Image certainty encryption double-blind secrecy matching method
A matching method and deterministic technology, which is applied in image analysis, image data processing, image data processing, etc., can solve the problems of difficult key transmission and distribution, uncrackable, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] An image deterministic encryption double-blind confidential matching method, the method comprises the following steps:
[0035] (1) Randomly generate a position replacement matrix N according to the size of the image matrix, and save the matrix;
[0036] (2) Use the permutation matrix N to scramble the pixel positions of the target image matrix Y to be matched in terminal A, and obtain the encrypted target image Y to be matched * ;
[0037] (3) Use the permutation matrix N to scramble the pixel positions of each floating image matrix in the terminal B database to obtain the encrypted floating image matrix X * (i), i=1, 2, ..., M, form the encrypted floating image matrix database;
[0038] (4) The target image Y to be matched after being encrypted in terminal A * Send to terminal B, and the encrypted floating image matrix X in terminal B * (i) subtraction, i=1, 2, ..., M, to obtain the residual sequence set {R(i): i=1, 2, ..., M};
[0039] (5) Calculate the non-stat...
Embodiment 2
[0042] An image deterministic encryption double-blind secret matching technology method, the method includes the following steps:
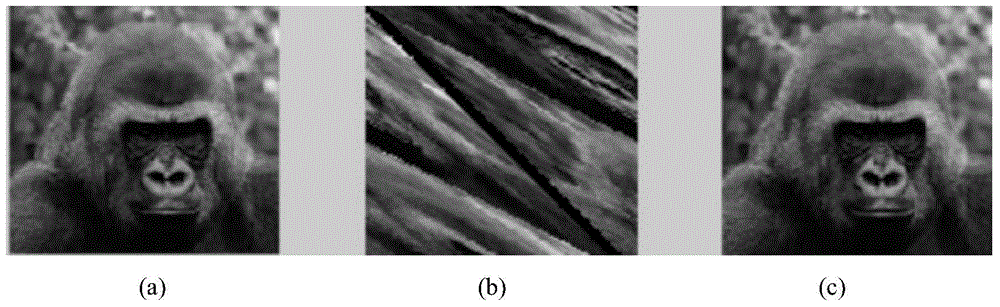
[0043] (1) Establish a database with 20 floating image matrices in terminal B, each image size is 200X200, such as figure 1 as shown in (a);
[0044] (2) Randomly generate a 200×200 position replacement matrix N, and save the matrix;
[0045] (3) Use the position replacement matrix N to scramble the positions of the floating image matrices in the terminal B database to obtain the encrypted floating image matrix X * (i), i=1, 2, ..., 20, obtain the encrypted floating image matrix database, such as figure 1 as shown in (b);
[0046] (4) Use the random matrix N to scramble the pixel position of the target image Y to be matched in terminal A, and obtain the scrambled encrypted target image Y to be matched * ;
[0047] (5) Send the scrambled and encrypted target image to be matched in terminal A to terminal B, and the encrypted floating image matr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com