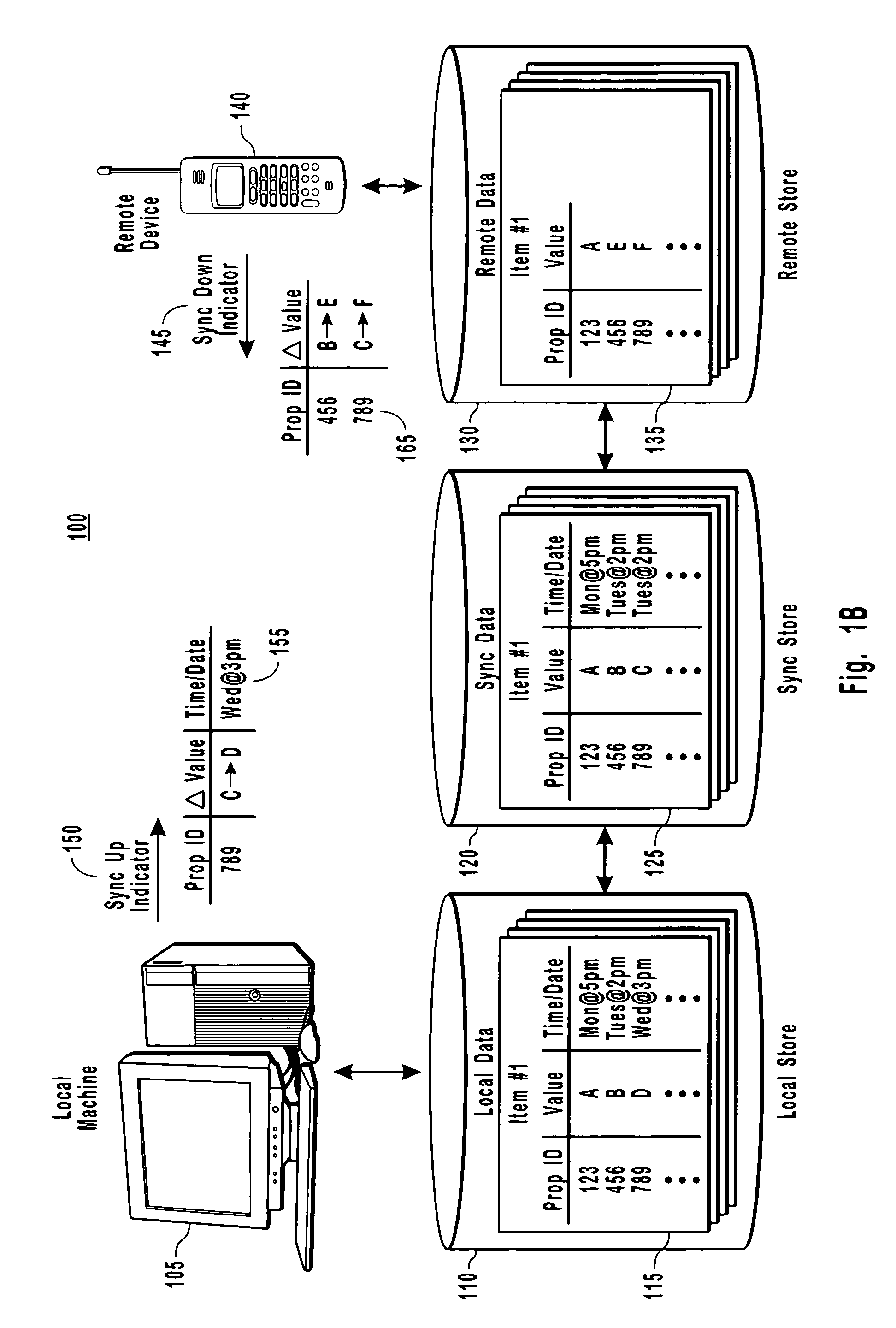
Detecting low fidelity sync data
InactiveUS20060028396A1Cathode-ray tube indicatorsMultiple digital computer combinationsData synchronizationTime information
The present invention provides for a distributed computing system that is capable of determining when data needs to be synced between two computer devices because data has changed on at least a remote device. More particularly, the present invention provides for a sync adapter that uses sync data to detect that a property on a device is new and needs to synchronize with corresponding data on another machine. The sync data is specific to the two devices in that the sync data mirrors data that was last synchronized between these two computing devices. Other example embodiments use the sync data to detect and mark data as low fidelity data for identifying any date and time information associated with the low fidelity data as potentially unreliable.
Owner:MICROSOFT TECH LICENSING LLC
Workload management in heterogeneous environments
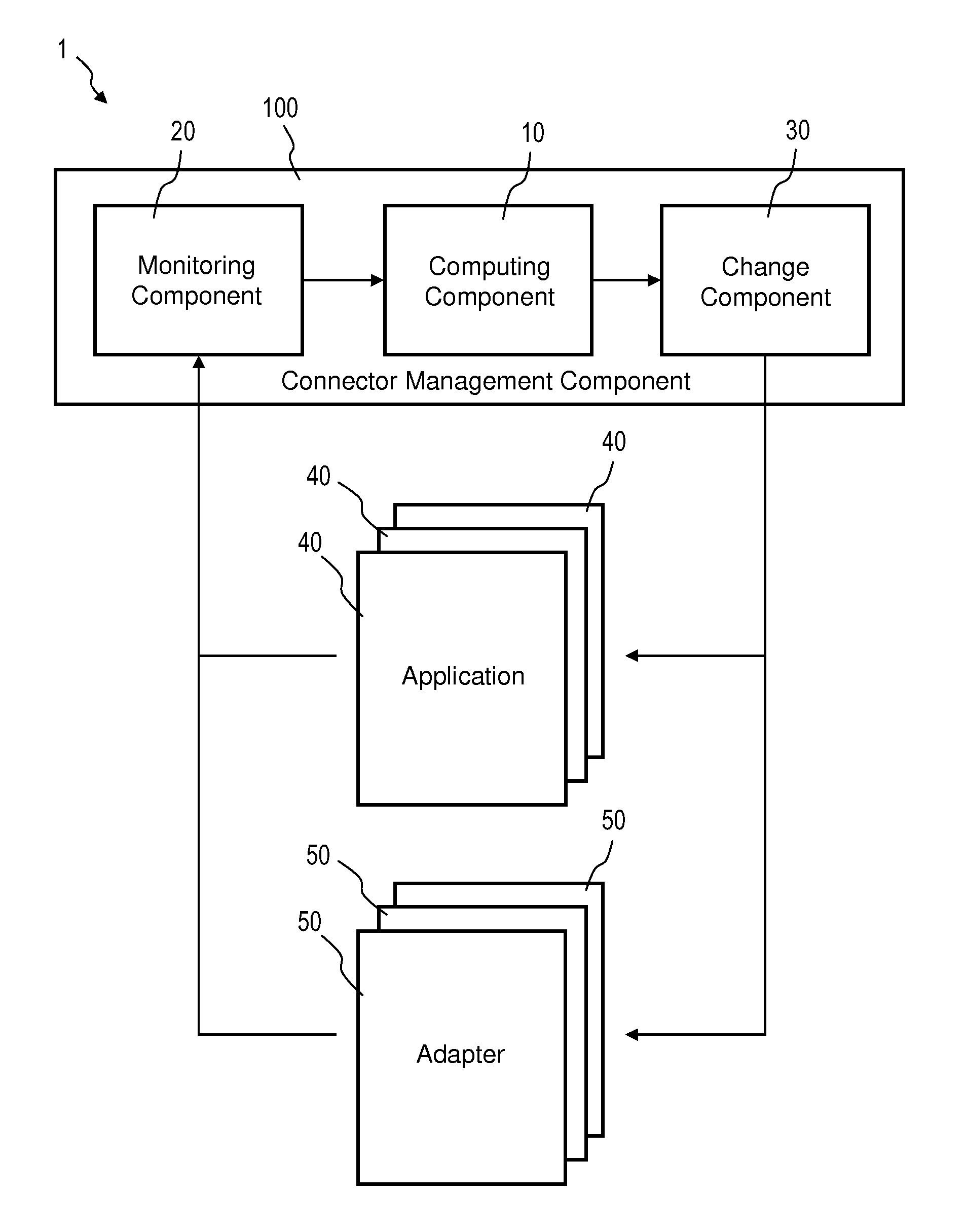
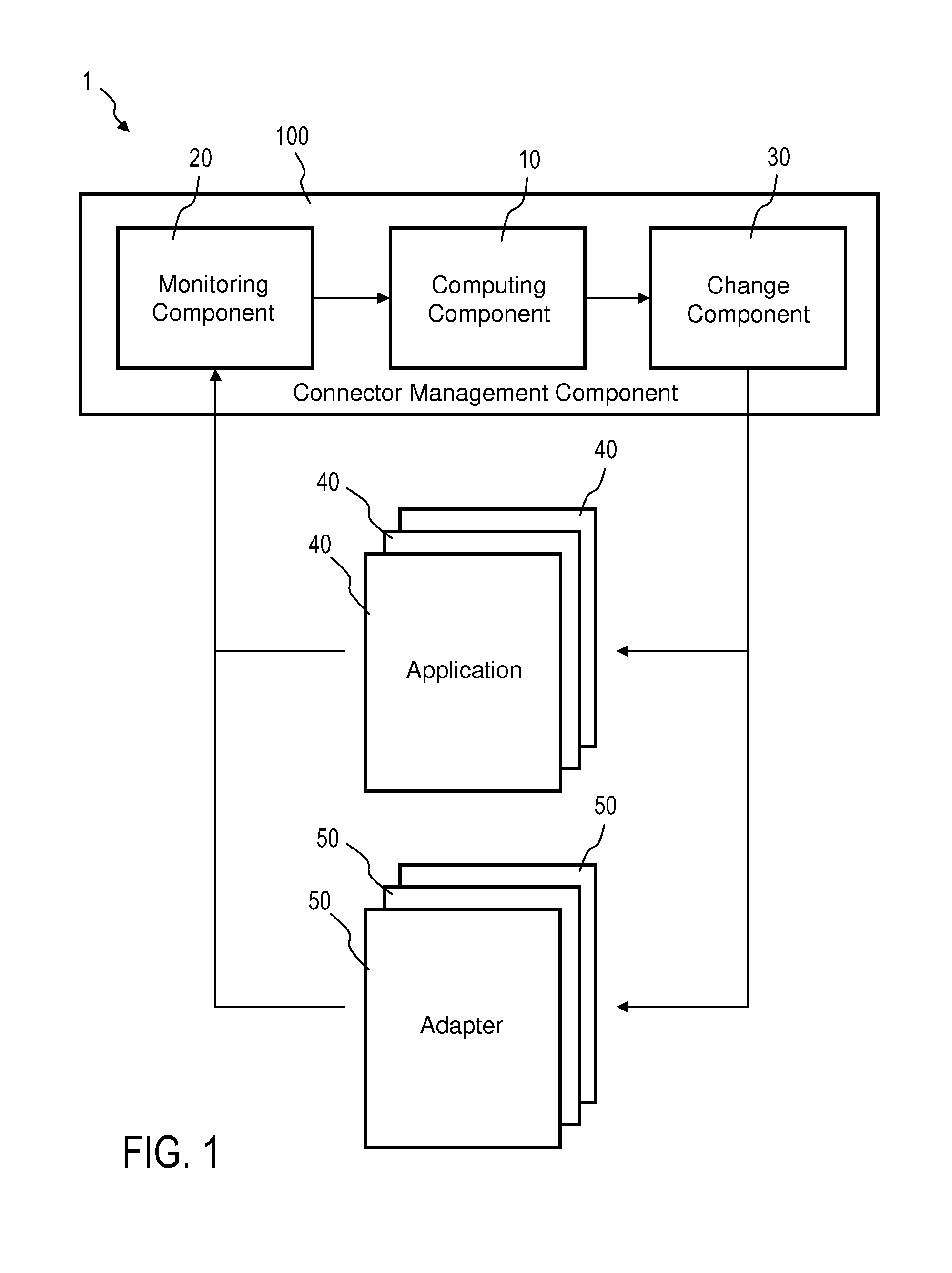
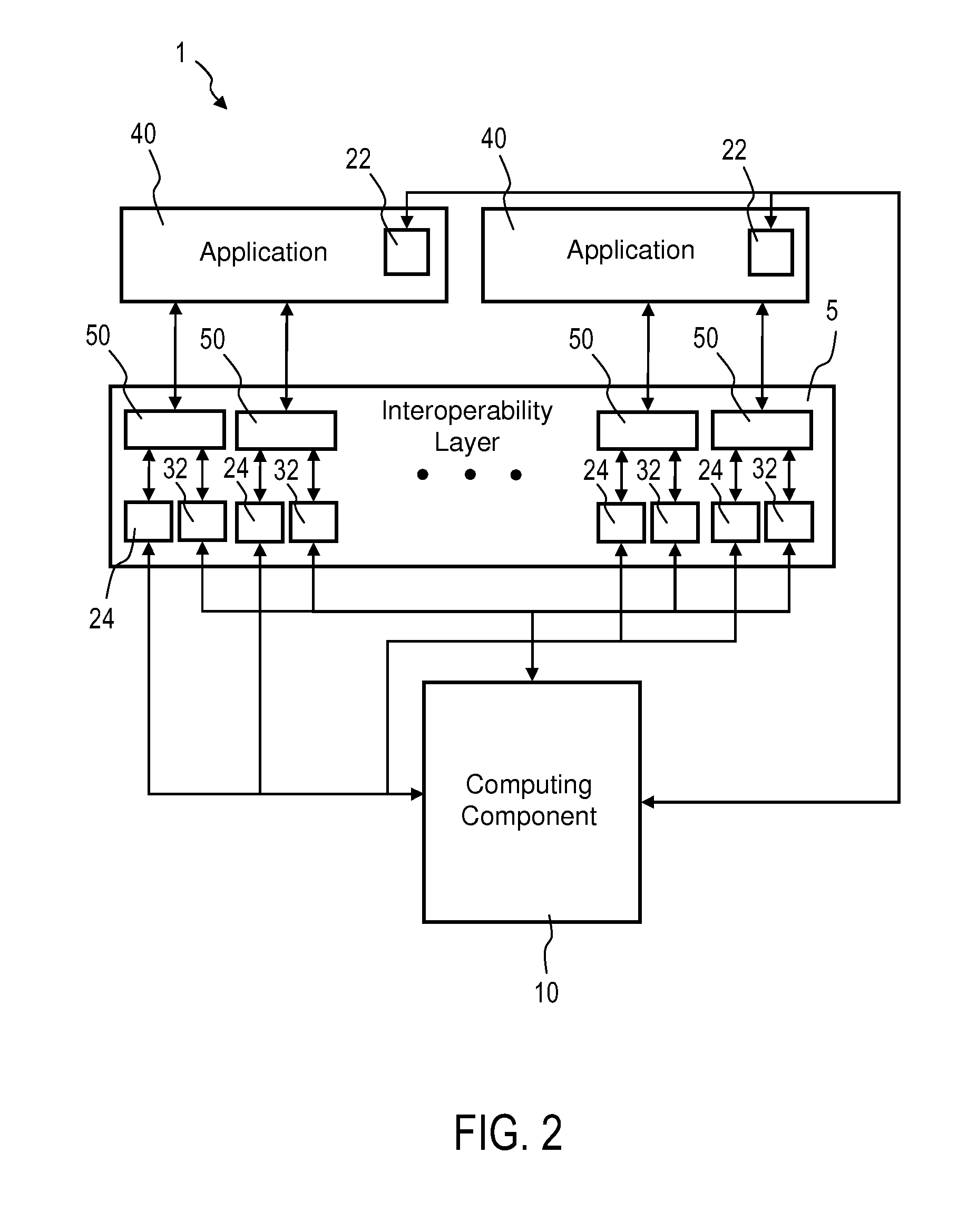
A system for managing a workload in a heterogeneous environment comprising at least one application, an interoperability layer for inter-application communication, and at least one adapter for connecting the at least one application to the interoperability layer, is disclosed. Such a system includes a self-adapting application connector management component which includes the following: a monitoring component for monitoring the performance and workload characteristics of one or more applications and / or one or more adapters; a computing component for computing a configuration change based on the monitored performance and workload characteristics; a change component for changing the configuration of the one or more adapters in accordance with the computed configuration change; and a change component for changing the configuration of the one or more applications in accordance with the computed configuration change.
