Agent re-encryption method for improving outsourced encrypted data sharing function
A proxy re-encryption and encrypted data technology, applied in the transmission system, electrical components, etc., can solve the problems of high overhead, inability to realize multi-user broadcast, high calculation and transmission overhead, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] In order to make the objectives, technical solutions, and advantages of the present invention clearer, the following further describes the present invention in detail with reference to the accompanying drawings and embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention. In addition, the technical features involved in the various embodiments of the present invention described below can be combined with each other as long as they do not conflict with each other.
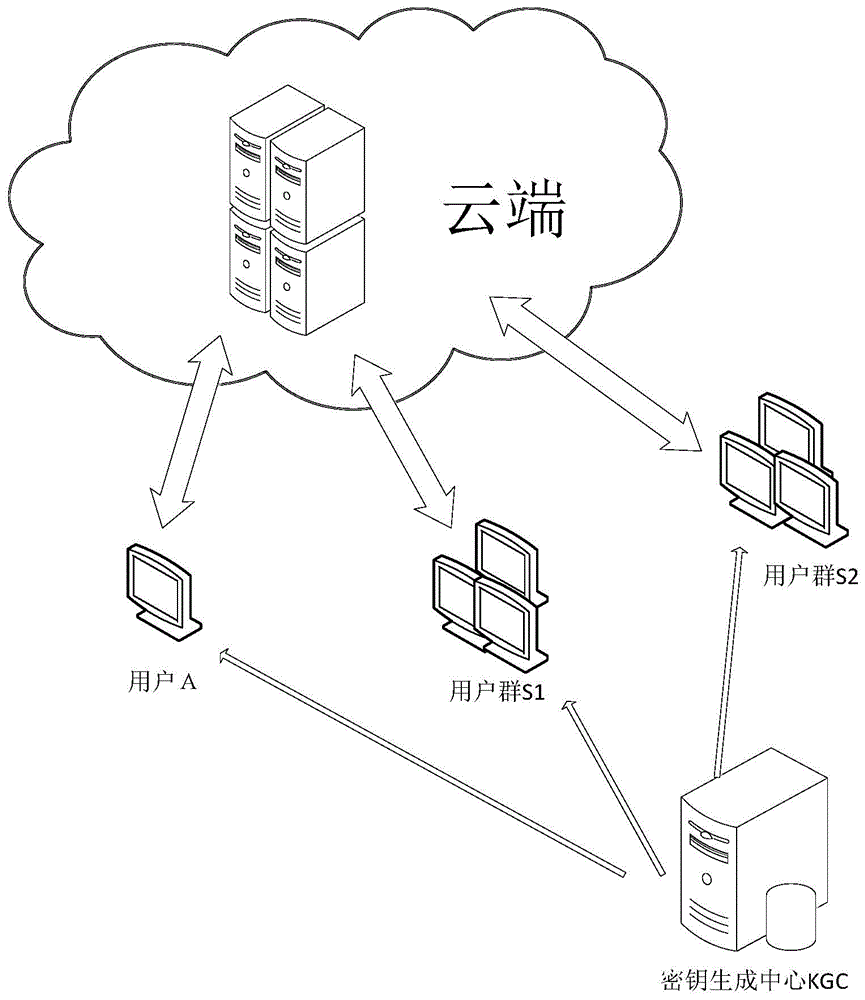
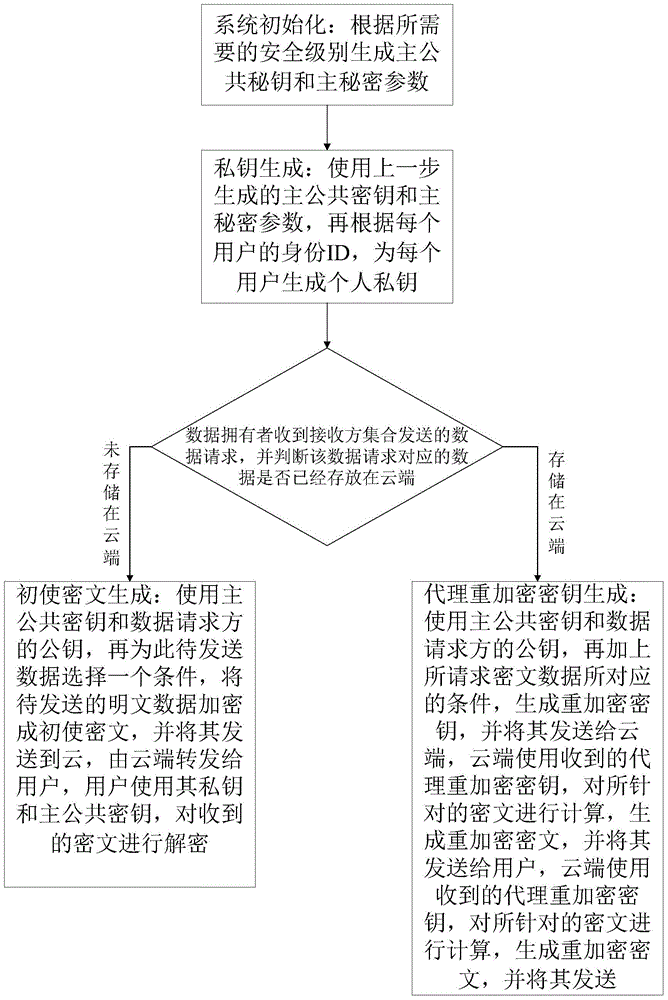
[0075] Such as figure 1 As shown, it shows the application environment diagram of the method of the present invention. The method involves three parties: user, Key Generation Center (KGC), and data storage cloud (Cloud). The user can encrypt the initial ciphertext for a friend and send it to the cloud. If a friend requests an existing ciphertext, the user is responsible for generating the re-encrypti...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap