SIP-protocol-based method and system for detecting communication network attack
A technology of SIP protocol and detection method, which is applied in the field of communication security, can solve the problems of no detection and protection, and achieve the effect of protecting security and avoiding attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
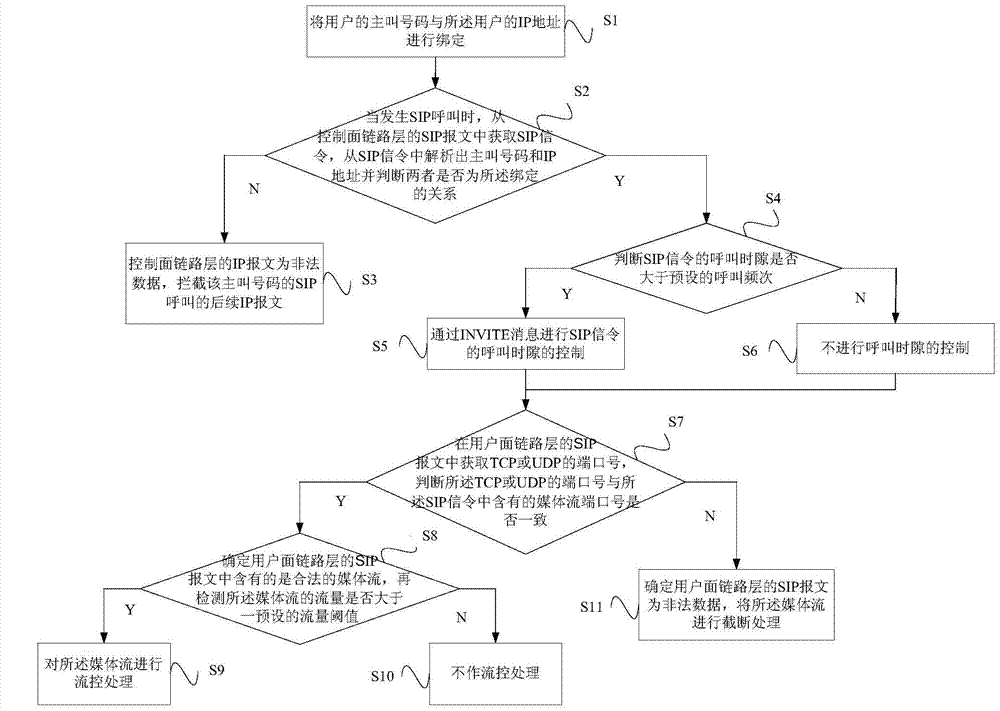
[0033] like figure 1 As shown, the present invention provides a method for detecting a communication network attack based on the SIP protocol, including steps S1 to S6.
[0034] Step S1, binding the calling number of the user with the IP address of the user; specifically, binding the calling number of the user with the IP address of the user here is to facilitate the SIP call in subsequent steps Perform authentication to prevent user account theft and prohibit illegal users from calling;
[0035] Step S2, when a SIP call occurs, obtain SIP signaling from the SIP packet at the link layer of the control plane, parse out the calling number and IP address from the SIP signaling, and determine whether the two are in the binding relationship , if so, go to step S3, otherwise go to step S4;
[0036] Step S3, the IP message of the link layer of the control plane is illegal data, and the subsequent IP message of the SIP call of the calling number is intercepted;
[0037] Preferably,...
Embodiment 2
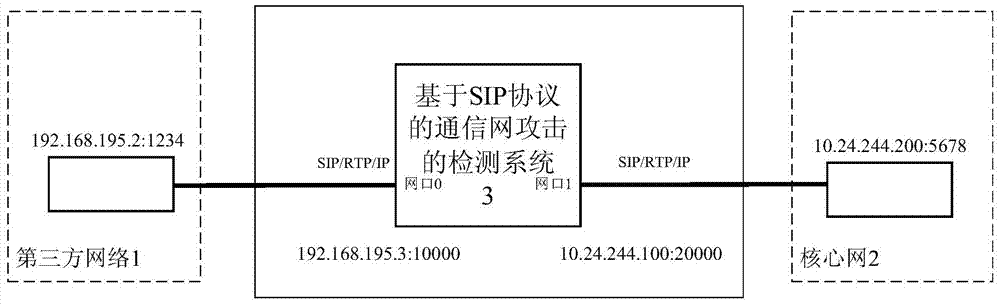
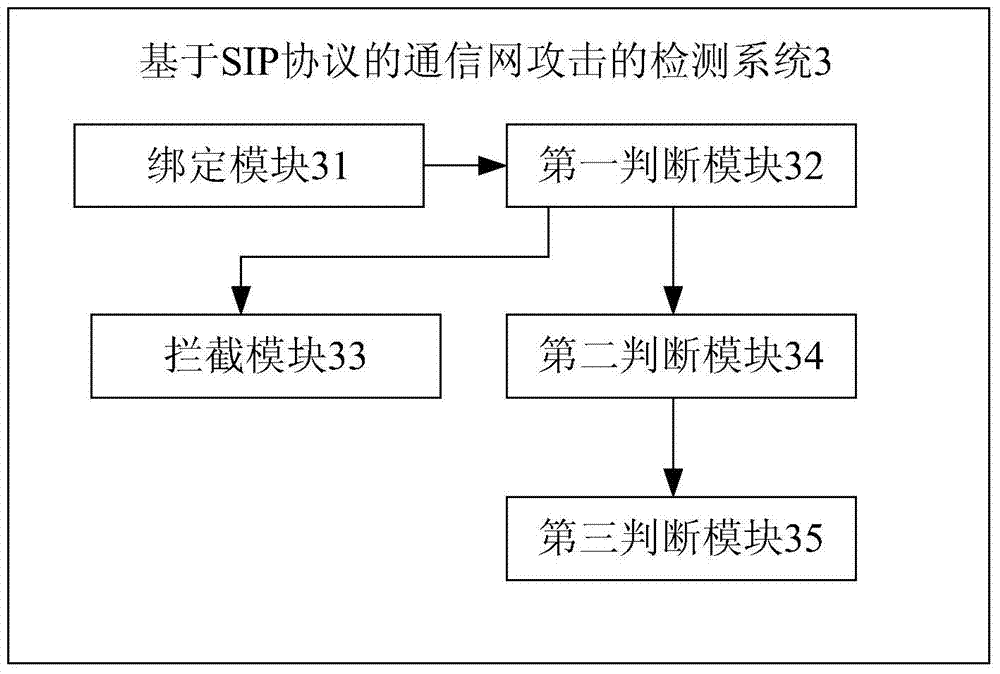
[0054] like figure 2 and 3 As shown, the present invention also provides another SIP protocol-based communication network attack detection system 3 , including a binding module 31 , a first judging module 32 , an intercepting module 33 and a second judging module 34 .
[0055] A binding module 31, configured to bind the user's calling number with the user's IP address;
[0056] The first judging module 32 is used to obtain the SIP signaling from the SIP message of the link layer of the control plane when a SIP call occurs, parse out the calling number and the IP address from the SIP signaling and judge whether the two are all The above-mentioned binding relationship, if so, then start the interception module 33, if not, then start the second judging module 34;
[0057] Intercepting module 33, is used for determining that the IP message of control surface link layer is illegal data, intercepts the follow-up IP message of the SIP call of this calling number;
[0058] Prefera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com