Owner:IBM CORP
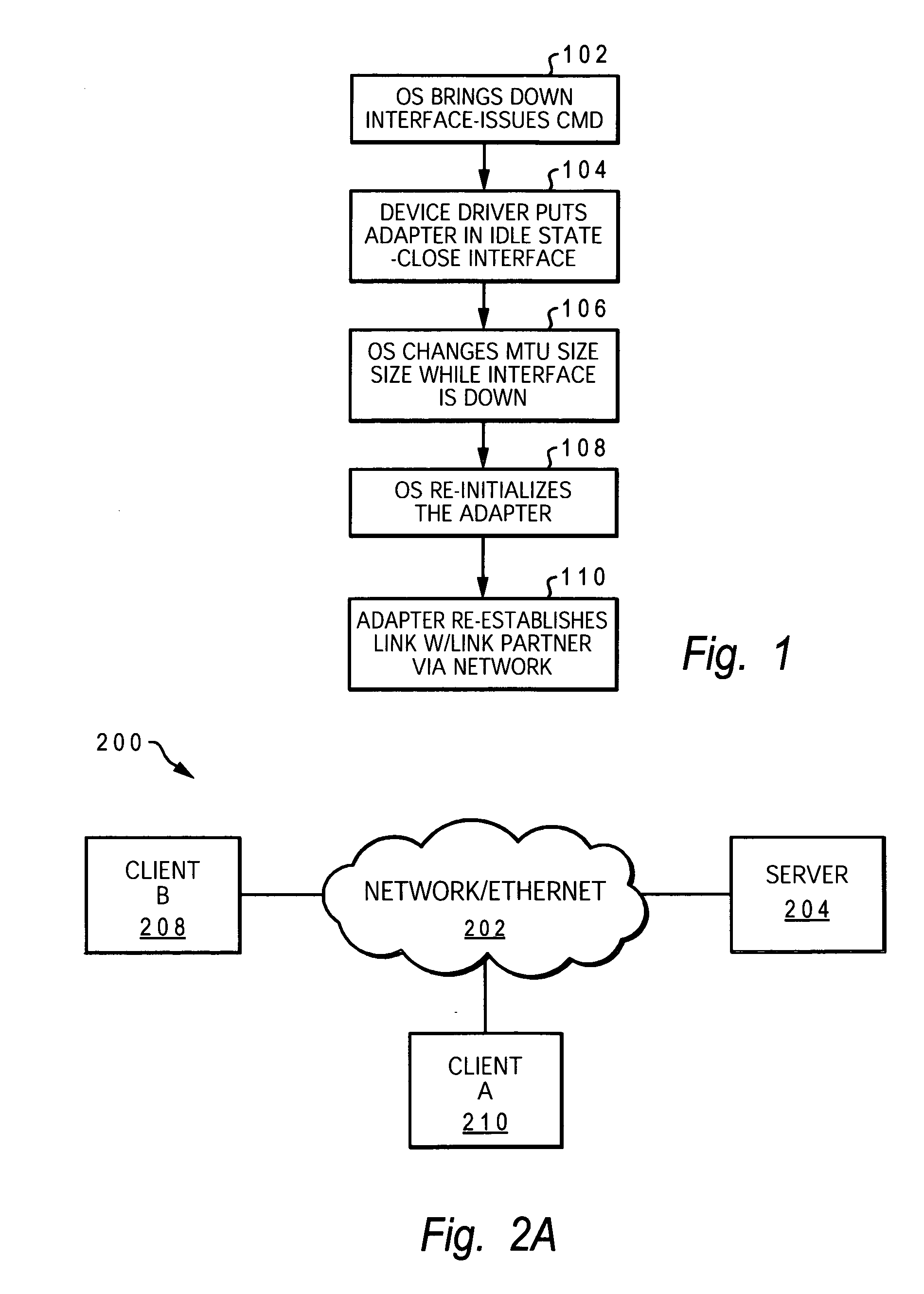
Method for changing ethernet MTU size on demand with no data loss
InactiveUS20070230344A1Avoid data lossError preventionFrequency-division multiplex detailsData packData loss
A method and system for substantially avoiding loss of data and enabling continuing connection to the application during an MTU size changing operation in an active network computing device. Logic is added to the device driver, which logic provides several enhancements to the MTU size changing operation / process. Among these enhancements are: (1) logic for temporarily pausing the data coming in from the linked partner while changing the MTU size; (2) logic for returning a “device busy” status to higher-protocol transmit requests during the MTU size changing process. This second logic prevents the application from issuing new requests until the busy signal is removed; and (3) logic for enabling resumption of both flows when the MTU size change is completed. With this new logic, the device driver / adapter does not have any transmit and receive packets to process for a short period of time, while the MTU size change is ongoing.
Owner:IBM CORP
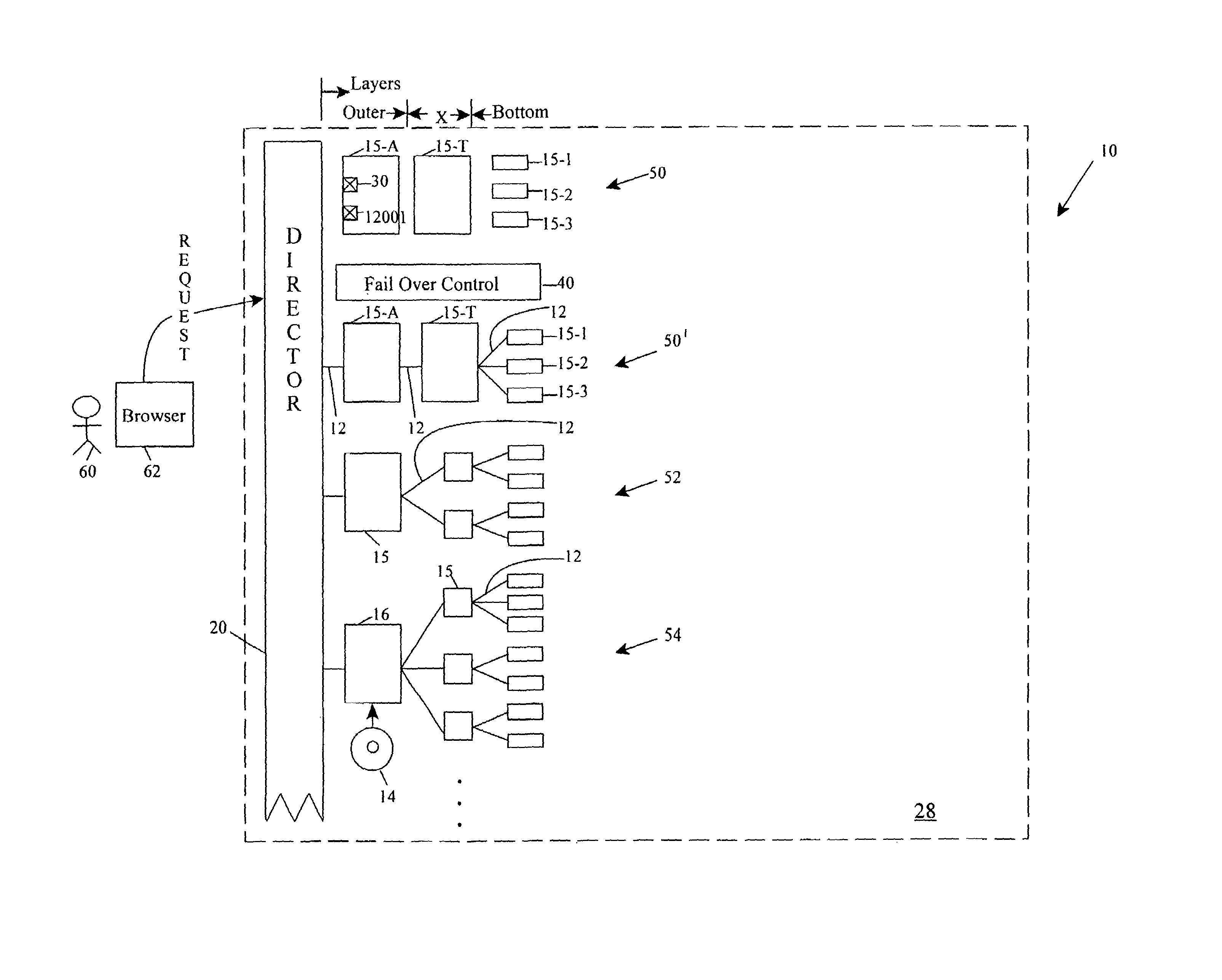
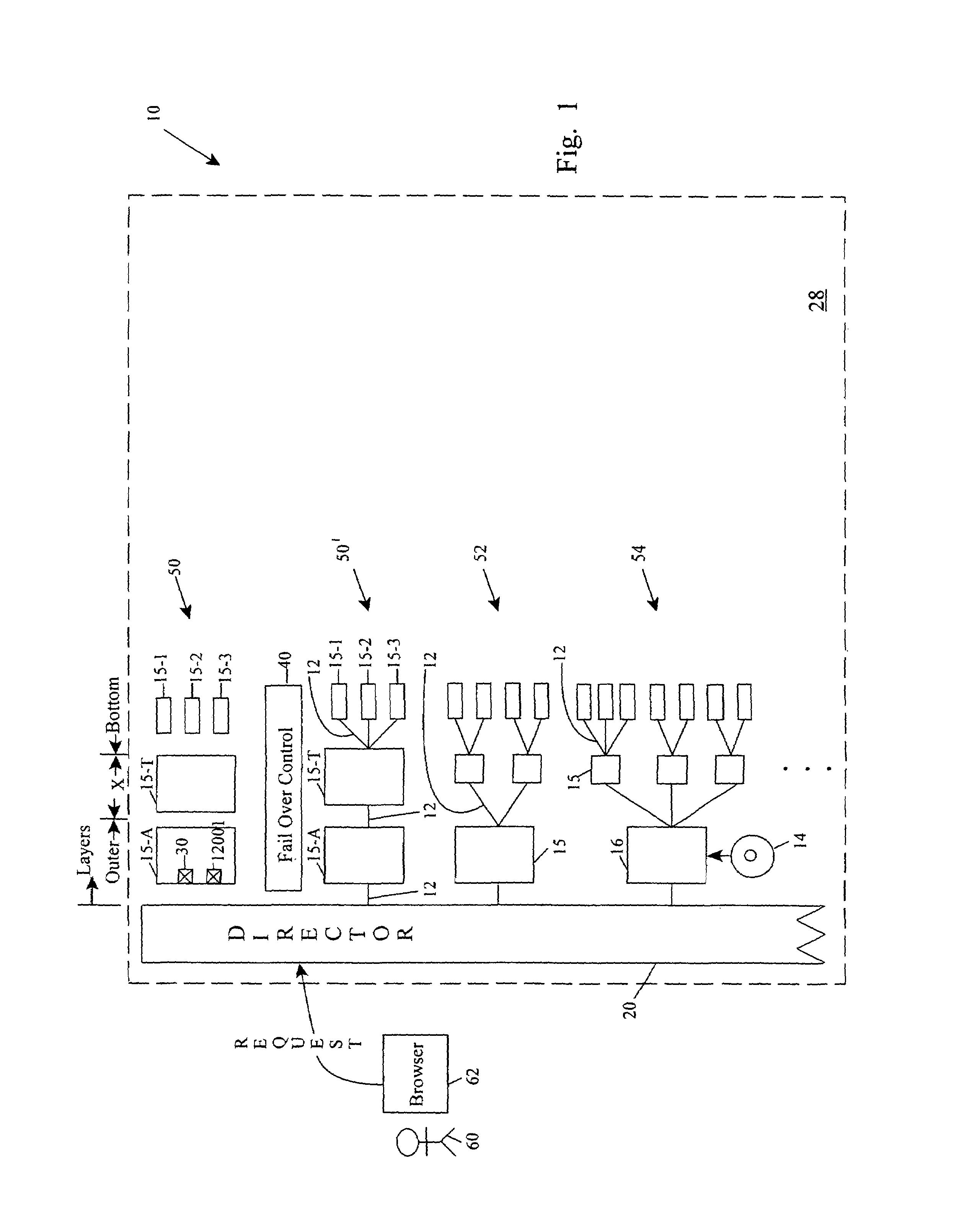
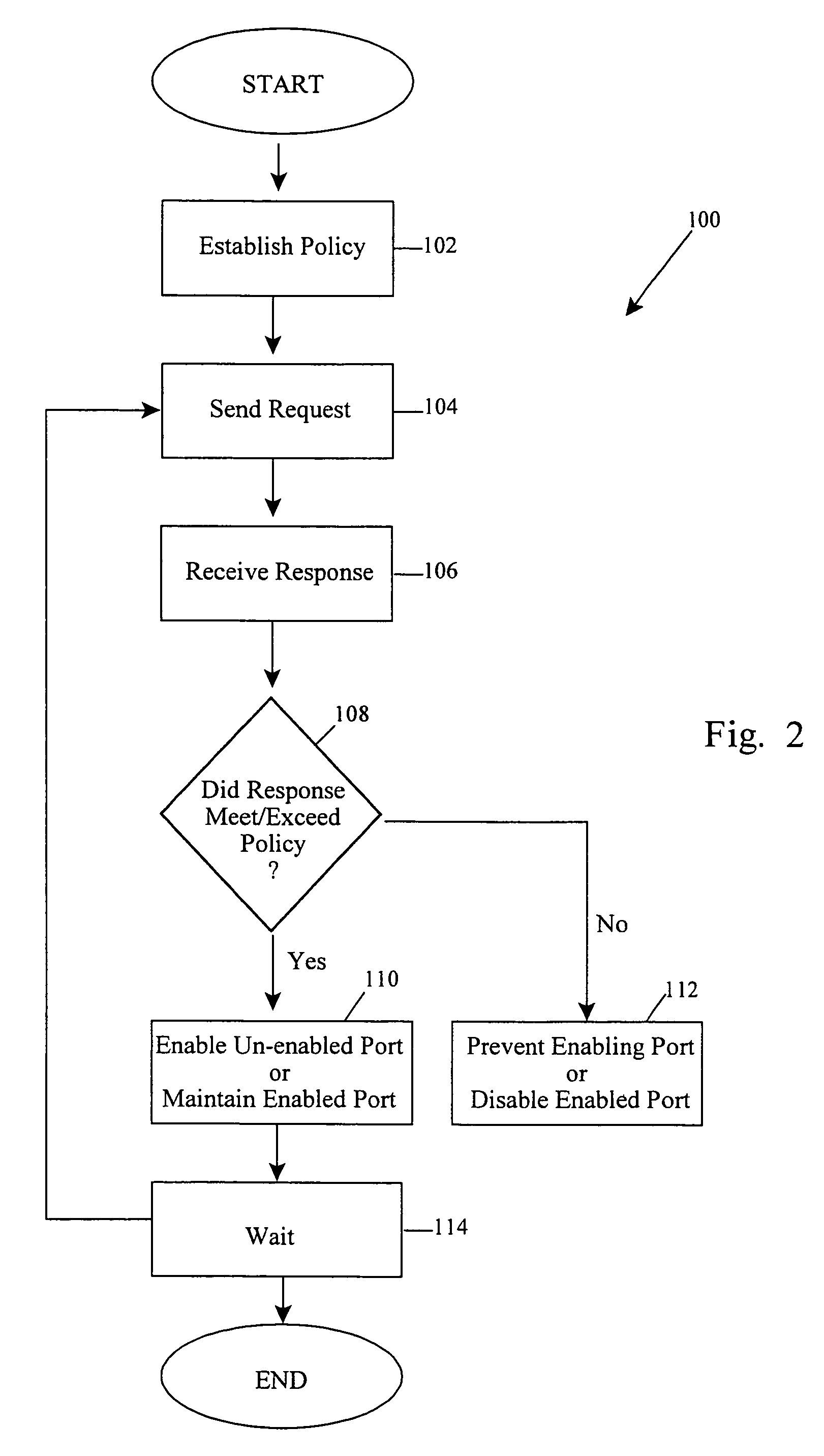
Control of communication ports of computing devices using policy-based decisions
In a computing system environment, an arrangement of computing devices includes multiple layers behind a content flow director, such as an L4 switch in a web service. In a computing device of an outermost layer directly communicating with the content flow director, a communications port is conditionally enabled upon policy being met or exceeded in the computing system environment behind the content flow director. If unmet, the communications port is disabled, if already enabled, or prevented from becoming enabled, if not otherwise already enabled. In this manner, policy establishes port enablement. In certain aspects, policy determinations include determining a time of response, a quality of service check or a pass / fail condition of the one of the computing devices. Policy is also easily implemented as remote or local computer executable instructions on the computing devices. Representative computing devices include switches, such as L4 switches, routers, servers, repeaters, adapters or the like.
Owner:APPLE INC
Intelligent failback in a load-balanced networking environment
InactiveCN101383732AImprove performanceHardware monitoringMultiple digital computer combinationsBalancing networkNetwork connection
One embodiment of the present invention sets forth a method for failing back network connections to a network interface card (NIC) within a computing device. The method includes the steps of monitoring a failed or unreliable NIC within the computing device, determining that the failed or unreliable NIC has recovered, determining that a functional NIC within the computing device is overloaded, selecting a first connection set communicating through the overloaded NIC, and transferring the first connection set to the recovered NIC. With this approach, intelligent decisions can be advantageously made regarding whether to fail back a network connection set to a recovered NIC based on the traffic loads on the overloaded NIC and the recovered NIC. Such an approach to balancing network traffic across the functional NICs within a computing device may substantially improve overall performance relative to prior art techniques.
Owner:NVIDIA CORP
Identifying malicious devices within a computer network
InactiveCN104426906AComputer security arrangementsTransmissionInternet trafficReliability engineering
This disclosure describes techniques for proactively identifying possible attackers based on a profile of a device. For example, a device includes one or more processors and network interface cards to receive, from a remote device, network traffic directed to one or more computing devices protected by the device, determine, based on content of the network traffic, a first set of data points for the device, send a response to the remote device to ascertain a second set of data points for the device, and receive, from the remote device, at least a portion of the second set of data points. The device also includes a security module operable by the processors to determine a maliciousness rating, and selectively manage, based on the maliciousness rating, additional network traffic directed to the one or more computing devices protected by the security device and received from the remote device.
