DES system capable of performing circulatory iteration to resist channel attack and remapping achieving SBOX method
A side-channel attack and cyclic iteration technology, applied in the field of data encryption, can solve problems such as precarious security, and achieve the effects of improving security, simplifying circuit structure, and reducing signal delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The present invention will be further elaborated below by describing a preferred specific embodiment in detail in conjunction with the accompanying drawings.
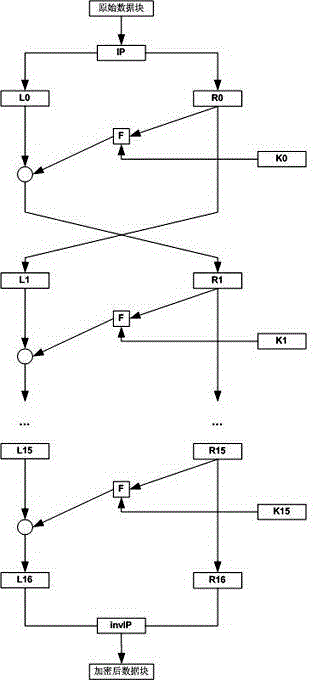
[0056] Such as figure 1 As shown, a DES system capable of cyclic and iterative resistance to side-channel attacks, the DES system includes: a computing unit, a multi-layer computing storage unit, a data storage unit and a mask storage unit.
[0057] Wherein, the multi-layer operation storage units are connected sequentially, and each layer of operation storage units is connected with the operation unit. The data storage unit is respectively connected with the operation storage unit and the operation unit of the last layer; the mask storage unit is connected with the operation unit.
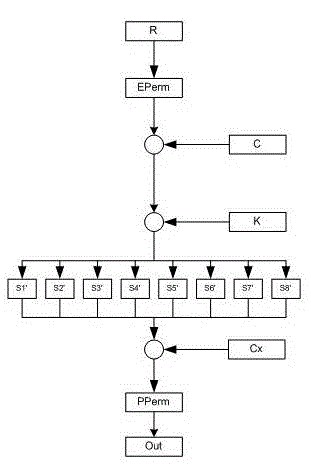
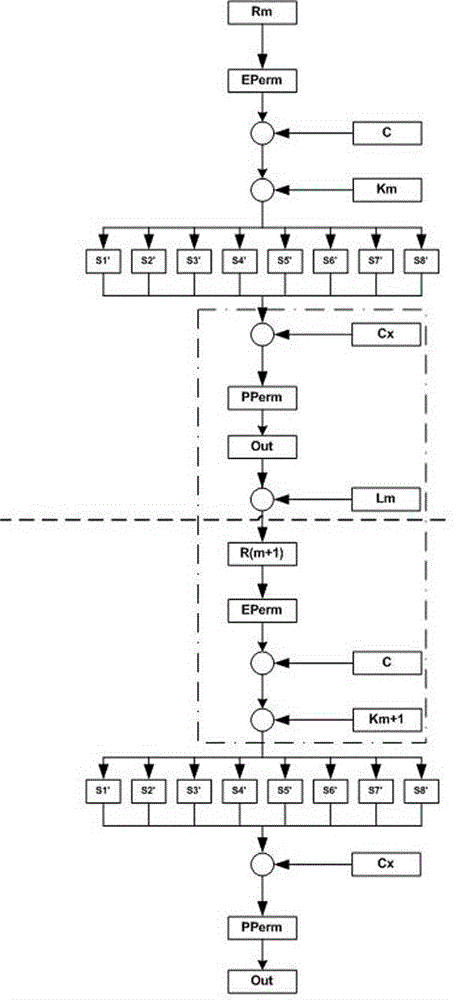
[0058] Each layer of operation storage unit includes L data storage, R data storage and K key storage; the L data storage, R data storage and K key storage of the operation storage unit of this layer are respectively connected with ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com