Method for preventing confidential conference information from leakage and terminal
A technology of information leakage and meetings, applied in the field of video communication, can solve problems such as difficult management and control, loose control of personnel access, long material life cycle, etc., to prevent theft, improve meeting efficiency, and save labor costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The specific embodiments of the invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
[0036] The present invention is mainly composed of a distributed C / S system framework, a terminal based on an Android operating system, and a management device based on a confidential conference server. The above-mentioned terminal may be a PC, or a portable tablet computer or a mobile phone, which is not specifically limited in the present invention.
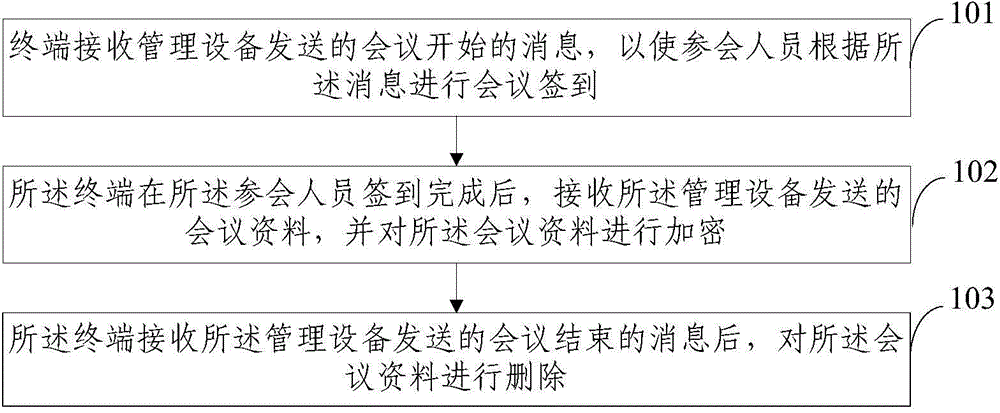
[0037] figure 1 A schematic flowchart showing a method for preventing leakage of confidential meeting information, as shown in figure 1 As shown, the method for preventing confidential meeting information leakage includes the following steps:
[0038] 101. The terminal receives a conference start message sent by the managem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com