Owner:JUMIPER NETWORKS INC
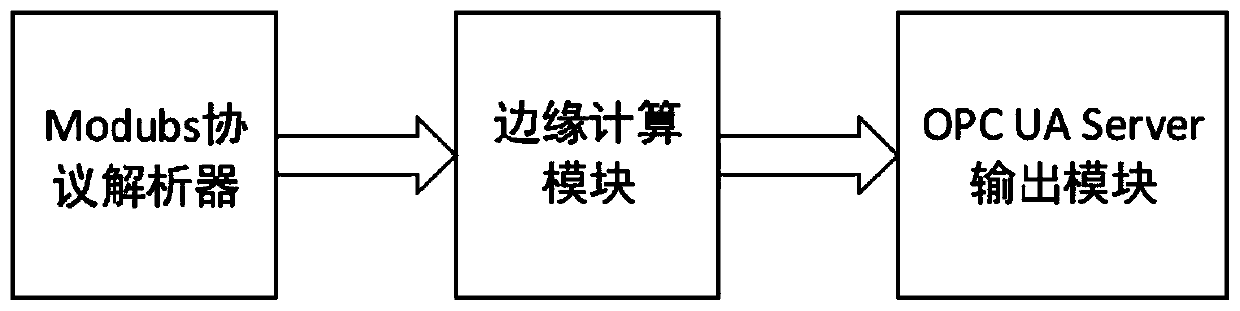
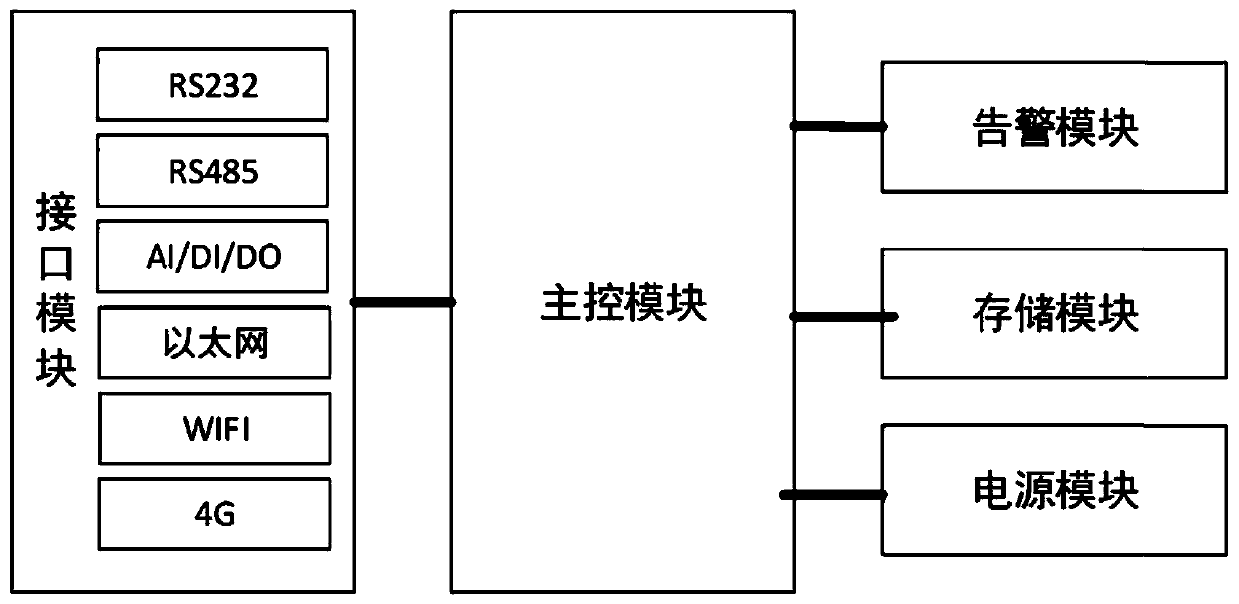
Edge computing intelligent adapter for industrial manufacturing and implementation method
InactiveCN110191138ARelieve dealing with stressReduce data processing pressureTransmissionModbusData center
The invention discloses an edge computing intelligent adapter for industrial manufacturing and an implementation method. The adapter comprises a Modbus protocol analyzer, an AI / DI / DO signal processingmodule, an edge computing module and an output module. The Modbus protocol analyzer analyzes the data of the acquisition equipment; the AI / DI / DO signal processing module converts analog quantity anddigital quantity input into digital quantity output control signals; the edge calculation module obtains prediction information through a lightweight machine learning algorithm submodule; a data processing sub-module performs data processing according to a processing mode preset by the configuration sub-module, the processed data is stored in the storage sub-module, and the output module providesOPC UA server service, reads the data in the storage sub-module, performs man-machine interaction operation and reports the data transmission at the same time. The edge calculation processing alleviates the network bandwidth and the data processing pressure of the data center, and enhances the response capability of the cloud service.
Owner:SHENYANG INST OF AUTOMATION GUANGZHOU CHINESE ACAD OF SCI +1
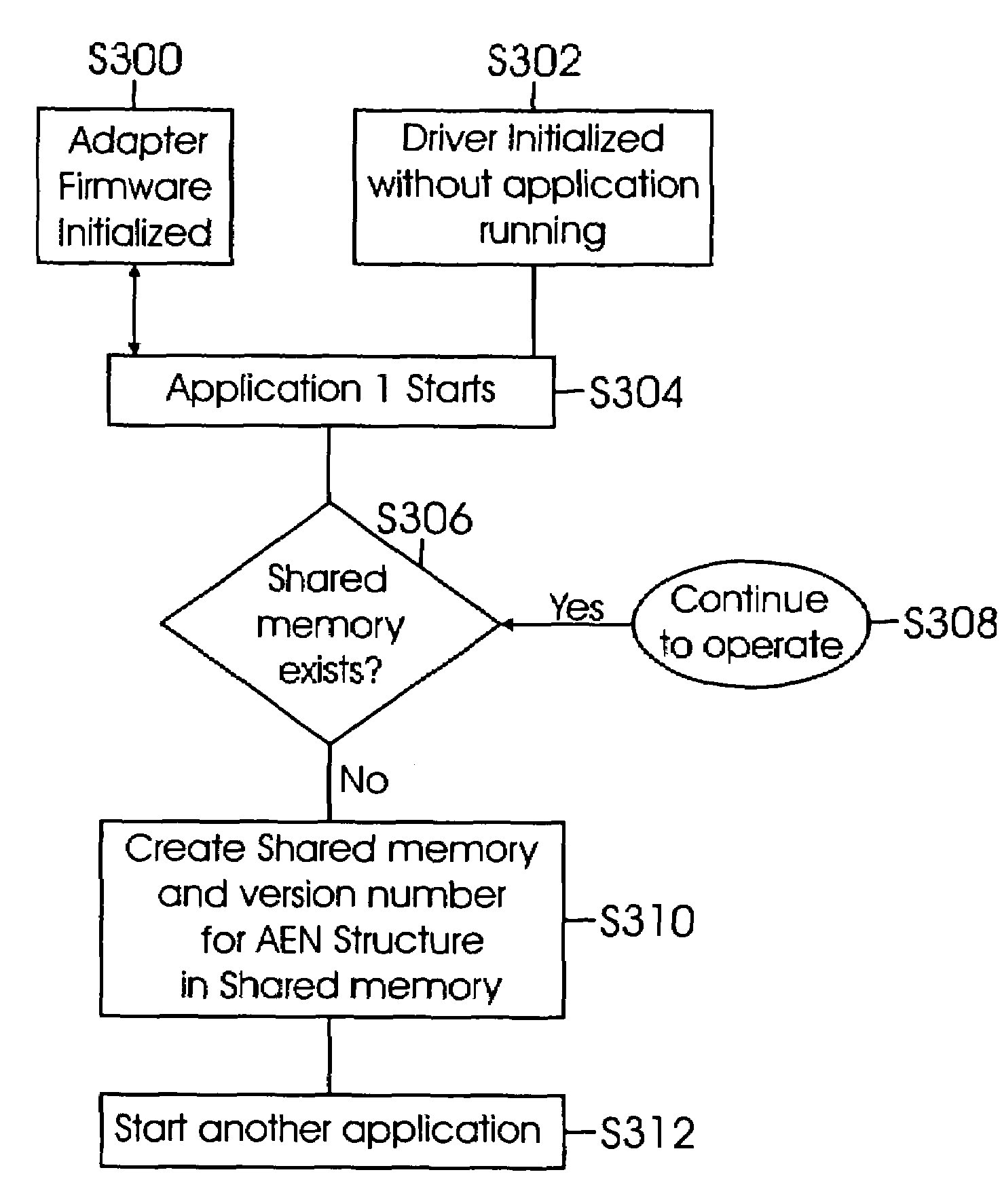
Method and system for processing asynchronous event notifications
InactiveUS7457887B1Quick understandingProgram controlInput/output processes for data processingComputer architectureEngineering
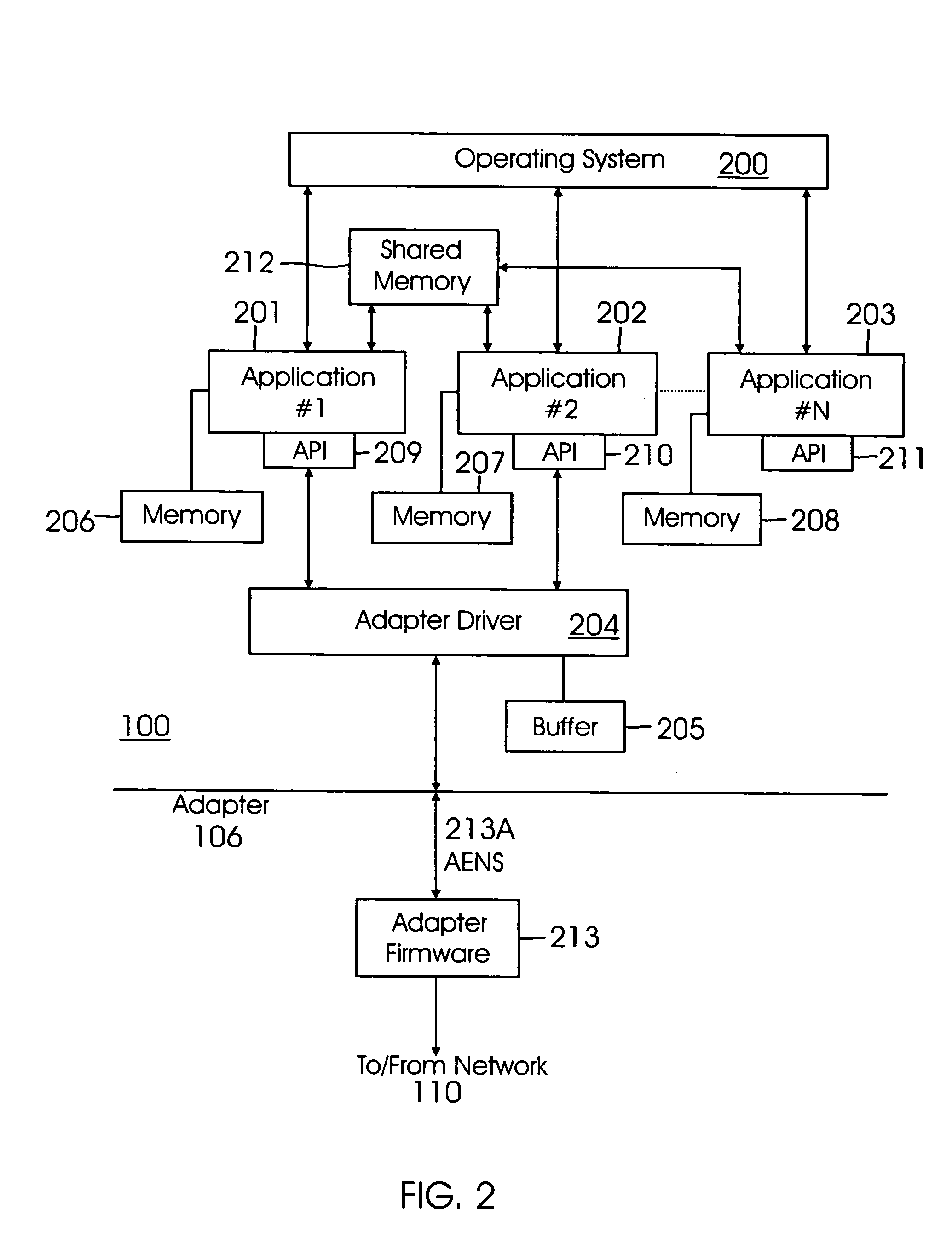
Method and system for managing asynchronous event notifications (AENs) including comparing an AEN sequence number at a shared memory location with an AEN sequence number at a local memory location controlled by a application; acquiring an AEN from the shared memory, if the sequence number of the AEN in the local memory is different from the sequence number of the AEN in shared memory; determining if a version number of the AEN is current; and generating an AEN if the version number is not current, wherein the generated AEN allows other applications to update AEN version numbers. The system includes firmware code executed in an adapter; an adapter driver executed on a host computing system stores the AENs in a memory buffer; and a plurality of applications that use a shared memory where AENs and a version number associated with the AENs are stored.
Owner:MARVELL ASIA PTE LTD
Technique for controlling selection of a write adapter from multiple adapters connected to a high speed switch
InactiveUS7161954B2Slow writing of dataIncrease path lengthError preventionTransmission systemsDistributed Computing EnvironmentControl selection
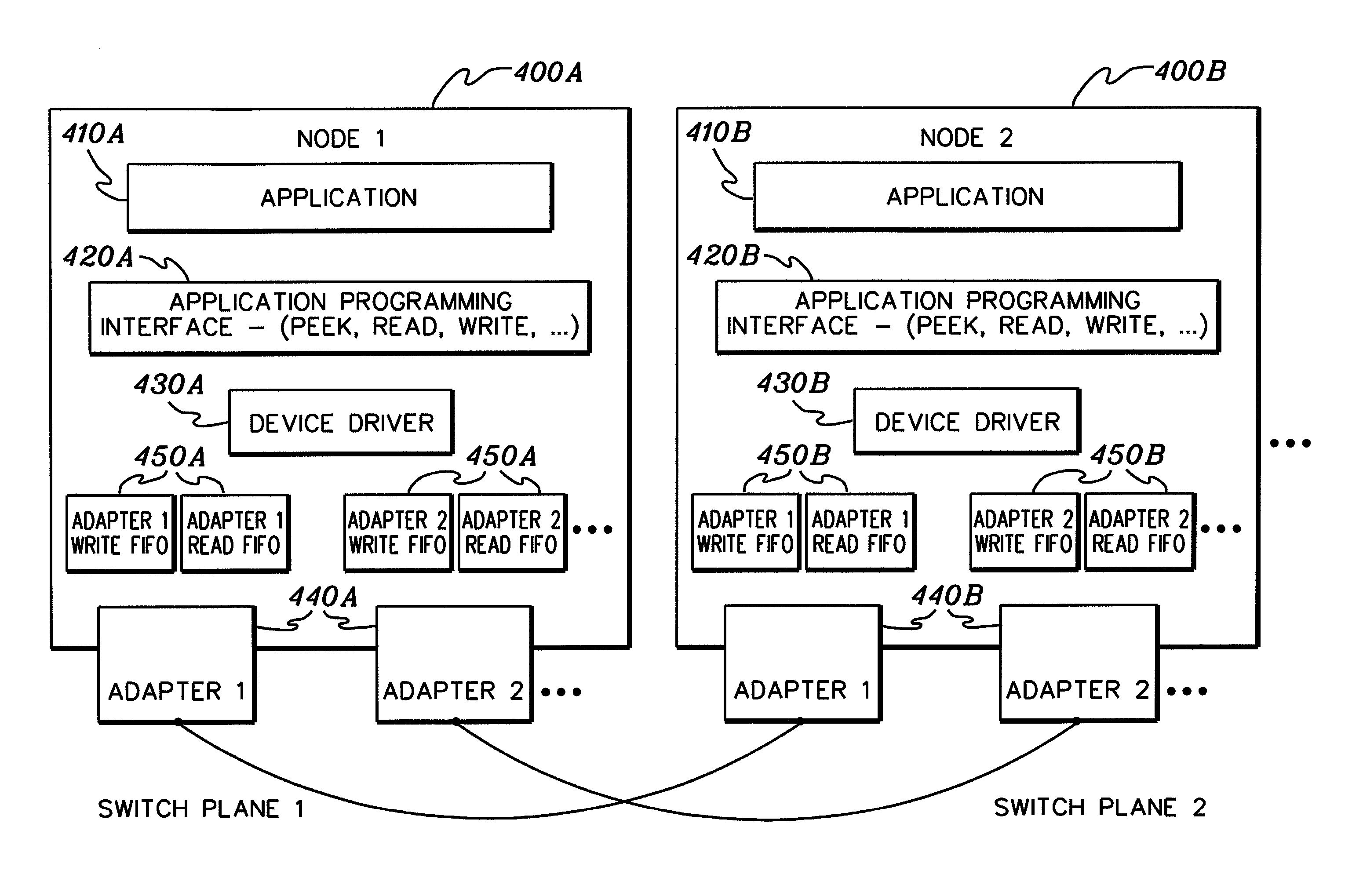
A technique is provided for facilitating writing of messages to multiple adapters connected to a high speed switch in a distributed computing environment. The technique employs a first, relatively quick filter to initially test whether a previously used adapter of the multiple adapters should be used to send a new message. If the first filter fails to select the previously used adapter, then the technique includes employing a second, more complicated filter to determine which adapter of the multiple adapters should be used to send the message. The first filter includes a first set of tests, and the second filter includes a second set of tests.
Owner:INT BUSINESS MASCH CORP
Method, system and program product for correlating data between operating environments
A data correlation technique is provided for a computing environment having multiple independent operating environments. The technique includes associating by a first operating environment a first key to a set of data to be obtained responsive to an identified event within the computing environment; obtaining by a second operating environment the set of data with the associated first key, and associating a second key therewith; and using the set of data with the associated first key and second key to match to the set of data at least one other set of data obtained by the first operating environment or the second operating environment responsive to the event. The at least one other set of data has only the first key or the second key associated therewith. In one implementation, the event is a fatal event at a network interface adapter.
Owner:INT BUSINESS MASCH CORP
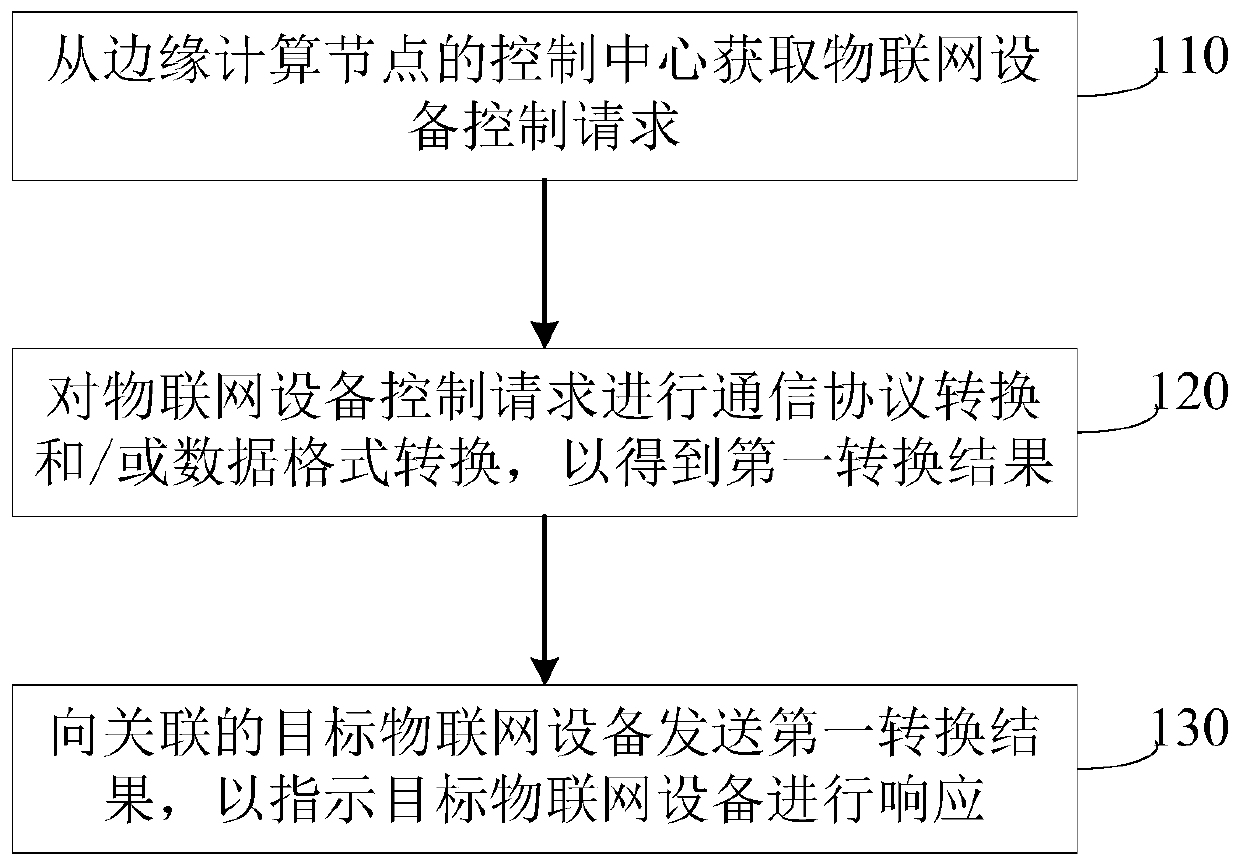
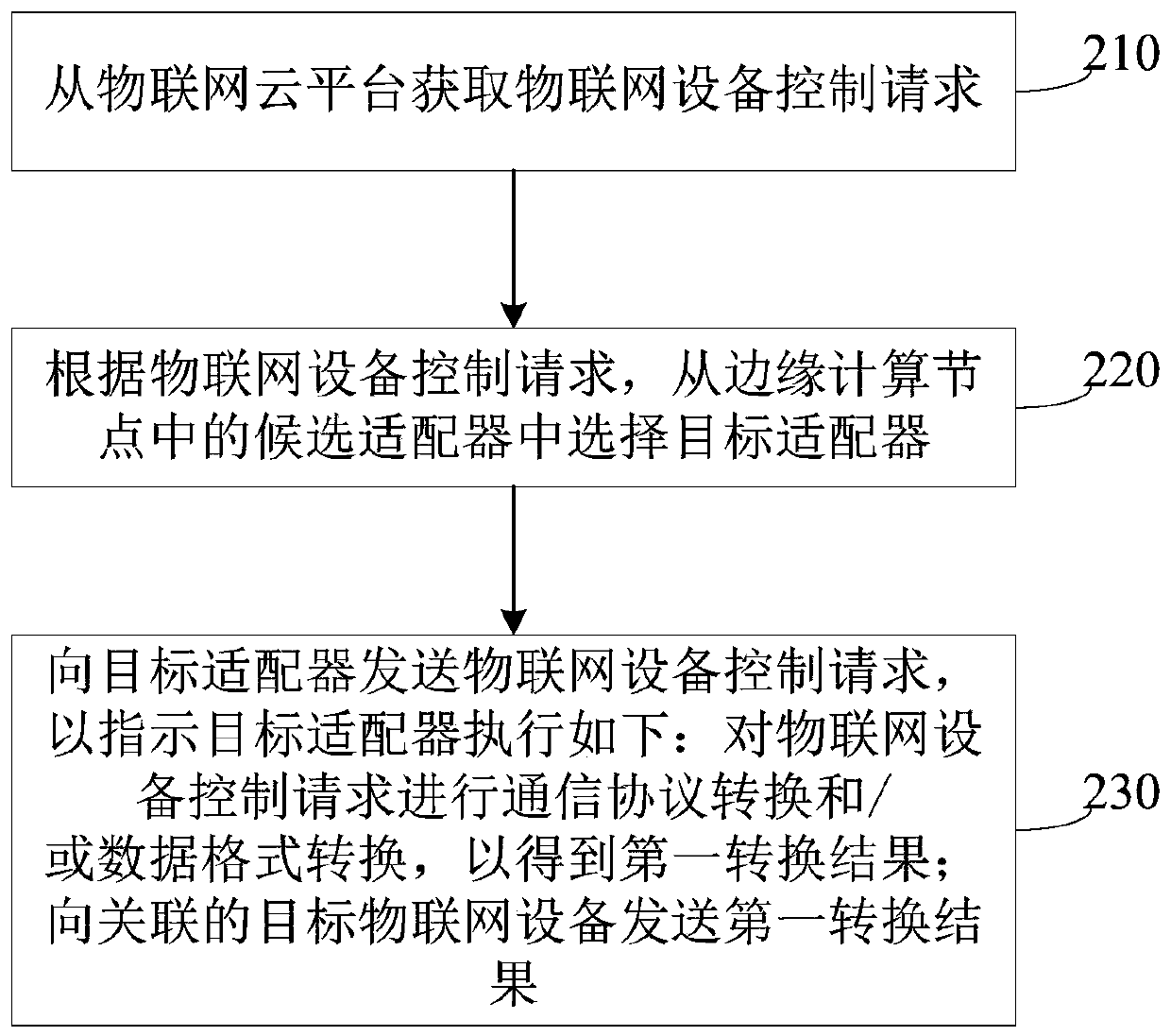
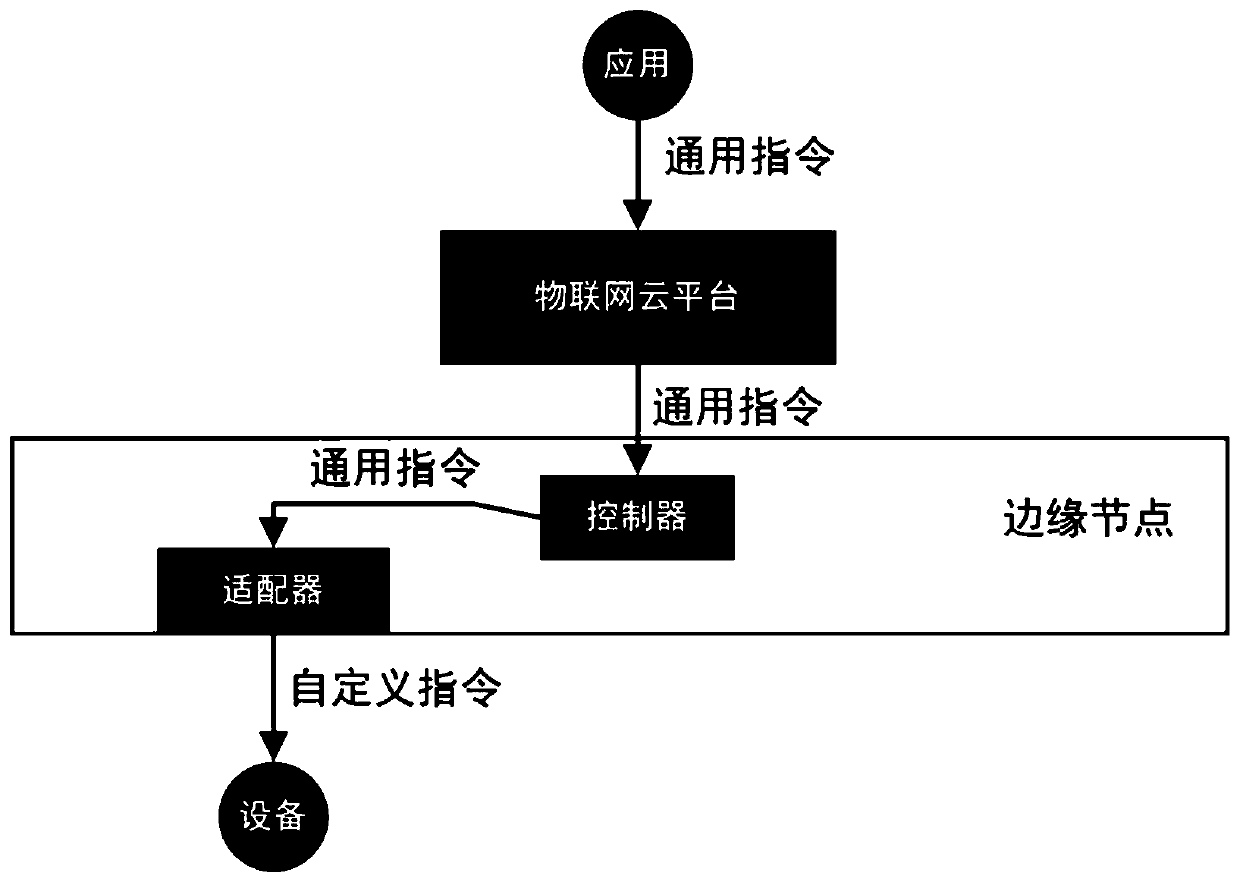
Control method, device and equipment of Internet of Things equipment and storage medium
InactiveCN111432000AReduce work stressPrevent affecting operationTransmissionComputer networkEdge computing
The embodiment of the invention discloses a control method, device and equipment of Internet of Things equipment and a storage medium. The method is executed by an adapter of an edge computing node, and comprises the following steps: acquiring an Internet of Things equipment control request from a control center of the edge computing node; performing communication protocol conversion and / or data format conversion on the Internet of Things equipment control request to obtain a first conversion result; and sending the first conversion result to associated target Internet of Things equipment to indicate the target Internet of Things equipment to respond. The Internet of Things equipment control request is converted into a format which can be received by the target Internet of Things equipmentat the edge computing node through the target adapter, so that the pressure of an Internet of Things cloud platform center is reduced, the equipment control time is saved, and the equipment control efficiency is improved.
Owner:CHINA CONSTRUCTION BANK
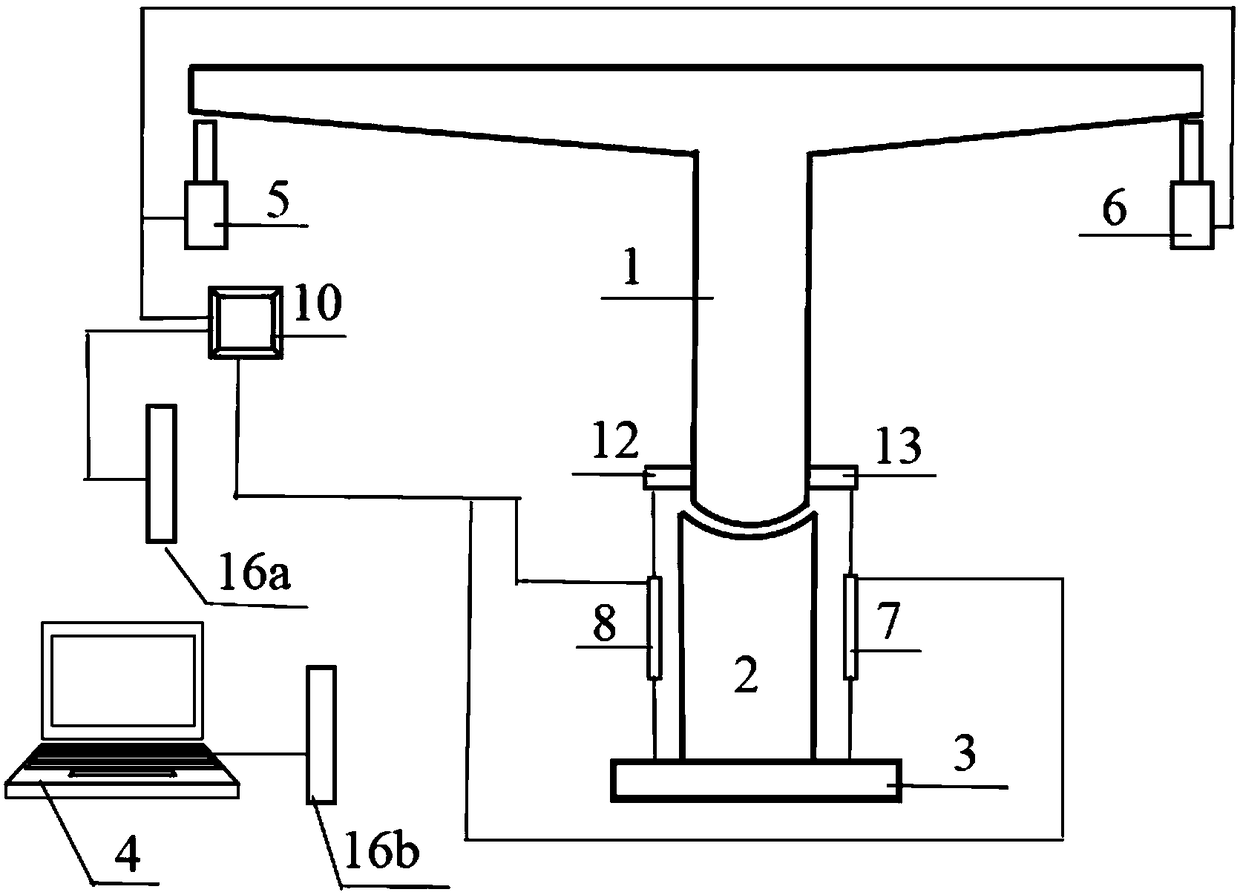
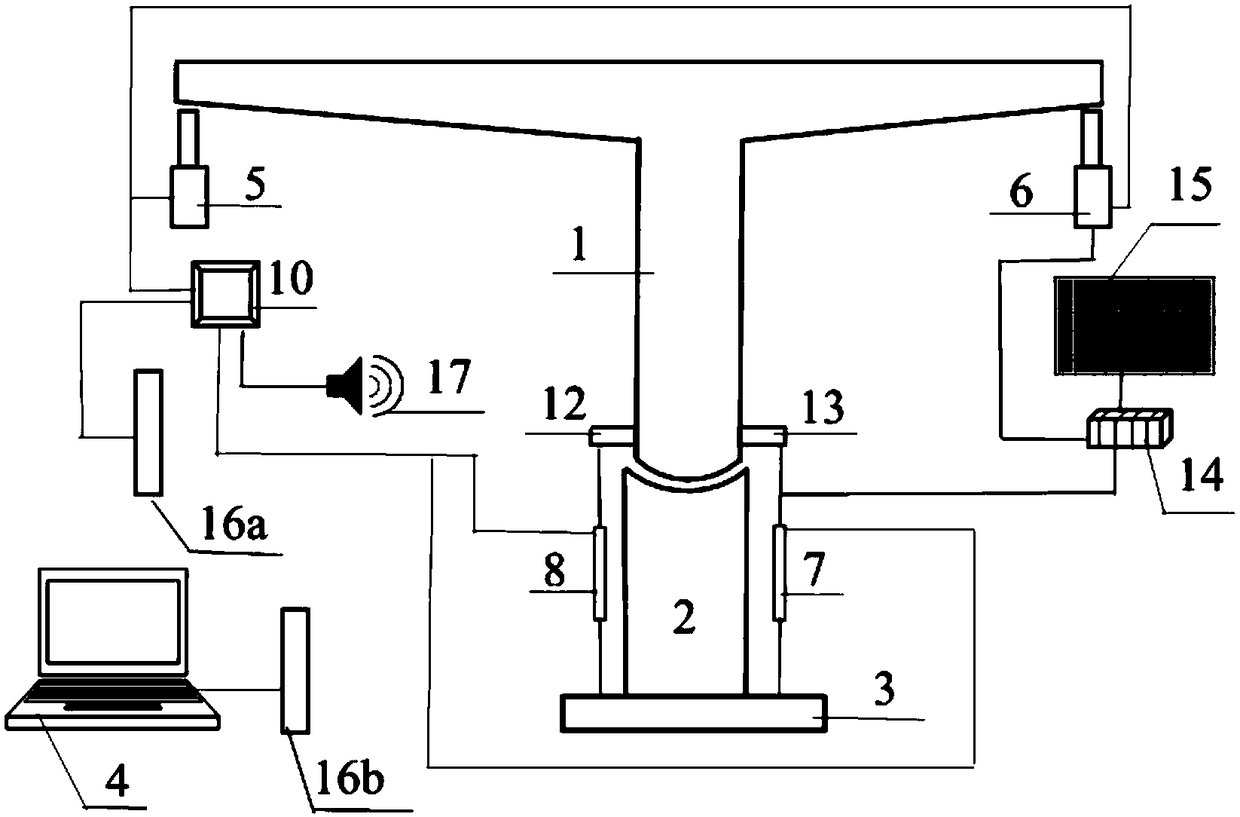
Device and method for judging critical balance of rotation of bridge and computing method
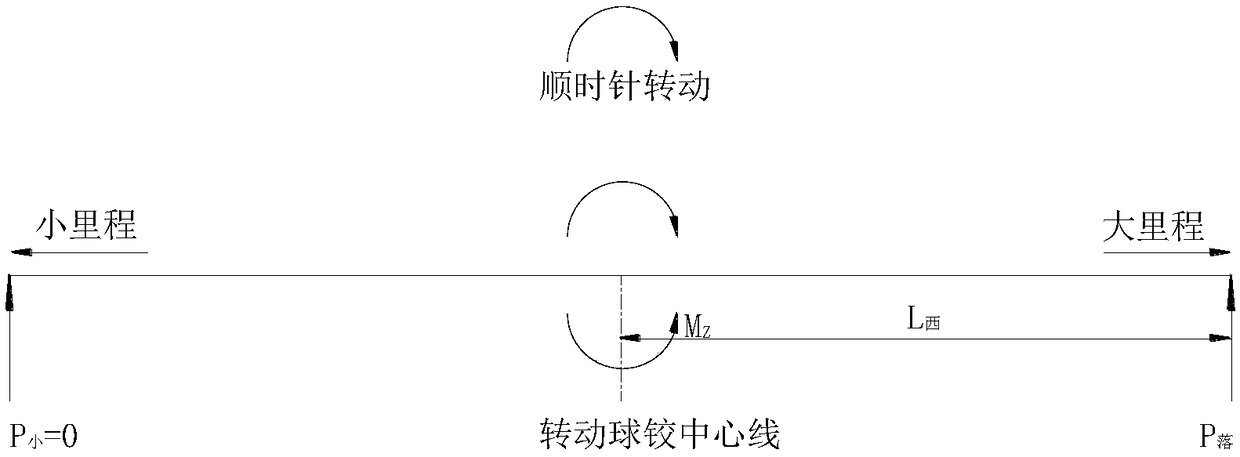
ActiveCN108982013AImprove construction qualityAvoid hinge slippageGeometric CADStatic/dynamic balance measurementStatic friction coefficientTest efficiency
The invention discloses a device for judging the critical balance of the rotation of a bridge, a method for judging the critical balance of the rotation of the bridge, and a method for calculating thestatic friction coefficient of a rotating spherical hinge in the rotation construction of the bridge. The device comprises a beam body, the rotating spherical hinge and a control device. A first jackand a second jack for loading the beam end of the beam body are arranged under the beam end of the beam body. One end, close to the rotating spherical hinge, of the beam body is symmetrically provided with a first adapter plate and a second adapter plate. The first adapter plate and the second adapter plate are respectively connected with a first displacement sensor and a second displacement sensor for measuring displacement. The critical balance state of the rotation of the beam body and the e rotating spherical hinge are searched out during loading, and the measurement of the static friction coefficient of the rotating spherical hinge in the key technology in the rotation construction of the bridge is achieved. The objective of the invention aims at improving the testing efficiency andconstruction safety, and finally achieving the improvement of the rotation construction of the bridge and the decrease of the safety risk of construction.
Owner:CHINA RAILWAY BRIDGE SCI RES INST LTD +1
Mass storage virtualization for cloud computing
Aspects of the present disclosure relate to systems and methods for virtualizing mass storage using an interface card, or other special hardware unit, operatively coupled to a host system. In various implementations, the interface device and host system may collectively emulate a mass storage device for another “terminal” computing system in a manner that is transparent to the terminal system. Moreover, in various implementations, a mass storage device may be emulated in a manner that is transparent to the terminal system, without requiring modifications to the terminal platform's hardware or software architecture.
Owner:SONY COMP ENTERTAINMENT AMERICA LLC
Processing system for precision tracking and instrumentation radar signal
InactiveCN110764081AEasy to handleImprove programmabilityRadio wave reradiation/reflectionComputer hardwareEngineering
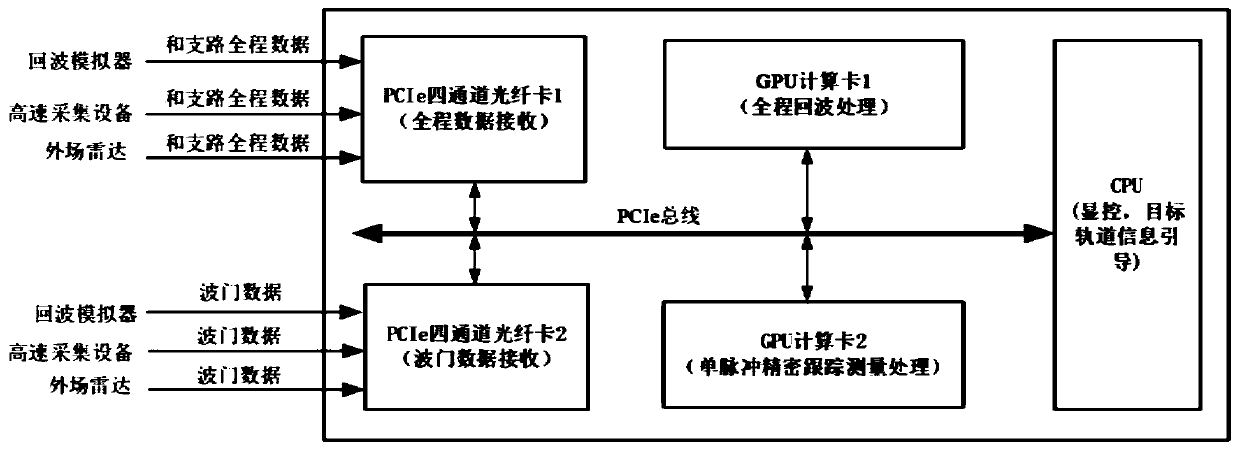
The present invention discloses a processing system for a precision tracking and instrumentation radar signal, which is composed of a commercial server, two GPU computing cards and two PCIE four-channel optical fiber interface cards on hardware. With the invention, data from an echo simulator, a high-speed acquisition device or an outfield radar can be respectively received, narrowband full rangeand gate echo signals can be respectively processed; A / R information can be generated; automatic closed-loop precision tracking and parameter measurement for a target can be carried out; echo signalswith different waveform parameters and target types under different environments can be processed; the requirements of the spatial target monopulse precision tracking and instrumentation radar for measurement accuracy, real-time capability and software adaptability can be satisfied; and the problems of traditional tracking measurement signal processors such as poor software portability, long development cycle and difficult upgrading are solved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
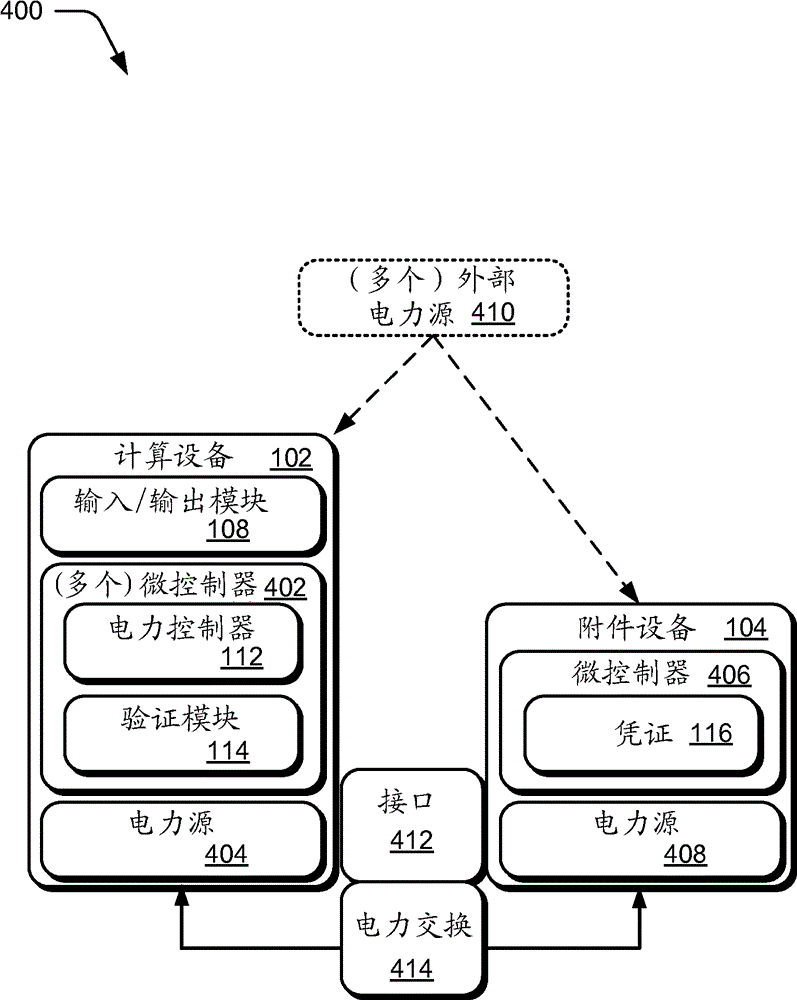
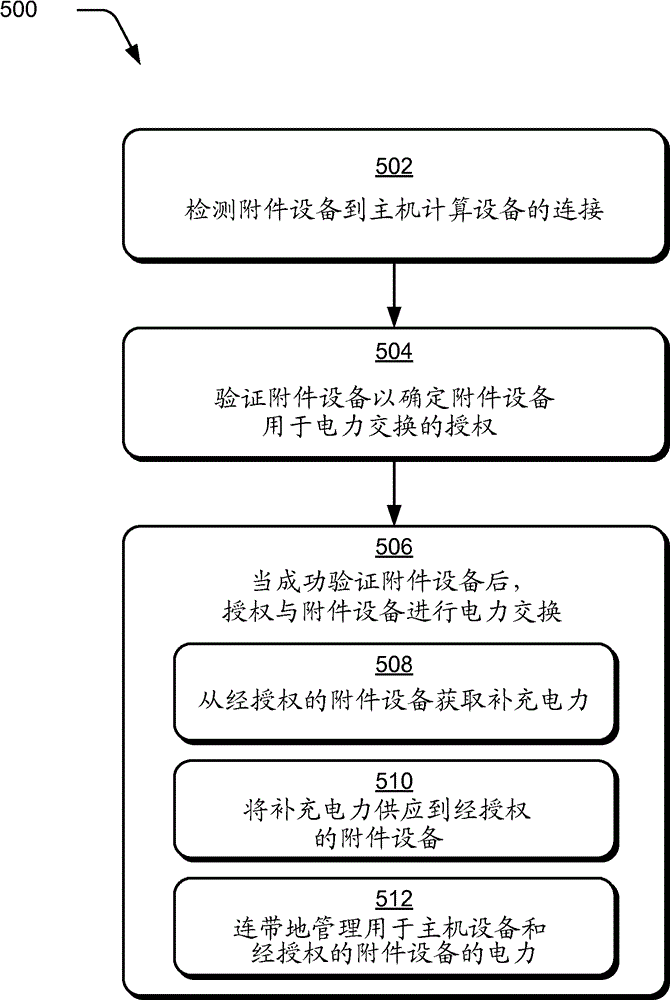
Accessory device authentication
ActiveCN104160406AVolume/mass flow measurementInternal/peripheral component protectionComputer hardwarePower exchange
Accessory device authentication techniques are described. In one or more embodiments, connection of an accessory device to a host computing device is detected. Responsive to the detection, an authentication sequence may occur to verify an identity and / or capabilities of the accessory device. Upon successful authentication of the accessory device, the host device may authorize the accessory device for power exchange interactions with the host device. The host device may then draw supplemental power from a power source associated with the authorized accessory device, such as a battery or power adapter. The host device may also enable the accessory device to obtain and use power supplied by the host device in some scenarios. Power exchange between a host device and an authorized accessory may be managed in accordance with capabilities of the accessory device that are identified during authentication.
Owner:MICROSOFT TECH LICENSING LLC
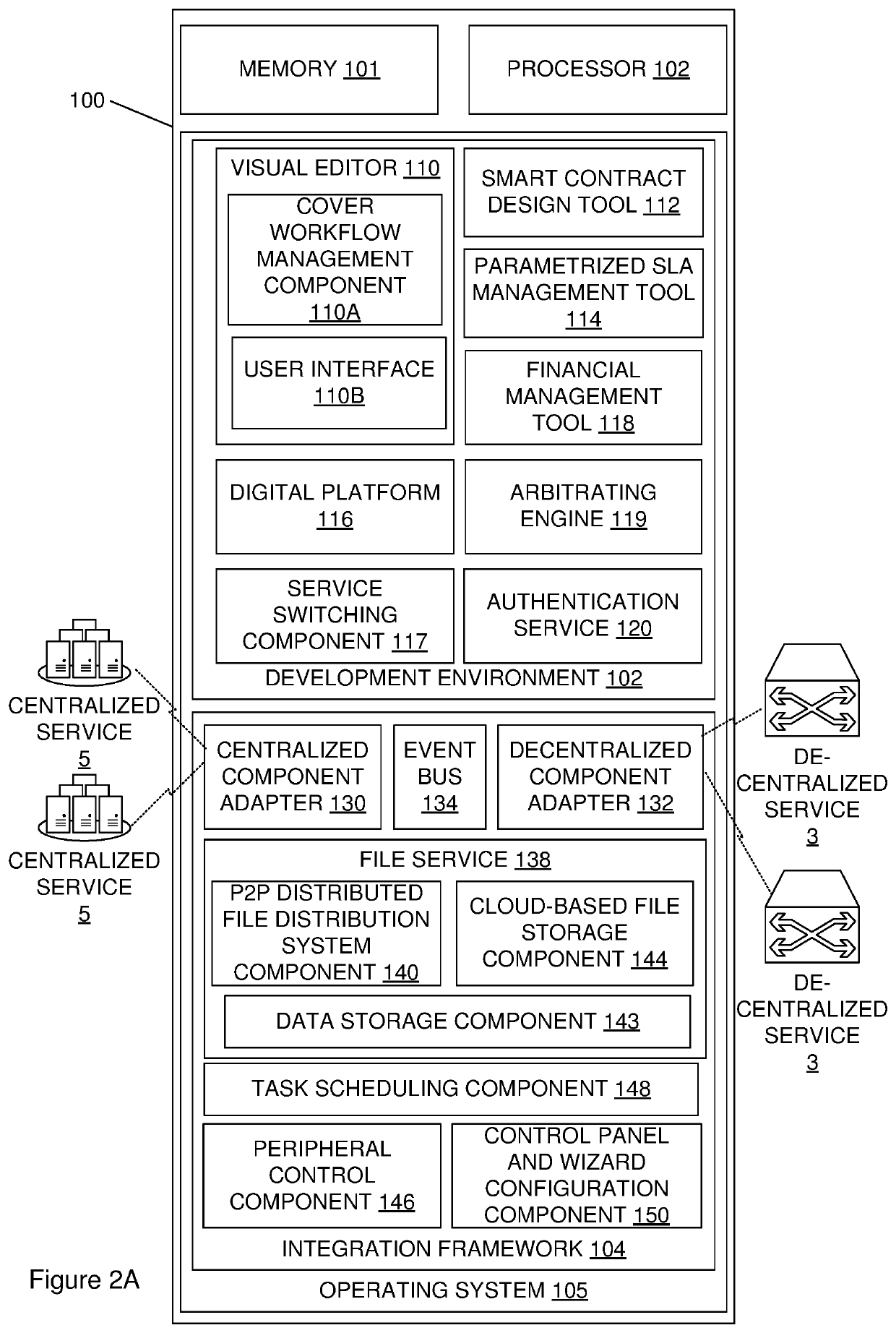
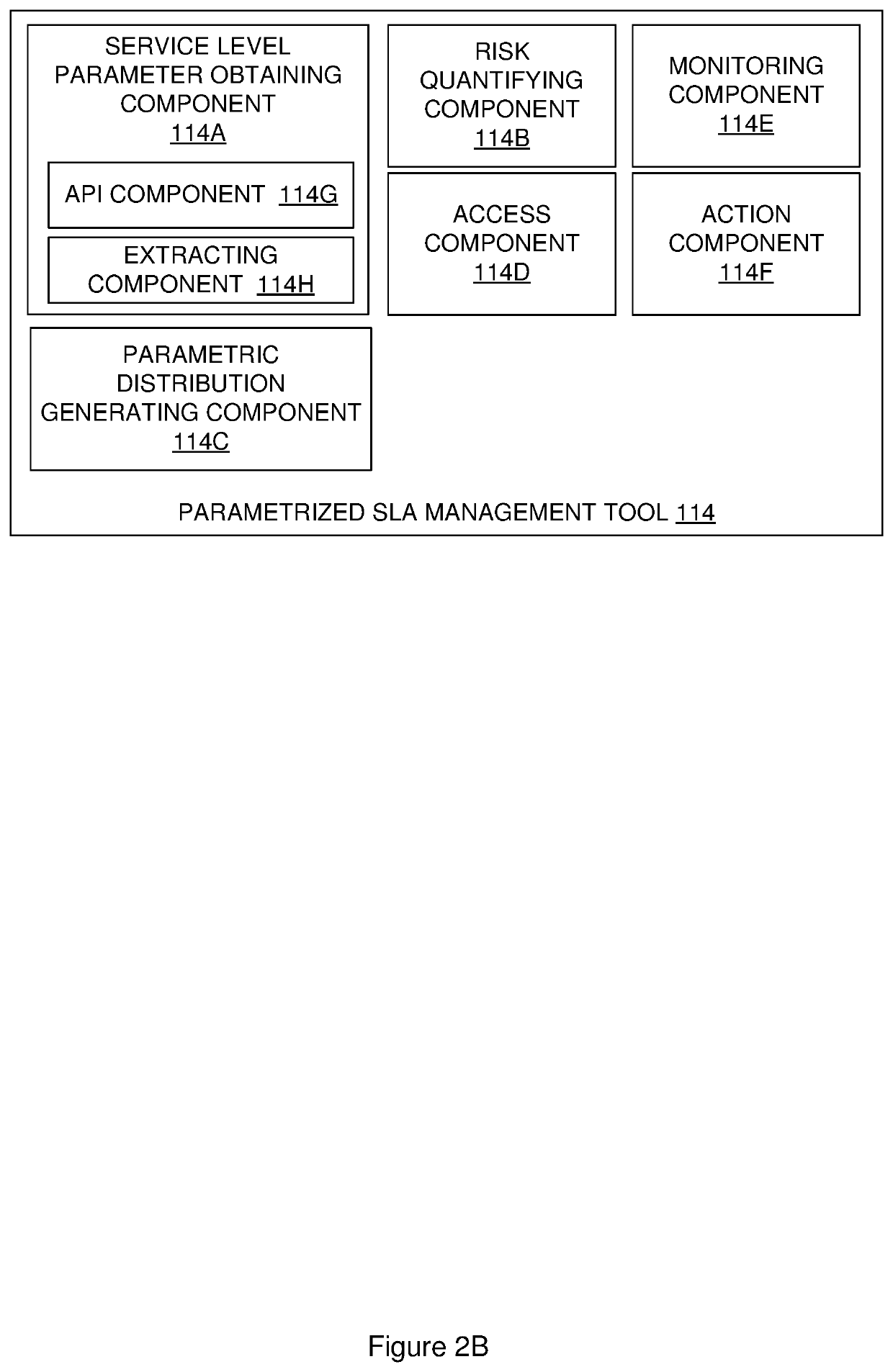
Distributed computing platform service management
A computer-implemented method and associated system is provided for distributed computing platform service management. The method is conducted by an operating system executing on a distributed computing platform accessible to client devices of an organization. The distributed computing platform facilitates access to a centralized or decentralized distributed service by the client devices. The method includes obtaining service level parameters for the service, quantifying risks associated with each parameter and generating a parametric distribution based on the quantified risks. Access is provided to the parametric distribution. The level of service associated with the distributed service is monitored via a centralized or decentralized component adapter. In response to detecting that a service level parameter is breached, a notification of the breach is transmitted to the digital platform. The notification may trigger connection of an alternative centralized or decentralized distributed service to the client devices.
Owner:TRIXTA INC
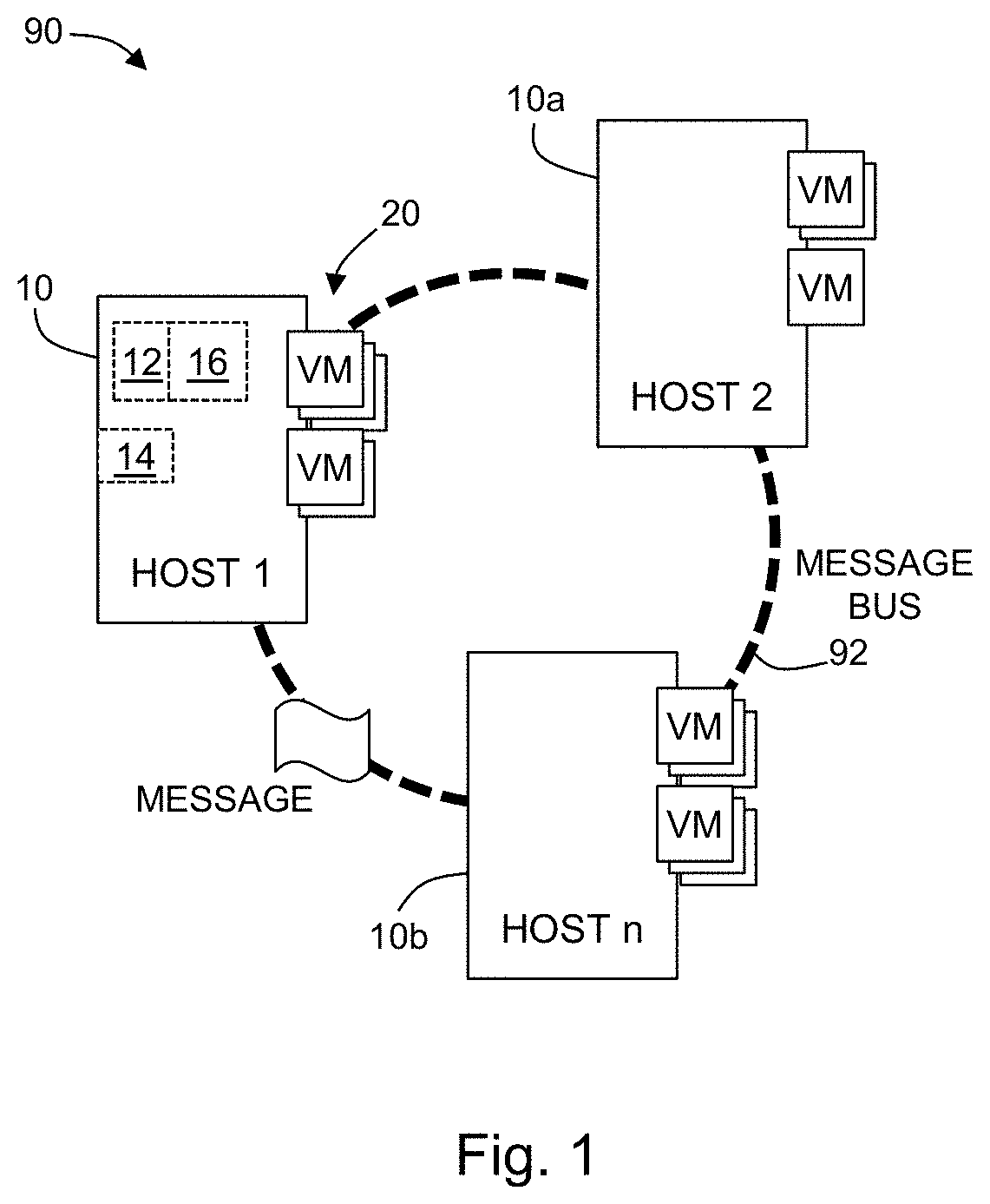
Virtual computing cluster resource scheduler
ActiveUS20210089350A1Program initiation/switchingHardware monitoringElectronic communicationTerm memory
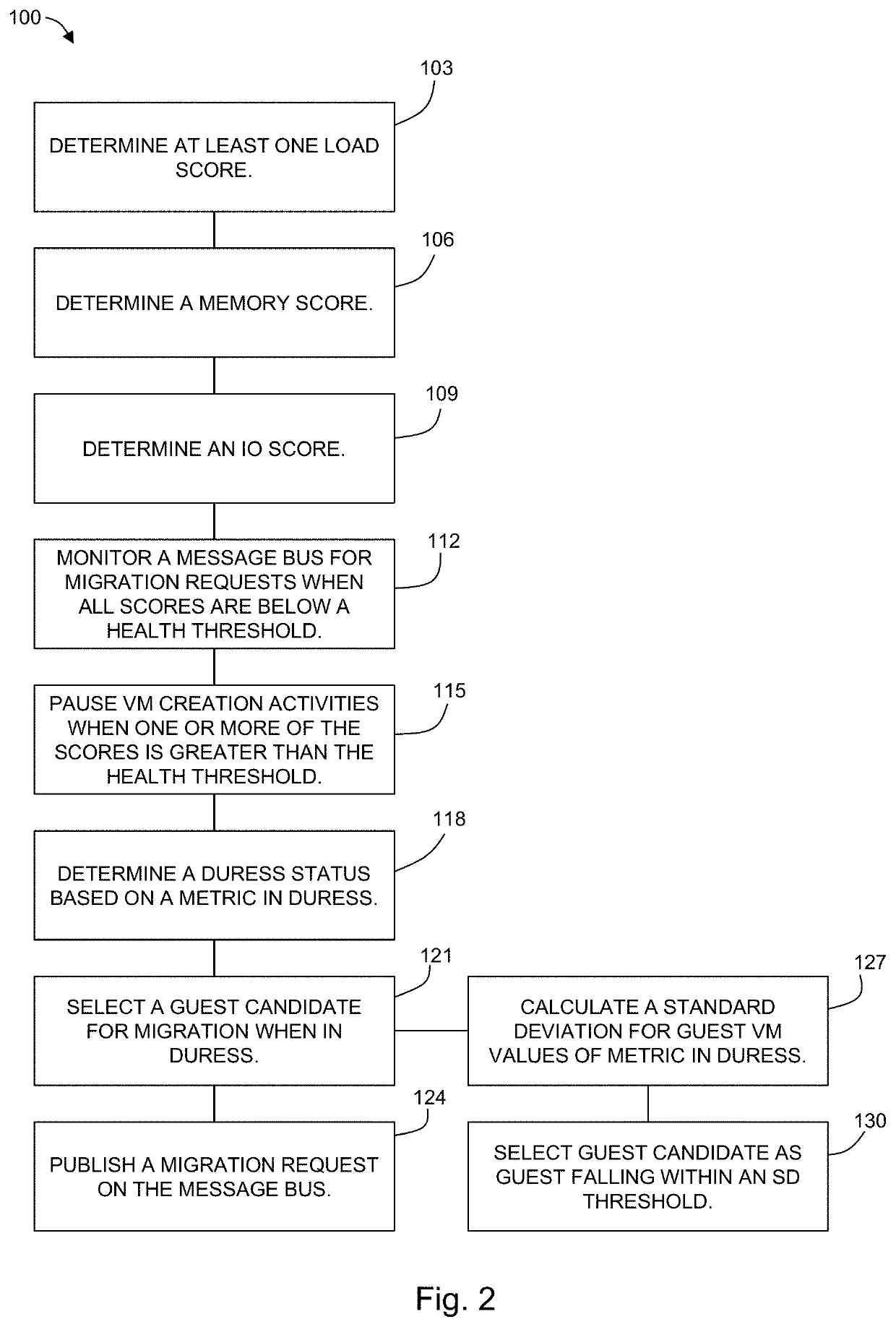
In some embodiments, a method for cluster resource scheduling, includes determining at least one load score; determining a memory score; determining an IO score; and monitoring a message bus for candidate messages when each of the at least one load score, memory score, and IO score is less than a pre-determined health threshold. In some embodiments, a host computer system for hosting a plurality of virtual machines (VMs), includes: a memory; a network adapter for communicating with the cluster by way of a message bus; a processor in electronic communication with the memory and the network adapter, wherein the processor is programmed to: determine at least one load score; determine a memory score; determine an IO score; and monitor the message bus for candidate messages when each of the at least one load score, memory score, and IO score is less than a pre-determined health threshold.
Owner:HIVEIO INC
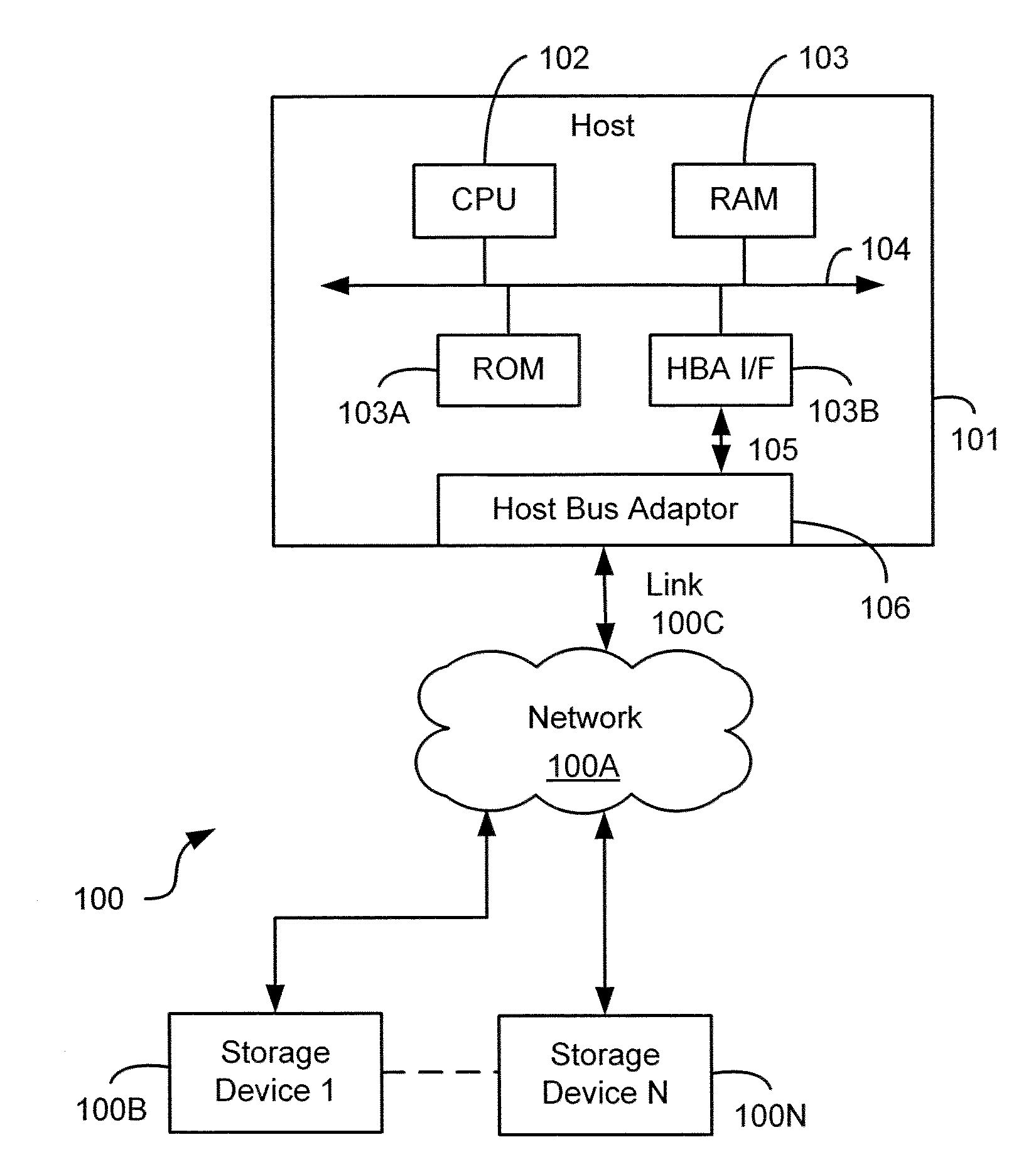
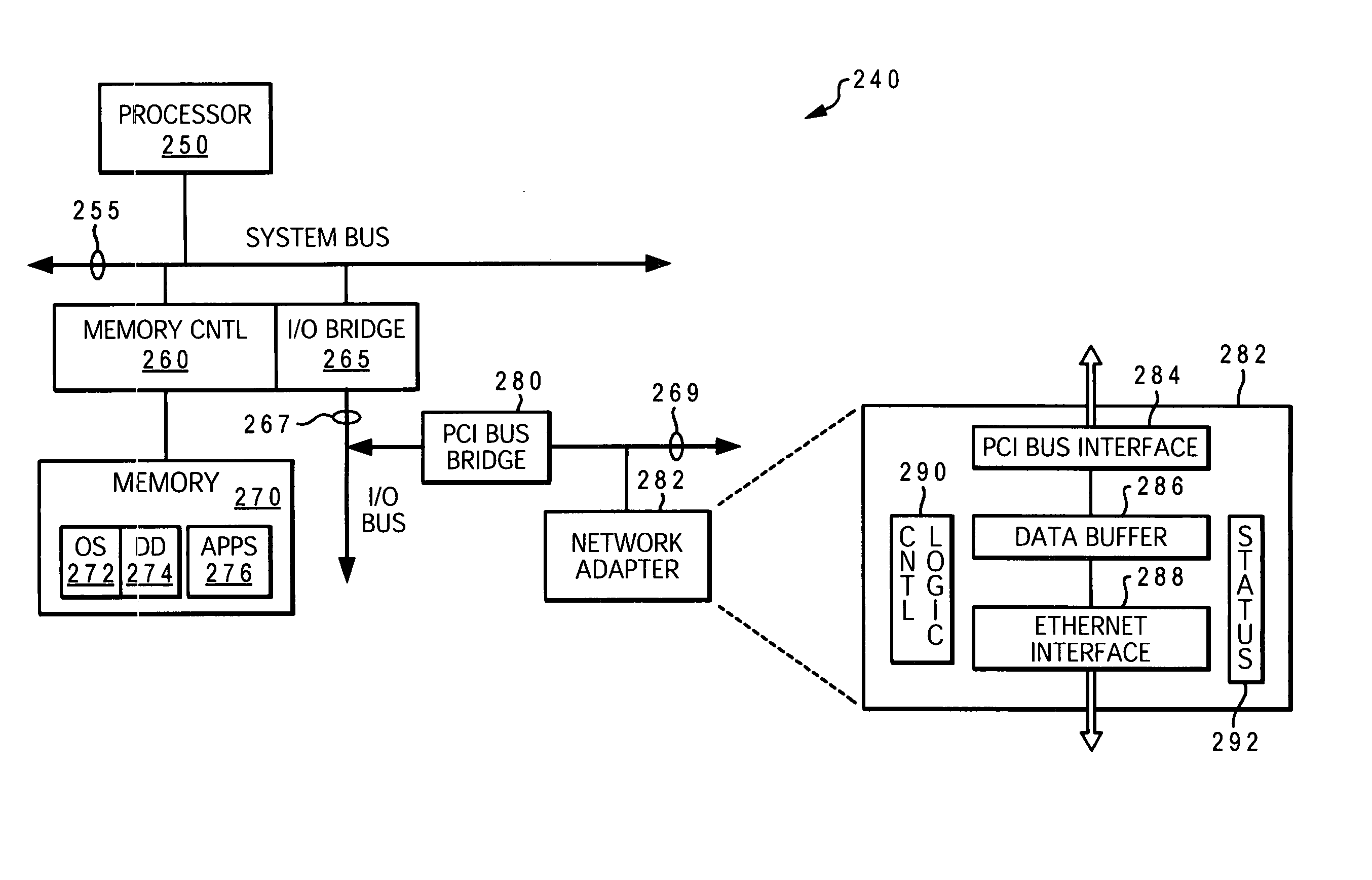
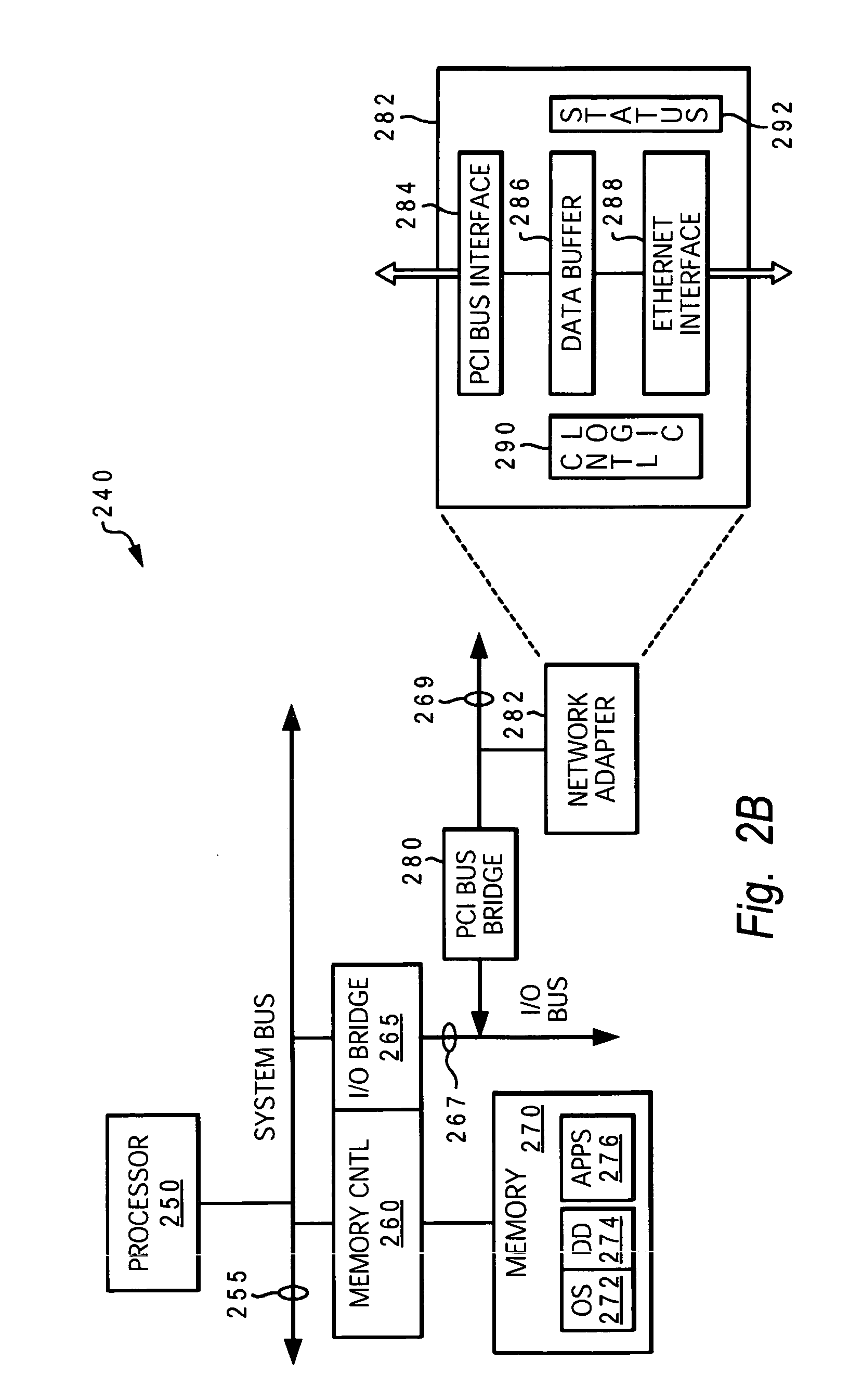
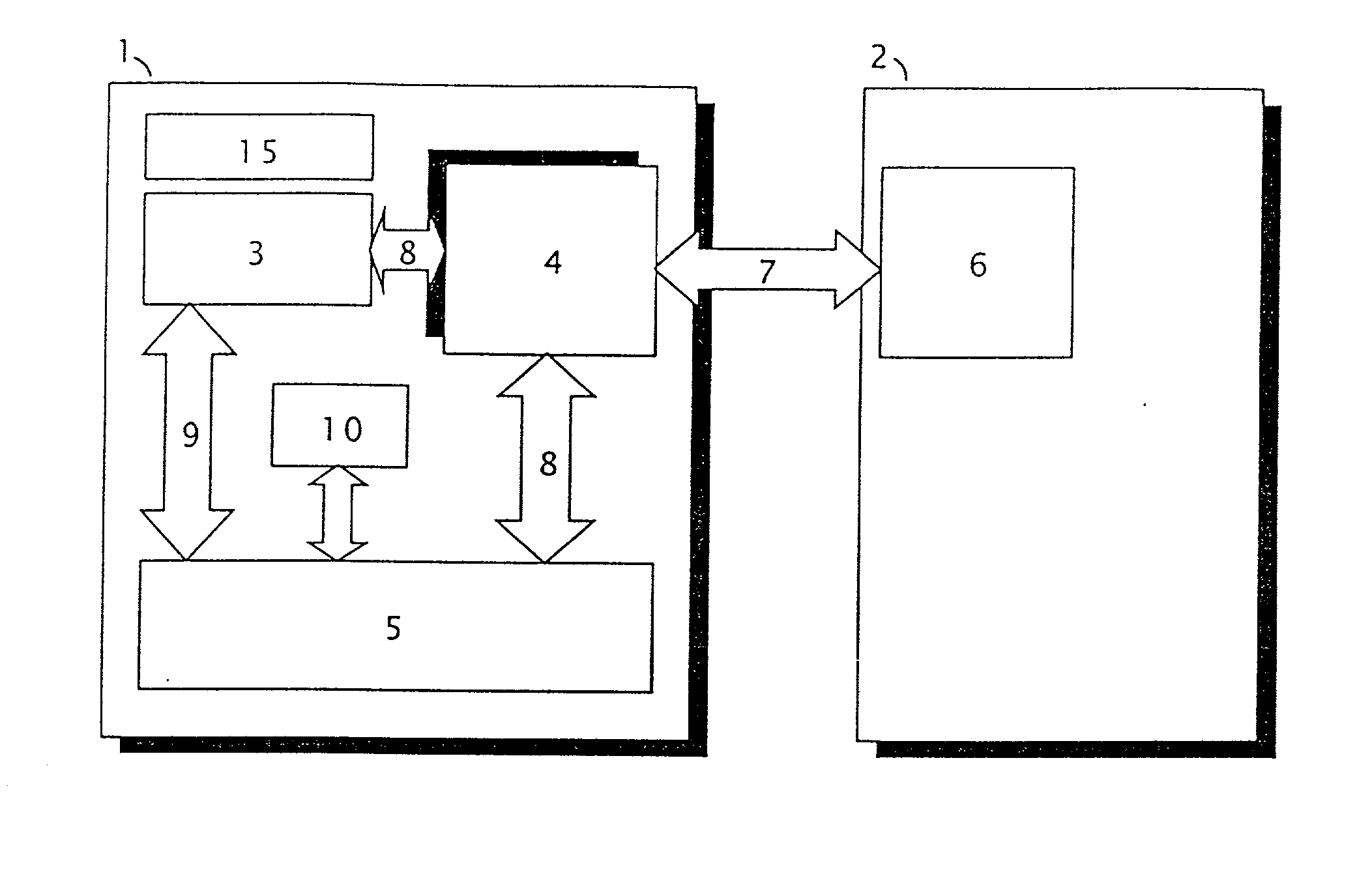
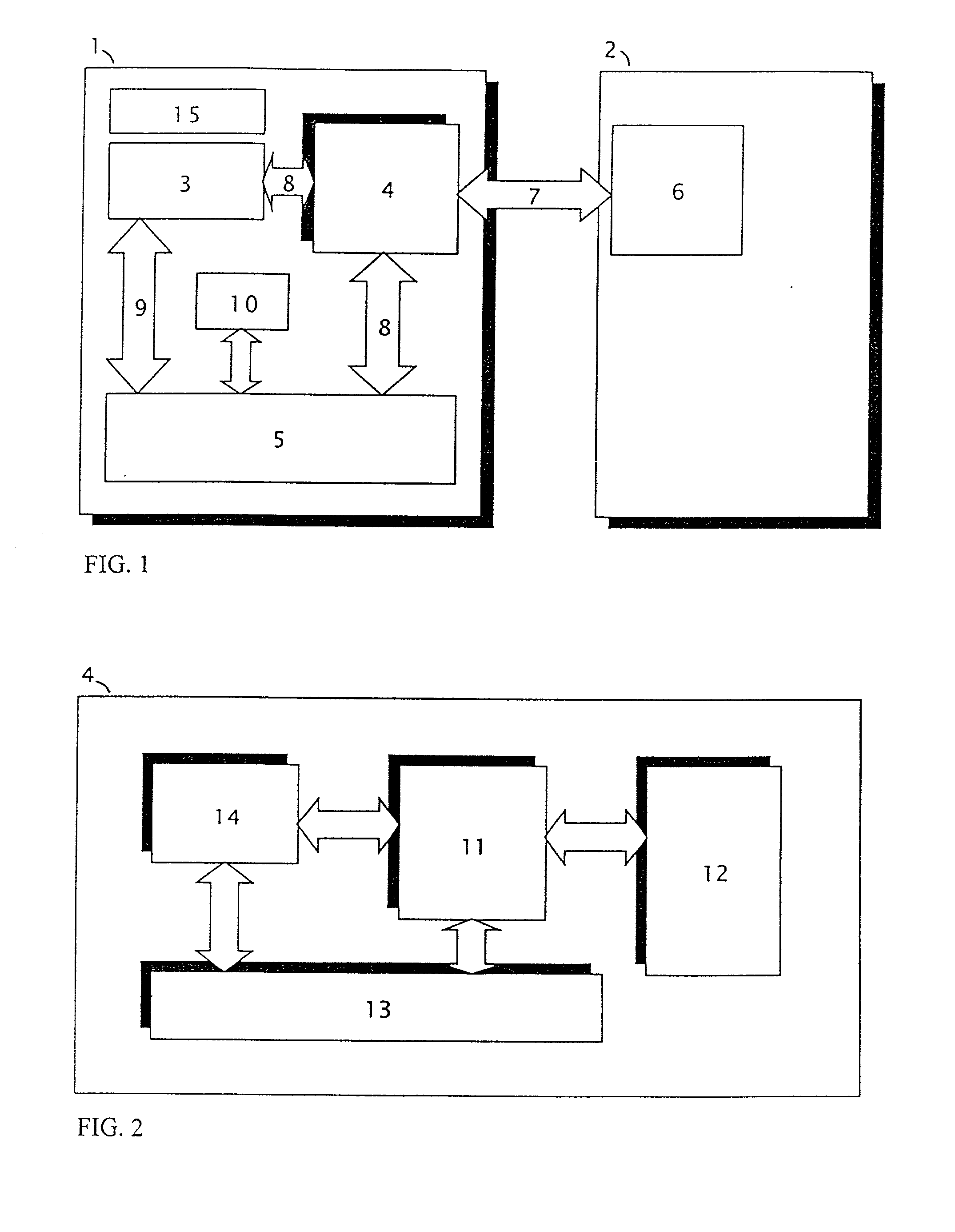
Control unit with PCI and SCSI buses and computing system with electronic semiconductor disc
Use of a control unit with PCI bus and SCSI bus with program equipment for the electronic semiconductor disc of a computing system. The electronic semiconductor disc includes a processor and semiconductor memory, selected from a group comprising dynamic memory, synchronous dynamic memory, static memory and flash type memory. A computing system (1) with electronic semiconductor disc with processor (3), where this processor (3) is connected by a PCI bus (8) to a PCI adapter (4), which is linked through the PCI bus (8) to the semiconductor memory (5), connected by the local bus (9) to a processor (3). The PCI adapter (4) comprises a unit (11) of the programmable SCSI control unit, connected both to the interface (13) of the PCI bus for communicating with the electronic semiconductor disc, and to the interface (12) of the SCSI bus for communicating with the external computing system (2) with the SCSI control unit (6).
Owner:SOLID ACCESS TECH L L C
Converged network interface card, message coding method and message transmission method thereof
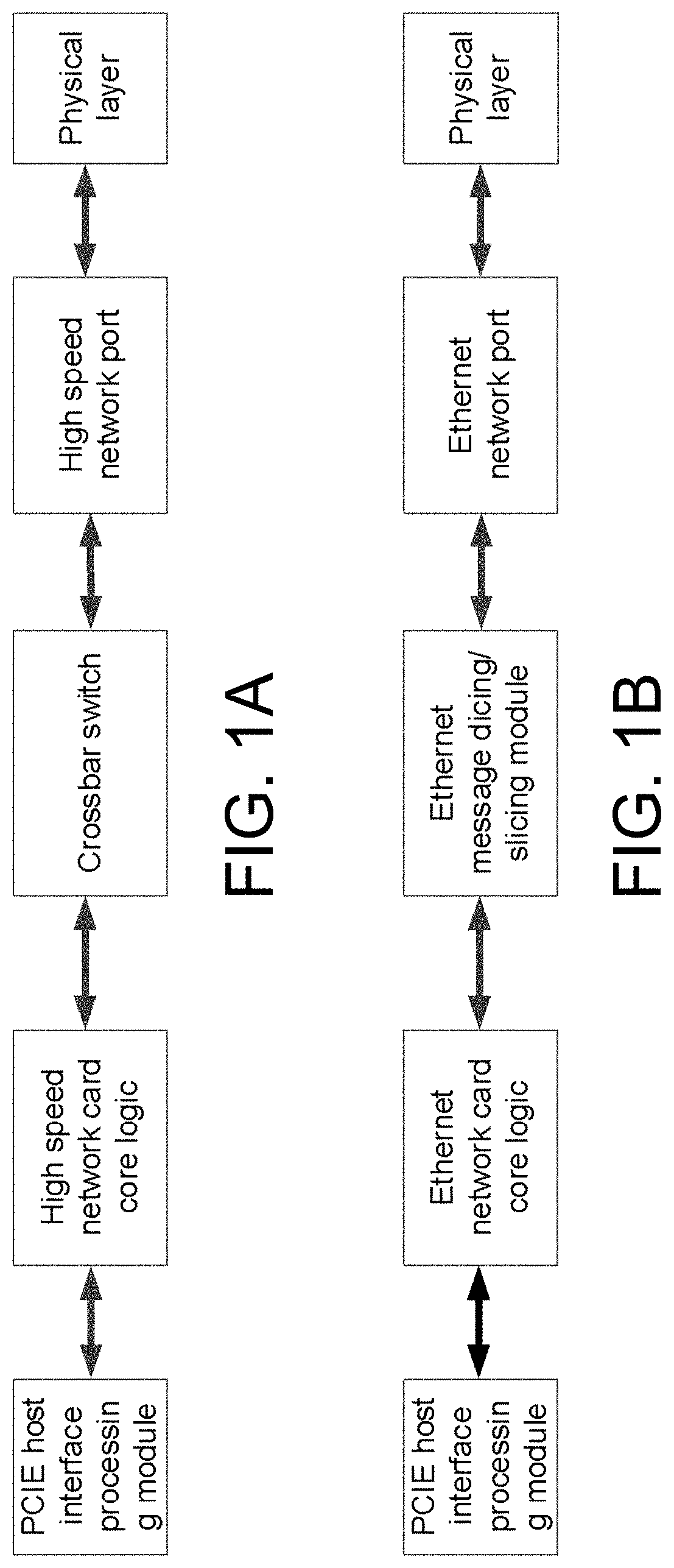
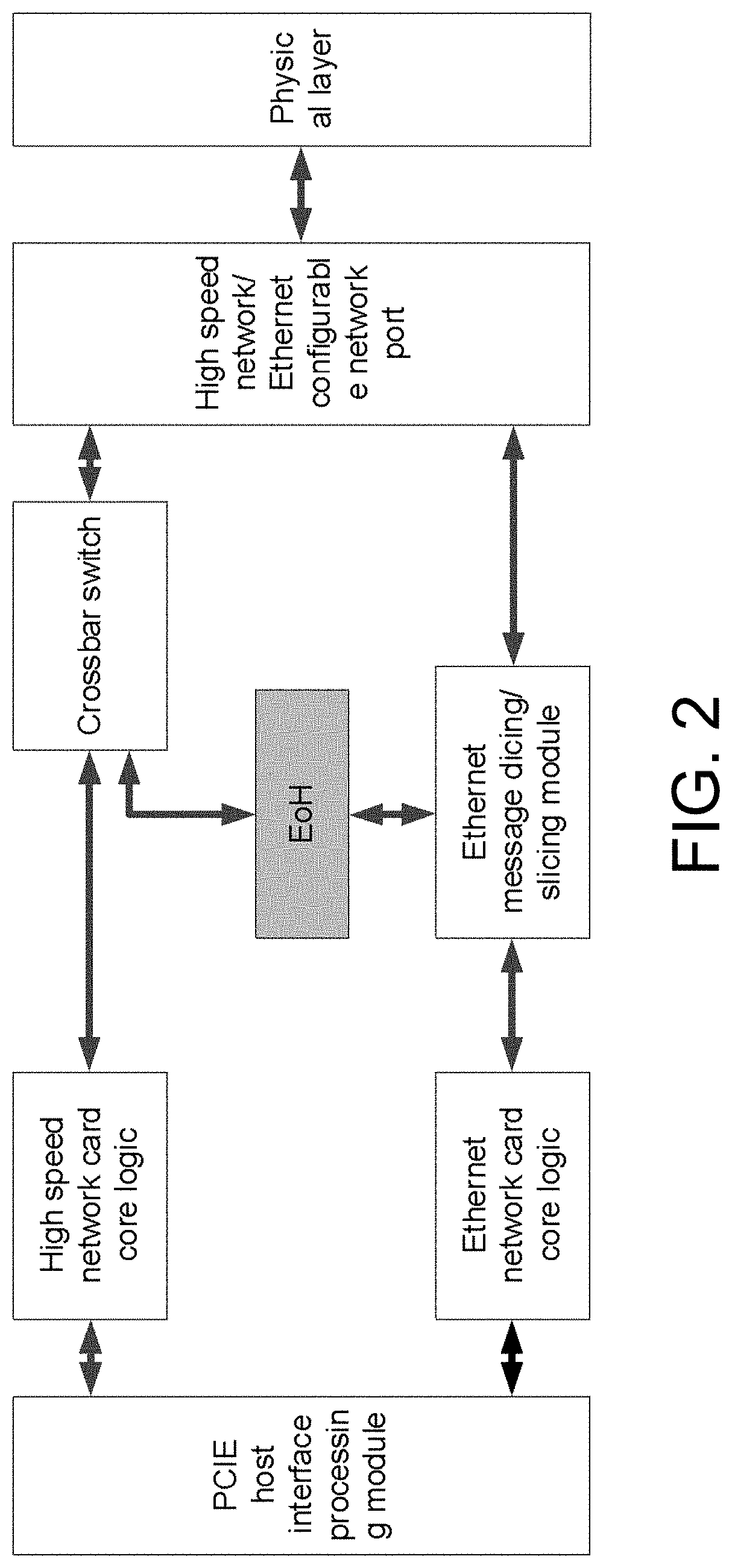
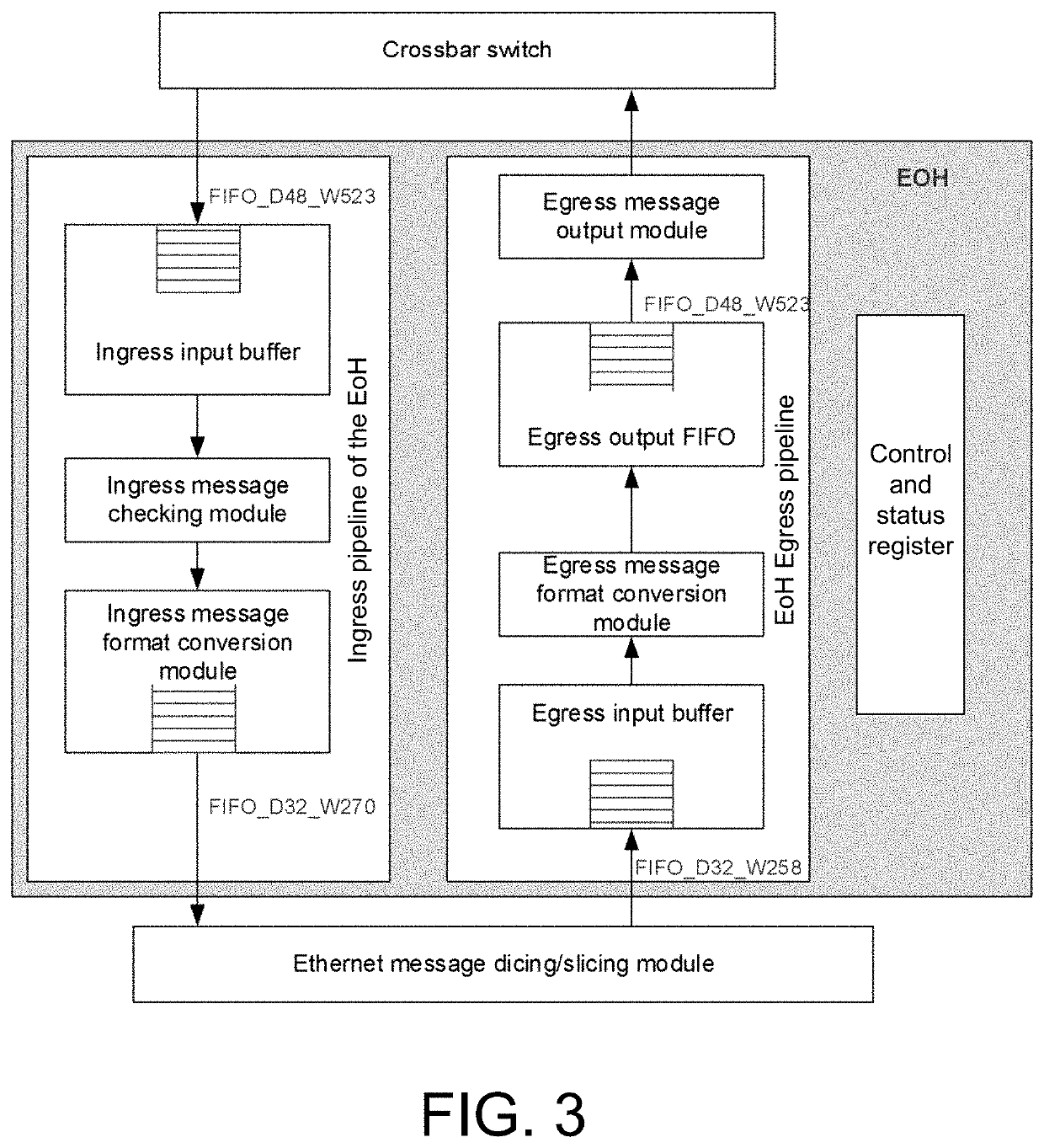
ActiveUS20210367906A1Data switching detailsElectric digital data processingCrossbar switchPhysical layer
The invention provides a converged network interface card, a message coding method and a message transmission method thereof. The converged network interface card comprises a PCIE host interface processing module, a high speed network card core logic, a crossbar switch XBAR, an Ethernet network card core logic, an Ethernet message dicing / slicing module, a physical layer, a high speed network / Ethernet message conversion module EoH, and a high speed network / Ethernet configurable network port. The invention supports customized high speed interconnection interface and a standard Ethernet interface on a set of network hardware, and supports three working modes on a set of physical hardware (high speed network mode, Ethernet mode and EoH mode transmitting Ethernet messages over the high speed network), implements seamless compatibility between the high speed network / Ethernet, and flexibly supports multimode applications such as scientific computing and cloud computing.
Owner:NAT UNIV OF DEFENSE TECH
Integrated Fan-Out Device, three dimensional integrated circuit System, and manufacturing Method thereof
InactiveCN111508934ASemiconductor/solid-state device detailsSolid-state devicesComputer hardwareWafering
Embodiments of the invention are about an integrated Fan-Out Device, a three dimensional integrated circuit System, and a manufacturing Method thereof. A three dimensional integrated circuit (3D-IC) module socket system includes an integrated Fan-Out (InFO) adapter having one or more integrated passive devices (IPDs) embedded in the InFO adapter. The InFO adapter is also integrated into the 3D-ICmodule socket system by stacking the InFO adapter between a socket and a SoW package. The InFO adapter with embedded IPDs allows for more planar area of the SoW package to be available for interfacingthe socket and provides a short distance between the embedded IPDs and computing dies of the SoW package which enhances a power distribution network (PDN) performance and improves current handling ofthe 3D-IC module socket system.
Owner:TAIWAN SEMICON MFG CO LTD
Third-party application control of devices in an IoT platform
In embodiments a computing device receives a selection of a device template associated with a physical device. The computing device receives a selection of a third-party device type associated with athird-party system. The computing device determines a device rule template associated with the device type, the device rule template comprising a first mapping between one or more commands and one ormore additional device properties in the device type. The computing device determines a second mapping between the one or more additional device properties and one or more device properties in the device template. The computing device generates an adapter template comprising the first mapping between the one or more commands and the one or more additional device properties and the second mapping between the one or more additional device properties and the one or more device properties.
Owner:AYLA NETWORKS (SHENZHEN) LTD
Computing device and method for registering identification information of network interface card in operating system
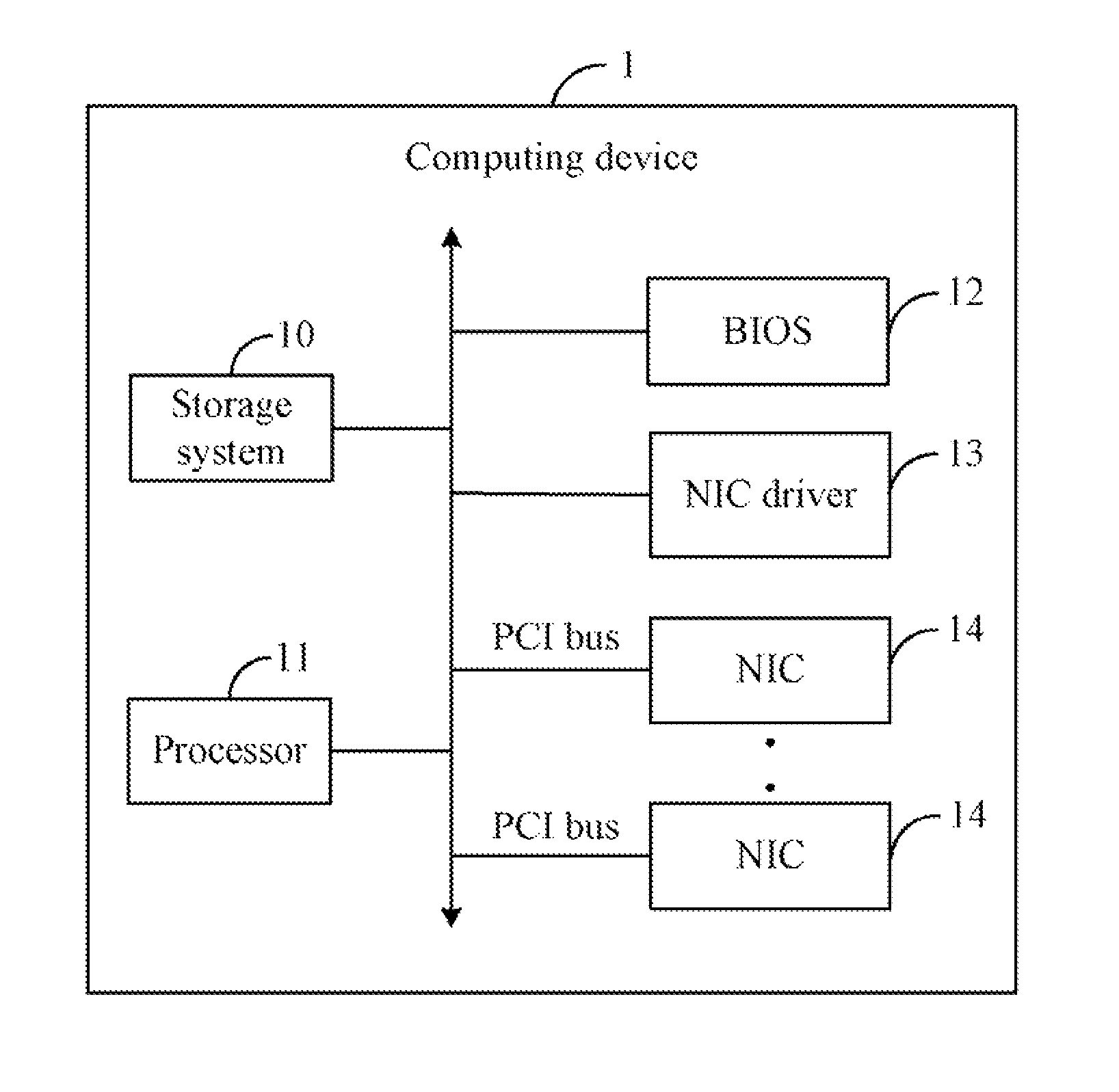
InactiveUS8762695B2Harder for the user to distinguishDigital computer detailsData resettingOperational systemBIOS
In a method for registering identification information of network interface cards (NICs) in an operating system of a computing device, each of the NICs is respectively and uniquely labeled with a number. A peripheral component interconnect (PCI) device identification (ID) of each of the NICs is allocated according to the labeled number of each NIC using a basic input output system (BIOS) of the computing device when the BIOS is booted up. Then identification information of each of the NICs is registered in the operating system according to the PCI device ID of each NIC using a NIC driver of the computing device, when the NIC driver is driven by the operating system during the booting up process of the operating system.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
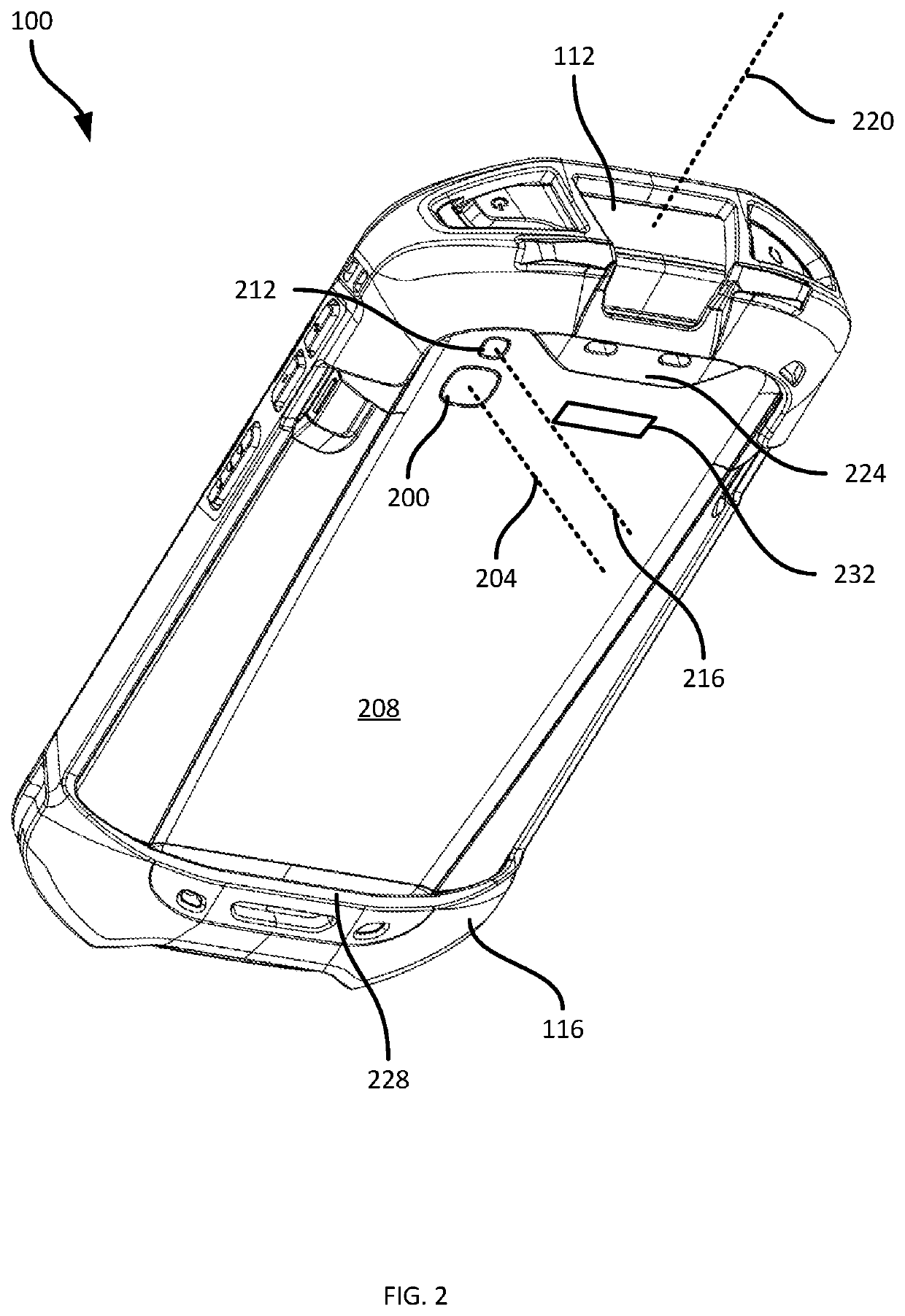
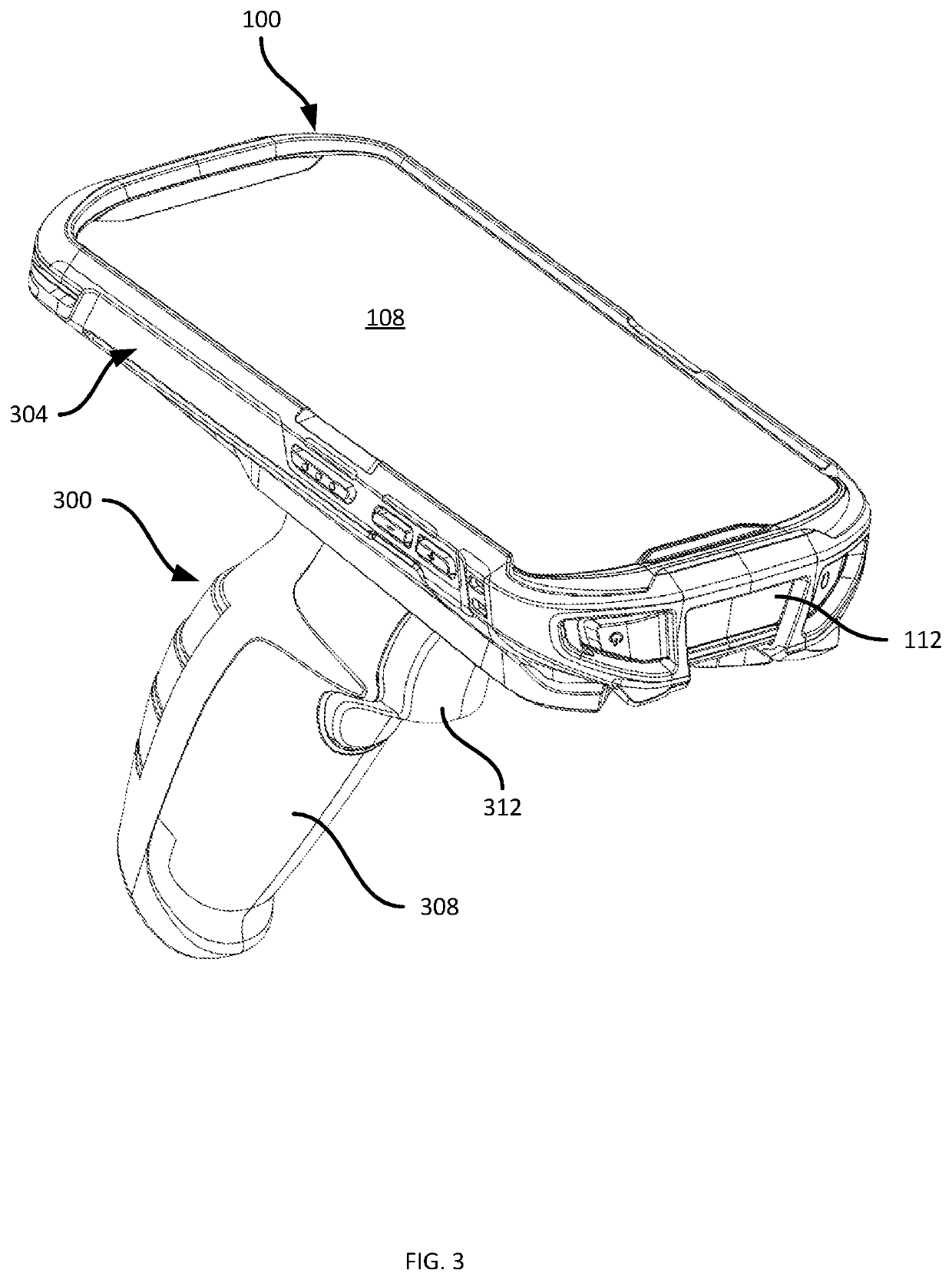
Camera-Compatible Handle Accessory for Mobile Computing Devices
PendingUS20220366164A1Television system detailsDigital data processing detailsComputer hardwareComputer graphics (images)
An accessory for a mobile computing device having a camera with a field of view (FOV), includes: an adapter including: an inner wall having a first opening; a retention mechanism configured to releasably retain the mobile computing device against the inner wall with the camera positioned over the first opening; an outer wall joined to the inner wall by a set of side walls, the outer wall having a second opening with a second perimeter larger than a first perimeter of the first opening; a set of channel walls extending between the first perimeter of the first opening and the second perimeter of the second opening, the set of channel walls defining an open channel permitting the camera FOV to traverse the adapter substantially unobstructed; and a handle mount disposed on the outer wall.
Owner:ZEBRA TECH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com